Laravel Ignition Remote Code Execution Vulnerability
Ignition versions prior to 2.5.2, as used in Laravel and other products, allows unauthenticated remote attackers to execute arbitrary code because of insecure usage of file_get_contents and file_put_contents. This is exploitable on sites using debug mode with Laravel versions prior to 8.4.2
Ignition is a beautiful and customizable error page for Laravel applications running on Laravel 5.5 and newer. It is the default error page for all Laravel 6 applications. It also allows to publicly share your errors on Flare. If configured with a valid Flare API key, errors in production applications will be tracked, and you’ll get notified when they happen. So, it can hook into the framework to display the uncompiled view path and your Blade view. It has various features such as app, user ,context and debug tab. It not only displays error but also suggests a solution.
Vulnerability | CVE-2021-3129
Ignition before 2.5.2, as used in Laravel and other products, allows unauthenticated remote attackers to execute arbitrary code. This is exploitable on sites using debug mode with Laravel before 8.4.2.
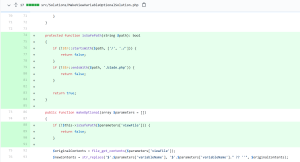
The vulnerability lies in a way in which the file_get_contents function is implemented in the module MakeViewVariableOptionalSolution.php of Ignition . The file_get_contents function doesn’t check the path and an attacker can abuse this weakness to view and write code of attackers choice at the path specified by an attacker.

This vulnerability is patched . When we look at the patched code we see that file_get_contents now checks the path before getting contents.
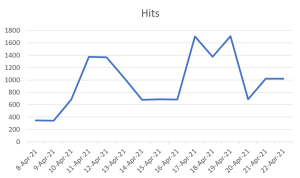
Threat graph:
SonicWall Capture Labs provides protection against this threat via following signatures:
-
- IPS 15444:Laravel Ignition Insecure Deserialization 1
- IPS 15445:Laravel Ignition Insecure Deserialization 2
