Introduction
After several months of hiatus, Emotet is back. SonicWall Capture Labs threat research team has observed starting last week that the notorious malware, which heavily targets large organizations, has returned with similar tactics and functionality observed in past variants. Originally a banking trojan, Emotet has evolved into a dropper-type class of malware. It has been spreading through malicious Microsoft Office documents via email. Initially using JavaScript, VBA macros are now used to compromise the victims’ machines.
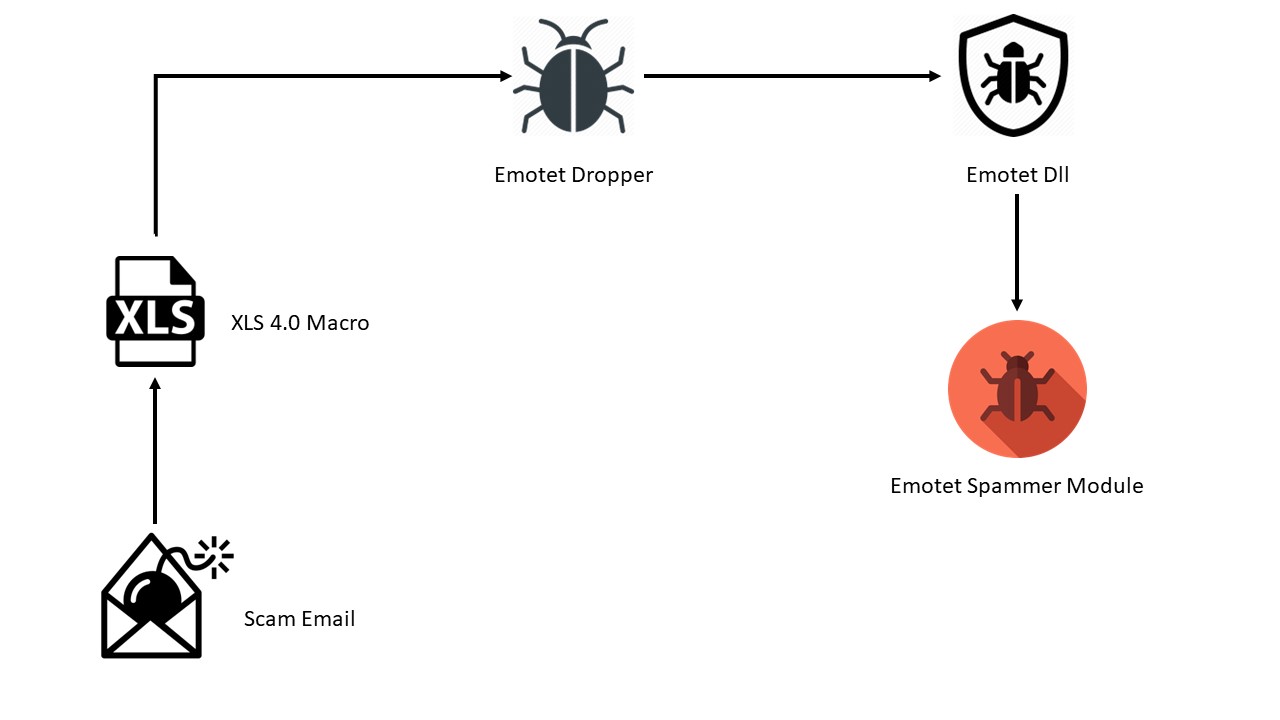
Figure 1: Infection Chain
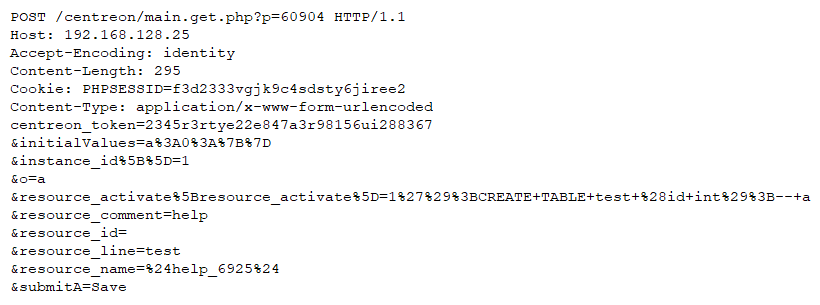
Infection Vector
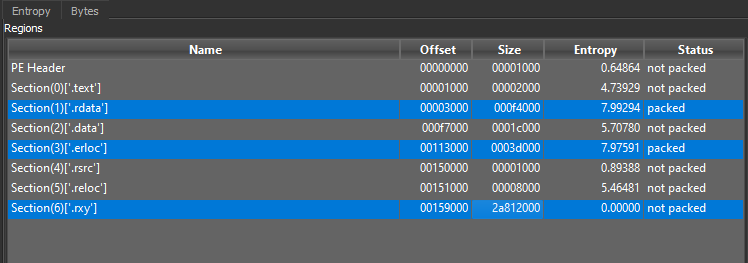
The infection vector is Excel 4.0 macros with malicious code distributed across excel spreadsheet cells. By default, the Excel file is opened in protected view, with the macros disabled. For this, Emotet Excel files have one image with instructions (Figure 2) asking user to copy the file to <Microsoft Office>\Templates folder and run again. This makes sure that execution of macros will be carried out seamlessly with user interaction.
