This Android Monero miner demands admin privileges
Description
Crypto miners have been rampant on Android devices for the last few months. Compared to ransomwares, crypto miners are believed to be more lucrative in terms of the quick revenue they generate. Sonicwall Capture Labs Threats Research Team observed yet another malicious crypto Monero miner threat for Android devices that mines Monero coins in the background without the victim’s knowledge.
The app uses the following permissions:
- Internet
- Read phone state
- Access network state
- Receive boot completed
- Wake lock
- Write external storage
The app does not show an icon in the app drawer upon installation. Once the app starts it requests for device administrator privileges:


If the privileges are not granted, the malware repeatedly pops the screen requesting admin access until they are granted:

Upon getting the desired privileges the app starts mining Monero coins in the background. No indications of this activity are shown to the victim, meanwhile CPU usage almost reaches 100% utilization:

The miner components can be seen in the lib folder:

Smartphones typically heat up if CPU intensive tasks are continuously performed for a longer duration. One such CPU intensive task is mining, recently we observed a number of Android malware that use the processing power of the infected device for mining cryptocurrency. We have covered miner malware for Android in our blogs in the recent past:
- Android mining trojan so aggressive it can break your device (Dec 22, 2017)
- Sudden surge in Android miner malware observed (Jan 8, 2018)
This malware is difficult to get rid of if administrator rights are granted to it upon infection:

We found the below hardcoded mining addresses in the samples we analyzed:
- 49Bq2bFsvJFAe11SgAZQZjZRn6rE2CXHz4tkoomgx4pZhkJVSUmUHT4ixRWdGX8z2cgJeftiyTEK1U1DW7mEZS8E4dF5hkn
- 43QGgipcHvNLBX3nunZLwVQpF6VbobmGcQKzXzQ5xMfJgzfRBzfXcJHX1tUHcKPm9bcjubrzKqTm69JbQSL4B3f6E3mNCbU
More details for the above wallets can be seen on supportxmr.com, few snippets are as below:
-
- 49Bq2bFsvJFAe11SgAZQZjZRn6rE2CXHz4tkoomgx4pZhkJVSUmUHT4ixRWdGX8z2cgJeftiyTEK1U1DW7mEZS8E4dF5hkn

- 49Bq2bFsvJFAe11SgAZQZjZRn6rE2CXHz4tkoomgx4pZhkJVSUmUHT4ixRWdGX8z2cgJeftiyTEK1U1DW7mEZS8E4dF5hkn
- 43QGgipcHvNLBX3nunZLwVQpF6VbobmGcQKzXzQ5xMfJgzfRBzfXcJHX1tUHcKPm9bcjubrzKqTm69JbQSL4B3f6E3mNCbU

Currently Monero (XMR) trades for $167.05 per XMR as of April 10, 2018.
Any kind of malware on a mobile device is dangerous but miners are more so than others for a simple reason – they can break the device. Smartphones in today’s age compact a lot of technology in a small package, this does not leave enough room for it to cool down under heavy load. Crypto miners are dangerous for the same reason, they put a huge processing load on the device. Crypto miners with device admin privileges can potentially lock-out the user while mining coins until the phone breaks. We urge our readers to be vigilant while installing apps on their devices.
Sonicwall Capture Labs provides protection against this threat with the following signature:
- GAV: AndroidOS.Monerominer.MNR_2 (Trojan)
Following are MD5’s few samples from this threat:
- 1efa8e98f208a44a6f310c790e112b7e
- 5177d220030ddf813b5bb05928c86585
- 73415fbf16952894e0620b40766d9e2f
- ef161923c7a6f99d134467ca21e34410
- 530bd6c95c3a79c04f49880a44c348db
- a765d2829b80d812b321c663d8d8320e
- 642bef4824d549ac56520657a1868913
- a13126ed31b3a7982133ff57e6f9676d
- e24a0d6b17a9dbf0456bbf4bb93adb25
- a0f776e61cf4ddc55c28051583fbb28e
- ef161923c7a6f99d134467ca21e34410
- c18f39c4b09e542926d728195b88e418
- 659909c20269c630372eac4878e679ca
- fffb8d51838af6bb742e84b8b16239bb

 The numbers are alarming. The threats continue to grow. And it’s the reason I promise that SonicWall teams around the world are dedicated to ensure our customers are protected from today’s most malicious cyber threats — both known and unknown.
The numbers are alarming. The threats continue to grow. And it’s the reason I promise that SonicWall teams around the world are dedicated to ensure our customers are protected from today’s most malicious cyber threats — both known and unknown.





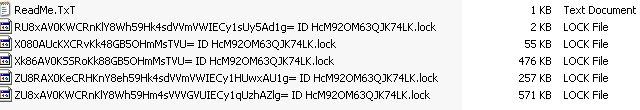
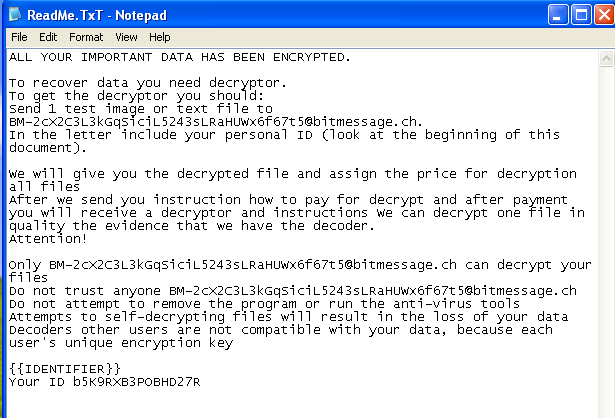


 The attacker can then submit a complex encryption key to encrypt the site’s content. This results to:
The attacker can then submit a complex encryption key to encrypt the site’s content. This results to:




