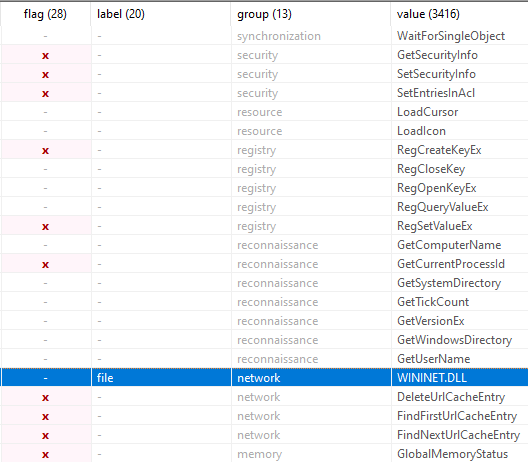
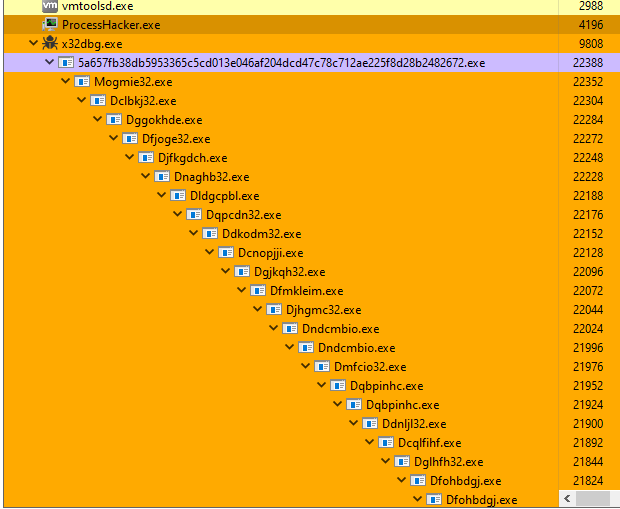
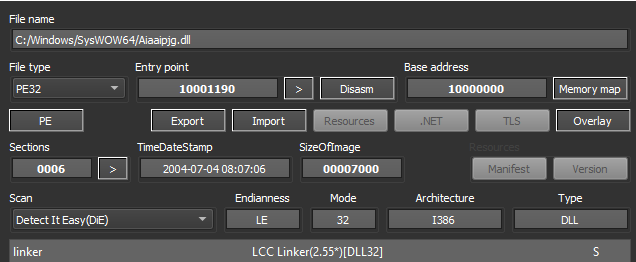
Microsoft Security Bulletin Coverage for February 2023
SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of February 2023. A list of issues reported, along with SonicWall coverage information, is as follows:
CVE-2023-21529 Microsoft Exchange Server Remote Code Execution Vulnerability
IPS 3520: Microsoft Exchange Server Remote Code Execution (CVE-2023-21529)
CVE-2023-21688 NT OS Kernel Elevation of Privilege Vulnerability
ASPY 403: Malicious-exe exe.MP_297
CVE-2023-21689 Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability
ASPY 404: Malicious-exe exe.MP_298
CVE-2023-21690 Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability
ASPY 405: Malicious-exe exe.MP_299
CVE-2023-21692 Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability
ASPY 406: Malicious-exe exe.MP_300
CVE-2023-21706 Microsoft Exchange Server Remote Code Execution Vulnerability
IPS 15834: Microsoft Exchange Server Remote Code Execution (CVE-2023-21706)
CVE-2023-21715 Microsoft Office Security Feature Bypass Vulnerability
ASPY 410: Malformed-File pub.MP.6
CVE-2023-21812 Windows Common Log File System Driver Elevation of Privilege Vulnerability
ASPY 409: Malicious-exe exe.MP_303
CVE-2023-21823 Windows Graphics Component Elevation of Privilege Vulnerability
ASPY 408: Malicious-exe exe.MP_302
CVE-2023-23376 Windows Common Log File System Driver Elevation of Privilege Vulnerability
ASPY 407: Malicious-exe exe.MP_301
The following vulnerabilities do not have exploits in the wild :
CVE-2023-21528 Microsoft SQL Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21553 Azure DevOps Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21564 Azure DevOps Server Cross-Site Scripting Vulnerability
There are no known exploits in the wild.
CVE-2023-21566 Visual Studio Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-21567 Visual Studio Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-21568 Microsoft SQL Server Integration Service (VS extension) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21570 Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability
There are no known exploits in the wild.
CVE-2023-21571 Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability
There are no known exploits in the wild.
CVE-2023-21572 Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability
There are no known exploits in the wild.
CVE-2023-21573 Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability
There are no known exploits in the wild.
CVE-2023-21684 Microsoft PostScript Printer Driver Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21685 Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21686 Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21687 HTTP.sys Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-21691 Microsoft Protected Extensible Authentication Protocol (PEAP) Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-21693 Microsoft PostScript Printer Driver Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-21694 Windows Fax Service Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21695 Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21697 Windows Internet Storage Name Service (iSNS) Server Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-21699 Windows Internet Storage Name Service (iSNS) Server Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-21700 Windows iSCSI Discovery Service Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-21701 Microsoft Protected Extensible Authentication Protocol (PEAP) Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-21702 Windows iSCSI Service Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-21703 Azure Data Box Gateway Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21704 Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21705 Microsoft SQL Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21707 Microsoft Exchange Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21710 Microsoft Exchange Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21713 Microsoft SQL Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21714 Microsoft Office Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-21716 Microsoft Word Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21717 Microsoft SharePoint Server Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-21718 Microsoft SQL ODBC Driver Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21721 Microsoft OneNote Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2023-21722 .NET Framework Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-21777 Azure App Service on Azure Stack Hub Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-21778 Microsoft Dynamics Unified Service Desk Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21797 Microsoft ODBC Driver Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21798 Microsoft ODBC Driver Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21799 Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21800 Windows Installer Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-21801 Microsoft PostScript Printer Driver Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21802 Windows Media Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21803 Windows iSCSI Discovery Service Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21804 Windows Graphics Component Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-21805 Windows MSHTML Platform Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21806 Power BI Report Server Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2023-21807 Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability
There are no known exploits in the wild.
CVE-2023-21808 .NET and Visual Studio Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21809 Microsoft Defender for Endpoint Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2023-21811 Windows iSCSI Service Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-21813 Windows Secure Channel Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-21815 Visual Studio Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21816 Windows Active Directory Domain Services API Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-21817 Windows Kerberos Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-21818 Windows Secure Channel Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-21819 Windows Secure Channel Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-21820 Windows Distributed File System (DFS) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-21822 Windows Graphics Component Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-23377 3D Builder Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-23378 Print 3D Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-23379 Microsoft Defender for IoT Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-23381 Visual Studio Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-23382 Azure Machine Learning Compute Instance Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-23390 3D Builder Remote Code Execution Vulnerability
There are no known exploits in the wild.