Mongo-Lock Ransomware
Overview:
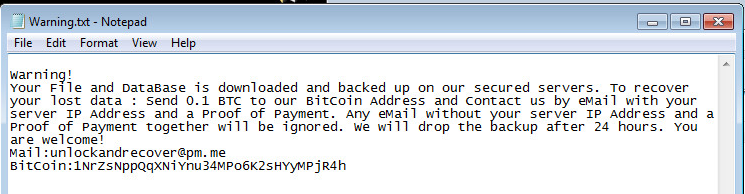
SonicWall Capture Labs Threat Research Team, recently found, MongoLock ransomware. MongoLock tries to remove files, along with formatting drives using special commands through “cmd” and targets databases with weak security settings. MongoLock will drop a ransom note in the form of a “warning.txt” using notepad or as an entry inside any database it may find on the system. This is a new form of MongoLock ransomware that is actively being used in the wild today with a global reach. The ransom note is asking for 0.1 BTC to a specified Bitcoin wallet. A picture of the ransom note is below:
Sample Static Information:
Unpacked Hash Information:
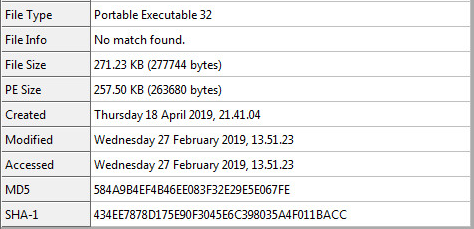
Entropy and Packer Information:
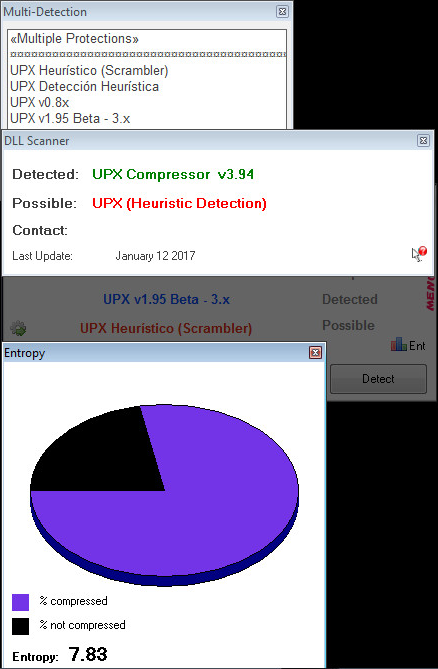
Now that we know what the packer and protector information is we can start to unpack it below.
Unpacking The Sample:
Unpacking this sample is trivial because CFF Explorer allows us to click just a single button to unpack it.
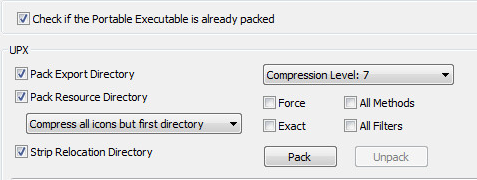
Once you unpack the sample with CFF Explorer press “Save As” to save the unpacked sample. The new hash information now looks like the following:
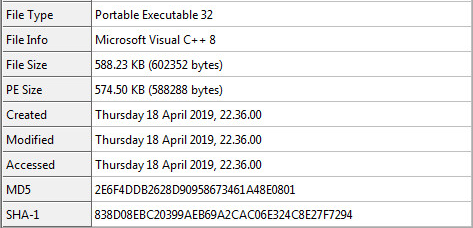
RDG tells us that the unpacked sample has traces from aPLib compression and it’s using IsDebuggerPresent().
