mySCADA Command Injection Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
mySCADA professional tools are for developing and managing HMI (Human-Machine Interface)/SCADA (Supervisory Control and Data Acquisition) industrial processes. myPRO is one tool in mySCADA that is used to allow remote access to HMIs created in mySCADA projects. Users can develop mySCADA projects through myDESIGNER, and upload them to myPRO to allow remote users the ability to access the HMI over the network.
A command injection vulnerability has been reported in mySCADA myPRO. The vulnerability is due to insufficient sanitization of user data used in commands.
A remote, authenticated attacker could exploit this vulnerability by sending a crafted request to the target server. Successful exploitation could result in command execution in the security context of the root user.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-2234.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.6 (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C).
Base score is 9.9 (AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is low.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.6 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
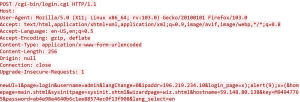
By default, mySCADA contains an HMI project to help administer the server it’s located in “/opt/myscada/prj2”. mySCADA projects can use server-side Node.js scripts to read or write data from various sources such as the sever database or PLCs (Programmable Logic Controller). The server-side scripts can be interacted with by sending an HTTP POST request to the endpoint “/sss2”, with parameters passed in the HTTP body within a JSON object.
When myPRO starts, it creates an Nginx reverse proxy with the configuration file “hmi.conf”. The configuration file includes the file “hmi.auth” containing the configuration for endpoints on the server. Requests made to the endpoint “/sss2” will be forwarded to “hxxp://127.0.0.1:8889” to a Node.js server. myPRO will start Node.js and run the file “/opt/mypro/prj2/Scripts/main.js”.
The main.js file will then call myscada.init() that will call listen() to start the server on port 8889. When the Node.js server receives a user request, the body of the HTTP request will be passed to the function JSON.parse() to parse the request. The decoded body is then passed to the function dataFromViewScripts() to process it. When dataFromViewScripts() is called, the value of the JSON key “type” is compared to multiple strings to determine how the request should be processed. If the “type” key value is “deleteBackup”, the function will first call require() with the parameter “child_process” to include the function exec().
Next, the function exec() is called with the string “/opt/myscada/bin/Backup -d” concatenated with the value of the “filename” key from the JSON from the user request. However, the value of the “filename” is not sanitized, allowing an attacker to inject arbitrary commands to the command-line before it is executed. If the value of the type key is “createBackup” or “restoreBackup”, the values of the “manualType” or “filename” keys will be added to a command-line and executed in a similar manner.
Triggering the Problem:
• The attacker must have network access to the target server.
• The target must be running a vulnerable version of the software.
• The attacker must be able to authenticate to the server.
Triggering Conditions:
The attacker sends a crafted request to the target sever. The vulnerability is triggered when the server attempts to process the crafted request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 3278 mySCADA myPRO Command Injection 1
• IPS: 3280 mySCADA myPRO Command Injection 2
• IPS: 3287 mySCADA myPRO Command Injection 3
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Updating the product to a non-vulnerable version.
• Filtering attack traffic using the signatures above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory