Exim remote command execution vulnerability has been exploited in the wild since June. This week, Security researchers have observed that Exim vulnerability (CVE-2019-10149) is being exploited to install a new Watchbog Linux malware variant. After successful exploitation, Watchbog will download and execute cryptocurrency miner payload on the compromised servers. As per Shodan search from today, there are over 1.5 million unpatched Exim servers that are vulnerable to this attack. SonicWall Capture Labs Threat Research team continues to observe attempts to exploit this vulnerability.
Exim
Exim is a mail transfer agent (MTA) used on Unix-like operating systems. It contains implementations of SMTP server for incoming messages as well ,as a SMTP ( Simple Mail Transfer Protocol) or LMTP ( Local Mail Transfer Protocol ) client for outgoing emails.
SMTP
SMTP is a connection-oriented, text-based protocol in which a mail sender communicates with a mail receiver by issuing command strings and supplying necessary data over a Transmission Control Protocol (TCP) connection. An SMTP session consists of commands originated by an SMTP client (the initiating agent) and corresponding responses from the SMTP server (the listening agent) so that the session is opened, and session parameters are exchanged.
An SMTP transaction consists of the follwing three command/reply sequences:
1. MAIL command, to identify the sender, to establish the return address or bounce-address.
2. RCPT command, to establish a recipient of the message. This command can be issued multiple times, one for each recipient.
3. DATA command, to give the mail data and finally the end of mail data indicator confirming the transaction.
SMTP Mail Transaction:

CVE-2019-10149:
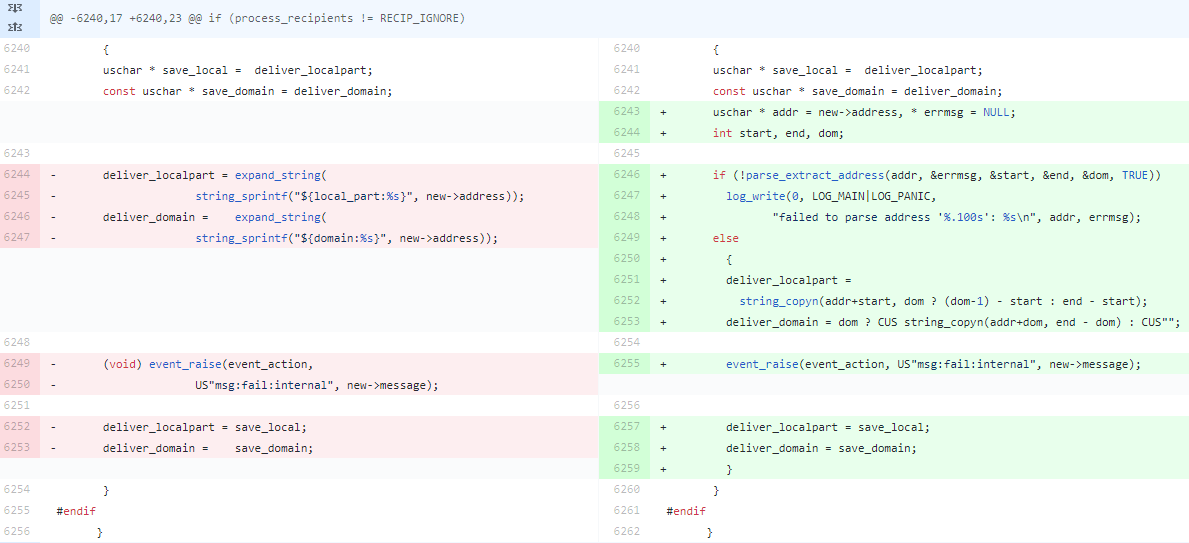
A command injection vulnerability has been reported in Exim. This is due to insufficient sanitization of recipient email addresses, whether the recipient is local or remote. In the vulnerable versions, local part of the receipt address is sent as input to the expand_string() method without enough validation. A remote attacker can exploit this vulnerability by attempting to send an email to a crafted recipient on the target server. Successful exploitation results in the execution of arbitrary commands as the root user.
