Mobef ransomware actively spreading in the wild
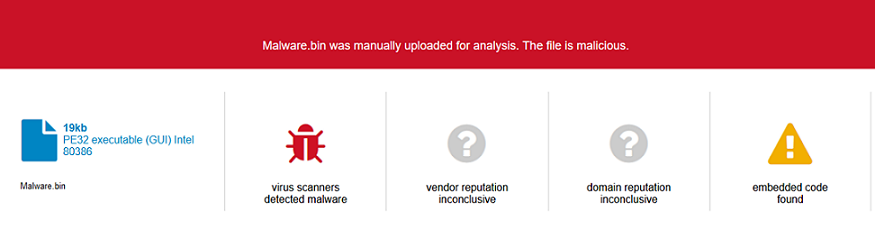
The SonicWall Capture Labs Threat Research team observed reports of a new variant family of Mobef ransomware actively spreading in the wild.

The Mobef ransomware encrypts the victim’s files with a strong encryption algorithm just for fun.
Infection Cycle:
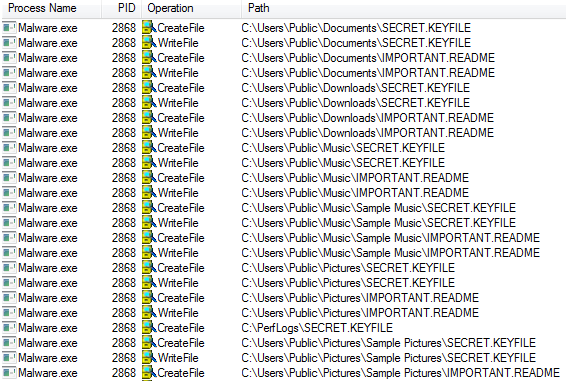
The ransomware adds the following files to the system:
- Malware.exe
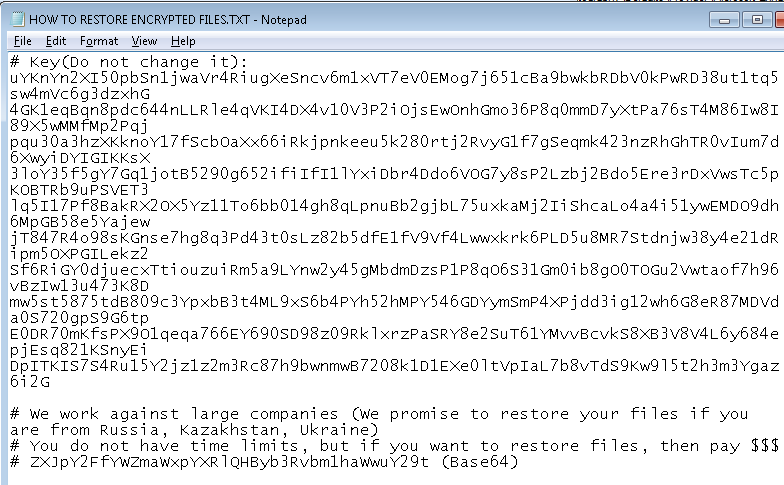
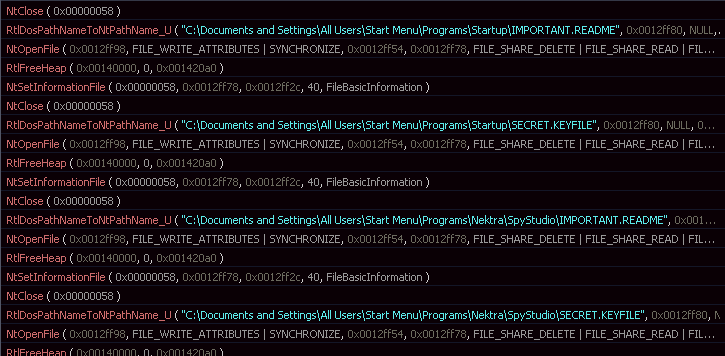
- %App.path%\ IMPORTANT.README
- %App.path%\ SECRET.KEYFILE
Once the computer is compromised, the ransomware runs the following commands:
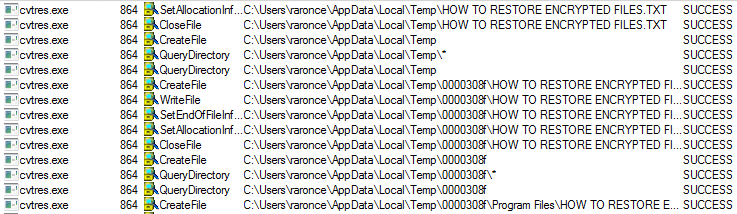
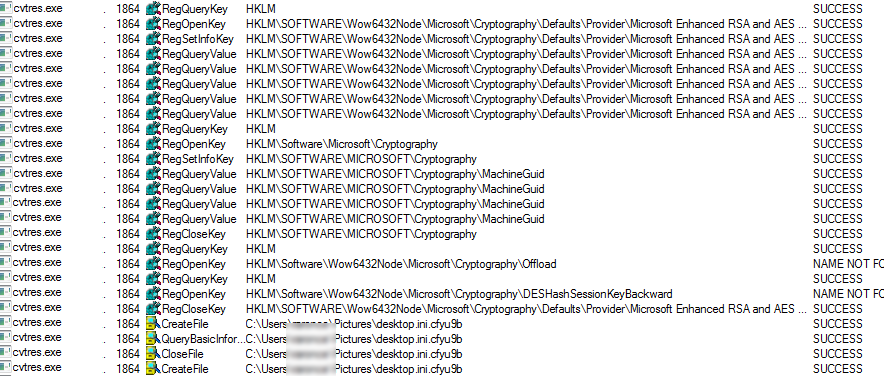
When Mobef is started it will create and assign a unique ID number to the victim then scan all local drives for data files to encrypt.
