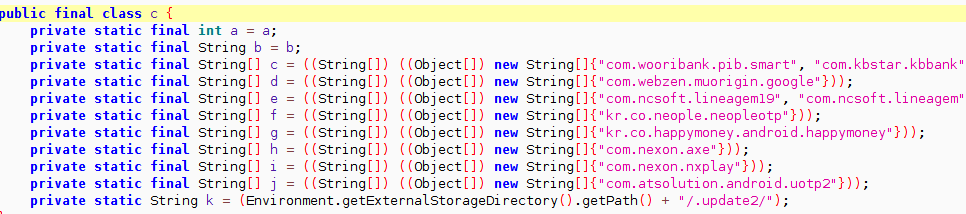
On May 25, the General Data Protection Regulation (GDPR) will officially go into effect in the European Union (EU). As you may have noticed, many organizations have been notifying end-users — regardless of their location — of updates to their terms of service (TOS) and privacy policies.
For the sake of simplicity, many companies are looking for vendors that help them align their privacy policies to adhere to compliance requirements worldwide versus having separate and distinct rules for every region. If GDPR remains the benchmark for data privacy, GDPR may become a welcome standard. However, if governing bodies decide to issue different data privacy laws for their own constituents, more confusion could be introduced across geographic customer bases.
To help further educate and build awareness, please reference these answers to the most popular questions about GDPR.
What is the GDPR?
The GDPR is legislation enacted by the EU to protect all EU citizens from privacy and data breaches. The GDPR applies to companies and organizations located in the EU, as well as to companies outside the EU that collect, use, transmit or store personal data of EU citizens, regardless of where the activities take place. At a high level, GDPR:
- Takes effect on May 25, 2018
- Applies generally to organizations located in the EU, as well as those outside the EU that handle the personal data of EU citizens
- Applies specifically to data controllers and data processers; with a controller being a company that determines the purposes and means of processing personal data, while a processor is responsible for processing personal data on behalf of a controller
- Is designed to protect the personal data of EU citizens, which is defined as any information about an identifiable person
- Requires organizations to give individuals access to and control over their data, and to take reasonable measures to protect it
Why was the GDPR drafted?
GDPR was designed to harmonize data privacy laws across Europe, to protect and empower all EU citizens’ data privacy and to reshape the way organizations across the region approach data privacy. By making data protection law identical throughout member states, the EU believes this will collectively save companies €2.3 billion annually.
When will the GDPR apply?
GDPR will be effective in all EU member states on May 25, 2018. Until it becomes effective, the 1995 Data Protection Directive (Directive 95/46/EC) and other country-specific law will continue to apply. Countries outside the EU may have their own data privacy laws and organizations are obligated to comply with these laws as well.
Who does the GDPR apply to?
If you are an organization located within the EU or an organization located outside of the EU and collect, use, transmit or store personal data, monitor the behavior of EU data subjects, GDPR applies to your processing and holding the personal data, regardless of your company’s location.
What are the key differences between the GDPR and the prior data privacy directive in the EU?
Although the key principles of data privacy still hold true to the previous directive, here is a high-level summary of the enhancements and other changes:
Increased Territorial Scope (extra-territorial applicability)
GDPR will apply to the processing of personal data by controllers and processors in the EU, regardless of whether the processing takes place in the EU or not. The GDPR will also apply to the processing of personal data of data subjects in the EU by a controller or processor not established in the EU, where the activities relate to: offering goods or services to EU citizens (irrespective of whether payment is required) and the monitoring of behavior that takes place within the EU.
Enhanced Penalties
Under GDPR, organizations in breach of GDPR can be fined up to 4 percent of annual global turnover or €20 million (whichever is greater). This is the maximum fine that can be imposed for the most serious infringements (e.g., not having sufficient customer consent to process data or violating the core of Privacy by Design concepts).
There is a tiered approach to fines (e.g., a company can be fined 2 percent for not having their records in order (Article 28), not notifying the supervising authority and data subject about a breach or not conducting impact assessment). It is important to note that these rules apply to both controllers and processors — meaning cloud environments will not be exempt from GDPR enforcement.
Robust Consent Requirements
The conditions for consent have been strengthened, and companies will no longer be able to use long illegible terms and conditions full of legalese, as the request for consent must be given in an intelligible and easily accessible form, with the purpose for data processing attached to that consent.
Consent must be clear and distinguishable from other matters and provided in an intelligible and easily accessible form, using clear and plain language. It must be as easy to withdraw consent as it is to give it.
Breach Notification
Under the GDPR, breach notification will become mandatory in all member states where a data breach is likely to “result in a risk for the rights and freedoms of individuals”. This must be done within 72 hours of first having become aware of the breach. Data processors will also be required to notify their customers, the controllers, “without undue delay” after first becoming aware of a data breach.
Right to Access
Data subjects have the right to obtain from the data controller confirmation as to whether or not personal data concerning them is being processed, where and for what purpose. Further, the controller shall provide a copy of the personal data, free of charge, in an electronic format. This change is a dramatic shift to data transparency and empowerment of data subjects.
Right to be Forgotten (data erasure)
A data subject has the right (subject to certain exceptions) to have the data controller erase his/her personal data, cease further dissemination of the data and potentially have third parties halt processing of the data.
