Schneider Electric IGSS Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
Schneider Electric’s Interactive Graphical Supervisory Control and Data Acquisition (SCADA) System (IGSS) is used for monitoring and controlling industrial processes. According to the vendor, more than 28,000 IGSS licenses have been sold around the world and IGSS is installed in many different industries, including the Oil and Gas, Traffic Control, and Waste Water industries.
An integer overflow vulnerability exists in Schneider Electric IGSS. The vulnerability is due to input validation error when processing ALMNOTE opcode.
A remote, unauthenticated attacker could exploit this vulnerability by sending a maliciously crafted packet to the target service. Successful exploitation could cause denial-of-service and potentially remote code execution.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-2329.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.5 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.5 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
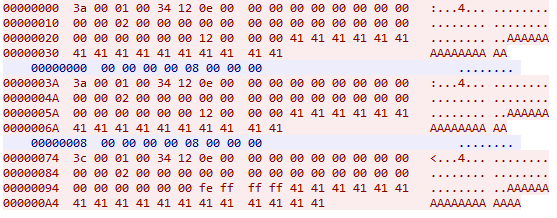
The vulnerability is due to the missing validation of the size field in the request sent to the server. When the data server receives a message, the function IGSSdataServer.exe+0xb30b0() is called, which calls the C library function WSARecv() to retrieve the contents of the message from the socket. Later, in the same function, the code checks that Opcode1 is equal to 1. If false the function exits. If true, the code calls a switch statement on the value of the Request Type field and enters the appropriate path of code execution.
If the Request Type field is equal to 14, then the code execution enters the potentially vulnerable code path. The code calls function IGSSdataServer+0xf7650(). This function is called using the function pointer which is set only after the first request. Therefore, this function is only called after the second or subsequent request. Inside this function, the code calls the C library function realloc() with the size parameter in this function set to the (size field from the previous request + size field from the current request). This function does not perform validation on the computed value of the vulnerable addition operation of the size fields in the previous request and in the current request.
Next, the code calls the C library function memcpy() to copy the “note” data field from the current request to the new buffer using the new reallocated heap buffer which maybe be smaller than intended due to integer overflow. The code keeps track of the value of the size field from the previous request in another heap buffer. Then, the code copies the “note” data in the current request to the new reallocated buffer. Since this new buffer size can be too small to fit the length of the “note” data field in the request, due to earlier integer overflow, a heap-buffer overflow can ensue.
Triggering the Problem:
• The target must have the vulnerable product installed and running.
• The attacker must have network connectivity to the server running the vulnerable product.
Triggering Conditions:
A remote attacker sends three crafted packets with Request Type set to 14. The vulnerability is triggered when the affected product parses the malicious requests.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• 7-Technologies (7T) IGSS Protocol
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 3304 Schneider Electric IGSS Integer Overflow
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Apply the vendor supplied patch to eliminate the vulnerability.
• Filter attack traffic using the signature above.
The vendor, Schneider Electric, has released an update and advisory regarding this vulnerability:
Vendor Advisory