CVE-2019-0859 exploits active in the wild
The SonicWall Capture Labs Threat Research observed CVE-2019-0859 being actively exploited in the wild.
An elevation of privilege vulnerability exists in Windows when the Win32k component fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
CVE-2019-0859 is a Use-After-Free vulnerability in the CreateWindowEx function. The exploit uses this vulnerability to elevate privilege and run shellcode.
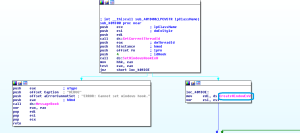
The above code is used to execute arbitrary shellcode.

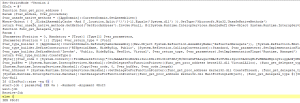
The injected shellcode payload (stored in $var_code) creates a named pipe. Any data read from the named pipe is executed directly as shellcode.
SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
ASPY 5452: Malformed-File exe.MP.64
This threat is detected pro-actively by Capture ATP w/RTDMI
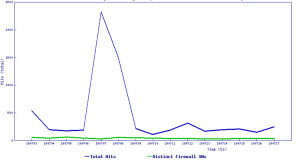
Threat Graph:
IOC:
eea10d513ae0c33248484105355a25f80dc9b4f1cfd9e735e447a6f7fd52b569
9f9ea63ad90da73185ff84378844902bf5ce8af0f1b9c8895775697822652d4f
772392b04d05f4b219c20daafa9f2edf727f51ab09c9796e5cdfb4916432bb66
1dfc83d5bc38b88623d54103aa58a2c08b494bc0d0d1098e857dde87f0be0616





