Gumblar web attacks (May 19, 2009)
SonicWALL UTM Research team observed an increase in use of Gumblar drive-by attack on many popular websites.
Gumblar exploit is dynamically generated and varies not only from site to site, but also from page to page on the same site. It is also heavily obfuscated, making detection difficult. According to ScanSafe, Gumblar compromises are increasing – up 188% from last week. According to Sophos, Gumblar infections accounted for 42 percent of all infections found on websites last week.
This attack consists of two stages: the first stage of this exploit attempts to compromise legitimate websites by injecting malicious code into them. These infections occur mostly through stolen or weak FTP logins. The second stage of this exploit happens when users visit the website infected by Gumblar. It attempts to load exploits in PDF and SWF (flash) files, and through those exploits infect the users with a Trojan. This Trojan can monitor network traffic and steal FTP logins, as well as meddle with Google search results.
At least 3,000 websites have been compromised. United States Computer Emergency Readiness Team (US-CERT), issued an alert about it: here (link to US-CERT).
The original version of this exploit loaded malicious content from a site in china called Gumblar.cn, which inspired the name ‘Gumblar’. Recently ‘gumblar.cn’ was shutdown, and the exploit evolved to load malicious payload from ‘martuz.cn’. The new version also detects the Google Chrome browser and avoids loading the exploit in it.
SonicWALL Gateway Antivirus detects Gumblar exploit with GAV: Suspicious#gumblar (Trojan) signature. This signature has 24,500 hits so far.
Gumblar malicious script is injected between the HEAD and BODY tags as seen in this screenshots:
Obfuscated: 
Decoded: 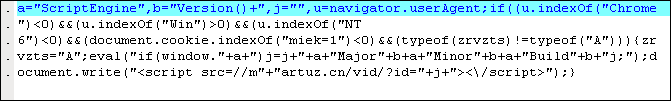
Below are the hits on our signature: 



