Microsoft Security Bulletin Coverage for August 2021
SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of August 2021. A list of issues reported, along with SonicWall coverage information, is as follows:
CVE-2021-26432 Windows Services for NFS ONCRPC XDR Driver Remote Code Execution Vulnerability
IPS 2045: Windows NFS Remote Code Execution (CVE-2021-26432)
CVE-2021-34480 Scripting Engine Memory Corruption Vulnerability
IPS 2044: Scripting Engine Memory Corruption Vulnerability (CVE-2021-34480)
CVE-2021-34535 Remote Desktop Client Remote Code Execution Vulnerability
ASPY 207: Malformed-File exe.MP.197
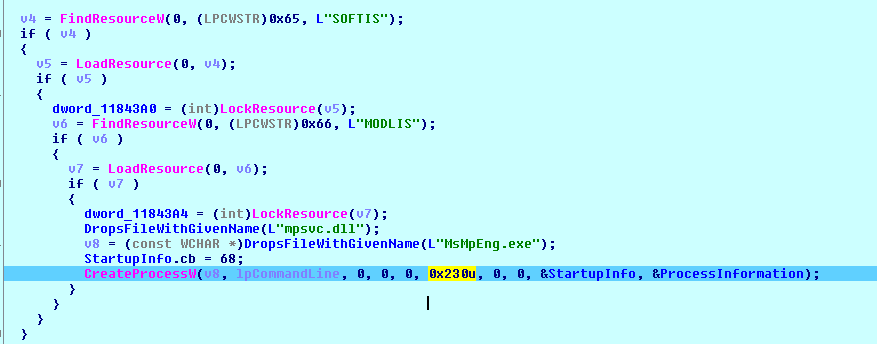
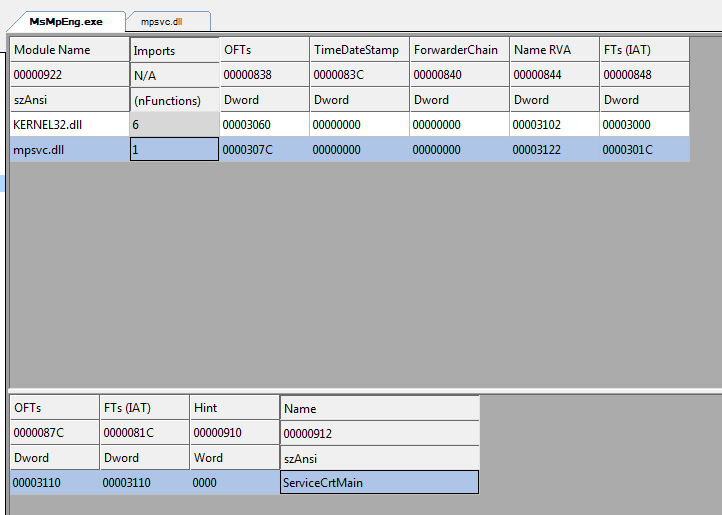
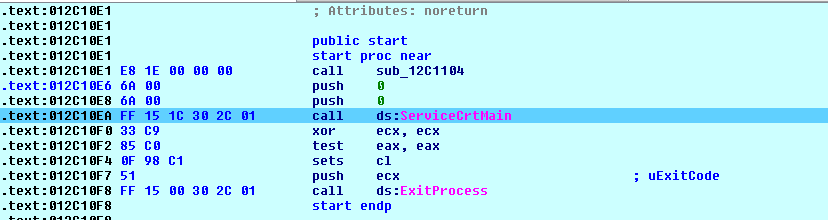
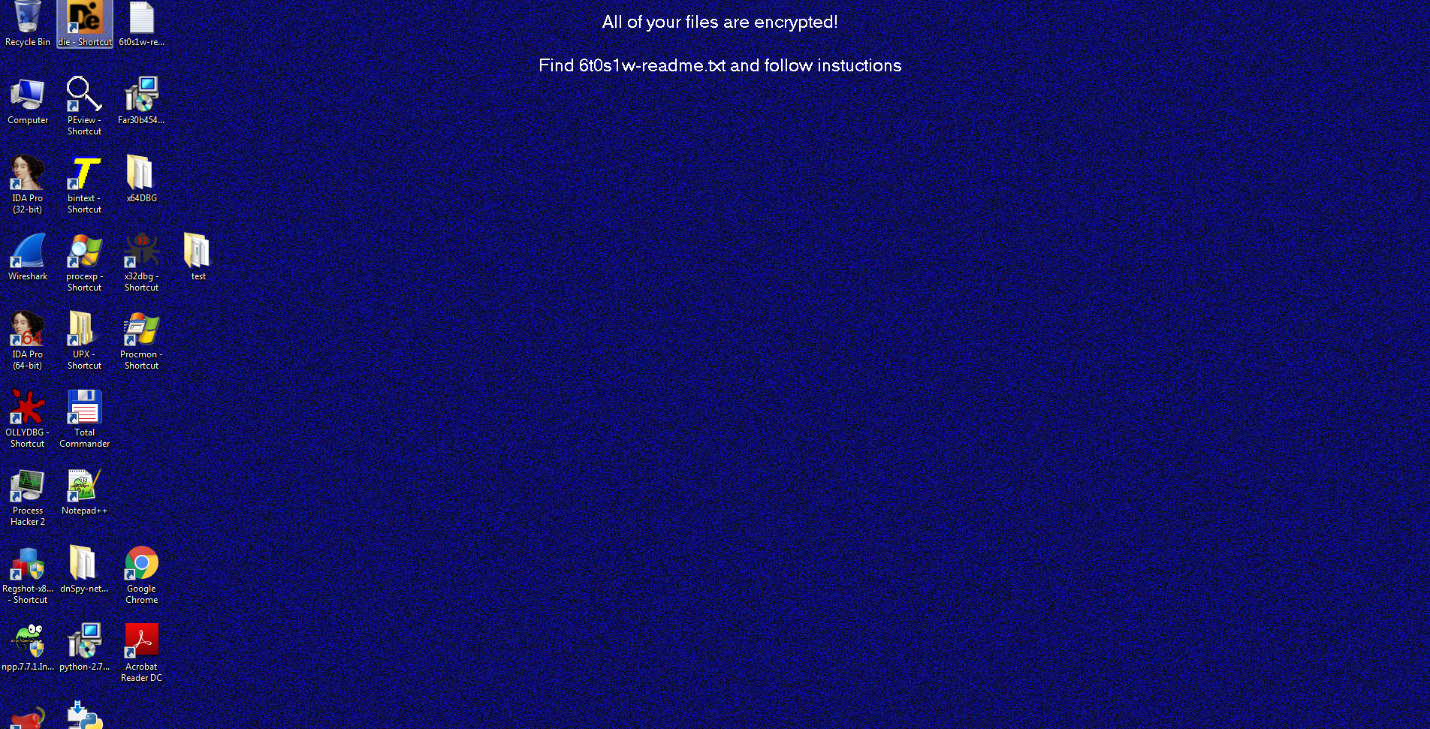
CVE-2021-36948 Windows Update Medic Service Elevation of Privilege Vulnerability
ASPY 208: Malformed-File exe.MP.198
The following vulnerabilities do not have exploits in the wild :
CVE-2021-26423 .NET Core and Visual Studio Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2021-26424 Windows TCP/IP Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-26425 Windows Event Tracing Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-26426 Windows User Account Profile Picture Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-26428 Azure Sphere Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-26429 Azure Sphere Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-26430 Azure Sphere Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2021-26431 Windows Recovery Environment Agent Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-26433 Windows Services for NFS ONCRPC XDR Driver Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-33762 Azure CycleCloud Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-34471 Microsoft Windows Defender Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-34478 Microsoft Office Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-34483 Windows Print Spooler Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-34484 Windows User Profile Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-34485 .NET Core and Visual Studio Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-34486 Windows Event Tracing Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-34487 Windows Event Tracing Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-34524 Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-34530 Windows Graphics Component Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-34532 ASP.NET Core and Visual Studio Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-34533 Windows Graphics Component Font Parsing Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-34534 Windows MSHTML Platform Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-34536 Storage Spaces Controller Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-34537 Windows Bluetooth Driver Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-36926 Windows Services for NFS ONCRPC XDR Driver Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-36927 Windows Digital TV Tuner device registration application Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-36932 Windows Services for NFS ONCRPC XDR Driver Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-36933 Windows Services for NFS ONCRPC XDR Driver Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-36936 Windows Print Spooler Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-36937 Windows Media MPEG-4 Video Decoder Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-36938 Windows Cryptographic Primitives Library Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-36940 Microsoft SharePoint Server Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-36941 Microsoft Word Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-36942 Windows LSA Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-36943 Azure CycleCloud Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-36945 Windows 10 Update Assistant Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-36946 Microsoft Dynamics Business Central Cross-site Scripting Vulnerability
There are no known exploits in the wild.
CVE-2021-36947 Windows Print Spooler Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-36949 Microsoft Azure Active Directory Connect Authentication Bypass Vulnerability
There are no known exploits in the wild.
CVE-2021-36950 Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability
There are no known exploits in the wild.