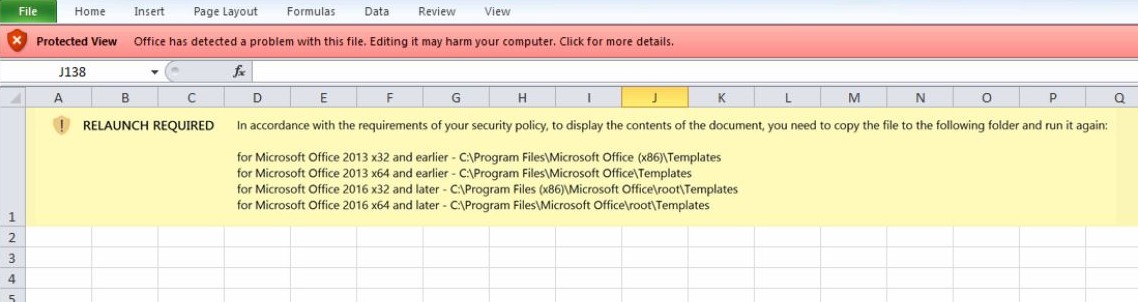 Figure 2: Malicious document warning. The required actions infect the machine.
Figure 2: Malicious document warning. The required actions infect the machine.
The macro code contains multiple URLs which further download the emotet dropper DLL.
URLs:
hxxp://app.clubdedocentes[.]com/storage/DCcq9ekgH99sI/
hxxp://linhkiendoc[.]com/app/payments/qoy5JqpLqrbsKl/
hxxp://sourcecool[.]com/throng/iOD/
hxxp://www.stickers-et-deco[.]com/Adapter/lYw/
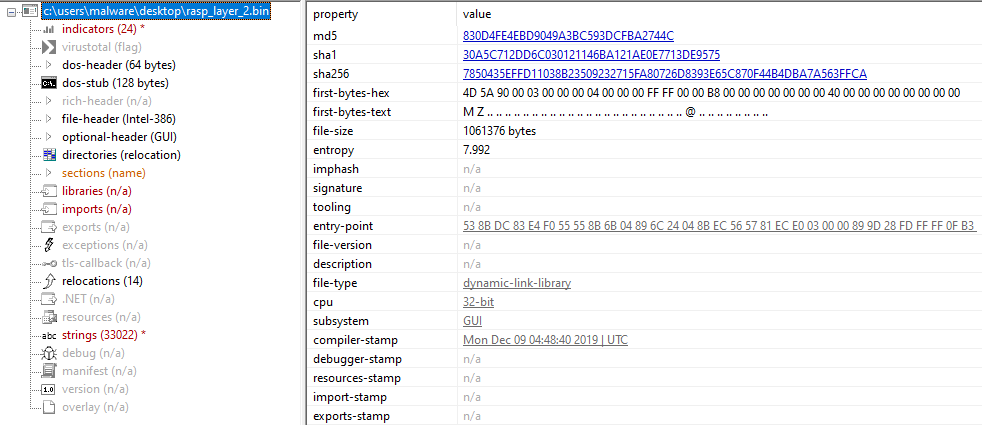
Out of these 4 URLs only 3 were active at the time of analysis. These URLs downloaded 3 Emotet dropper DLLs having similar functionality. The DLLs are executed using regsvr32.exe.