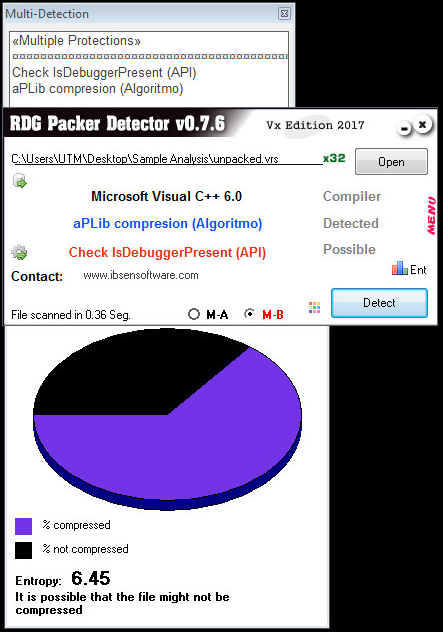
The following crypto signatures were found, Base64, CryptCreateHash, CryptEncrypt, CryptGenRandom, CryptHashData.
Ransom Note:
A long static ransom string is checked, then written to a warning file.
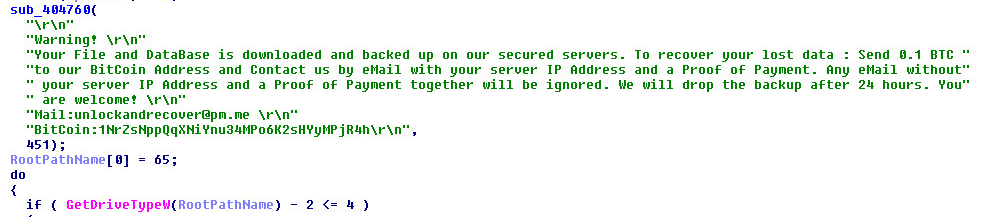
A glimpse into how they write the warning:
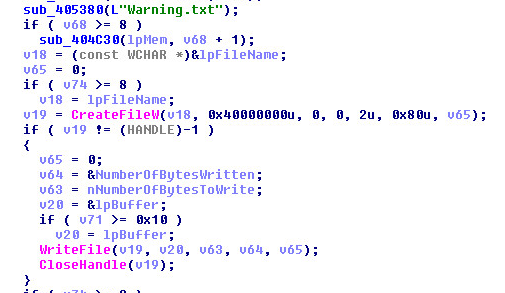
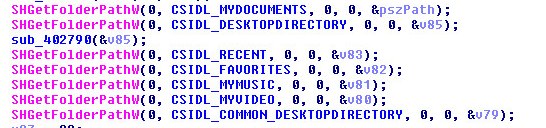
Directory List:
SHGetFolderPathW API is a deprecated API. This API gets the path of a folder identified by a CSIDL value.
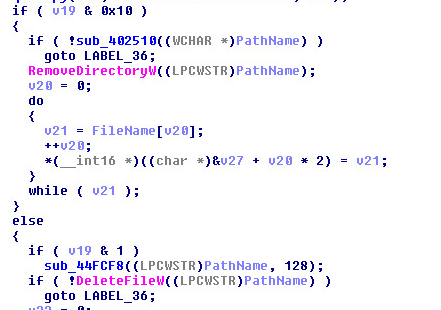
Removal of Directories and Files:
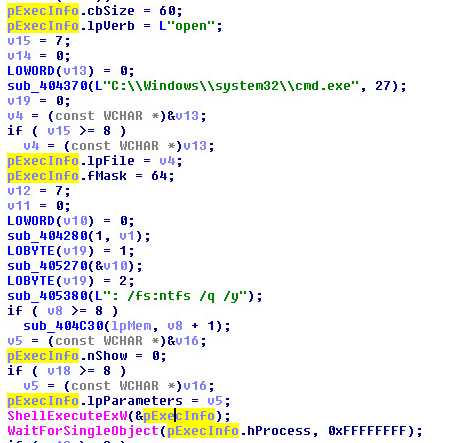
Formatting:
The string, : /fs:ntfs /q /y will be updated with “format”, a drive letter and “cmd” will be called upon to execute the formatting of your drives.
Supported Systems:
The sample was tested and debugged on (x86) – 32 Bit, Windows 7 Professional.
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: MongoLock.A





