.NET Nanocore Trojan
Overview:
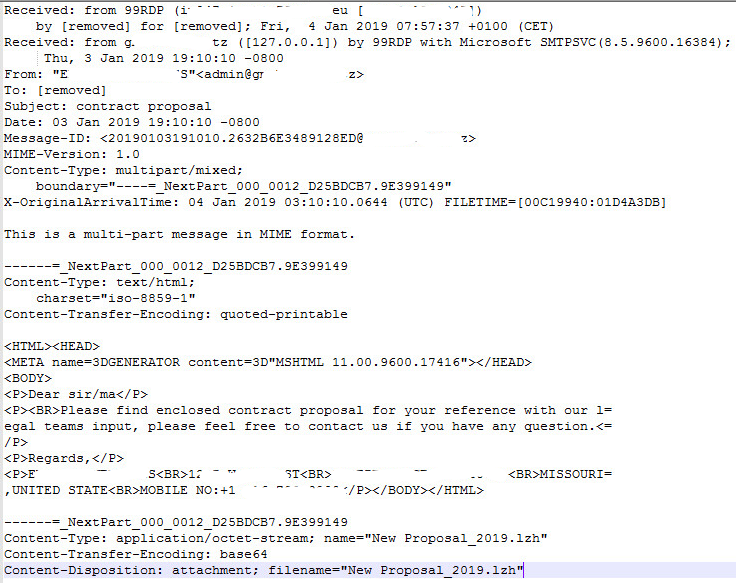
The SonicWall Capture Labs Threat Research Team would like to showcase the following spear phishing attempt with the attached .NET Nanocore Trojan. The following email details are below:
—
From: “E… V…”<a…@g…co.tz”
Subject: contract proposal
Date and Time: 03 Jan 2019 19:10:10 -0800
Dear sir/ma
Please find enclosed contract proposal for your reference with out legal teams input, please feel free to contract us if you have any question.
Regards,
E… V…
1… 25th St., MO xxx, MISSOURI, UNITED STATE
MOBILE NO: 1 8xx xxx xxxx
—
This picture explains the email in more detail:
This email was attached with the following binary data:
Content-Type: application/occtet-stream; name=”New Proposal_2019.lzh”
Content-Transfer-Encoding: base64
Content-Disposition: attachment; filename=”New Proposal_2019.lzh”
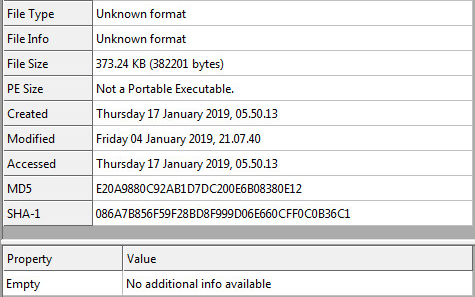
Compressed Static Information:
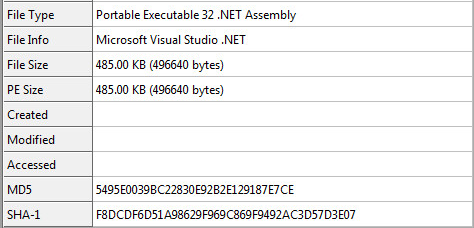
Decompressed Static Information:
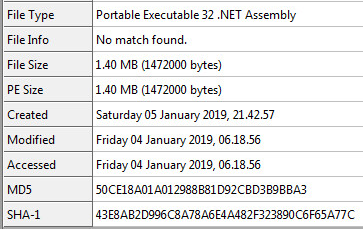
Decrypted Static Information:
Unpacking & Decrypting The Sample:
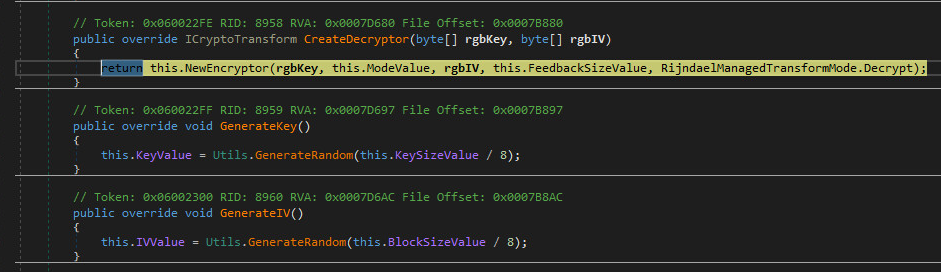
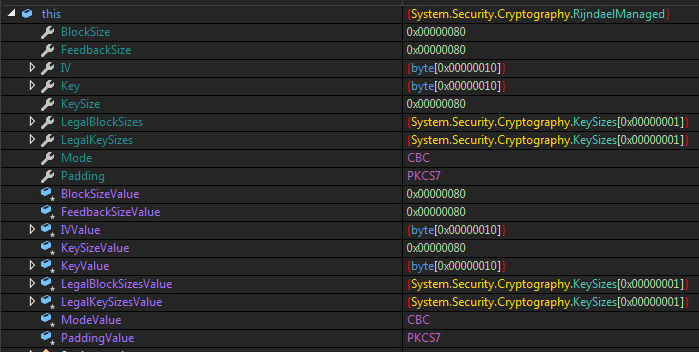
The encryption used is called “Rijndael” selected by (NIST) as the candidate for the Advanced Encryption Standard (AES). The key and IV, uses 16 bytes or you can say it’s 128 bit. The mode used is called “CBC” which stands for “Cipher Block Chaining”. The Sample also uses RSA Security LLC standard called “PKCS7”. The Cryptographic Message Syntax Standard.
Host-Based Persistence:
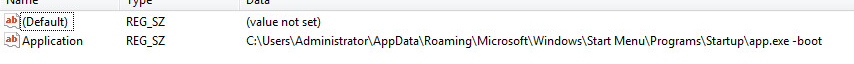
Once decrypted, it will copy the executable to the “Startup” Folder and add the “-boot” parameter.
Registry Location: HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Application
It also copies itself to the following location and renames itself.
Registry Location: HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\UDP Subsystem
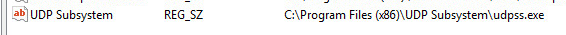
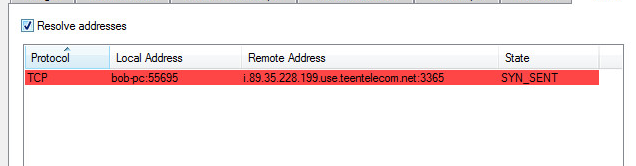
Active Network Information:
This sample, connects to (i.89.35.228.199.use.teentelecom.net:3365).
The port 3365 is known as a “Content Server”. This will download and upgrade files on the host machine.
SonicWall, Gateway Anti-Virus (GAV), provides protection against this threat:
- GAV: NanoBot.RAR (Trojan)
- GAV: NanoBot.RSM (Trojan)




