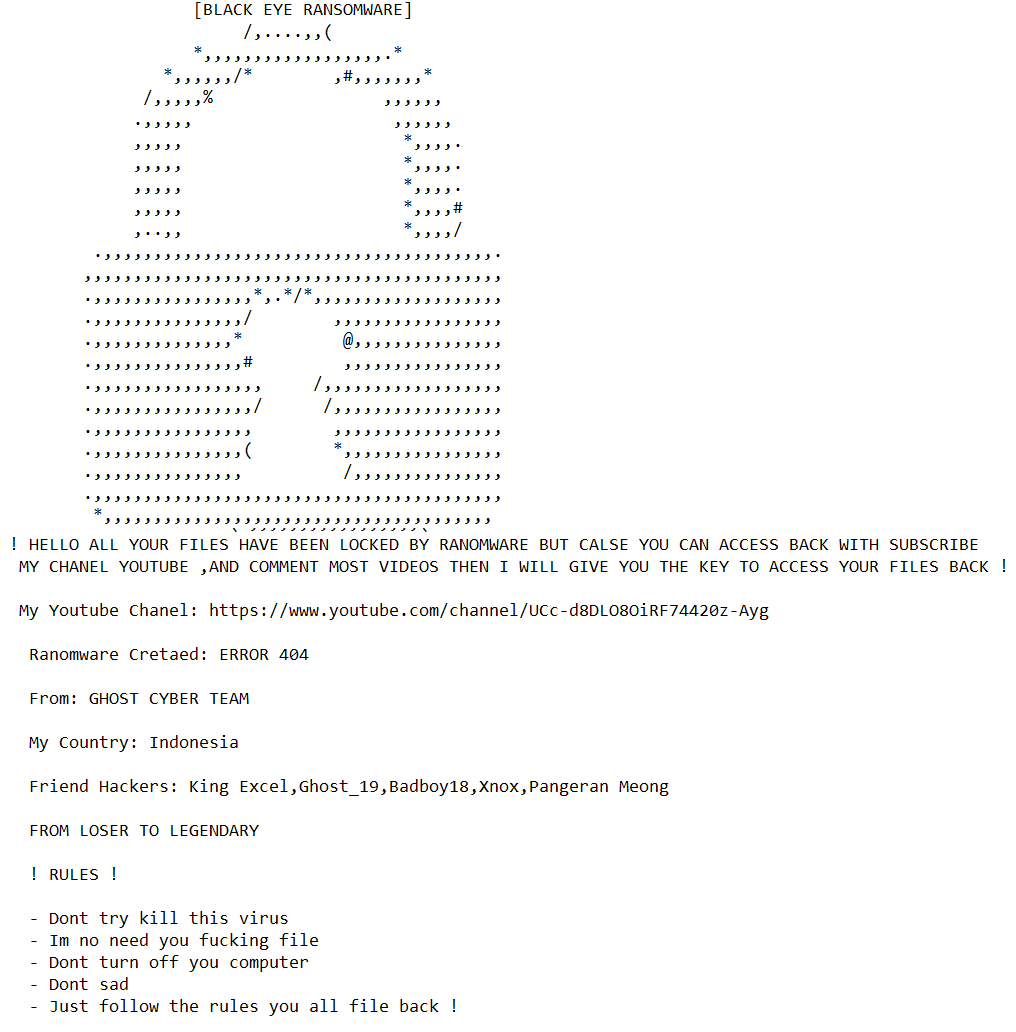
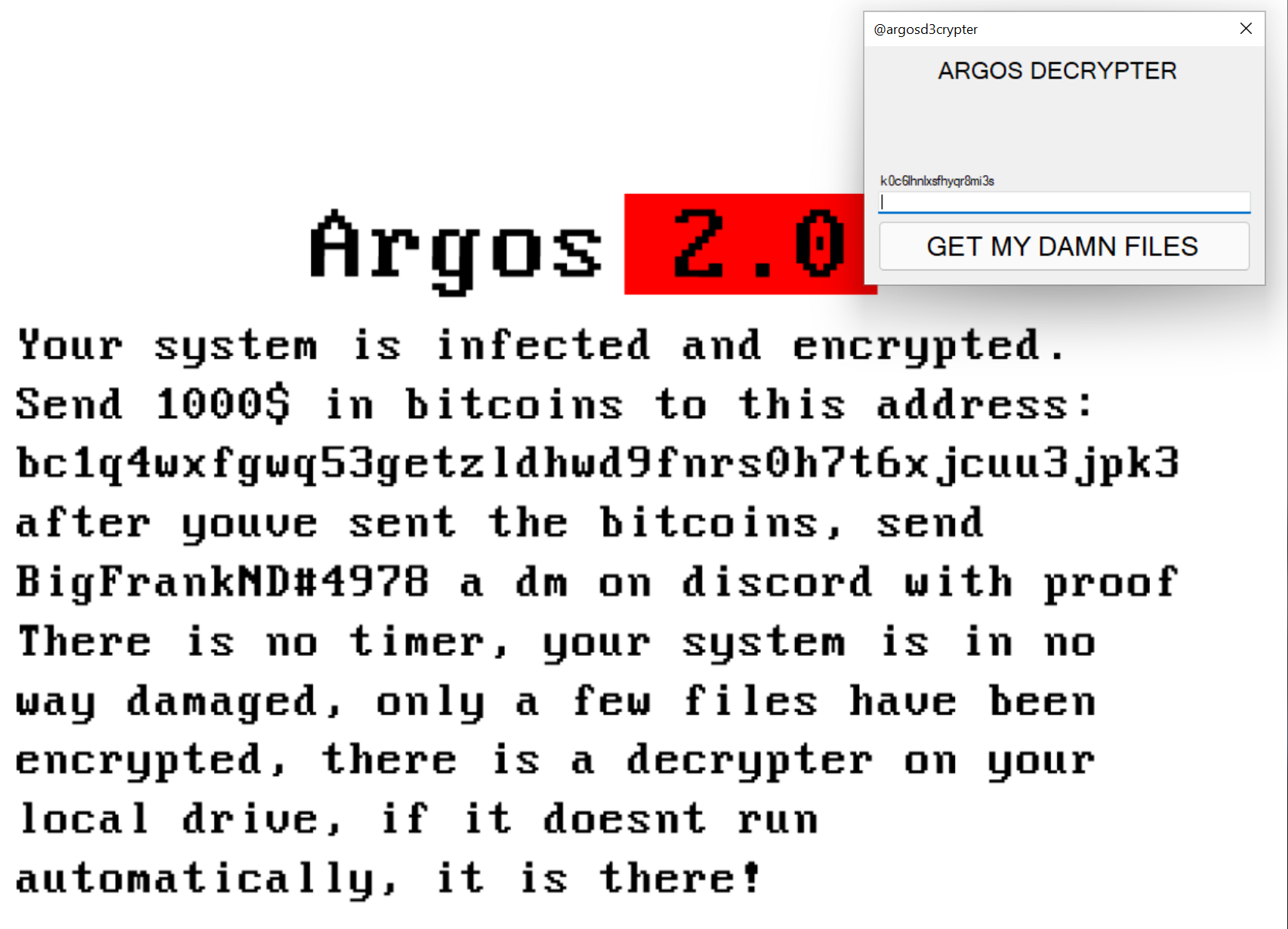
Functionality rich Android malware identified in the wild
SonicWall Threats Research Team received reports of an Android malware in the wild that was hosted on an active domain. This malware appears to be a Remote Access Trojan that has a number of capabilities.
