–Updated March 27, 2009—
SonicWALL UTM Research team saw a third wave of DHL Tracking number invoice spam with different attachment payloads starting late afternoon on March 26, 2009.
SonicWALL Gateway Antivirus provides protection against this new wave via GAV: Zbot.JJP (Trojan) signature. Total Signature hits recorded since yesterday – 872,128 hits (Signature statistics image below)
————————————————
–Updated March 26, 2009—
SonicWALL UTM Research team saw a new wave of DHL Tracking number invoice spam with different attachment payloads starting March 25, 2009.
SonicWALL Gateway Antivirus provided proactive protection against this new wave via GAV: Suspicious#waledac.8 (Worm) signature that was released on March 9, 2009. Total Signature hits recorded since yesterday – 576,942 hits (Signature statistics image below)
————————————————
–Original publish date: March 23, 2009—
SonicWALL UTM Research team observed a new wave of the on-going Tracking number invoice spam campaign starting Sunday, March 22, 2008. The email has a zip archived attachment which contains the new Buzus Trojan variant.
SonicWALL has received more than 1,700 e-mail copies of this malware till date. The e-mail looks like following:
Attachment: DHL_DOC.zip (contains DHL_DOC.exe)
Update [March 26, 2009]:
Attachment: DHL_HELP.zip (contains DHL_HELP.exe)
Update [March 27, 2009]:
Attachment: dhl_n756512.zip (contains dhl_n756512.exe)
Subject: DHL Tracking number #[15 digit alphanumeric ID]
Email Body:
————————
Hello!
We were not able to deliver postal package you sent on the 14th of March in time because the recipient’s address is not correct.
Please print out the invoice copy attached and collect the package at our office.
Your personal manager: Nathan Lund,
Customer Service: 1-800-CALL-DHL
Fax: 888-221-6211
DHL International, Ltd. All Rights Reserved.
————————
Update [March 26, 2009]: The executable file inside the zip attachment in the new wave has an icon disguised as a Microsoft Help file and it looks like following:

The executable file inside the zip attachment has an icon disguised as a Microsoft Word document file and it looks like following:

Update [March 27, 2009]: A screenshot of a sample e-mail for the third wave is shown below:

Update [March 26, 2009]: A screenshot of a sample e-mail for the second wave is shown below:

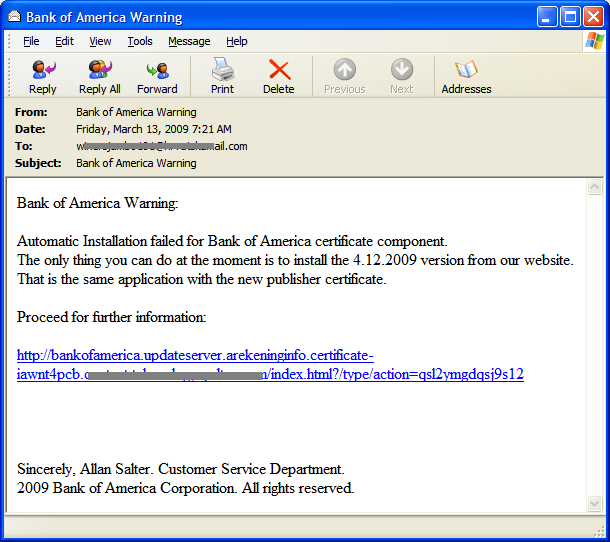
A screenshot of a sample e-mail is shown below:

The Trojan when executed performs following host level activity:
- Creates a directory lowsec in Windows System folder
- Creates files local.ds, user.ds, and user.ds.lll in the lowsec directory
- Drops a copy of itself as sdra64.exe in Windows system directory
It modifies the following Registry key for running sdra64.exe on system reboot:
- HKLMSOFTWAREMicrosoftWindows NTCurrentVersionWinlogonUserinit: “(System_Dir)userinit.exe,(System_Dir)sdra64.exe,”
It also tries connect and download an encrypted configuration file from the following URL:
The Trojan is also known as DR/Delphi.Gen [AntiVir], trojan W32/Trojan3.AIY [F-Prot], and VirTool:Win32/DelfInject.gen!J [Microsoft]
SonicWALL Gateway AntiVirus provides protection against this malware via GAV: Buzus.ARQX (Trojan),GAV: Suspicious#waledac.8 (Worm) and GAV: Zbot.JJP (Trojan) signatures.