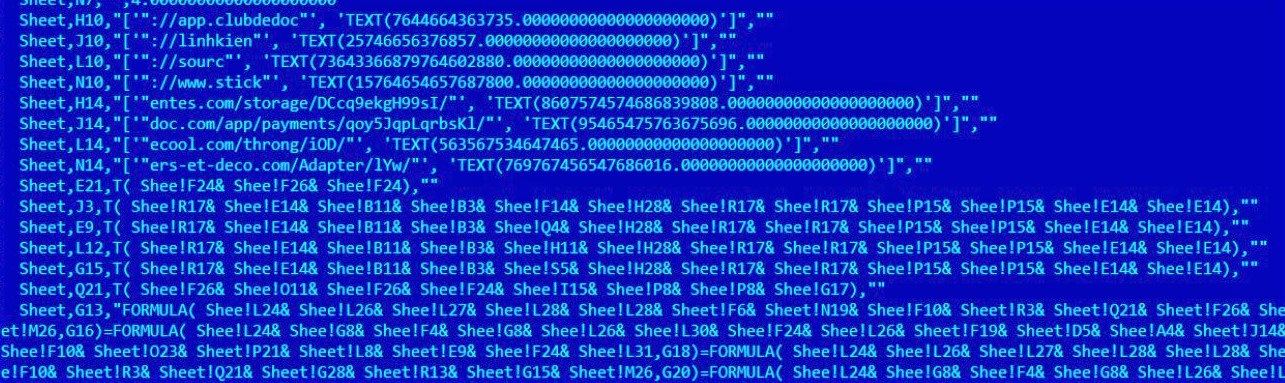 Figure 3: View of the malicious VBA macro
Figure 3: View of the malicious VBA macro
DLL Analysis
Emotet is known for distributing many different malware families. During the analysis of two samples, no additional malware was observed being dropped or downloaded.
Sample 1
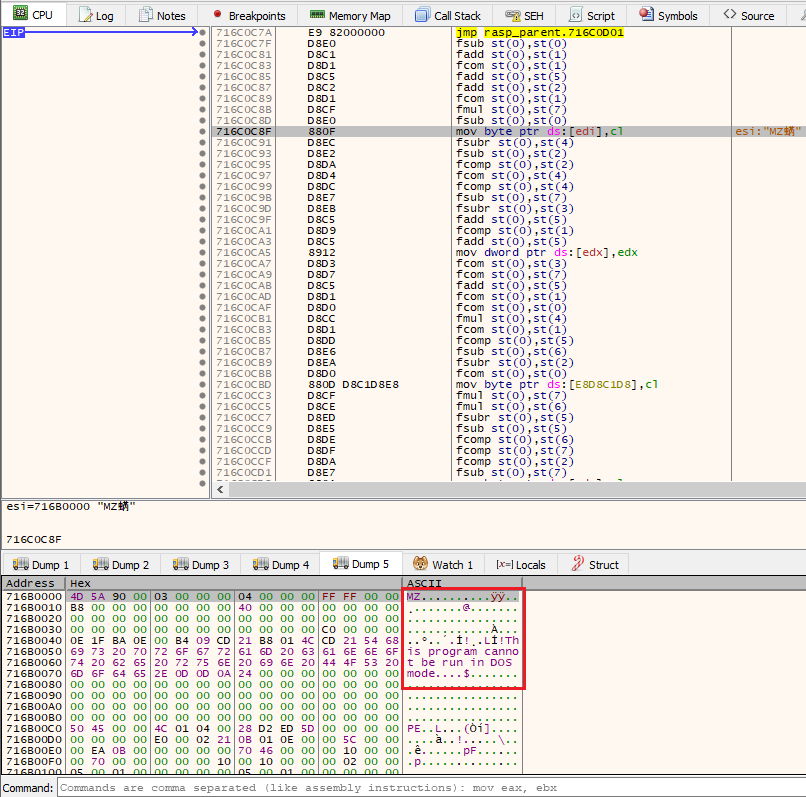
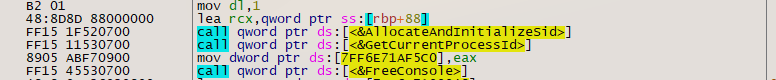
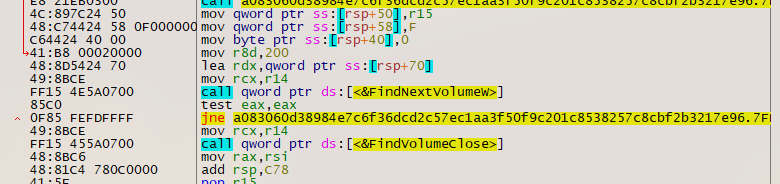
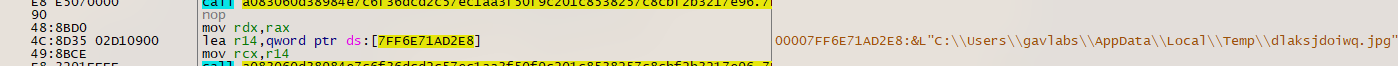
The dropper DLL has highly obfuscated custom packer code, including encrypted main Emotet DLL. The listed APIs involve multiple imports that are known to be used with malware. These cover multiple areas of monitoring, enumeration, execution, encryption, persistence, and exfiltration. Multiple APIs are loaded using DWORDs stored in memory (Figure 4).
