Jenkins CI server at Risk: High risk vulnerability
Jenkins is an open source build automation tool written in Java. It is the most widely used tool for Continuous Integration (CI) & Continuous Delivery (CD). It offers hundreds of plugins to support software build development, deployment & test automation process. Jenkins CI server runs on servlet containers such as Apache Tomcat. It supports various version control software such as subversion, Git, CVS, Perforce etc.
A serious policy bypass vulnerability has been reported in Jenkins CI server (CVE-2018-1999001). This is due to insufficient validation of login requests by Jenkins instance. A remote attacker could exploit this vulnerability by sending a crafted HTTP request to a vulnerable Jenkins CI server. Successful exploitation causes Jenkins to revert to default settings granting administrator access to anonymous users
CVE-2018-1999001 :
Unauthenticated users could provide maliciously crafted login credentials that cause Jenkins to move the config.xml file from the Jenkins home directory. This configuration file contains basic configuration of Jenkins, including the selected security realm and authorization strategy. If Jenkins is started without this file present, it will revert to the legacy defaults of granting administrator access to anonymous users.
Root configuration file: JENKINS_HOME\config.xml
[ This contains basic configuration of the Jenkins instance. ]User Configuration file: JENKINS_HOME\users\<username>\config.xml
[This contains user information such as the users password and role.]When an user attempts to login Jenkins web interface, the following HTTP POST request is sent to the Jenkins instance:
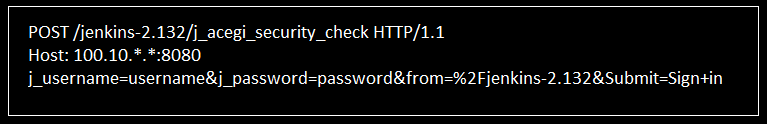
Upon receiving the login request, Jenkins instance calls getOrCreate() function. getOrCreate() checks if the current path to the user’s config.xml file contains any unsanitized directory traversal character. If unsanitized directory traversal character is found, the config.xml file is moved to a different file path in order to fix another vulnerability.
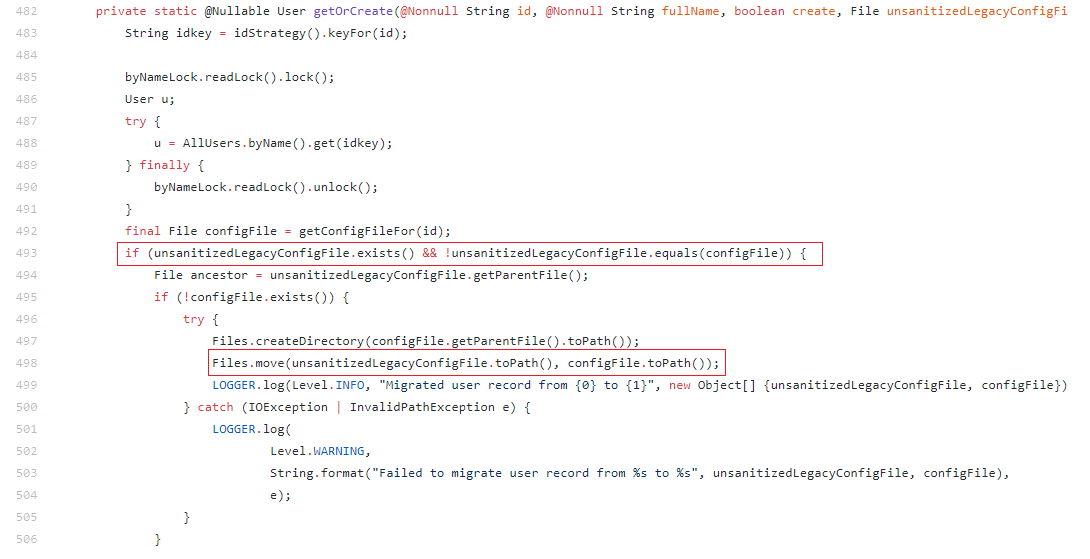
Fig:1 code snippet from User.java in Jenkins
If a user attempts to login with an username “..”, config file path will become JENKINS_HOME\users\..\config.xml i.e JENKINS_HOME\config.xml. ‘If’ statement unsanitizedLegacyConfigFile exists & contains bad characters passed. As a result, Jenkins instance moves the config.xml to a different path JENKINS_HOME/$002e$002e/config.xml. When Jenkins get restarted without config.xml in the home directory, it reverts to default settings allowing administrator access to anonymous users
Patch:
SonicWall has observed attackers leveraging this vector. We strongly recommend all customers to update the Jenkins to version 2.133
Find below the Security advisory from Jenkins:
https://jenkins.io/security/advisory/2018-07-18/#SECURITY-897
Sonicwall Threat Research Lab provides protection against this exploit with the following signature:
- IPS: Jenkins CI Server Authentication Bypass




