New ZBot variant (May 12, 2009)
–Updated May 12, 2009—
SonicWALL UTM Research team saw a new wave of ZBot variant spam campaign comprising of fake e-mail message from Western Union money transfer service, starting early morning today May 12, 2009.
SonicWALL Gateway Antivirus provides protection against this new wave via GAV: Suspicious#waledac.8 (Worm) and GAV: ZBot.MT (Trojan) signature. Total Signature hits recorded today- 296,341 hits (Signature statistics image below)
SonicWALL has received more than 2,200 e-mail copies of this malware till now. The e-mail looks like follwoing:
Attachment: MTCN_NR8621982.zip (contains MTCN_NR8621982.exe) or MTCN_INVOICE.zip (contains MTCN_INVOICE.exe)
Subject: Western Union Transfer MTCN: (10 digit random number)
Email Body:
————————
Dear client!
The money transfer you have sent on the 21st of March wasn’t received by the recipient.
According to the Western Union treaty the transfers which are not received in 30 business days are to be returned to sender.
To collect funds you need to print the invoice attached to this e-mail and visit the nearest Western Union branch.
Thank you!
[(some site) : nospam] [EMAILID: (random email address on above site)]
[TIME:(timestamp)]
————————
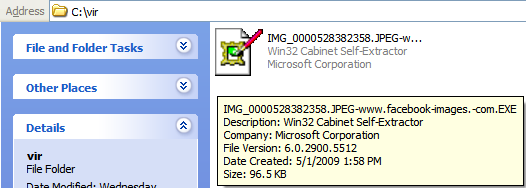
The executable file inside the zip attachment has an icon disguised as a Microsoft Office Excel sheet and it looks like following:

A screenshot of a sample e-mail is shown below:

–Updated May 08, 2009—
SonicWALL UTM Research team saw a second wave of ZBot WorldPay card spam campaign with different attachment payloads starting on May 07, 2009.
SonicWALL Gateway Antivirus provides protection against this new wave via GAV: Suspicious#waledac.8 (Worm) signature. Total Signature hits recorded since yesterday – 390,249 hits (Signature statistics image below)
–Original publish date: April 23, 2009—
SonicWALL UTM Research team observed a new wave of ZBot Trojan spam campaign starting today, April 23, 2009. The email has a zip archived attachment which contains the new ZBot Trojan variant.
SonicWALL has received more than 2,000 e-mail copies of this malware till now. The e-mail looks like follwoing:
Attachment: WorldPay_TRANS_8651.zip (contains WorldPay_TRANS_8651.exe)
[May 08, 2009] Update: Attachment: WorldPay_CONFR.zip (contains WorldPay_CONFR.exe)
Subject: WorldPay CARD transaction Confirmation
Email Body:
————————
Thank you!
Your transaction has been processed by WorldPay, on behalf of Amazon Inc. The invoice file is attached to this message. This is not a tax receipt. We processed your payment. Amazon Inc has received your order, and will inform you about delivery. Sincerely, Amazon Team
This confirmation only indicates that your transaction has been processed successfully. It does not indicate that your order has been accepted. It is the responsibility of Amazon Inc to confirm that your order has been accepted, and to deliver any goods or services you have ordered.
————————
[May 08, 2009] Update: The executable file inside the zip attachment has an icon disguised as a Microsoft Office Excel sheet and it looks like following:

The executable file inside the zip attachment has an icon disguised as a Microsoft Help file and it looks like following:

[May 08, 2009] Update: A screenshot of a sample e-mail is shown below:

A screenshot of a sample e-mail is shown below:

The Trojan when executed performs following host level activity:
- Creates a directory lowsec in Windows System folder
- Creates files local.ds, user.ds, and user.ds.lll in the lowsec directory
- Drops a copy of itself as sdra64.exe in Windows system directory
It modifies the following Registry key for running sdra64.exe on system reboot:
- HKLMSOFTWAREMicrosoftWindows NTCurrentVersionWinlogonUserinit: “(System_Dir)userinit.exe,(System_Dir)sdra64.exe,”
[May 08, 2009] Update: It also tries connect and download an encrypted configuration file from the following URL:
- bklinkov.ru/hi/start.cfg
It also tries connect and download an encrypted configuration file from the following URL:
- grafjasqq.ru/kiew/kiew.cfg
The Trojan is also known as TR/Spy.ZBot.66560 [AntiVir], Trojan-Spy:W32/Zbot.OSK [F-Prot], and PWS:Win32/Zbot.M [Microsoft]
SonicWALL Gateway AntiVirus provides protection against this malware via GAV: ZBot.M (Trojan), GAV: Suspicious#waledac.8 (Worm) and GAV: ZBot.MT (Trojan) signatures.