Data Portability
Under GDPR, a data subject has the right to receive the personal data concerning them, which they have previously provided in a ‘commonly used and machine-readable format’ and have the right to transmit that data to another controller.
Privacy by Design
Privacy by design, as a concept, has existed for years, but it is only just becoming part of a legal requirement with the GDPR. At its core, privacy by design calls for the inclusion of data protection from the onset of the designing of systems.
More specifically, companies need to implement appropriate technical and organizational measures to effectively meet the requirements of GDPR and protect the rights of data subjects. Controllers must hold and process only the data absolutely necessary for the completion of its duties (data minimization), as well as limiting the access to personal data to those needing to act out the processing.
Data Protection Officers (DPO)
A DPO appointment will be mandatory only for those controllers and processors whose core activities consist of processing operations which require regular and systematic monitoring of data subjects on a large scale (e.g., Facebook, Google, etc.) or of special categories of data or data relating to criminal convictions and offences.
What counts as personal data under the GDPR?
The GDPR applies to ‘personal data,’ meaning any information relating to an identifiable person who can be directly or indirectly identified in particular by reference to an identifier.
This definition provides for a wide range of personal identifiers to constitute personal data, including name, identification number, location data or online identifier, reflecting changes in technology and the way organizations collect information about people. Personal data that has been pseudonymized (e.g., key-coded) can fall within the scope of the GDPR depending on how difficult it is to attribute the pseudonym to a particular individual.
When can people access the data stored about them?
People can ask for access at “reasonable intervals,” and generally a response is required within one month. The GDPR requires transparency in how data is collected, what is done with it and how it is processed.
What is the “right to be forgotten”?
Individuals have the right to have their personal data deleted under certain circumstances. This is known as the ‘right to be forgotten.’ An individual has the right to have to request that his/her personal data be erased, to cease further dissemination of the data and potentially have third parties halt processing of the data.
When does the “right to be forgotten” apply?
The points below are subject to legal interpretation, but as outlined by the ICO, the “right to be forgotten” generally applies when:
- The personal data is no longer necessary for the purpose which you originally collected or processed it for
- You are relying on consent as your lawful basis for holding the data, and the individual withdraws their consent
- You are relying on legitimate interests as your basis for processing, the individual objects to the processing of their data, and there is no overriding legitimate interest to continue this processing
- You are processing the personal data for direct marketing purposes and the individual objects to that processing
- You have processed the personal data unlawfully (i.e., in breach of the lawfulness requirement of the first principle)
- You have to do it to comply with a legal obligation
What if they want to move their data elsewhere?
Under the GDPR, individuals have the right to obtain, reuse, move, copy or transfer personal data easily from one IT environment to another in a safe and secure way, without hindrance to usability.
What are the data security requirements under the GDPR?
The GDPR requires personal data be processed to protect against unauthorized or unlawful processing and against accidental loss, destruction or damage. It requires use of appropriate technical or organizational measures, which in many instances require the use of network security.
What if a data breach occurs?
If a data breach were to occur, it is the responsibility of the data controller and/or processor to inform the relevant data protection authority of certain data breaches within 72 hours of becoming aware of it.
If the breach is likely to result in a high risk of adversely affecting individuals’ rights and freedoms, the data processor and/or controller must also inform those individuals without undue delay.
What about Brexit?
The United Kingdom (UK) is leaving the EU. But because the UK government only triggered Article 50 in March 2017, which sets in motion the act of leaving the EU within a two-year timeframe (though it could take longer), this means the GDPR will take effect before the legal consequences of Brexit. Organizations located in the UK must still comply and the GDPR applies to natural individuals who are citizens of the UK.
A new Data Protection Bill, put forward by the UK government in August 2017, essentially replicates the requirements of the GDPR into UK legislation, meaning those compliant with the GDPR should be compliant with the new UK data protection law.
By aligning with GDPR, the UK hopes to build an enhanced data protection mechanism that goes beyond the adequacy model the EU imposes on ‘third’ countries, allowing personal data to flow freely between the UK and EU.
Is the GDPR solvable with technology alone?
No. The GDPR requires a comprehensive approach to data privacy that includes sound policies, procedures, training and technology.
Isn’t GDPR just hype?
No. It is reality and by all indications this new EU regulation will be monitored and enforced by EU regulators. It must be taken especially seriously in light of recent revelations regarding the collection and use of personal data by various types of organizations.
Once GDPR is enforced, a flurry of breaches may be announced that will raise the profile of GDPR. Organizations will be under pressure to respond by getting the proper infrastructure in place. Fines for noncompliance could reach up to €20 million ($24 million USD) or 4 percent of annual global turnover.
SonicWall and the GDPR
SonicWall is working hard to ensure compliance with GDPR requirements. SonicWall takes information security seriously and has implemented policies and procedures for safeguarding personal data that is stored, processed and/or transferred by SonicWall.
These policies and procedures include, without limitation, physical and logical access restrictions, data classification, access rights, credentialing programs, record retention, data privacy, information security and the treatment of personal data and sensitive personal data throughout its lifecycle.
To learn more about how GDPR applies to SonicWall products and services, please read “How SonicWall Adheres to GDPR Requirements” and review the official SonicWall Privacy Statement.