Linux Kernel KSMBD NULL Pointer Dereference Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
KSMBD is an integral server component within the Linux kernel. Its primary function is to implement the SMBv3 protocol, which is essential for sharing files over a network. Operating in kernel space ensures that KSMBD offers efficient and seamless file sharing capabilities to users of the Linux operating system.
Recently, a significant vulnerability has been identified in ksmbd. This vulnerability stems from a NULL pointer dereference issue, a critical flaw in the system’s architecture. The root cause of this vulnerability is the system’s inability to validate user-supplied data adequately, especially when processing compounded requests. Given the importance of ksmbd in the Linux Kernel, this vulnerability raises substantial security concerns.
The vulnerability provides an avenue for remote attackers to compromise the system. By sending specifically crafted packets to the target, which is vulnerable, attackers can exploit this flaw. If they succeed in their exploitation attempt, the aftermath can be detrimental, leading to a denial of service. This means that the targeted system could be rendered inoperable, disrupting its functionality and potentially causing significant downtime.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-3866.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 6.5 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H/E:U/RL:O/RC:C).
Base score is 7.5 (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is none.
• Impact of this vulnerability on data integrity is none.
• Impact of this vulnerability on data availability is high.
Temporal score is 6.5 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
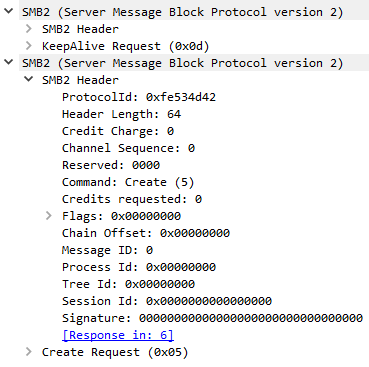
A NULL pointer dereference vulnerability has been identified in the ksmbd kernel module when it processes compounded SMB2 requests. This issue arises because certain pointer validations can be overlooked during the processing of combined SMB2_NEGOTIATE, SMB2_SESSION_SETUP, or SMB2_ECHO requests.
The internal function, __handle_ksmbd_work, manages these incoming SMB messages. This function invokes smb2_check_user_session() to ensure the SMB2 message contains a valid session ID for the intended operation, and smb2_get_ksmbd_tcon() to check if the SMB2 message has a valid tree ID. Notably, these validations always pass for the aforementioned SMB2 requests since they haven’t established a session.
The vulnerability emerges when the function doesn’t account for these SMB2 requests being part of compounded requests. If the NextCommand field in any such SMB2 message isn’t set to zero, subsequent SMB2 requests sidestep the validation, potentially leading to a NULL pointer being used in session or tree dereferences.
Triggering the Problem:
• The vulnerable system must be listening on the vulnerable SMB port, and accept incoming connections.
• The attacker must have connectivity to the target system.
Triggering Conditions:
The attacker establishes a connection with the targeted ksmbd server. Once this connection is in place, the server becomes susceptible to the aforementioned threat. The vulnerability is activated when the attacker transmits a compounded request loaded with malicious content to the server in question. It’s essential for server administrators to be aware of such vulnerabilities to ensure their systems are adequately protected and to monitor for any unusual connection requests.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• SMB/CIFS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 4022 Linux Kernel ksmbd NULL Pointer Dereference 1
• IPS: 19332 Linux Kernel ksmbd NULL Pointer Dereference 2
• IPS: 19333 Linux Kernel ksmbd NULL Pointer Dereference 3
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Configure the vulnerable product to allow access to trusted clients only.
• Update to a non-vulnerable version of the product.
• Filter attack traffic using the signatures above.
The vendor has released the following commit regarding this vulnerability:
Vendor Advisory
