Joomla! User Notes SQL Injection

Joomla! is a free and open source content management system (CMS) used for building websites and for publishing web content. It is estimated to be the second most used content management system on the Internet after WordPress.
An SQL injection vulnerability exists in the Joomla! com_users component due to insufficient input validation of the filter “category_id”. This component can be invoked by accessing the following URI.
/administrator/index.php?option=com_users&view=notes
The method getListQuery() in the com_users component gets called to create an SQL SELECT query to list all the user notes for the value passed in the HTTP request. One such key is category_id and the value of category_id gets used in the SQL query without proper validation. So a malicious user can craft a HTTP request with a value of category_id that modifies the constructed SQL query to perform operations that the programmer did not originally intend. Successful exploit can lead to sensitive information disclosure, tamper with existing data or execute administration operations on the database.
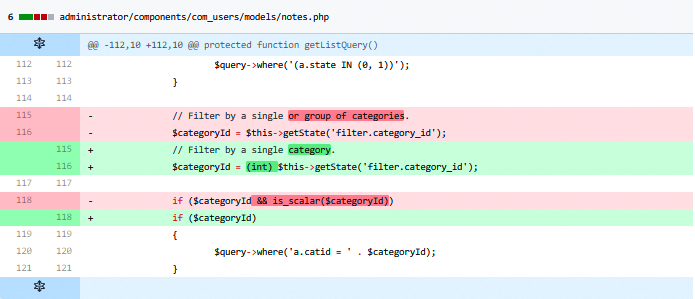
An example of the crafted HTTP request to the vulnerable server is given below:
POST /joomla/administrator/index.php?option=com_users&view=notes HTTP/1.1\r\n
Text data: filter%5Bcategory_id%5D=7+AND+ascii(substring((SELECT+concat(1,password,0x2F)+ from+#__users+limit+0,1), 2,1))>31&
This can be mitigated by upgrading to the latest non-vulnerable version of the software.
SonicWALL Threat Research Team have the following signatures to protect their customers.
IPS 13316: Joomla! User Notes SQL Injection
WAF 1001: Blind SQL Injection Attack Variant 5
WAF 9002: Blind SQL Injection Attack Variant 1
WAF 9004: Blind SQL Injection Attack Variant 3
WAF 9006: SQL Injection Attack 2
WAF 9045: SQL Injection Attack 11
WAF 9002: Blind SQL Injection Attack Variant 1
WAF 9004: Blind SQL Injection Attack Variant 3
WAF 9006: SQL Injection Attack 2
WAF 9045: SQL Injection Attack 11





