Microsoft Silverlight Remote Code Execution Vulnerability – CVE-2016-0034 (Mar 18,2016)
Microsoft Silverlight is a powerful development tool for creating interactive user experiences for Web and mobile applications. Silverlight is a free plug-in, powered by the .NET framework and compatible with multiple browsers. Microsoft Silverlight 5 before 5.1.41212.0 mishandles negative offsets during decoding, which allows remote attackers to execute arbitrary code or cause a denial of service (object-header corruption) via a crafted web site, aka “Silverlight Runtime Remote Code Execution Vulnerability.”
The vulnerability is triggered when the System.Text.Decoder class tries to allocate buffer using value returned by GetChars() function. The attacker can override the GetChars function in a derived class to return a negative value.This leads to memory corruption.
To exploit this vulnerability an attacker could host a specially crafted Silverlight application on a website and entice the user to click it. Successful exploitation could lead to remote code execution in context of the logged in user.
The overridden GetChars function in the derived class looks like this

IE crashes when System.Text.Decoder class tries to allocate a negative buffer size.


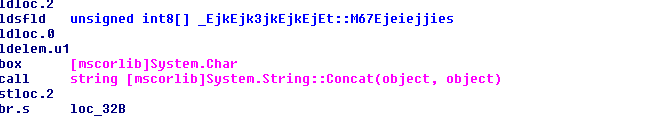
The exploit code is an obfuscated .net assembly. The decompiled and deobfuscated dll code looks like this


Demcompiled

Deobfuscated

The exploit code tries to decode a long byte array.

Attaching a debugger we see that the malicious dll sprays the memory with malicious code . We can also see some code that could tamper with registry.

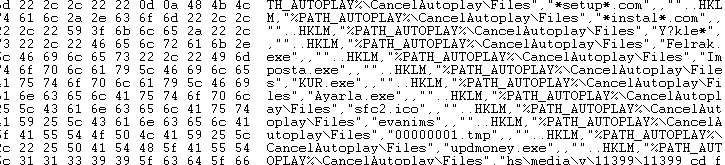
The graphical view of exploit code looks like this.

Dell SonicWALL Threat Research Team has researched this vulnerability and released following signature to protect their customers
- IPS 11388: Microsoft Silverlight Remote Code Execution (MS16-006)





