Node.js zlib Module DoS
Node.js is an open-source, cross-platform JavaScript run-time environment for executing JavaScript code server-side. A denial of service vulnerability exists in Node.js. When the zlib v1.2.9 component in Node.js handles the 8-bit Z_STREAM_ERROR error code, there is an logic error that ignored certain values, causing an unhandled exception. An attacker could cause denial of service by sending a certain crafted HTTP request via the WebSocket protocol. The affected version includes node.js before 4.8.5, 6.x before 6.11.5, and 8.x before 8.8.0.
zlib is a lossless compression library which is natively supported by Node.js. It can be called inside the code via a wrapper module:
const binding = process.binding('zlib');
The windowBit value in the zlib library could be assigned by a client request by sending the “server_max_window_bits=X” and “client_max_window_bits=X” values in the “Sec-WebSocket-Extensions” header.
Below is the logic of error exception handling in zlib. When the windowBit value is set to 8, it won’t fall into any of the conditions of throwing an Z_STREAM_ERROR and leads to an unhandled exception.

In order to exploit this DoS vulnerability, an attack could simply send a HTTP request and set the windowBit to 8:
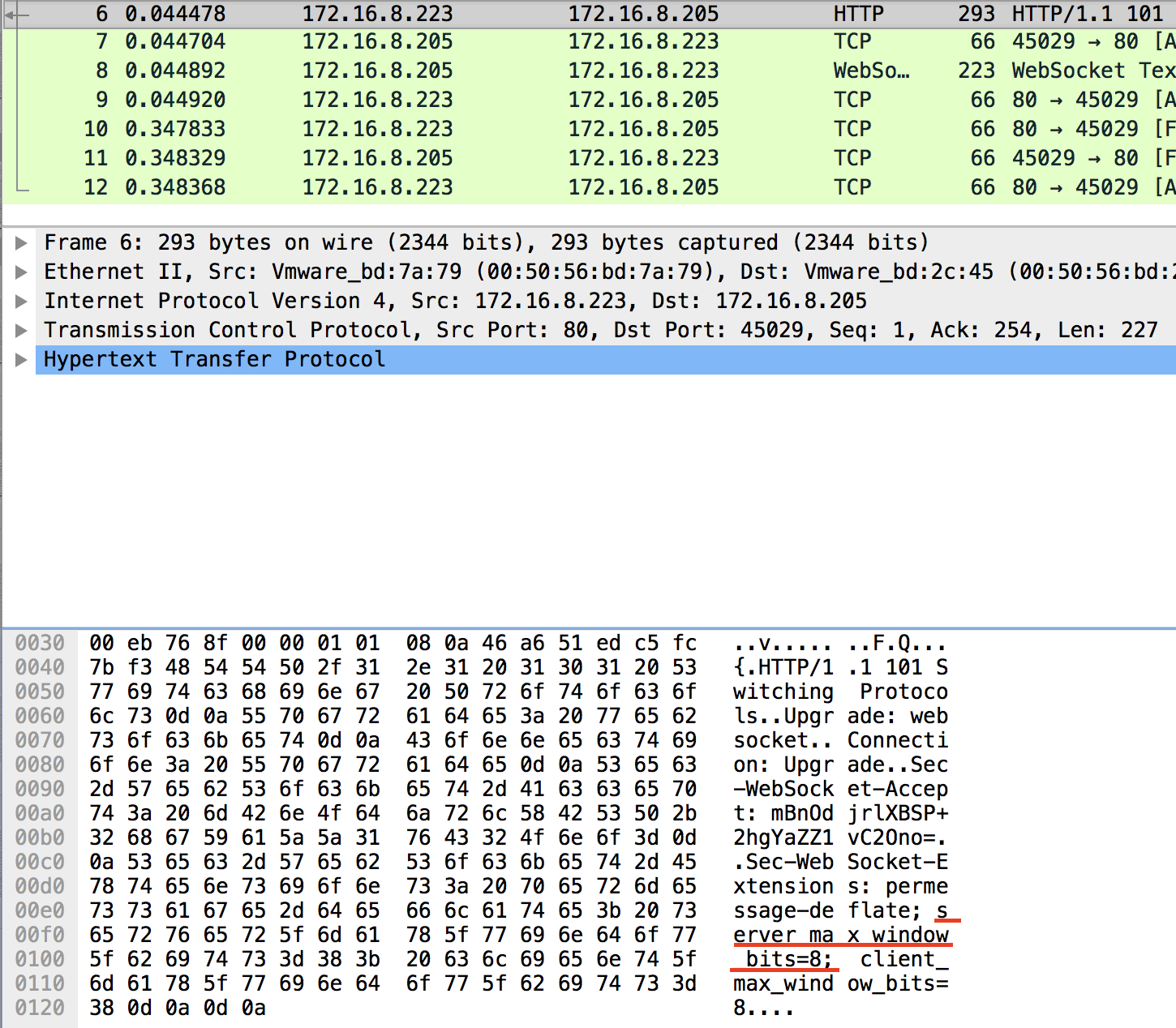
SonicWall Capture Labs Threat Research team has developed the following signature to identify and stop the attacks:
- IPS 13169: Node.js zlib Module DoS
- WAF 1674: Node.js zlib Module DoS




