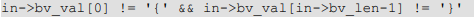OpenLDAP slapd Integer Underflow Vulnerability
Overview:
OpenLDAP is an open-source implementation of the Lightweight Directory Access Protocol (LDAP) service. On a default installation, the OpenLDAP server uses TCP port 389 for communication. The OpenLDAP server has a modular architecture where the OpenLDAP server daemon, slapd, can be configured as a frontend, a backend or as an overlay. A frontend server typically listens on a TCP port and manages connections. Backend servers can either store the Directory data using one of various available engines (e.g. back-bdb for using BerkeleyDB, backldif for using LDIF text files), or act as a proxy server for other data storage systems (e.g. back-ldap for proxying to other LDAP servers, back-sql for talking to arbitrary SQL databases, back-passwd to use Unix system passwd and group data), or as a dynamic backend that generates data on the fly.
A denial-of-service vulnerabilities has been reported in the slapd of OpenLDAP. The vulnerability is due to improper input validation in controls in LDAP search requests.
A remote attacker can exploit the vulnerability by sending a crafted query to the target OpenLDAP server. Successful exploitation could cause integer underflow which leads to denial of service condition.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2020-36221, dated 2021-01-25.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 4.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L/E:P/RL:O/RC:C).
Base score is 5.3 (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is none.
• Impact of this vulnerability on data integrity is none.
• Impact of this vulnerability on data availability is low.
Temporal score is 4.8 (E:P/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
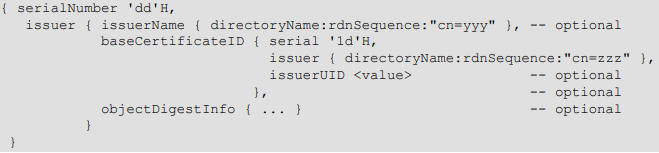
An integer underflow vulnerability exists in the OpenLDAP daemon, slapd. When slapd receives an incoming SearchRequest message including a valuesReturnFilter control with attributeCertificateExactMatch assertion, it calls a function serialNumberAndIssuerSerialPretty() to normalize the string value in matchValue. Before the normalization, it will call a function serialNumberAndIssuerSerialCheck() to validate the syntax of the string. According to the implementation, a valid syntax of the string should be like follows:
The order of the serialNumber and issuer does not matter for the validation. The validations include checking minimum length of the assertionValue or matchValue, the first and last characters are “{” and “}”, the existence of key words such as “issuer” and “serialNumber” etc. However, the validation of “{” and “}” logic is mistakenly implemented as follows:
Therefore, if the assertionValue or matchValue only starts with “{” or ends with “}” will bypass the validation. Also, the vulnerable function has an internal variable of type “unsigned long” to record the remaining length of the assertionValue or matchValue for validation. During the process of the validation, the variable will be decreased until 0. Since the vulnerable function does not validate that the last character is “}”, it failed to decrement the variable correctly. When the last character of the assertionValue or matchValue is ‘”‘, there is a chance that the length variable will be decremented beyond zero which effectively translates to a large positive value for an unsigned long integer (integer underflow). Then, the variable will be used in a loop as the upper bound for the loop counter, leading to an out-of-bound read violation.
Note that the filter part of a LDAP SearchRequest message can be used to reproduce this vulnerability too, since it also has an extensibleMatch field with the type of MatchingRuleAssertion. If the MatchingRuleId is set with OID “2.5.13.45”, the time string in the matchValue field will be parsed by the vulnerable function serialNumberAndIssuerSerialCheck() too.
A remote attacker can exploit this vulnerability by sending a crafted SearchRequest message with a Filter that contains an crafted matchValue. Successful exploitation will result in the slapd process terminating abnormally.
Triggering the Problem:
The server must have the vulnerable product installed and running.
• The attacker must be able to send an LDAP SearchRequest to the target.
Triggering Conditions:
The attacker sends a crafted SearchRequest. The server will processes this request, the vulnerability is triggered.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• LDAP, over port 389/TCP
• LDAPS, over port 636/TCP
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2084 OpenLDAP slapd serialNumberAndIssuerCheck Integer Underflow 1
• IPS: 2093 OpenLDAP slapd serialNumberAndIssuerCheck Integer Underflow 2
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Filtering attack traffic using the signatures above.
• Allowing only trusted authenticated users to Bind to the server.
• Applying the vendor provided patch.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory