Android Marcher update adds anti-emulation feature
Android malware that target banking apps have plagued the Android ecosystem for a while, Marcher and BankBot being one of the most active families. SonicWall Threats Research team observed a new version of the popular banker for Android – Marcher. This new version brings with it a new way to avoid detection by security analysts and automated sandbox engines.
This new version of Marcher attempts to hide critical strings by obfuscating them in a bid to evade automated malware analysis engines and make it difficult to analyze the sample. One of the class files in the apk contains a heap of strings, however every character is separated by **[three letters]** for example **izn** or **iCp** as shown below for two apk’s: 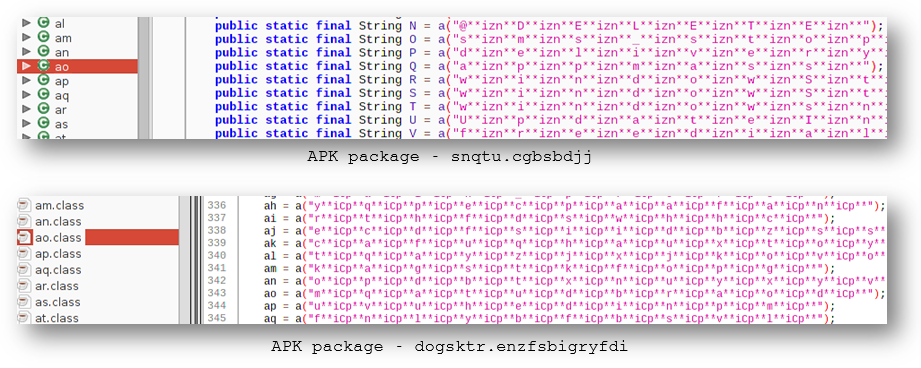
The code uses references to these obfuscated strings instead of using actual strings in the code. We re-created all the class files by substituting the proper strings thereby giving a readable code. One such instance is highlighted below: 
What sets this Marcher variant different from older variants is the new emulation check. This new variant stops execution as soon as it discovers that it is being run on an emulated environment. The anti-emulation check can be seen in the code as highlighted below: 
There are few data elements that are unique to an emulated Android environment. Below are few checks that the malware does and the default values for an emulator:
- Build.FINGERPRINT.startsWith “generic” or “unknown”
- Build.MODEL.contains “google_sdk” or “Emulator” or “Android SDK built for x86”
- Build.MANUFACTURER.contains “Genymotion”
- Build.BRAND.startsWith “generic”
- Build.DEVICE.startsWith “generic”
- Build.HARDWARE.contains “golfdish” or “ranchu”
- Build.PRODUCT equals “google_sdk” or “sdk_x86” or “vbox86p” or “generic”
- IMEI = 000000000000000, 012345678912345 or 004999010640000
- IMSI = 012345678912345
- NetworkOperatorName is empty
- SimOperatorName is empty
The app contains a list of targeted banking apps, if any of these apps are opened then a different login screen is displayed. Credentials entered by the victim on these fake screens are captured and sent to the attacker. The app also checks the device for presence of a number of anti-virus apps installed on the device. Code for both the above scenarios can be seen below: 
Overall these new Marcher samples indicate once more how malware writers constantly strive to bring new methods that innovate and evolve malware.
