CVE-2013-3893 exploit actively serving malware (September 26, 2013)
Dell SonicWall Threats research team found a malicious site that exploits Microsoft Windows IE Vulnerability (CVE-2013-3893) to serve the attack payload onto the victims machine. More information about the actual vulnerability can be found on a Sonicalert covering the same attack case.
Infection Cycle:
The following steps illustrate the infection cycle:

Upon successful exploitation an encrypted file pretending to be an image logo.jpg is downloaded on the system. The extension of this file is misleading as it is actually a malicious Windows Executable XORed with 0x95 key as shown below:
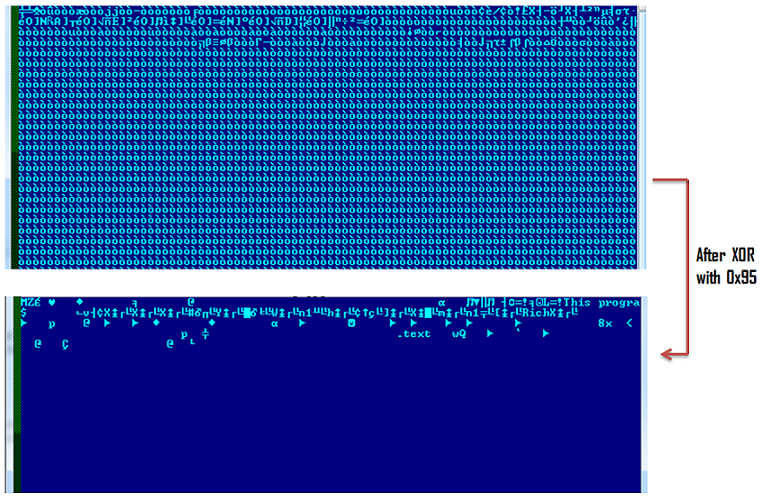
The malware executable also ensures that it is named as “runrun.exe” before it infects the system, otherwise it terminates. The following screenshot shows the name check function:

The Trojan adds the following key to the Windows registry to enable startup after reboot:
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun IEXPLORE “%Temp%runrun.exe””
The Trojan adds the following mutex on the system to mark its presence:
- ;A>6gi3lW
We observed the Trojan attempting to connect to login.momoshop.org via SSL but we did not see any further network activity from the server side. We also observed the following hardcoded IP in the code, the server appears to be down at the time of writing this blog.

Dell SonicWALL Gateway AntiVirus provides protection against these threats with the following signature:
- GAV: Unruy.JPG (Trojan)
- GAV: Unruy.JPX (Trojan)



