Legitimate software website was seen distributing malware (Jul 22, 2016)
The Sonicwall Threat Research team has received reports of a trojan bundled with a legitimate remote desktop tool. Cybercriminals found a way to slip Lurk Trojan with Ammyy Admin program and distribute this malicious application via software downloads through the company’s official website. This is not the first time the Ammyy Admin website has been comprised. In the past year, it has been reported to distribute different malware families through malware-laced copies of their installers hosted on the company’s website.
Infection Cycle:
The infected copy is an NSIS packaged installer that upon execution will extract and execute the legitimate Ammyy admin installer along with the Trojan installer.
Figure 1: NSIS packaged installer extracts the legimitate and malicious programs

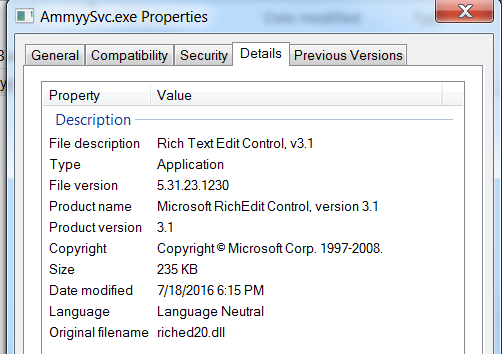
The Trojan installer AmmyySvc.exe has file properties that resembles a legitimate program:
Figure 2: AmmyySvc.exe file properties
Upon execution of the malicious exe, it drops a DLL file in the following directory:
- %temp%/19B.tmp
This file also has legitimate-looking file properties:
Figure 3: 19B.tmp DLL file properties

It also lists the following fake export functions:
Figure 4: Fake DLL Export functions

When in reality, none of these export functions are used by the program, and it is registered through DllRegisterServer with regsvr32.exe.
Figure 5: AmmyySvc.exe spawns regsvr32.exe to register the malicious DLL component

The Trojan checks the basic settings of the infected systems and scours the registry to possibly understand what methods can be used to gain access, if the machine is part of a network or to learn how to circumvent security settings:
Figure 6: AmmyySvc.exe checks for Internet Settings and System Policies

Figure 7: AmmyySvc.exe checks for Internet feature control settings

It also gathers information such as the computer name and web browsing history information including URLs visited, cookies created and files that were downloaded in the cache.
Figure 8: Lurk Trojan reads the victim machine’s computer name

Figure 9: Lurk Trojan checks the victim machine’s web history

Figure 10: Lurk Trojan checks the victim machine’s cookies

It also tried to make the following connections to a remote server but it was already taken down at the time of our analysis:
Figure 11: Lurk Trojan connects to bandgap75r.com

This example of a watering hole attack, where malware authors target unsuspecting visitors to the Ammyy Admin official website, is a very effective way to distribute malicious software and infect their target. Victims will likely trust installers that were downloaded from a presumably safe source. Ammyy Admin has since cleaned up their website and no longer distributes the malicious installer, but given that their website has previously been compromised multiple times, we urge our users to be doubly cautious when downloading and executing installer from their website.
Dell SonicWALL Gateway AntiVirus provides protection against this threat with the following signatures:
- GAV: Lurk.A_2 (Trojan)
- GAV: Lurk.A_3 (Trojan)




