Delta Electronics Deserialization Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
Delta Electronics InfraSuite Device Master is a tool for centralized monitoring and control of a large number of devices. Users create a human-machine interface (HMI) to manage the devices. Users observe the status of all devices, query event logs or history data, and assists users in taking appropriate action. InfraSuite Device Master implements a 3-tiered architecture, including the Data Collection layer, Gateway layer and Presentation layer.
An insecure deserialization vulnerability exists in Delta Electronics InfraSuite Device Master. The vulnerability is due to missing input validation when processing messages sent to Device-DataCollect service.
A remote, unauthenticated attacker could exploit this vulnerability by sending crafted requests to the target server. Successful exploitation allows arbitrary code execution with privileges of the user running the vulnerable software.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-38142.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.5 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.5 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
The vulnerability is due to a combination of a lack of authentication required to access the exposed Device-DataCollect service and also for insecure deserialization when processing messages sent to Device-DataCollect service. When a BinaryFormatter serialized request is sent to DeviceDataCollect, the InfraSuiteManager.Common.PacketHeader object is deserialized by calling the vulnerable method DeSerializeBinary() in the .NET class InfraSuiteManger.Common.Serialization from the method CheckPacket() in the .NET class InfraSuiteManager.Common.PacketOperation.
Next, the method DoUpperLayerNWPacket() in InfraSuiteManager.DataCollectionLayer.DataCollectionLayerMngt is called from the MainLoop() method in the same class to process the packet payload object which is expected to be one of the objects of type:
InfraSuiteManager.Common.DCLayerNWCommand_DeviceObject,
InfraSuiteManager.Common.DCLayerNWCommand_Protocol,
InfraSuiteManager.Common.DCLayerNWCommand_Polling,
InfraSuiteManager.Common.DCLayerNWCommand_Server,
InfraSuiteManager.Common.DCLayerNWCommand_DCServerSand,
InfraSuiteManager.Common.DCLayerNWCommand_LogPollingRawData
This method will call one of the methods: DCLayerNWCommand_DeviceObject(), DCLayerNWCommand_Protocol(), DCLayerNWCommand_Polling(), DCLayerNWCommand_Server(), DCLayerNWCommand_DCServerStatus() or DCLayerNWCommand_LogPollingRawData(), dependent on the value of the i32PayloadType field in the InfraSuiteManager.Common.PacketHeader object. Each of these methods call the vulnerable method DeSerializeBinary() in .NET class InfraSuiteManger.Common.Serialization.
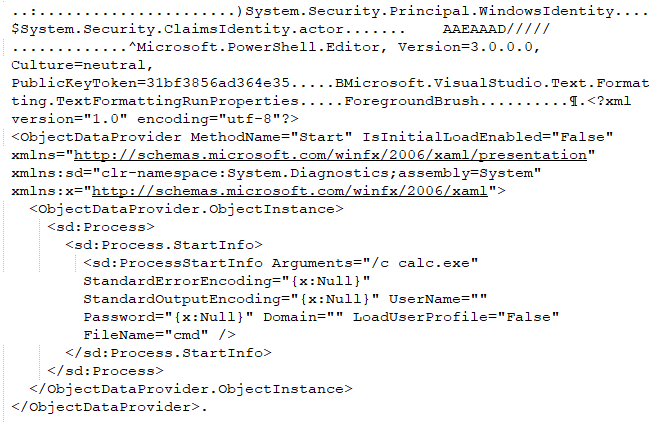
The vulnerable method DeSerializeBinary() invokes the method System.Runtime.Serialization.Formatters.Binary.BinaryFormatter.Deserialize() where the insecure deserialization can occur. The code does not perform checks on the contents of the serialized object. The attacker can thereby employ ysoserial.net gadget generator to craft malicious payloads instead of PacketHeaderObject or PacketPayloadObject leading to arbitrary code execution vulnerability.
Triggering the Problem:
• The target must have the vulnerable software installed.
• The attacker must have network connectivity to the target server.
Triggering Conditions:
The attacker sends a malicious serialized payload to the target server. The vulnerability is triggered when the server processes the request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• Device-DataCollect Protocol
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2063 Delta Electronics InfraSuite Device Master Insecure Deserialization
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Upgrading the product to a non-vulnerable version.
• Detect and filter malicious traffic using the signature above.
The vendor has released the following advisory regarding this vulnerability:
ICS-CERT Advisory