Angler Exploit Kit drive by attack (June 25, 2014)
The Dell SonicWALL Threats Research team analyzed a drive by attack involving the Angler Cyber-crime exploit kit which leads to the download of additional malware on the target system upon successful exploit run. The malware in this case is from a Backdoor Trojan family Caphaw.
The Angler Exploit Kit is yet another web based Cyber-crime exploit kit that emerged late last year with exploit payloads targeting Adobe Flash and Java vulnerabilities. The author added exploit payloads for Microsoft Silverlight 5 remote code execution vulnerability within a month which significantly increased the infection rates for this Exploit Kit. It appears to be the Exploit Kit of choice for Reveton Ransomware gang that was previously using Cool Exploit Kit, a premium Blackhole Exploit Kit version that became extinct after the arrest of the author. Like many other web-based exploit kits, Angler Exploit Kit utilizes browser plugin detectors to identify target system environment which includes versions of browser, Java, Adobe Flash, Silverlight etc. The targeted exploit payload is then served based on the identified vulnerable application leading to malware infection.
The Angler exploit kit follows the standard exploit flow cycle where users are redirected from compromised website to the exploit kit hosting site also known as landing page. This kit uses 3 levels of redirection before redirecting user to landing page. JavaScript code that generates first and second redirection URL, uses compromised host’s name to generate redirection URL. It also creates a cookie with key as “google_api” and value as “1”. The landing page consist of highly obfuscated JavaScript code to evade AV detection.

Figure 1: Obfuscated code stored in variables
Angler Exploit Kit Landing Page infection cycle
Landing page contains highly obfuscated JavaScript code segregated across multiple HTML span tags, followed by JavaScript code used for deobfuscation. Below is the function that is responsible for deobfuscation:
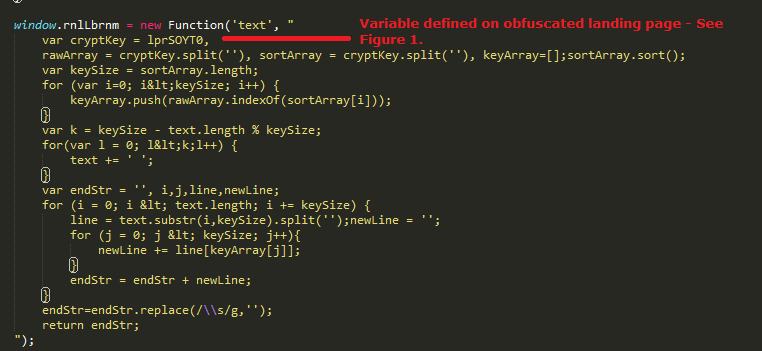
Figure 2: Deobfuscation function
- The first chunk of deobfuscated code checks for presence of the following driver files which belongs to Antivirus vendors Kaspersky and TrendMicro:
- c:\Windows\System32\drivers\kl1.sys
- c:\windows\system32\drivers\tmactmon.sys
- c:\windows\system32\drivers\tmcomm.sys
- c:\windows\system32\drivers\tmevtmgr.sys
- c:\windows\system32\drivers\TMEBC32.sys
- c:\windows\system32\drivers\tmeext.sys
- c:\windows\system32\drivers\tmnciesc.sys
- c:\windows\system32\drivers\tmtdi.sys
- It then deobfuscates next code chunk that checks for Silverlight version on the system. If vulnerable, it will generate a URL for the exploit payload that gets executed on the target system. The exploit payload being served by this instance was for CVE-2013-0074 – Silverlight Double Dereference Vulnerability
- If Silverlight version is not vulnerable then it performs similar version checks for Adobe Flash player and Java plugins respectively, serving exploit payloads if the installed version is vulnerable.
- Upon successful exploitation, it will download and install a Backdoor Trojan from Caphaw malware family on the target system.
It utilizes the following function leveraging ActiveXObject to check for above files:

Figure 3: Checking for AV driver files
If any of these files are present on the target system, it will stop the exploit cycle and redirect the user to a predetermined URL.

Figure 4: Check for vulnerable plugin versions on the system

Figure 5: Variables used for marking vulnerable plugins

Figure 6: Generating Exploit request based on identified environment (JAVA in the case above)
SonicWALL Gateway AntiVirus provides protection against this threat via the following signature:
- GAV: Angler.EKI (Exploit)
- GAV: Angler.EKR (Exploit)
- GAV: Angler.EKR_2 (Exploit)
- GAV: Angler.EKLP (Exploit)
- GAV: Malformed.Flash.OT (Exploit)
- GAV: Malformed.Java.OT (Exploit)
- GAV: Caphaw.AK (Trojan)
- GAV: Caphaw.AMX (Trojan)