 Figure 4: Packed code shown in x64dbg
Figure 4: Packed code shown in x64dbg
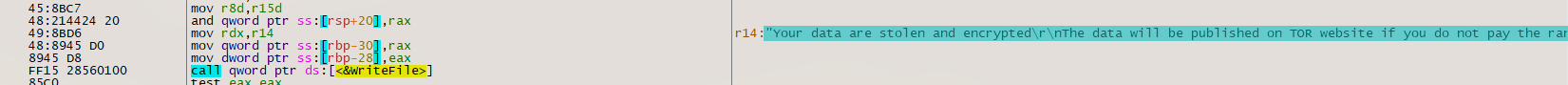
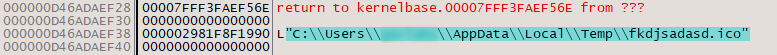
The custom decryption loop is used to decrypt the main Emotet DLL using key “vGZlfkkg?U^>+xzU”. Once regsvr32.exe is executed, the DLL is moved and renamed to “~\AppData\Local” and/or “\Windows\System32\” locations with a randomized name for both the parent folder and the file itself. A registry key is then created to autorun when the system is restarted (Figure 5).
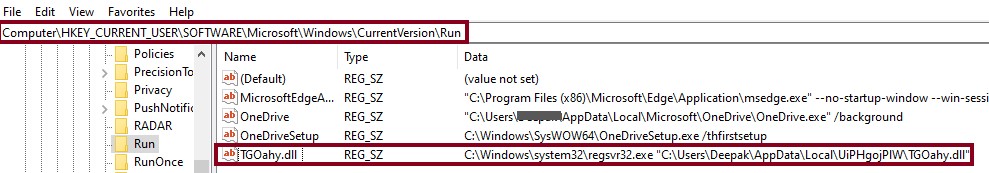
Figure 5: Run Entry created for persistence
The process will then attempt to reach out to multiple IP addresses with a generated cookie and collected data. After initial communication with CnC servers it downloads further Emotet spammer module to the same folder or the “Appdata” directory.
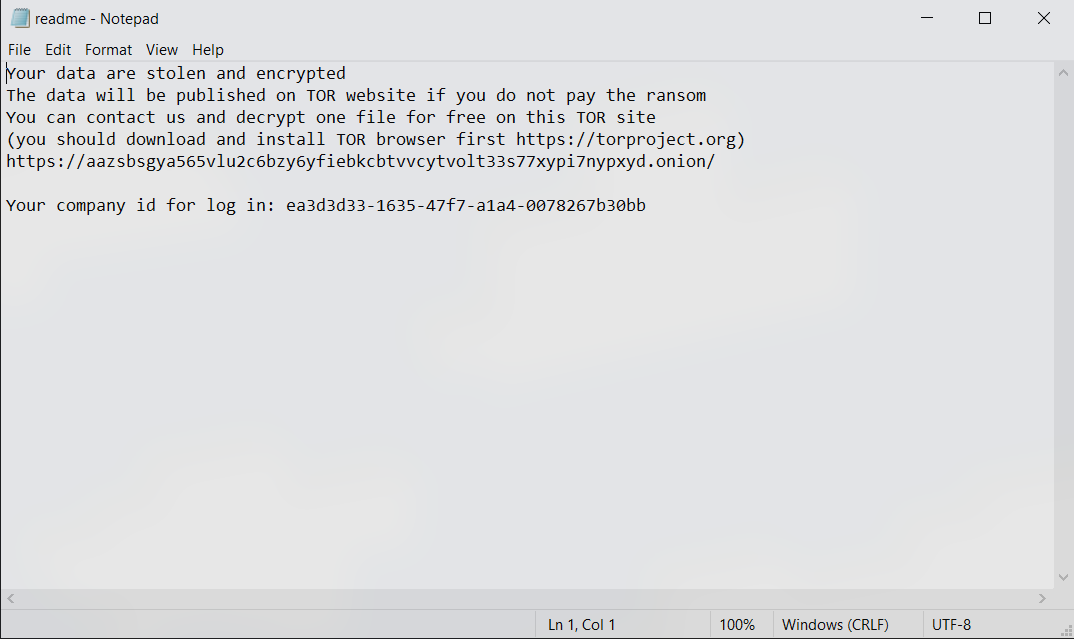
For further spreading spammer module uses multiple malicious email templates like the one mentioned in Figure 6 below.
