ServStart Backdoor Spotted in the Wild
The Dell SonicWALL Threats Research Team has recently encountered an example of the ServStart backdoor family. This malware was captured in the wild as a drive-by-download and although it seems to be an outdated family, it has some interesting features.
Infection Cycle

This sample of ServStart consists of a single file with two modes of execution. When launched directly as a standalone binary, it installs a copy of itself as a system service. After the malicious service is launched, it melts the original file in common fashion, utilizing cmd.exe to do the deletion: [C:Windowssystem32cmd.exe /c del c:windowstemp13FD80~1.EXE > nul]

When the threat is launched as a system service, it registers a mutex for itself, then spawns threads to communicate with two hardcoded hosts.

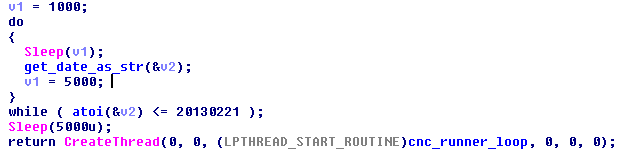
One host is specified with a hardcoded IP address while the other uses a static hostname. It is interesting to note that a date check is performed before the threat will attempt to connect to the hostname. It’s even more interesting that the date is in 2013 even though this sample appears to have been compiled in June 2014.
Once the malicious service is active, the host operating system version and CPU speed are collected to send with the callback to the attacker’s server.

While both hosts appear to be online, they no longer seem to be accepting the callback communications, and send only TCP RST packets in response.
It’s unclear if this is an attempt to hinder analysis via disassembly or decompilation or simply a side effect of implementation on either side, but the way the hardcoded hostname is constructed is a bit unique. A quick read of the disassembled or decompiled code would suggest that the hostname is “vip.3252300.com”. However, due to the way the variables are actually arranged in memory, the host turns out to be “vip.1325213100.com”.

Indicators of Compromise
In order to persist across reboots, the malware installs itself as a system service that starts at boot time.
The following mutex was seen during analysis and is used to prevent unnecessary reinfection and to manage execution threads:
- BaseNamedObjectsWindows Dfsr My Teast 3.0
- HKLMSYSTEMControlSet001ServicesWindows Dfsr My Teast 3.0
- C:Windowssystem32vmware-vmx.exe
Summary
Overall, the purpose of this malware is to gain control of a target machine. Although the command and control servers are not currently responding to the malware’s communications, the attackers may be able to reactivate the servers or update the hostname’s dns and gain control of any active infections at any time. Dell SonicWall Gateway Anti-Virus provides protection against this threat with the following signature:
- GAV: ServStart.A_4




