Buffer overflow vulnerability in glibc library (CVE-2015-7547)
Dell SonicWALL firewalls are not susceptible to the glibc buffer overflow vulnerability. The Dell SonicWALL Vulnerability Research team has created a signature that protects our customers from this attack and has already pushed the signature to Dell SonicWALL firewalls to protect infrastructure behind Dell SonicWALL firewalls that has active IPS subscription services.
This bug was discovered to exist in glibc versions greater than 2.9. It is one of the most widely used component of many applications including hardware device software. A successful exploitation can lead to malicious code execution, possibly leading to attackers taking control over the DNS server or to man-in-the-middle attacks.
Specifically, a function called ‘getaddrinfo()’ fails to properly allocate memory in certain situations which causes buffer overflow. This takes place in the client side resolver. glibc allocates 2048 bytes on the stack through ‘alloca()’ function to allocate response to a DNS query. If the response is greater than 2048 bytes, a new buffer is reserved on the heap. Due to some specific conditions, there becomes an inconsistency between the stack buffer and the heap buffer. This results in storing the large response(2048+ bytes) on stack buffer instead of heap buffer, thus causing a buffer overflow.
The following diagram portraits a scenario of how this bug can be exploited:
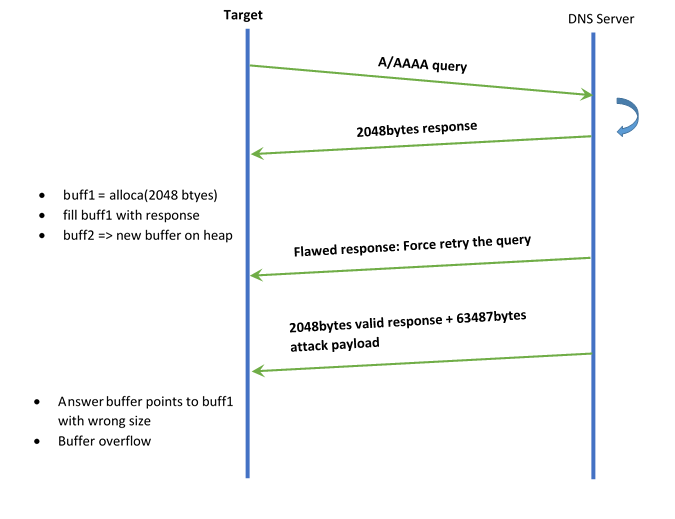
It is very easy to trigger this vulnerability; although, the exploitation has its challenges such as ASLR (address space layout randomization).
It is highly recommended that all vulnerable systems be patched immediately.
Affected versions:
- glibc 2.9+
Dell SonicWALL team has created the following signatures that protect customers from this attack:
- IPS 11465 : glibc getaddrinfo Function Buffer Overflow 1
- IPS 11467 : glibc getaddrinfo Function Buffer Overflow 2
- IPS 11470 : glibc getaddrinfo Function Buffer Overflow 3
- IPS 11480 : glibc getaddrinfo Function Buffer Overflow 4
- IPS 11481 : glibc getaddrinfo Function Buffer Overflow 5