SonicWALL provides protection against multiple versions of this threat via the following signatures:
- GAV: AndroidOS.Marcher.RN (Trojan)
- GAV: AndroidOS.Marcher.VR (Trojan)
Samples analyzed for this blog:
- MD5: 22a4e3872ab51eb9f231ddc9814a51fb Package: gnpwibfapfjtdr.orvcpqiilijrbih
- MD5: 18a1562f769f0790d54cea97f050cbab Package: snqtu.cgbsbdjj
- MD5: 68ce40e9bdb43b900bf3cb1697b37e29 Package: etcqlnzwauf.hflivryhdnjb
We observed the following hardcoded attacker domains in the malicious apk’s that we analyzed:
- internetservicees.be
- music-streams.at
- autohauss.at
- internetservicees.ch
- internetservicees.at
- chucknorris.at
- l33tchuck.at
- chucksfactory.at
- engesappies.at
- 2A2032D36694D3B80E6E5F4B5E8D9E0A.ag
- 2a2032d36694d3b80e6e5f4b5e8d9e0a.am
- 726C6317C7004C35DD3204D72ED59DCC.sg
- readingift.at
- bendecker.at
- provincest.at
Complete list of targeted banking apps:
- ar.com.santander.rio.mbanking
- at.bawag.mbanking
- at.easybank.mbanking
- at.spardat.netbanking
- at.volksbank.volksbankmobile
- biz.mobinex.android.apps.cep_sifrematik
- br.com.bb.android
- cl.santander.smartphone
- co.com.bbva.mb
- com.akbank.android.apps.akbank_direkt
- com.akbank.android.apps.akbank_direkt_tablet
- com.akbank.softotp
- com.bancodebogota.bancamovil
- com.bancomer.mbanking
- com.bankaustria.android.olb
- com.bapro.movil
- com.barclays.android.barclaysmobilebanking
- com.bbva.nxt_argentina
- com.bbva.nxt_peru
- com.bcp.bank.bcp
- com.citibanamex.banamexmobile
- com.db.mm.deutschebank
- com.finansbank.mobile.cepsube
- com.garanti.cepbank
- com.garanti.cepsubesi
- com.grppl.android.shell.BOS
- com.grppl.android.shell.CMBlloydsTSB73
- com.grppl.android.shell.halifax
- com.grupoavalav1.bancamovil
- com.htsu.hsbcpersonalbanking
- com.ingbanktr.ingmobil
- com.ing.diba.mbbr2
- com.intertech.mobilemoneytransfer.activity
- com.isis_papyrus.raiffeisen_pay_eyewdg
- com.itau
- com.mosync.app_Banco_Galicia
- com.pozitron.iscep
- com.rbs.mobile.android.natwest
- com.rbs.mobile.android.rbs
- com.rbs.mobile.android.ubr
- com.santander.app
- com.starfinanz.mobile.android.dkbpushtan
- com.starfinanz.smob.android.sbanking
- com.starfinanz.smob.android.sfinanzstatus
- com.teb
- com.tmob.denizbank
- com.tmobtech.halkbank
- com.todo1.davivienda.mobileapp
- com.todo1.mobile
- com.vakifbank.mobile
- com.ykb.android
- com.ykb.android.mobilonay
- com.ykb.androidtablet
- com.ziraat.ziraatmobil
- de.adesso.mobile.android.gadfints
- de.comdirect.android
- de.commerzbanking.mobil
- de.consorsbank
- de.dkb.portalapp
- de.fiducia.smartphone.android.banking.vr
- de.ing_diba.kontostand
- de.postbank.finanzassistent
- mobile.santander.de
- mx.bancosantander.supermovil
- org.banelco
- org.microemu.android.model.common.VTUserApplicationLINKMB
- pe.com.interbank.mobilebanking
- se.accumulate.me.core.androidclient.csb
- se.accumulate.me.core.androidclient.occidente
- tr.com.sekerbilisim.mbank
- uk.co.santander.santanderUK
- uk.co.tsb.mobilebank
Complete list of hardcoded anti-virus apps that are checked for:
- avg.antivirus
- com.anhlt.antiviruspro
- com.drweb
- com.antivirus
- com.antivirus.tablet
- com.avast.android.mobilesecurity
- com.avira.android
- com.bitdefender.antivirus
- com.cleanmaster.boost
- com.cleanmaster.mguard
- com.cleanmaster.mguard_x8
- com.cleanmaster.sdk
- com.cleanmaster.security
- com.dianxinos.optimizer.duplay
- com.duapps.antivirus
- com.eset.ems2.gp
- com.eset.ems.gp
- com.ikarus.mobile.security
- com.kms.free
- com.netqin.antivirus
- com.nqmobile.antivirus20
- com.nqmobile.antivirus20.clarobr
- com.piriform.ccleaner
- com.psafe.msuite
- com.qihoo.security
- com.qihoo.security.lite
- com.referplish.VirusRemovalForAndroid
- com.sonyericsson.mtp.extension.factoryreset
- com.symantec.mobilesecurity
- com.thegoldengoodapps.phone_cleaning_virus_free.cleaner.booster
- com.trustlook.antivirus
- com.womboidsystems.antivirus.security.android
- com.zrgiu.antivirus
- droiddudes.best.anitvirus
- oem.antivirus