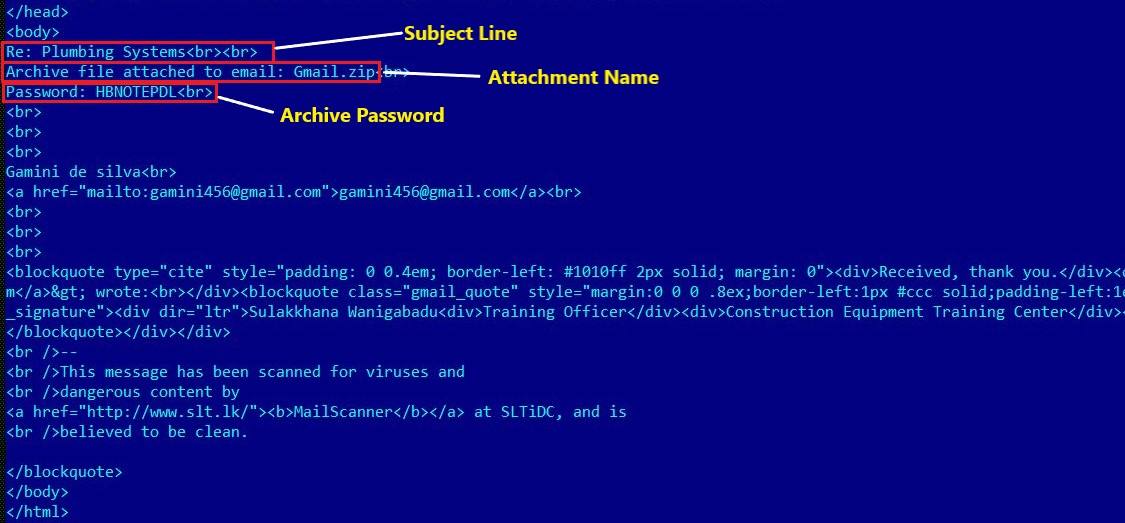
Figure 6: Email Template
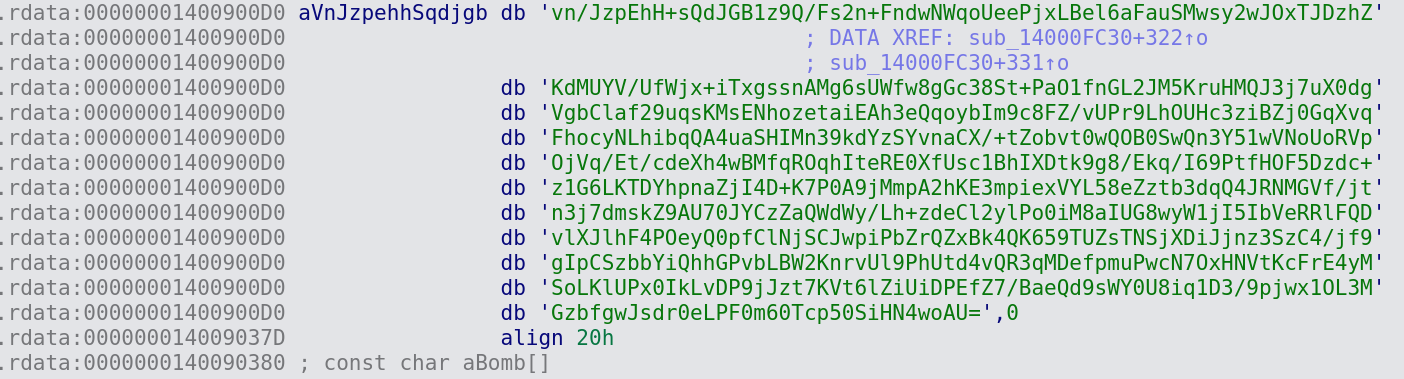
It also uses a number of email domains, email addresses, their passwords and other information including malicious email attachments to spread across domains as seen in Figure 7.
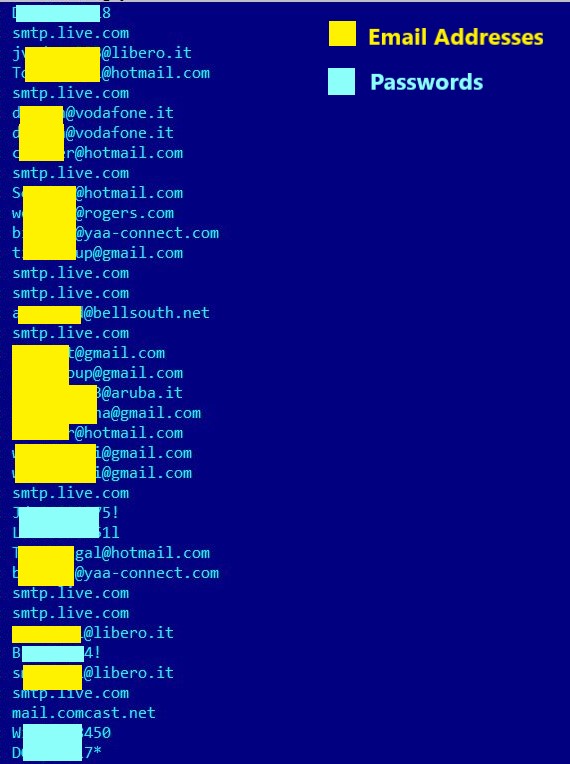 Figure 7: Email Addresses and Passwords
Figure 7: Email Addresses and Passwords
This elaborates the redistribution mechanism of malware to infect other victims using already compromised email credentials.