Application Specifics
- MD5: bfdd4663a096b21a1d2b7c993bb0aecd
- Package Name: com.picture.mammal
App Execution
Installing the application, the icon is visible without any application name:
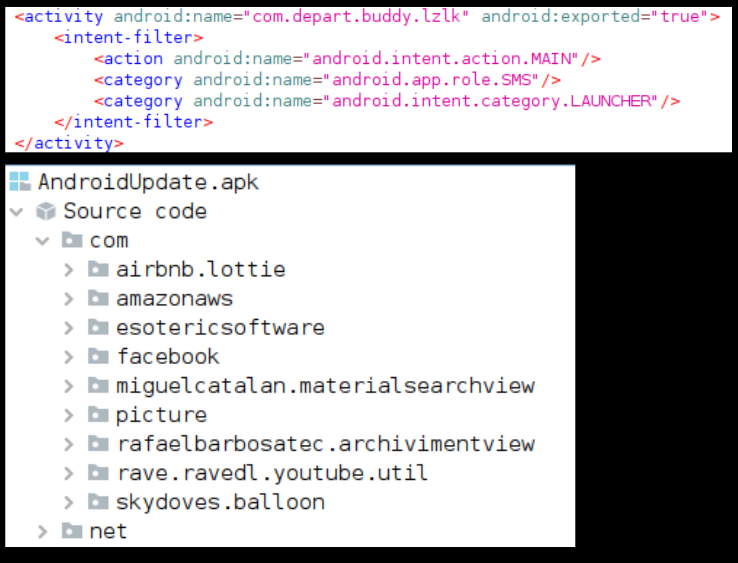
The AndroidManifest.xml file can be used to identify how the application starts the execution flow. In this application the main activity is listed as – com.depart.buddy.lz. However looking at the code, this class is not visible in the list of classes:
This indicates that most likely a new dex file might be dropped during execution and this file will contain the class pointed as the main activity. Once executed, a file named kreaslX.json is dropped in the folder below:
Renaming the .json file to .zip and opening it in a disassembler shows us the missing class files:
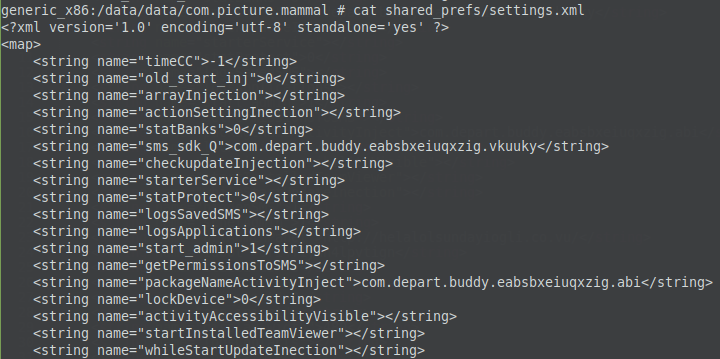
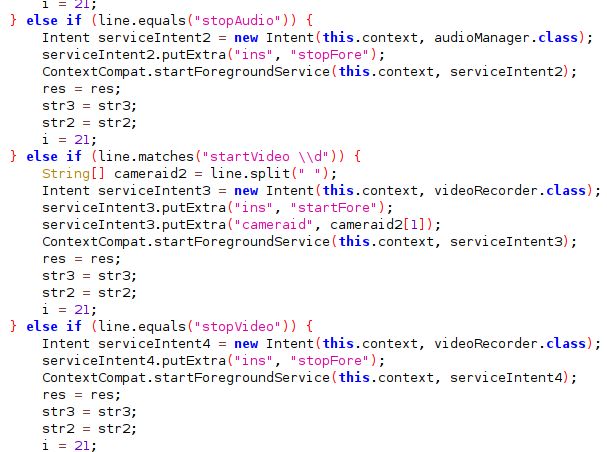
The file shared preferences file settings.xml can be viewed as the configuration file for this application. A number of capabilities of this malware are listed in this file:
Notable capabilities include:
- Log SMS messages on the device
- Log applications installed on the device
- Log contacts
- Request for Admin privileges
- Lock device
- Start TeamViewer application
- Switch the sound off
- Kill an application
- Keylogger functionality
- Turn PlayProtect off
Network Investigation
The application is hosted on hxxps://www.kisa.link/PMmG. VirusTotal graph shows multiple malicious indicators connected with this domain:
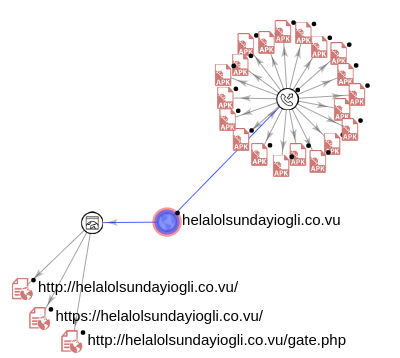
A hardcoded admin panel IP was identified in the shared_preferences.xml fille – hxxp://helalolsundayiogli.co.vu. VirusTotal graph for this domain shows multiple apk files connected to this domain:
Overall this application appears to be part of a larger campaign which is being propagated via the links mentioned. The nature of this application is that of a Remote Access Trojan which is capable of accepting commands and executing the in-built functionality.
Sonicwall Capture Labs provides protection against this threat using the signature listed below:
- AndroidOS.Spy.SM
Indicators of Compromise:
- bfdd4663a096b21a1d2b7c993bb0aecd
- 2dc70002c841181ee1e832381f8429ab