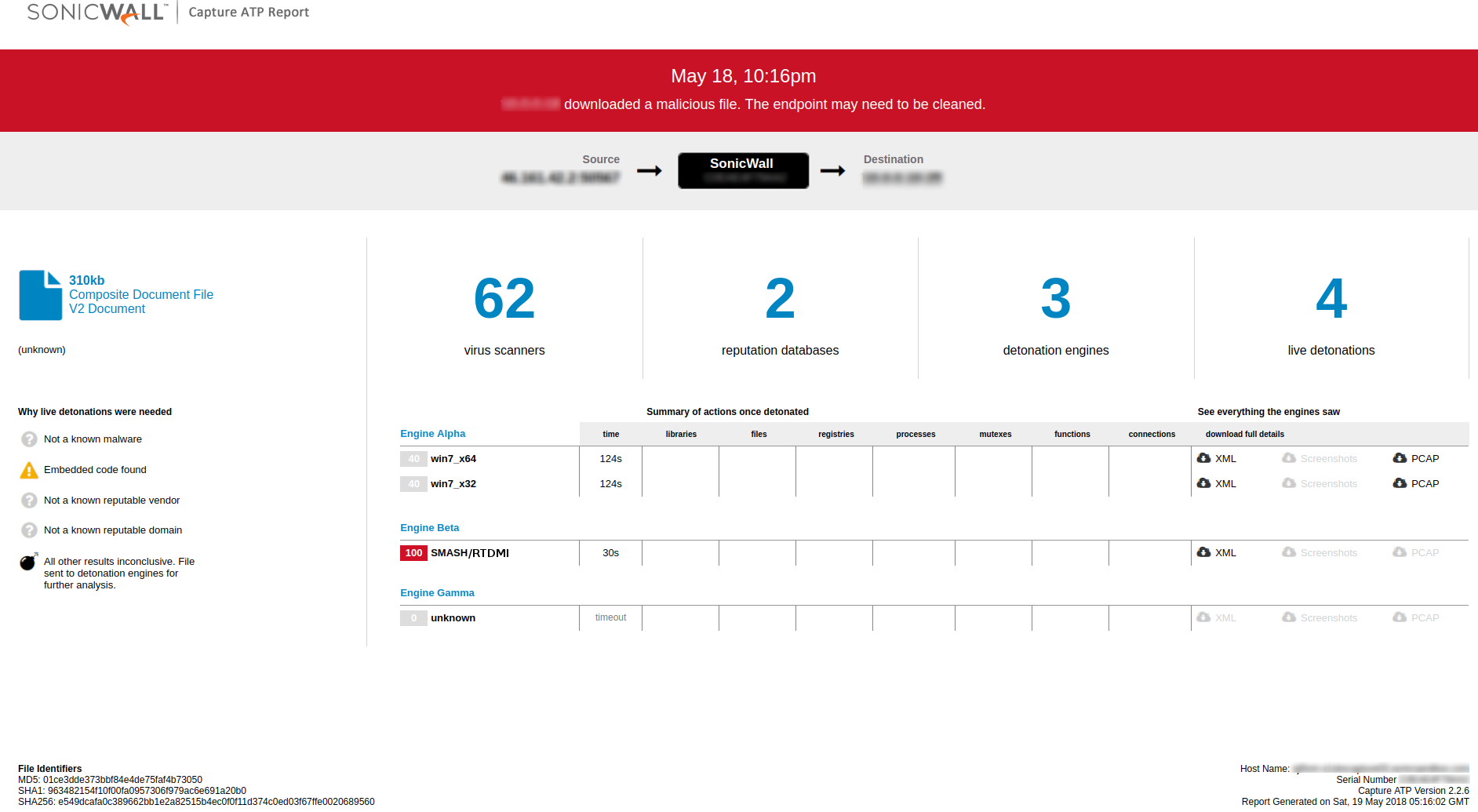
SonicWall RTDMI engine identifies malicious VBA macro laced MS Office Document in real-time (May 22, 2018)
SonicWall RTDMI engine identified a new malware campaign using malicious Microsoft Office Document files. The document file contains VBA macro code, which gets triggered once the document is opened. Upon execution the macro decrypts a URL hidden inside an embedded form in the document and downloads the payload. SonicWall RTDMI engine technology can look inside multiple layers of packaging and obfuscation to find well entrenched malware components in real-time and provide unparalleled detection capabilities. The non-existence of this malicious file on popular malware search portals (VirusTotal or Reversing Labs) indicates the effectiveness of the RTDMI engine .
On opening the office document, VBA code is executed to decrypt the URL. XOR based encryption is used by the malware and the key is stored as a custom variable in the document itself:

Encrypted URL is stored inside a form as shown below:
The payload being downloaded belongs to a Ransomware family called GANDCRAB, we blogged about this ransomware recently. The RTDMI engine also detects the payload ransomware as it gets downloaded.
On execution, the ransomware drops a copy of itself into %appdata%/Microsoft/<random_name.exe> folder, and starts encrypting the files on the hard drive. It modifies the desktop background with a ransom alert. It also drops a text file named ‘CRAB-Decrypt.txt’ with ransom notes as shown below:
Indicators of Compromise:
- e549dcafa0c389662bb1e2a82515b4ec0f0f11d374c0ed03f67ffe0020689560 : Malicious Document File
- 52b4f795ace71a37c133fa8c36f8502103f0ae4dcbe3bc4210f0f95557ec66ac : GandCrab Ransomware
- hxxp://209.141.49.93/upxxxe.fud
Capture ATP Report: