FakeAV Spam Continues (Apr 23, 2010)
SonicWALL UTM Research team continued to monitor the FakeAV spam campaigns appearing with variety of themes. Below is the e-mail format and a sample e-mail for each of these spam themes that we saw during the week:
Campaign #1 – DHL Tracking Invoice
- Subject: DHL Tracking NR[8-digits].
Attachment: DHL_invoice_Nr[5-digits].zip (contains DHL_invoice_Nr[5-digits].exe)
Email Body:
————————
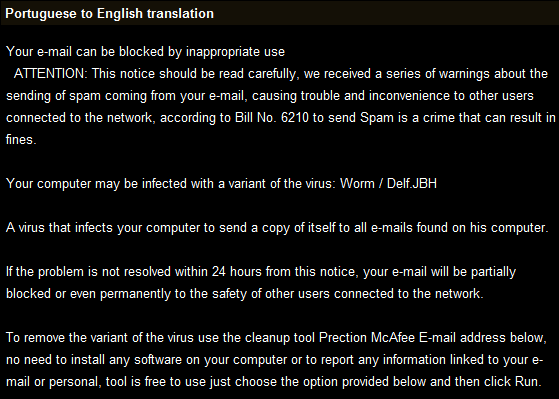
Dear customer!
Unfortunately we were not able to deliver postal package sent on
the 22nd of March in time because the addressee’s address is wrong
Please print out the invoice copy attached and collect the package
at our department
DHL Delivery Services.
————————
The e-mail message looks like below:
Campaign #2 – DHL Delivery Services
- Subject: Please attention!
Attachment: label.zip (contains label.exe)
Email Body:
————————
Dear customer!
The courier company was not able to deliver your parcel by your address.
Cause: Error in shipping address.
You may pickup the parcel at our post office personaly.
Please attention!
The shipping label is attached to this email.
Print this label to get this package at our post office.
Please do not reply to this e-mail, it is an unmonitored mailbox!
Thank you,
DHL Delivery Services.
————————
The e-mail message looks like below:
Campaign #3- Myspace Password
- Subject: Myspace Password Reset Confirmation! Your Support
Attachment: password.zip (contains password.exe)
Email Body:
————————
Because of the measures taken to provide safety to our clients,
your password has been changed. You can find your new password
in attached document
Thanks,
The Myspace Team
————————
The e-mail message looks like below:
Campaign #4 – Account Information
- Subject: {Mail Domain} account notification
Attachment: setup.zip (contains setup.exe)
Email Body:
————————
Dear Customer,
This e-mail was send by {mail domain} to notify you that we have
temporanly prevented access to your account
We have reasons to beleive that your account may have been
accessed by someone else. Please run attached file and Follow
instructions
(C) {mail domain}
————————
The e-mail message looks like below:
Campaign #5 – Love Mail
- Subject:I love… our love.
Attachment: open.zip (contains open.exe)
Email Body 1:
————————
I think… our relationship is beautiful
————————
Email Body 2:
————————
Your love has made me… wealthy beyond my dreams
————————
The e-mail message looks like below:
SonicWALL Gateway AntiVirus provided protection against these spammed FakeAV variants via following signatures:
- GAV: Bredolab.DI#email (Trojan) – 2,395,432 Hits
- GAV: FakeAlert.GEN_6 (Trojan) – 581,491 Hits
- GAV: Bredolab.MP#email_2 – 344,011 Hits
- GAV: FakeAV.KO (Trojan) – 1,443 Hits
- GAV: Bredolab.CA (Trojan) – 4,964 Hits
- GAV: FakeRean_5 (Trojan) – 2,343 Hits