Zeus P2P variant served via spammed Blackhole exploit links (Mar 2, 2012)
SonicWALL UTM Research team observed reports of multiple spam campaigns leading to Blackhole exploit kit infected websites. The most recent campaign involved emails pretending to be from Better Business Bureau, warning the user of a customer complaint against them and contains a link to the alleged complaint report. Another related spam campaign involved e-mails pretending to be from Intuit Inc. customer service, informing the user of a software order purchase information and contains a link to view the Order information.
SonicWALL has received more than 1000 copies of e-mails from these campaigns in past few days. In both these campaigns, URL inside the message will lead the user to a compromised website running Blackhole exploit kit which also recently featured in a recent mass-defacement of wordpress based websites. The Blackhole exploit kit on these sites targets known Java VM vulnerabilities and upon successful exploitation will download and run a new Zeus variant with P2P capabilities.
Please note that in our test labs, machines running latest Java version 6 update 31 were not compromised. It is highly recommended for the users to keep their Java software updated.
The sample e-mail messages are shown below:


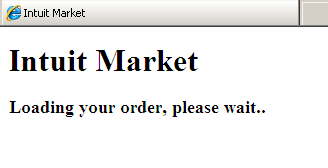
If the user clicks on the link then a temporary loading page will appear while the Blackhole exploit kit runs in the background:
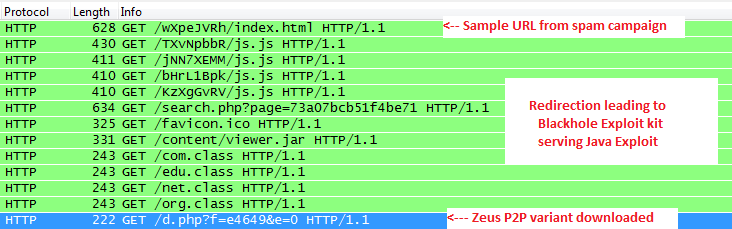
The downloaded Zeus P2P variant file looks like below:

It modifies the registry to ensure that the dropped Zeus P2P variant gets executed on system reboot and also modifies the Windows Firewall policy to open UDP Port 29833 and TCP port 26645 for P2P communication with the other bots as seen below:

SonicWALL Gateway AntiVirus provides proactive protection against this spam campaign via following signature:
- GAV: Zbot.gen_246 (Trojan)
- GAV: Blacole.gen (Trojan)