Sample 2
This sample was a separate DLL file that showed several differences in both code and behavior. Manually running the decryption function resulted in a DLL being created within newly allocated memory space, but instead of a randomly named file, it’s called ‘clover.dll’ (Figure 8) and differs from the dropper in multiple ways.
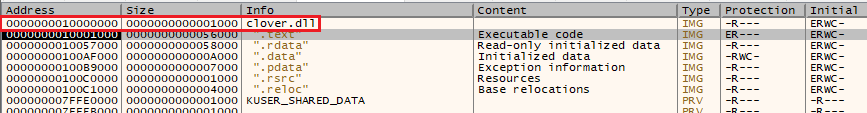
Figure 8: Clover.dll allocated in memory
The first point is that when clover.dll drops, it lacks several of the anti-analysis features that the original has; notably, one can go directly to the entrypoint in a debugger without the program terminating itself. There is also a string that produced only two Google results (f:\rtm\vctools\vc7libs\ship\atlmfc\include\afxwin2.inl), both of which are samples on Alienvault OTX[i][ii].
Running ‘clover.dll’ with regsvr32.exe results in the same behavior as the dropper sample. It is moved to ~AppData\Local, a registry key is created for persistence, and system enumeration begins. Regsvr32 then spawns a child process and kills the parent (Figure 9), becoming a ‘non-existent process’; this is an anti-analysis technique that prevents debuggers from attaching to the process.
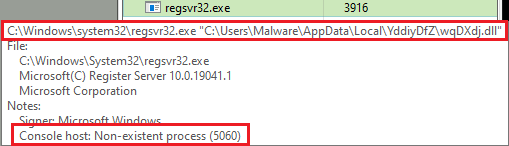
Figure 9: This process does not exist (to a debugger)
The second part to note is the way Emotet is communicating with the C2 servers: using regsvr32.exe to send TCP requests. No tool normally used for packet capture will show the action (Fiddler, Wireshark, TCPMon), except for Procmon. The entire communication occurs within 2-3ms as seen in Figures 10 and 11. Attempts to use netstat also failed.
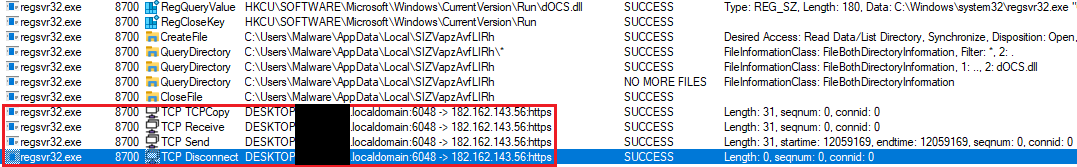
Figure 10: Procmon output of TCP communications

Figure 11: Timestamps from beginning to end
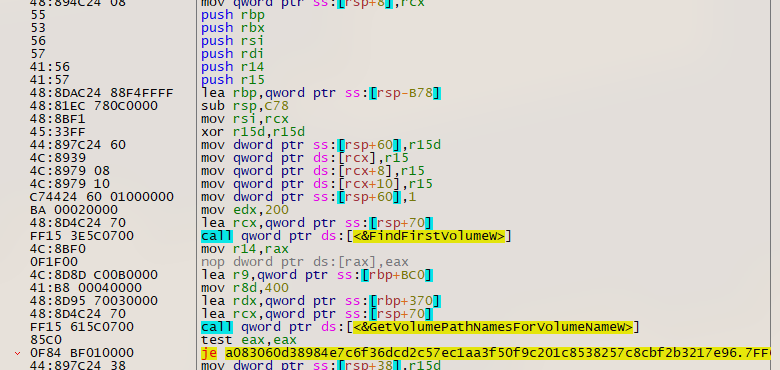
Looking at the runtime memory of regsvr32, a large list of C2 addresses were found (Figure 12), along with cookie information and public keys.

Figure 12: Beginning of C2 list in private-mapped memory
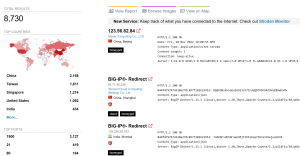
SonicWall Real Time Deep Memory Inspection (RTDMI) is detecting the malicious Excel spread sheet in CAPTURE ATP. The emotet dropper, emotet dll and spammer module are also being detected by RTDMI.
