Android Pincer Trojan equipped with data stealing and anti-analysis modules (June 7, 2013)
Dell SonicWALL Threats Research Team received reports of Pincer Android Malware that can execute a host of commands from the Command and Control (C&C) once it infects a device. Apart from the commands that it can execute, one interesting feature about this malware is its capability to detect if it is being run in an emulator. Anti-analysis tricks are a commonplace in Windows Malware but not so much in its Android/Mobile counterpart.
Infection Cycle
We analyzed a number of samples for Pincer but observed two variants, one was installed on the system as Certificate and the other as Mobile Security.

Core functionalities in both these variants are the same with just minor differences in the two. The following permissions are requested during installation:
- Internet
- Send_SMS
- Read_Logs
- Call_Phone
- Receive_SMS
- Call_Privileged
- Read_Phone_State
- Modify_Phone_State
- Receive_Boot_Completed
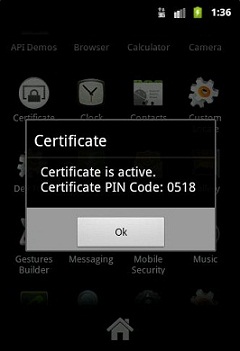
Upon execution of Certificate app the following was displayed indicating that the certificate is now active on the device, the Mobile Security app crashed during our analysis session.
Once executed, the apps send device related information to their respective C&C sources:
- C&C for Certificate app: 198.211.118.115:9081/Xq0jzoPa/g_L8jNgO.php and the number +447937xxxxxx
- C&C for Mobile Security app: img-cache.com/android_panel/gate.php and the number +447937xxxxxx
The following information about the device is sent to the C&C:
- Device Model
- Device Serial number
- Carrier for the device
- OS Version
- Phone Number
- Whether the device is rooted or not
The attacker can send the following commands via SMS in the format command : [command_code] to be executed:
- start_sms_forwarding
- start_call_blocking
- stop_sms_forwarding
- stop_call_blocking
- send_sms
- execute_ussd
- simple_execute_ussd
- stop_program
- show_message
- delay_change
- ping
The above commands indicate that the Malware tries to gather sensitive information about the user via SMS and calls and transfers this data to the C&C.
Malwares trying to understand if they are being analyzed in a debugging environment has been an old trick seen in Windows Malware, but observing the same being done for Android Malware is very rare. The Pincer samples we analyzed try to identify if they are being run in an Android Emulator, which is one of the most basic tools used for Android Malware Analysis. The Malware tries to match the following:
- Network Operator = Android
- Device Id = 000000000000000
- Line Number = 15555215554
- Android OS Build Model = sdk and generic
These are default values for an Android Emulator, meaning that this is a good way to identify if the Malware is being run inside an Android Emulator. Even though it is possible to change these values, the fact that the change is not so straightforward to make gives the Malware enough reason to have this check in place. We can expect more Malwares to follow suit and employ this trick in future.
Dell SonicWALL Gateway AntiVirus provides protection against these threats with the following signatures:
- GAV: AndroidOS.Pincer.CR (Trojan)
- GAV: AndroidOS.Pincer.MS (Trojan)