Fig: Snapshot of the code snippet
Local Exploitation:
The utility expand_string() in the above shown code recognizes the “${run{<command> <args>}}” specified as input, and because new->address is the recipient of the mail that is being delivered, a local attacker can simply send a mail to “${run{…}}@localhost” and execute arbitrary commands, as root.
Remote Exploitation (Non-default configuration):
The above exploitation method doesn’t work remotely as the Exim’s default configuration requires the local part of the recipient’s address (the part that precedes the @ sign) to be the name of a local user when requests come from the remote server.
But in various non-default configurations this vulnerability can be exploited remotely say If the “verify = recipient” ACL that checks the local part of the recipient’s address to be the name of a local user was removed manually by an administrator or If Exim was configured to recognize special tags like “+” in the recipient’s address then a remote attacker can simply use the local exploitation method i.e RCPT TO “local_user+${run{…}}@localhost” instead of local_user@localhost.
Remote Exploitation (Default Configuration):
Another elaborate way specified in the vulnerability report that allows remote exploitation in the Exim’s default configuration. If the attacker can set up a malicious email server on a domain they control and place the malicious string expansion in the local portion of the sender’s address and send a message with a valid recipient but crafted to bounce back to the attacker controlled email server. In order to make the outgoing message from Exim server fail i.e to set RECIP_FAIL_TIMEOUT, the attacker controlled server can very slowly send a long SMTP response over a 7 day period and finally send a response such as a 550 error to cause the outgoing message to be “frozen” by Exim. On the next scheduled queue run, Exim will then attempt to deliver the bounce message once again but because the message is older than the default permitted age for frozen messages, process_recipients is set to RECIP_FAIL_TIMEOUT, and the malicious string specified in the sender address is then expanded by the expand_string() utility and executed as root.
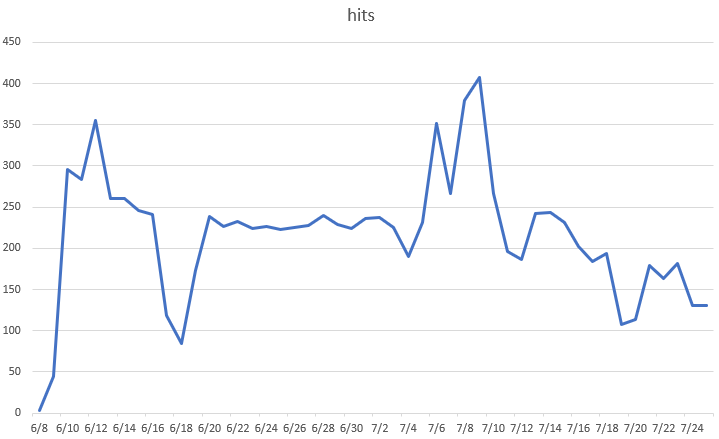
Trend Chart:
The below graph shows how this vulnerability has been actively exploited.
Fig: IPS hits for the sig ID 14240 in the last 40 days
Majority of the exploit attempts come from the IP address “89.248.171.57”. Exim users have also reported online that they have been hacked by this attacker. This attacker is still actively looking for vulnerable Exim servers.
Fix:
Exim version 4.87 to 4.91 is vulnerable by default. This vulnerability is fixed in version 4.92.
SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
IPS: 14240 Exim deliver_message Remote Command Execution 1
IPS: 14241 Exim deliver_message Remote Command Execution 2
IPS: 14242 Exim deliver_message Remote Command Execution 3
IPS: 14243 Exim deliver_message Remote Command Execution 4
The SonicWall Capture Labs Threat Research Team gathers, analyzes and vets cross-vector threat information from the SonicWall Capture Threat network, consisting of global devices and resources, including more than 1 million security sensors in nearly 200 countries and territories. The research team identifies, analyzes, and mitigates critical vulnerabilities and malware daily through in-depth research, which drives protection for all SonicWall customers. In addition to safeguarding networks globally, the research team supports the larger threat intelligence community by releasing weekly deep technical analyses of the most critical threats to small businesses, providing critical knowledge that defenders need to protect their networks.