Evidence of detection by RTDMI ™ engine for the emotet dll can be seen in the below screenshot :
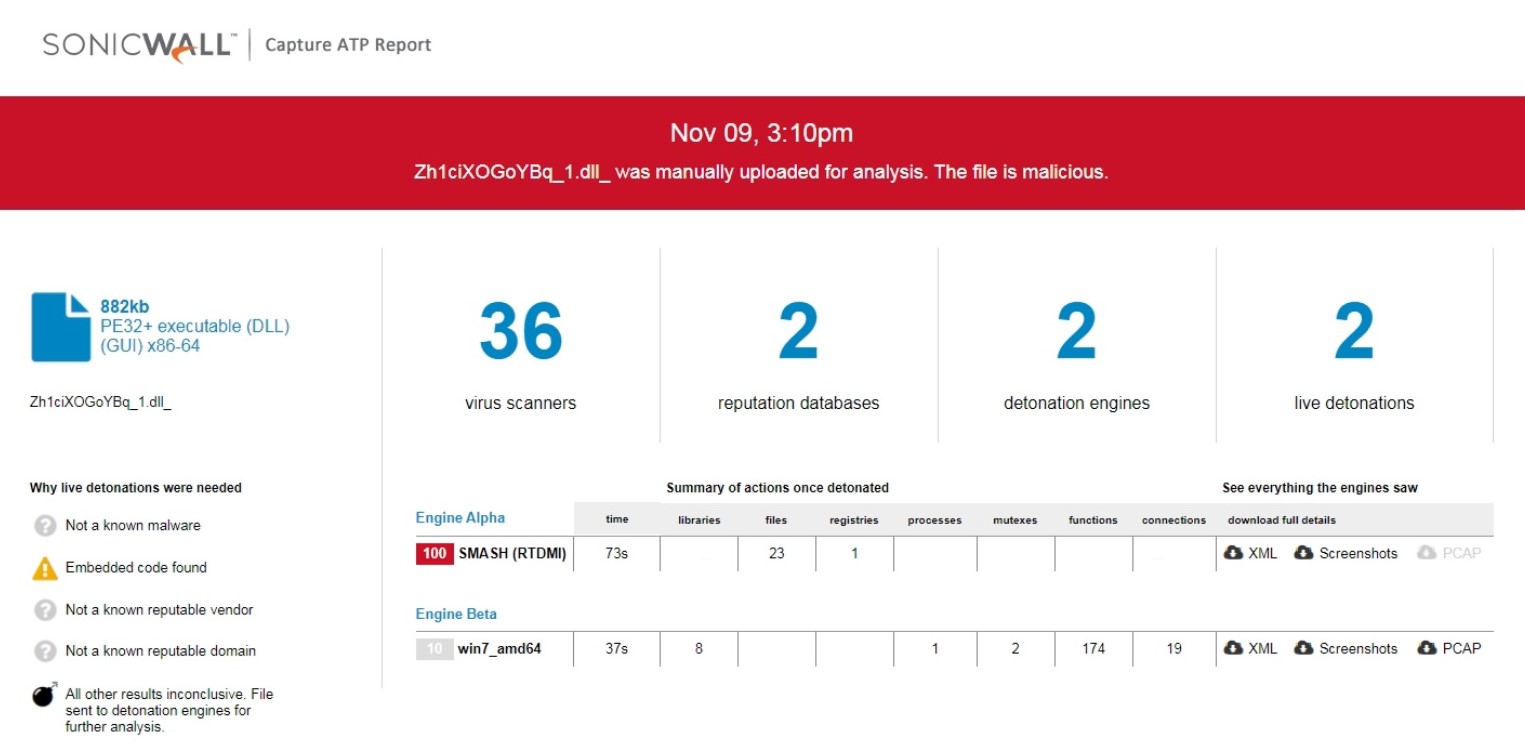
Figure 13: RTDMI ATP Report results
IOCs
SHA256:
0bbcf67529105af0086ba37236adde773fa862a9af187c75903868d01b390202
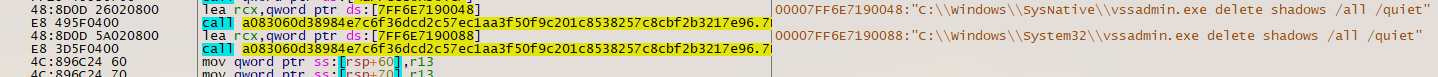
a116213f16ecd416cbde43ddf94d3e5af1935886d19db1e978225c15616c1d7b
faf0a6cea7e6a5d7fea43ed8e2f89eee56f712e6334e19e1b4c2b75ffb71f720
dcb3f8703accb02764306e112857adf35fd93c46cd7bfe45a295f16e6a215c72
bf60837275da15ef6f67ab6214fea56a084045d19c056c01faecd3c5d5b7f207
baf72fda8d35b6f6653ecdae1bfac9ddb373b9a4e7d27e586cce30201557a1f8
c680183e3a3650a0930960227d8659ee5bba1406ef5c8f01546fd0c165c9eca2
04c40a669fcfcd20bd429cbe4f78c71e8403ca70f804262a24024cb40dba321b
64dca5069a1e7b3ed910d6525550cf1235de5199cb2a195da490d2cfb65334e4
b8d2ad91155d779270b7cb8b914e5a262d8a05bf39ba44dd56935a1ee9bc066e
C2 IP Addresses:
1.234.2[.]232:8080
101.50.0[.]91:8080
103.132.242[.]26:8080
103.43.75[.]120:443
103.75.201[.]2:443
104.168.155[.]143:8080
107.170.39[.]149:8080
110.232.117[.]186:8080
115.68.227[.]76:8080
119.59.103[.]152:8080
129.232.188[.]93:443
139.59.126[.]41:443
139.59.56[.]73:8080
147.139.166[.]154:8080
149.28.143[.]92:443
149.56.131[.]28:8080
153.126.146[.]25:7080
159.65.140[.]115:443
159.65.88[.]10:8080
159.89.202[.]34:443
160.16.142[.]56:8080
163.44.196[.]120:8080
164.68.99[.]3:8080
164.90.222[.]65:443
167.172.199[.]165:8080
167.172.253[.]162:8080
169.57.156[.]166:8080
169.60.181[.]70:8080
172.104.251[.]154:8080
172.105.226[.]75:8080
173.212.193[.]249:8080
182.162.143[.]56:443
182.162.143[.]5:8080
54.37.136[.]187:8080
95.54.66[.]204:1013
183.111.227[.]137:8080
185.4.135[.]165:8080
186.194.240[.]217:443