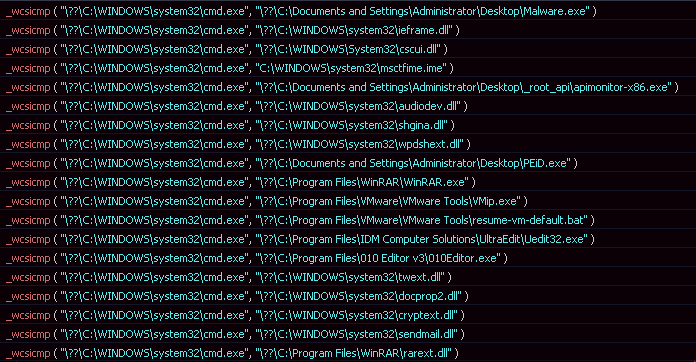
When encrypting files it will use the AES encryption algorithm and only encrypt those files that match the following extensions:
mp3, mp4, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, rwl, srf, srw, wb2, wpd, wps, xlk, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, xls, xlsb, xlsm, xlsx, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf.
Here is an example:
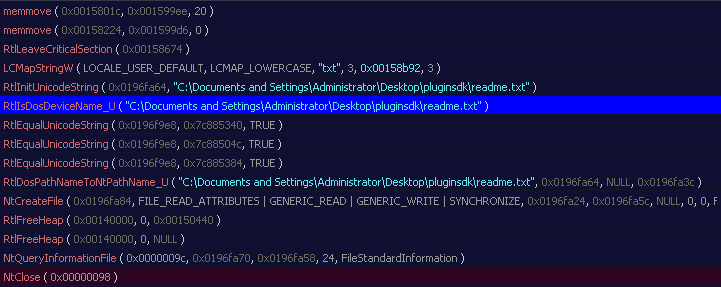
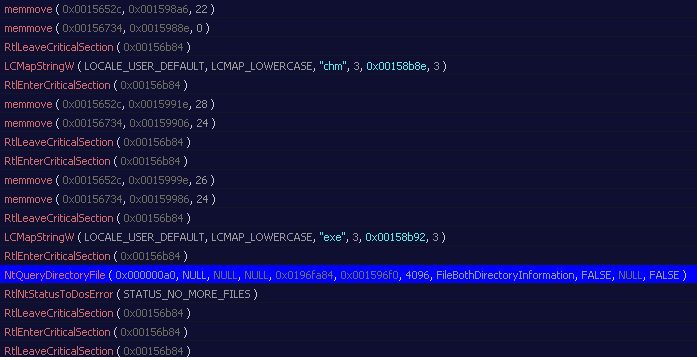
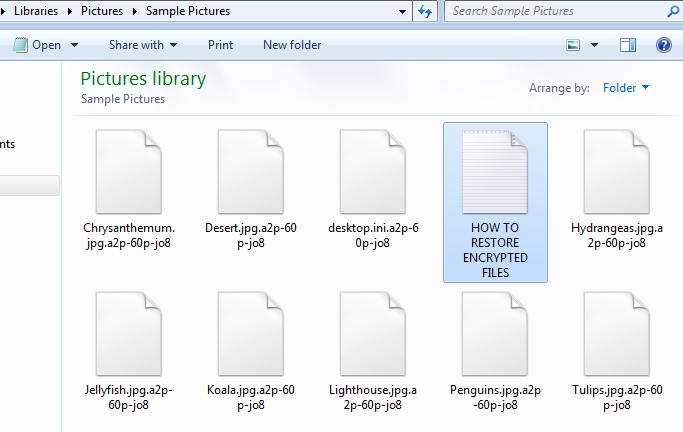
The ransomware encrypts all the without changing their extension filename.
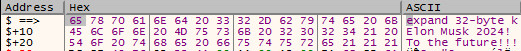
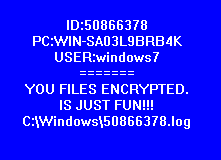
After encrypting all personal documents, the ransomware shows the following image containing a message reporting that the computer has been encrypted just for fun.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Mobef.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.