188.44.20[.]25:443
197.242.150[.]244:8080
201.94.166[.]162:443
206.189.28[.]199:8080
209.97.163[.]214:443
212.24.98[.]99:8080
213.239.212[.]5:443
45.118.115[.]99:8080
45.176.232[.]124:443
45.235.8[.]30:8080
5.135.159[.]50:443
51.161.73[.]194:443
72.15.201[.]15:8080
79.137.35[.]198:8080
82.223.21[.]224:8080
91.187.140[.]35:8080
91.207.28[.]33:8080
94.23.45[.]86:4143
95.217.221[.]146:8080
URLs:
hxxp://app.clubdedocentes[.]com/storage/DCcq9ekgH99sI/
hxxp://linhkiendoc[.]com/app/payments/qoy5JqpLqrbsKl/
hxxp://sourcecool[.]com/throng/iOD/
hxxp://www.stickers-et-deco[.]com/Adapter/lYw/
Public Keys:
RUNTMSAAAABAX3S2xNjcDD0fBno33Ln5t71eii+mofIPoXkNFOX1MeiwCh48iz97kB0mJjGGZXwardnDXKxI8GCHGNl0PFj5z/VpKQADAJA=
RUNLMSAAAADzozW1Di4r9DVWzQpMKT588RDdy7BPILP6AiDOTLYMHkSWvrQO5slbmr1OvZ2Pz+AQWzRMggQmAtO6rPH7nyx2a/UNKQAXAJA=
JA3 fingerprint:
8916410db85077a5460817142dcbc8de
Cookies:
WnnMFWF=0d3850HcEUxB57edscLqHsb2YxPDCKbPSZncMTx3O0h9lQgJCvRMC//BrnYhPFxgMRGCoZSHhMyTtzRWyGhLZIyda+8qlUGgEDzQZ0FNyFIFUjbe0aBVe6vknvoT1bSoMmylmeeNjwtPr1DVQt8JBHpbWAXjxP+zpYCEPYLK2b02cC0/cJtzfFLcECfpMT9WAGpj2uFr6QqpTPIivkS/Ta2r9sHA20takVBoZ9TbfwVVtlUfqlozgTltkAtCazcU/W8R9mfAVM1Y
Qs=0WODCSXcomwJtgWqI5e4bPB3yrdQoAEow+xn5MRK9/ao9xobva9p8/jpU6RvJLwBpREszZe6f224Qoc20YVdaKXLpEoD+CwRklu0H7XCKQZe8V+CPjtzCo5fzkDm2SHBIMJmPkIdY0HZvSGjXBvSwpA74U8FBJdbzKmUSvZKeLE2D1zGVF25KW5b0s+FQ9ah7qgmwJxNkXCL7cbrL73Cnqi5G3XPALWmwxxRbX2F/rzzDxIkkxHSBI7ggXr5ndl799lGGQd4F0v171zhI+/VNrTtpcEnZM5drvJsD/wrrEGBY7NJUGIom7MjeZtu8/cOx+TR
[i]https://otx.alienvault.com/indicator/file/7fbcad6af8fc4b6aa18f877feabcfc31b0a4b1a4895ccaf70a90bceaff9331d2/
[ii]https://otx.alienvault.com/indicator/file/f8fa14b1f1d267d5c348d97f516ea9e6912f8747a6e659b45c428d931082f6e6